This video will show you how to protect others from accessing saved password on Google Chrome. Saving account passwords in browsers are useful for time saving as well as threatening for malicious activity. This is dangerous for security. So you must protect your accounts detail from others to secure your browsing. Watch the video and follow all the steps carefully.

Welcome back, my tenderfoot hackers! I have written many tutorials on hacking using Metasploit, including leaving no evidence behind and exploring the inner architecture. Also, there are my Metasploit cheat sheets for commands and hacking scripts.

Lock screen apps are a dime a dozen, but every now and then one pops up that defies expectations. We've already covered some good ones for the Samsung Galaxy S4, including Picture Password Lockscreen (which gives you secret unlock gestures), SlideLock (which improves notifications), and TimePIN (which gives you a more clever PIN).

Welcome back, my novice hackers! The worst thing that can happen to any hacker is being detected by a security admin, the security technologies (IDS, firewall, etc.), or a forensic investigator.
This video will guide you how to blur faces in YouTube video. Many times it’s needed to blur the faces of people in videos. In many sensitive cases faces are blur due to security or confidentiality reasons.

Figuring out someone's password, pattern, or PIN isn't very difficult—simply watching over their shoulder or following the oil marks left across their screen is enough to figure them out and bypass whatever lock screen security they have.

Some of my favorites hacks are the ones that speed up the process of accessing my favorite and most-used apps. So, in this softModder guide, I'll be showing you a super fast way to open those apps straight from your Samsung Galaxy Note 3's lock screen.

With the the general computer users understanding of Information security rising (at least to the point of not clicking on unknown links), and operating system security getting better by default. We need to look for new and creative ways to gain a foothold in a system.

From personal photos and videos to online banking passwords saved in your web browser, your phone has all kinds of sensitive data that needs to be protected. One of the best things you can do for your Samsung Galaxy S4's data is have a lock screen with a hard-to-guess PIN or password.

Welcome back, my novice hackers! This next subject might seem a bit obscure, but I promise you, this lesson will benefit you significantly either as a hacker or system admin. This tutorial will cover what is usually referred to as a regular expression, or regex for short.

Let's be honest for a second; we all have sensitive material on our phones that we wouldn't want anyone else to ever see. Maybe it's to protect ourselves or someone else, or maybe it's none of your business why I don't want you to see pictures of my bachelor party. Regardless, sometimes we need to keep things hidden and safe.

Welcome back, my fledgling hackers! As nearly everyone has heard, Target Corporation, one of the largest retailers in the U.S. and Canada, was hacked late last year and potentially 100 million credit cards have been compromised. Happening just before Christmas, it severely dampened Target's Christmas sales, reputation, and stock price (the company's value has fallen by $5B).

#FOMO. If it bugs the living hell out of you that you don't know what that means, you're presently FOMO, as in you've got a Fear of Missing Out.

Samsung just concluded their live unveiling of the Samsung Galaxy S4! A more in-depth look can be found here.

Even though iOS 6.1 was only released a couple of weeks ago, hackers released evasi0n a couple days after. Evasi0n, the only iPhone 5 jailbreak currently on the market, is the most popular jailbreak in history—with nearly 7 million iOS devices already hacked in the mere four days after its release. Well, now it seems that iOS 6.1 is being taken advantage of again, this time with a simple exploit figured out by YouTube user S1riOS6, which lets you bypass the lock screen on an iPhone running iO...

An internet connection has become a basic necessity in our modern lives. Wireless hotspots (commonly known as Wi-Fi) can be found everywhere!

UPDATE: A patch to fix the exploit has been released. Download it here.

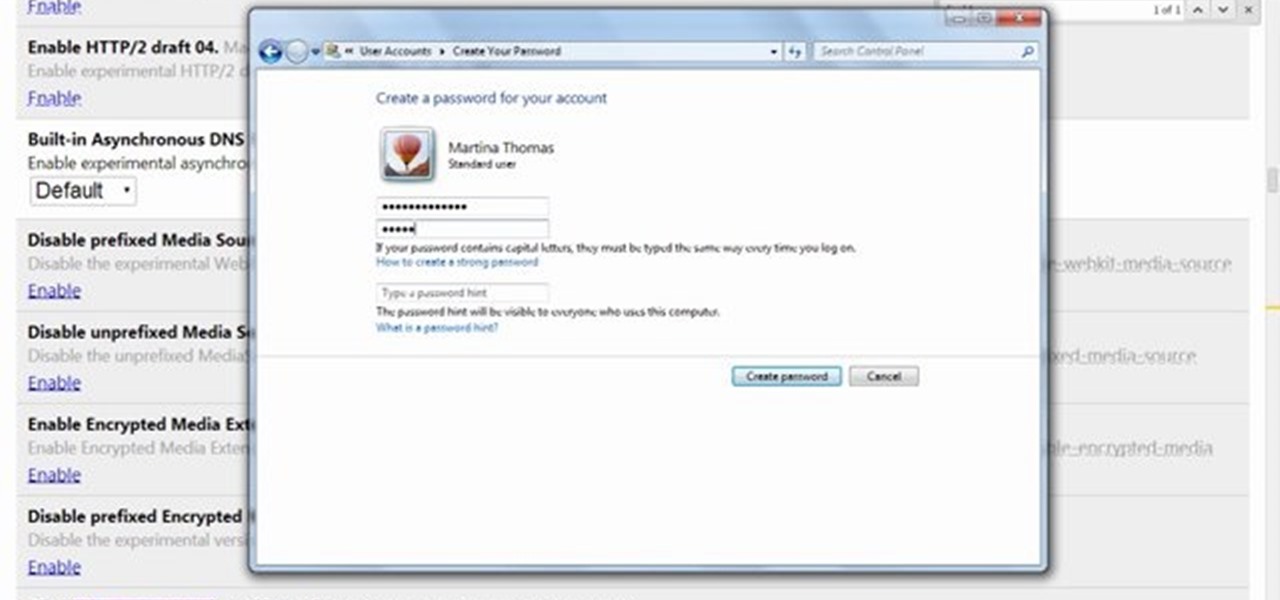
Even though we all know it's a bad idea, a lot of people still use their browser's store password function to keep up with all their accounts. While convenient, this shortcut also makes their passwords very easy to find if you have access to the computer they're stored on.

If you use Ubisoft's uPlay browser extension, you should probably get rid of it right now. An Information Security Engineer at Google discovered that the plugin has a hole in it that allows programs to be installed through uPlay, essentially letting anyone who feels so inclined to take over your computer. How the Exploit Works

It used to be that you only had to worry about maids rummaging through your belongings in your locked hotel room. But now anyone with 50 bucks of hardware and some programming skills can hack their way in—as long as it's locked by keycard.

Most of the time, asking to borrow someone's car will elicit a really long string of excuses. But unlike letting your buddy use your car, which usually gets you nothing more than an empty tank, GM has found a way to make car sharing beneficial for everyone involved. If you're one of the 6 million people who have a GM vehicle that's connected to OnStar, you're in luck: according to an OnStar employee, you can make up to $1,000 a month just by letting other people rent out your car when you're ...

If anybody knows how to pick a lock, it's Schuyler Towne.

Apple's latest big software update includes an entirely new Apple app, a controversial change in the TV app, better Siri control, an improved Shortcuts app, interesting Safari upgrades, Apple Music Sing, and more. Keep reading to see what iOS 16.2 has to offer your iPhone.

Android 11 is here. Prior to Google dropping the naming scheme, this would have been a dessert with an R name (maybe Rice Krispies Treat or Red Velvet Cake) — but nope, just plain ol' Android 11. And after months of betas and a global pandemic, it finally debuted a little over a year after Android 10.

The new iOS 14 for iPhone arrived Wednesday, Sept. 15, 2020, alongside iPadOS 14, and there are a lot of features to uncover. Improved widgets. Better home screen customization. Exciting Messages improvements. New abilities in Camera and Photos. There's so much here that it'll take months for you to learn everything by heart.

Penetration testing, or pentesting, is the process of probing a network or system by simulating an attack, which is used to find vulnerabilities that could be exploited by a malicious actor. The main goal of a pentest is to identify security holes and weaknesses so that the organization being tested can fix any potential issues. In a professional penetration test, there are six phases you should know.

Thanks to Yifan Lu, it's been discovered that the operating system running on the Kindle Touch is written mostly in HTML5 and JavaScript, unlike the previous models which used Java. This is exciting, because when a device is hacked or rooted, that means homebrew programs can be run on the device, maximizing its potential and getting the most for your money.

This video tutorial belongs to the software category which is going to show you how to convert a Word document to a password protected PDF file with NovaPDF. Go to NovaPDF and download the program and install it. It is a paid program. Select the word document that you want to convert and select print option. Under the name of the printer you will find novaPDF option. Select this and click 'preferences'. Now click on 'security' and select high level encryption. In the document permissions, sel...

To take apart a PS3, you will need the following tools: Phillips-head screwdriverPliersTiny Phillips-head screwdriversTiny flat-head screwdrivers

Do you like to play hockey but have no idea how to skate? Are you more of a summer person than a winter one? Do you live somewhere where ice is hard to find? Well, then check out this tutorial and learn to play street hockey! Get all the fun of hockey without the cold, icy mess!

Cars are expensive to buy, replace or repair. Check out this video and learn how to avoid the most statistically dangerous parking areas. There is no guarantee that no one will touch your vehicle, but by take precautions you are much less likely to be targeted.

Nothing to wear but have an old scarf hanging around? No problem! In a few easy steps you can transform that boring scarf into a cute, summery halter top!

Follow the steps outlined in this video to learn how to connect to XBox Live using a laptop running Windows XP. The first step is to connect the XBox with the laptop by using an Ethernet cable. When they are connected you have to click on Start and select 'Connect To' and then 'Show all connections'. Select both the Wireless Area connection and the Local area connection icons by highlighting both of them. To do so hold the Ctrl button until they are both highlighted. At this point right click...

Stan shows an easy way to see and clean the files that are hogging hard drive space in the computer using a free software called "windirtstat". Now enter the following address in the web browser "windirtstat.info" and scroll down the page until you get the downloading and installing section. Click on the link "windirtstat1.1.2Setup(Ansi&Unicode)" which will be right after the "for all flavors of windows" this will direct you to "SOURCEFORGE.NET" download creations. This will ask you to save t...

Keep your house safe! Learn how to replace door locks in this free home security video from our professional handyman.

The newest feature for Pixel smartphones puts a home theater in your pocket. Spatial Audio outputs sound that appears to come from in front of and behind you, adding a new level of immersion to your streaming video and music apps.

If you're using or need to use Zoom, the popular video teleconferencing service, you've almost certainly heard about "Zoombombing" by now. While Zoom has been adding security measures to address the problem, there are other things you can do to prevent or stop Zoombombers in their tracks so that your video meetings and chats go undisturbed and uninterrupted.

Compromised uTorrent clients can be abused to download a malicious torrent file. The malicious file is designed to embed a persistent backdoor and execute when Windows 10 reboots, granting the attacker remote access to the operating system at will.

Samsung decided to jump into the foldable category early, announcing the Galaxy Fold in February 2019. After a major hiccup, Samsung released the phone four months later to praise. But Samsung's not finished with foldables, as the new Galaxy Z Flip is just on the horizon.

Android 10 is officially out, but a lot of phones didn't get it in 2019, and others may not get it at all. With this page, you'll at least know when or if.