Dropbox announced Tuesday that a recent security breach compromised a list that included the email addresses of certain Dropbox users. To avoid future complications, the service announced that it would be implementing two-factor authentication, and even more useful, a security page that lets you monitor all activity on your account. In light of this and other recent web security threats, you might also want to know that services like Gmail, Facebook, and Yahoo! Mail have similar pages where y...
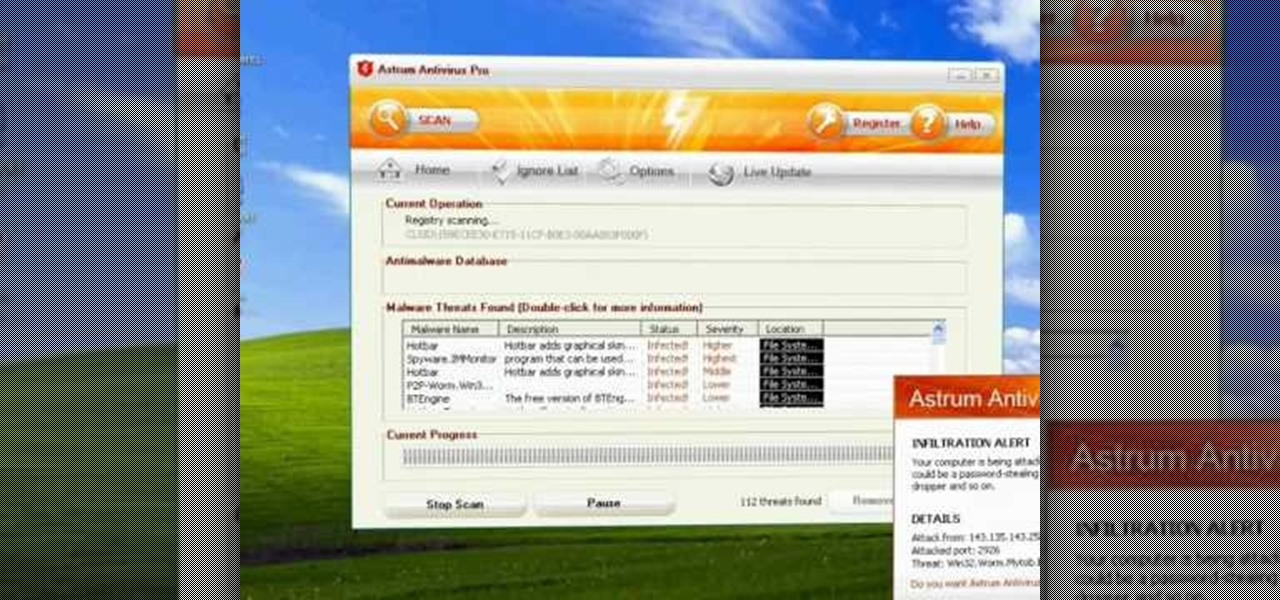
Astrum Antivirus Pro is a rogue anti-spyware application and a clone of VirusTrigger and Antivirus Trigger. Astrum Antivirus Pro is often downloaded and installed by a Trojan or through browser security holes. Astrum Antivirus Pro may generate large numbers of popup adverts. Astrum Antivirus Pro will also display notifications of imaginary security risks in its attempts to get the user to purchase the full version. Astrum Antivirus Pro may run a fake system scanner and then display fake syste...

Housing clips can be deliate and fragile. When slipping your camera into it's case, make sure you don't apply too much pressure in the wrong place and break the clip. This video shows you the right way to close the case around your camera and avoid breakage.

A non-CPU lens is one which does not have contacts on the rear mount, meaning it communicates with the rest of the camera solely through the aperture. This tutorial shows you how to set up the lens data for your camera, so you can get the most out of your non-CPU lens.

You don't need an elaborate camera to take stunning close-up photos. Watch this photography tutorial video to learn how to take nice close-ups with your Canon A550. You'll be able to take beautiful close-up photos with this camera after you've mastered the tips in this helpful how-to video.

The camera connector kit from Apple is a great accessory if you want to instantly edit and interact with photos that you take on your portable digital camera. This tutorial will show you how to make use of the iPad's camera connector so that you can adjust those photos on the go.

The Droid 3 smartphone from Verizon has a great camera perfect for taking beautiful photos. If you want to learn how to perfect your on-the-go photography, take a look at this tutorial from Verizon Wireless that features instructions on all the different settings in the Camera app on the Android device.

If you take a lot of photos with your smartphone or cheap digital camera, you can see the difference compared to results from a pro camera. So, if you want to get a professional camera look without dropping the money, check out this video to learn how to enhance your pics. This trick works with Photoshop, or any photo editing software that has a selection tool, a gradient tool and a gaussian blur filter.

No one in their right mind would ever volunteer to be one of the Red Shirts, the security officers from Star Trek who so often died during the crew's away missions. Well, it is a pretty easy-to-make and easy to recognize costume, so it might be a good choice for your next nerdy Halloween party or other get-together. This video wills show you how to make a Red Shirt shirt of a long-sleeve shirt and paint.

Old camera equipment like flashes and lenses are often praised by modern photographers, but getting them integrated into new digital photography setups can be a challenge. This video will show you some tips for using old flashes with new digital cameras, including a great trick for making your digital camera recognize the flash by covering one specific contact. Don't get a new flash, use an old one with the skills you learn in this video.

Kipkay's ingenuity is enough to amaze us all, especially all of you indie filmmakers. These five tips for aspiring filmmakers will help you keep your sanity and avoid frustrating times. Have you ever got stuck in the rain while shooting? Have your recorder tapes ever gotten disorganized? Is your camera's display getting scratched up more than you want? Kipkay answers all of these questions with his five ingenious video tips.

Attention photography lovers! Put down the digital camera for a day and try this DIY project out, constructing a camera that dates back to as early as 4th century BC.

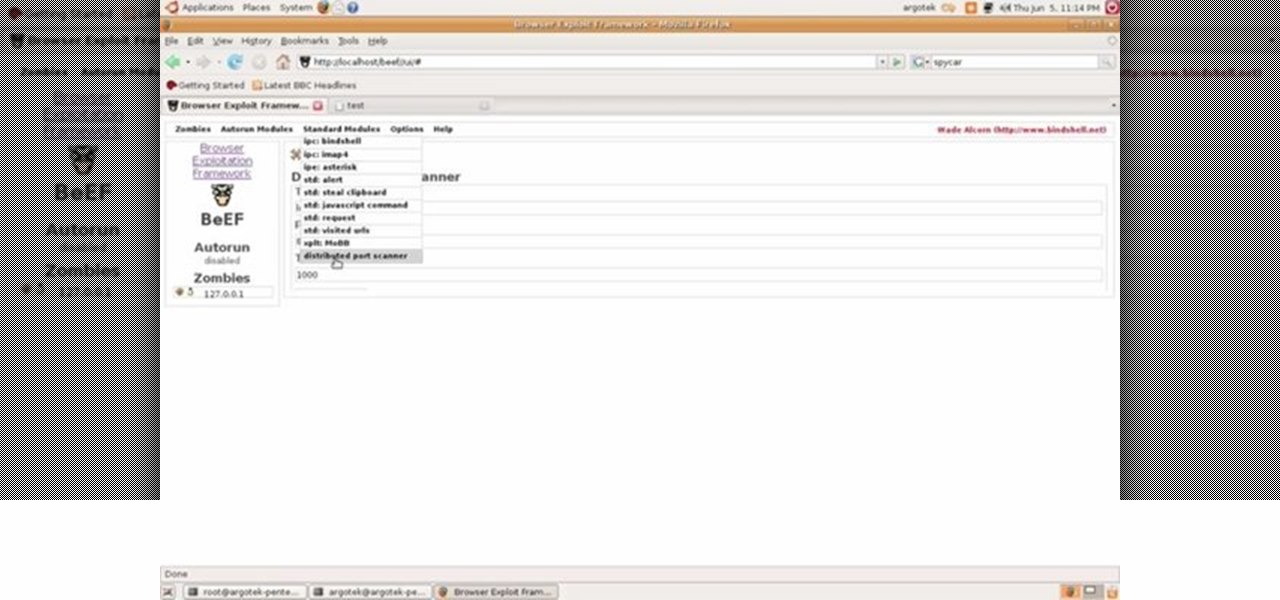
This video tutorial talks about browser exploitation. Particularly, it talks about tools, like BeEF, that can be used to hack known vulnerabilities within browsers and some cool frameworks that you can use to check the security of your own browser. To get started hacking your own browser, watch this how-to.

This tutorial builds the RED ONE camera from scratch into a traditional film style camera, complete with matte box and follow focus.

The Red One Camera has three buttons labeled A B and C on the back of the camera. Each of these buttons have a specific feature that is the default setting. Learn what these buttons do.

This is the most basic thing, but you gotta learn it. How do I turn the Red One camera on? There is only 1 on/off button and its on the back of the camera.

Camera angles can be expressed in both physical and psychological terms. The first episode presents the physical angles: low-angle, high-angle, and dutch angle.

Watch this video and learn how to convert a Super Wide Polaroid camera into a pinhole camera. This conversion will also work for super shooter and colorpack cameras. Strip down the camera, "chop" the body and prep to recap for a super wide angle pinhole camera. This project works for cameras that accept 3.25 x 4.25 polaroid and fujifilm instant pack films.

This video gives you a basic understanding of how to use Radio Frequency Identification (RFID) and text to speech modules. Learn how to integrate your home PC with external modules for security and fun!

Kipkay has developed a shoplifting prank, and all you need is a little electromagnetic strip to play this prank at Walmart (or wherever). You also need to bring a magnet. You swipe the strip thirty times with the magnet and this will actually magnetize the strip. Use this as inspiration for one of your April Fools Day pranks!

This video shows you how to set up and hide mini wireless spy camera. Where you put it is up to you. Who you spy on is up to you. If you're wanting to keep an extra set of eyes on someone, watch and learn. Whether it's your bathroom or kitchen, put your eyes on the prize.

If you have a new Canon EOS 7D camera, but have yet to purchase a Zoom H4N recorder, have no fear! In this clip, you will learn how to make a comparable device using your MacBook. This clip will give you a step by step for this relatively simple process so that you can get started making movies, right away!

If you are out with friends and don't have anyone to take your photo for you, you will need to take a self portrait. Instead of fumbling with a self timer, most people hold the camera themselves and take a snap. Unfortunately, these photos are hard to center and you often cut people off and lose what could have been a great shot.

This video shows how to setup and use your DynaSpy wireless video surveillance camera.

One of the biggest advantages of the front-mounted ultrasonic fingerprint sensor found on the Galaxy S10 and S10+ is that you no longer have to physically pick up your device and reach around the back to unlock it. Instead, you simply place your finger on the screen for easier access and added convenience — at least on paper.

The "controversial" Pixel. No phone in the history of Google's Pixel lineup deserves this title more than the Pixel 3 XL. For some (including myself), the design is a welcome change that embodies the modern design of 2018 flagship phones. For others, it has an ugly huge display notch that destroys symmetry.

When BlackBerry first announced the KEY2 back in June, the biggest gripe we heard was about the price. It was reasonable criticism, as BlackBerry was asking a lot of its consumers at $650. Knowing this, BlackBerry went back, made some downgrades, and cut the price, creating the KEY2 LE.

A massive leak appeared the web today, and it's got some huge security implications for every iPhone on the market. On the plus side, it also has some potential for enabling deep-level modifications and jailbreak tweaks.

Because of the way Google Play works, Android has a "bad app" problem. Google allows any developer to upload an app to the Play Store, regardless of if it works, how it looks, or whether or not it can harm users. Malware scanning happens primarily after apps are uploaded, and though Google has recently taken steps to safeguard users with its Play Protect program, you don't have to depend on them.

The last quarter of 2017 brought us some downright excellent smartphones. Between the iPhone X, Pixel 2, and Note 8, consumers have more fantastic options than ever when choosing a new device. It's now the perfect opportunity for Samsung to set the tone for 2018 smartphones with their exceptional S9 and S9+.

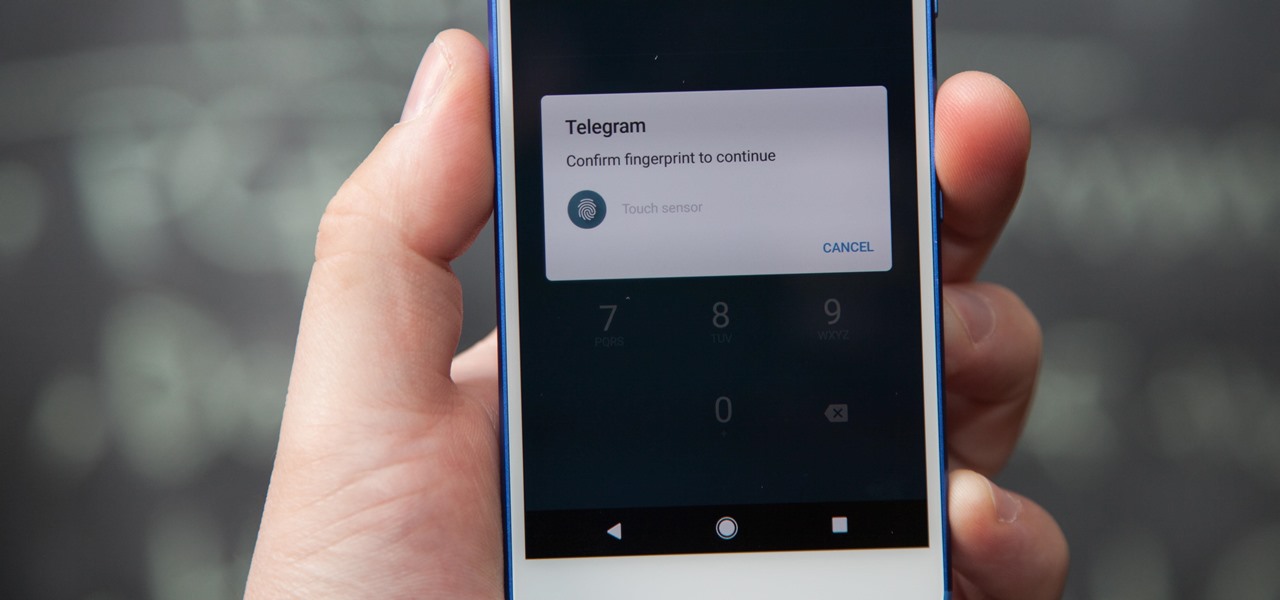
If you're using Telegram for its "Secret Chats" feature, which provides end-to-end encryption for your messages, then I'd highly recommend locking down the app itself with a passcode, PIN, or password. While your phone itself may have a secure lock screen already, if that gets compromised, you'll at least have an extra layer of security on your important conversations.

If Detective Alonzo Harris from Training Day taught me anything, it's that "It's not what you know, it's what you can prove." So when items mysteriously go missing from my room or my section of the fridge, it's up to me to figure out and prove which roommate took them.

Yes, "Safer Internet Day" is a real thing, and it's actually been around for 12 years. This year, Google again will be commemorating the event by giving away a 2-gigabyte storage bump for their Google Drive cloud service if you simply run through a security checkup.

Losing your phone is a much bigger ordeal today than it was just 10 years ago. Our smartphones carry with them lots of sensitive data that, in the wrong hands, is capable of being used for identity theft and fraud.

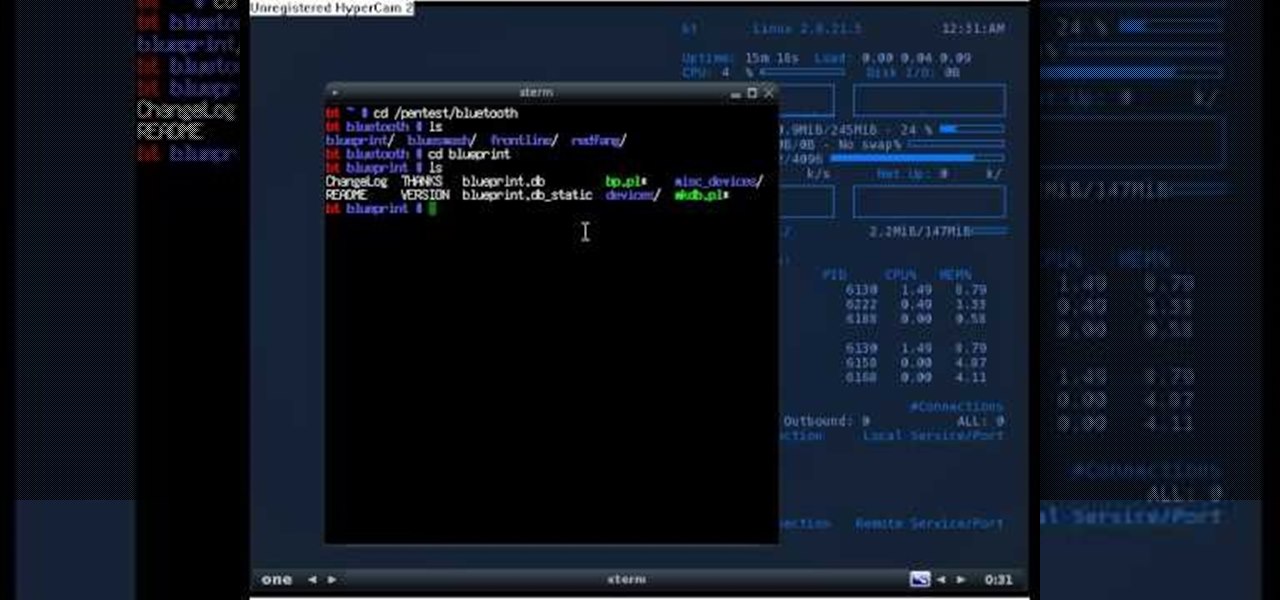
If you're new to the Bluetooth hacking world, here's a little background on using Linux BackTrack to hack a Bluetooh device: Linux Backtrack is a Live DVD device that offers security tools - like password crackers - that allow you penetrate networks.

Security is tighter than ever in U.S. airports. From the recent instigation of the hotly debated full-body scans and pat-downs to the TSA limiting every ounce of body lotion you bring, it's hard to make it through the security gates without some major airport hate.

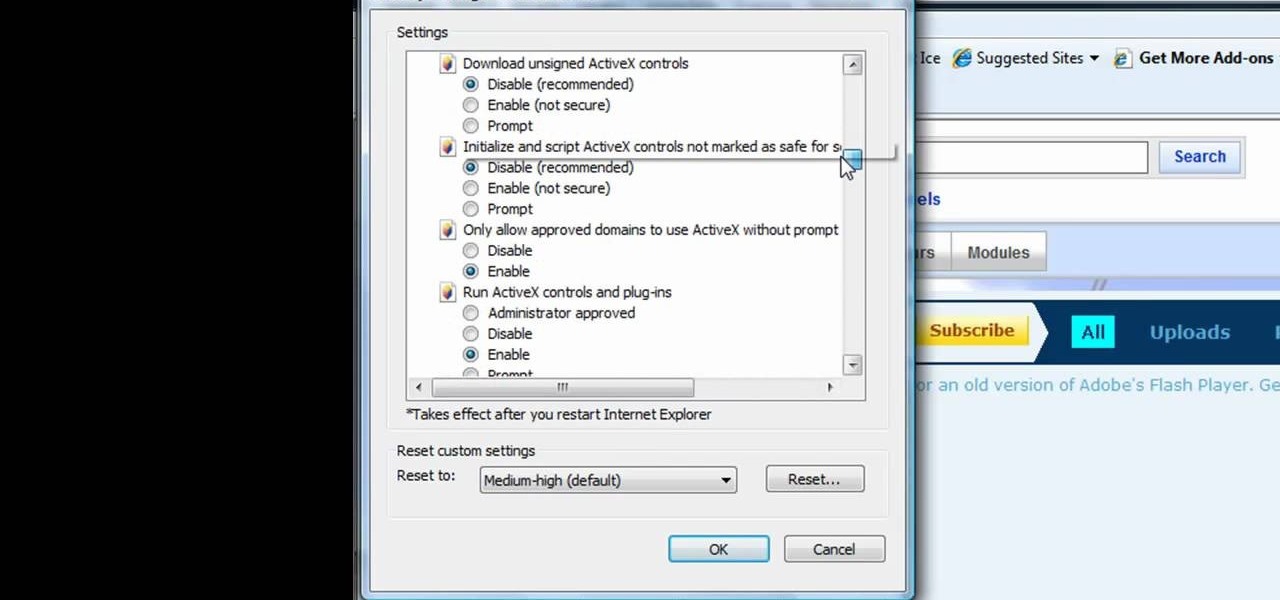
This tutorial shows us how to enable JavaScript in Internet Explorer. First, go to the top right of IE and click "tools". Then, click "internet options" and then go to the security tab. From here, select your security level that you want by clicking "custom level". Scroll down to the bottom and find the tab that says "active scripting" and make sure it's enabled. Click on "ok", then refresh the page that you are on. Now you should be able to watch videos and use anything that uses JavaScript ...

The difference between an amateur piece of jewelry and a professional one often lies in the details. Almost anyone can link chains together into a necklace and add small floral baubles, but the professional will take care to make sure the baubles are attached almost imperceptibly and the closure blends in with the rest of the necklace and also won't budge.

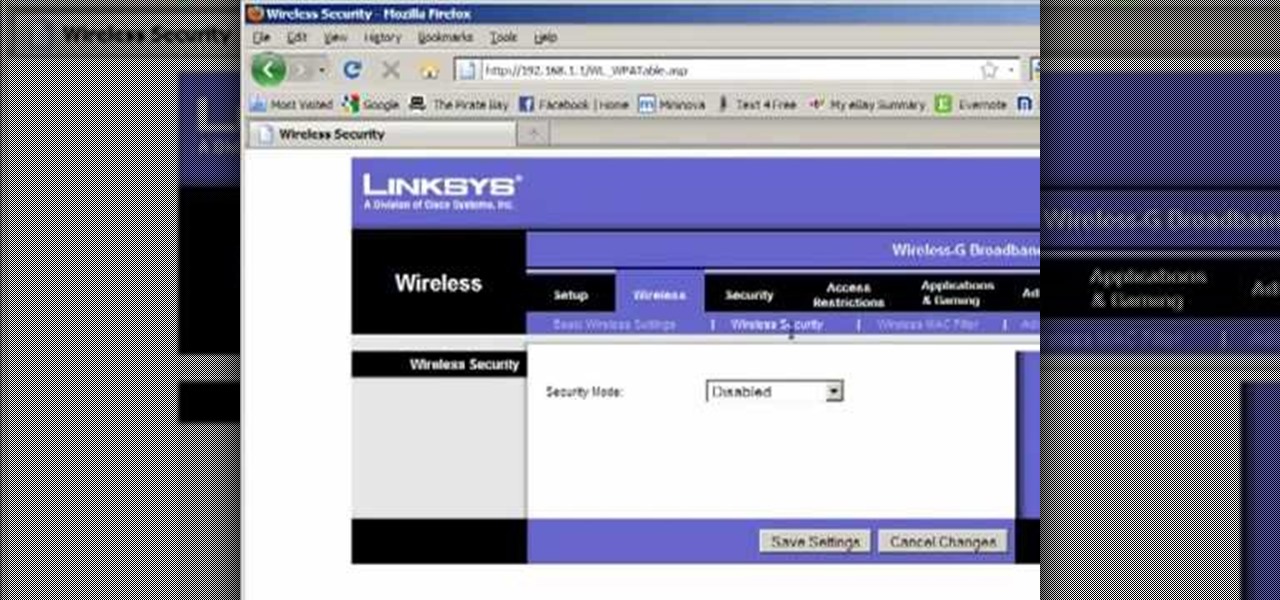
Most of the home wireless networks are not set up by professionals and hence they might lack in security features. People just set up the wireless networks by connecting the devices and powering them up and never care to apply security settings to the network. This may result in your wireless network being compromised by unwanted external entities. How ever you can do a web based configuration settings and secure your wireless network by password protecting it. This settings differ from the m...

Llewyn demonstrates how to configure your router for Wifi. Access the router by opening up your internet browser and typing in your router's IP address. That will bring up the router configuration page. Now, click on the wireless tab. You can set the wireless network mode to accommodate your computers. As a precaution, set the mode to mixed for greater flexibility. Set your wireless SSD broadcast to enable which will enable your wireless card to actually see the webpage and the internet. You ...