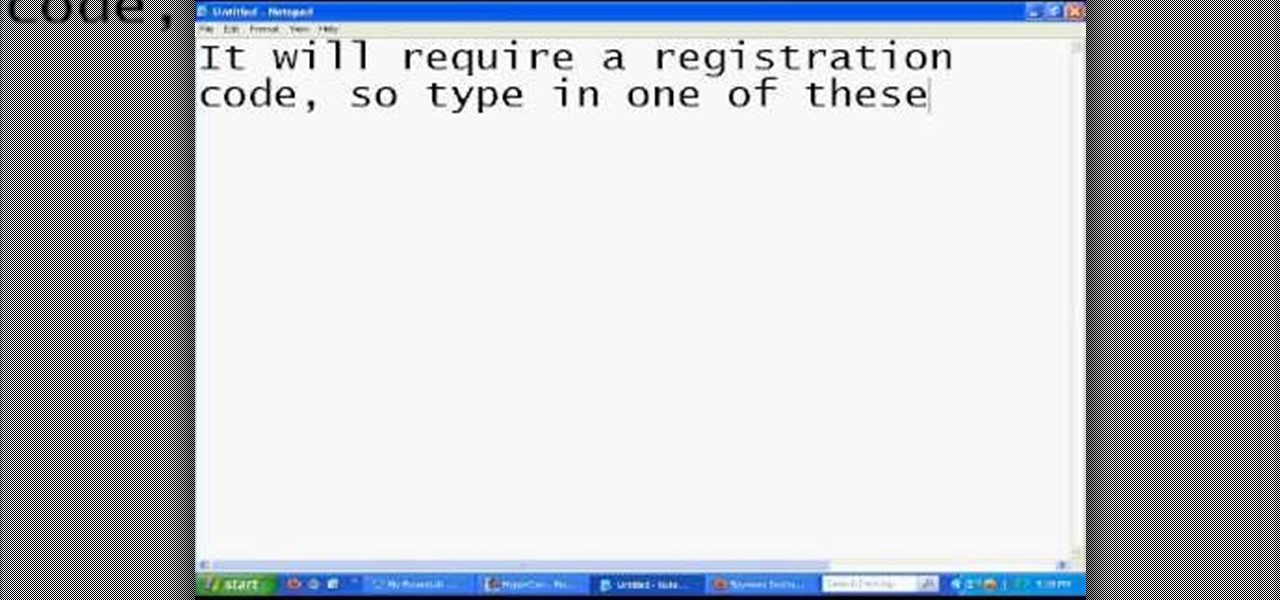
This video shows you how to easily remove the Security Tool virus. The first thing you have to do is restart you computer. Once restarted, immediately hold down CTRL+ALT+DEL. In the Task Manager you should see: Security Tool. Quickly end it now. The virus is temporarily disabled. Now go to: Download and install Spyware Doctor. Scan your computer and click Fix All. It will ask you for an account...
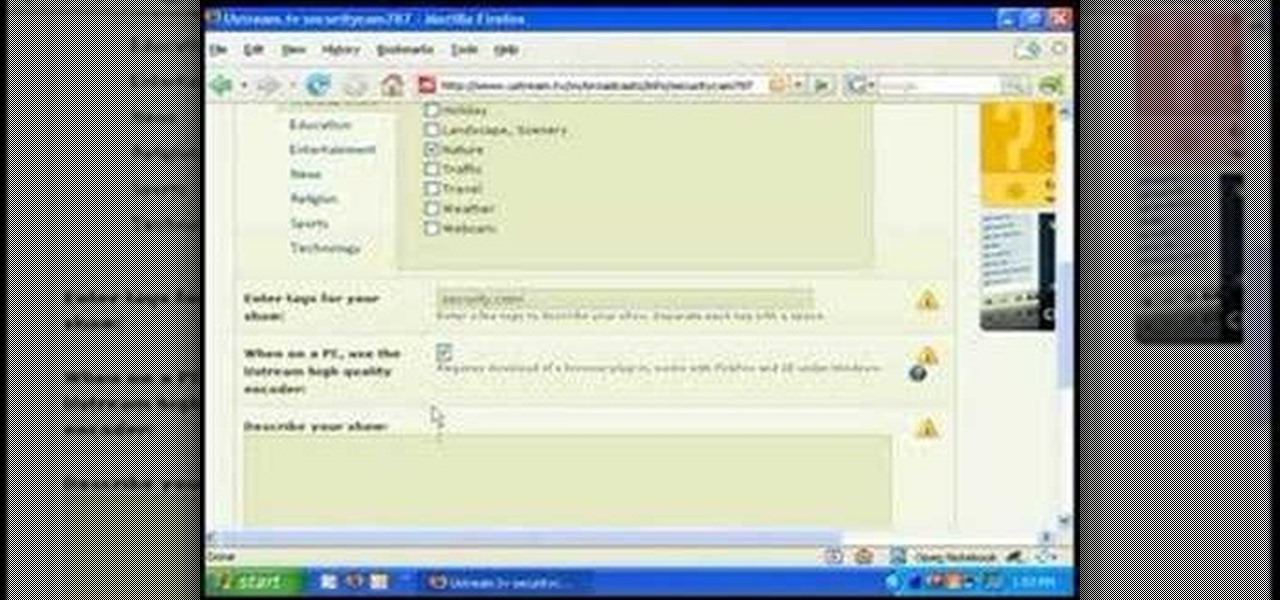
You have a webcam, right? Nowadays, who doesn't? But just because you all have webcams doesn't mean you're using them the same way. And a great way to take full advantage of your peripheral or built-in webcam is by turning it into a security camera. This video will show you how to turn it into a security cam by accessing the video feed remotely over the internet. And it's a really simple solution—you just need to sign up for a USTREAM account, which allows you to stream webcam footage live!
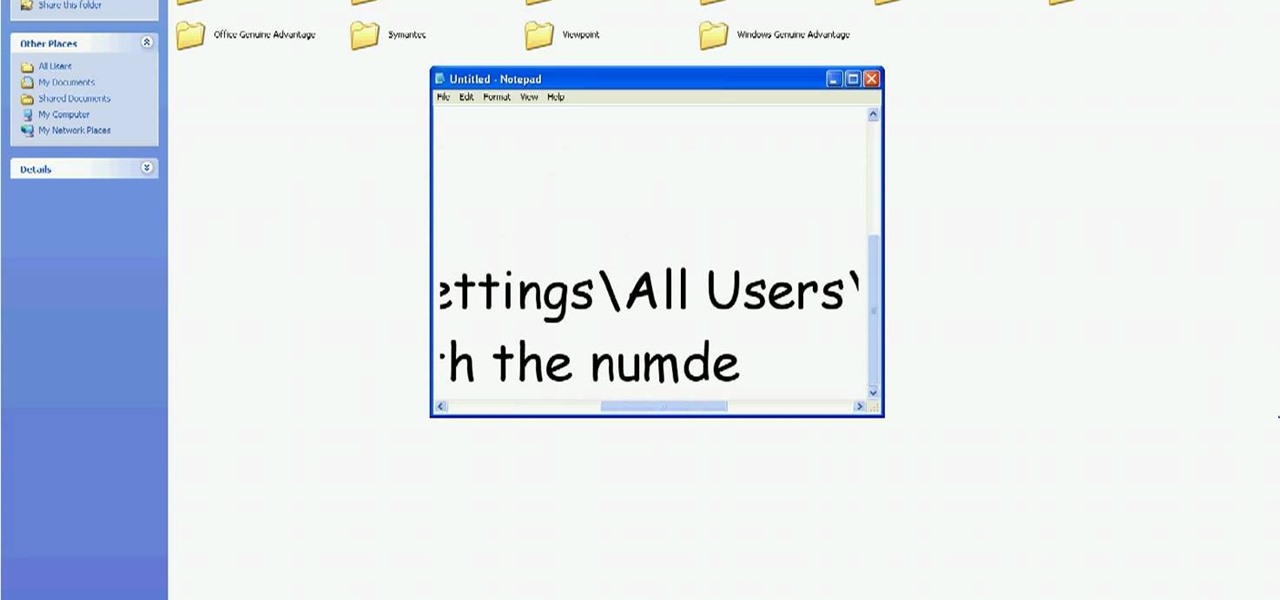
In this tutorial, we learn how to delete Security Tool from your computer. First, you will need to restart your computer. After this, go to your documents on your computer. Then, type in "Type C:/Documents and Settings\All Users\Application Data". After this, delete the file with all of the numbers. If you now get an error that says "access denied" then restart your computer again. Once the starting screen appears, press "F8", then select safe mode and redo the steps that you just took. After...

In this clip, you'll learn how to get started using SkyRecon's Stormshield. It's easy! So easy, in fact, that this helpful how-to can present a complete overview of the app in just over four minutes. For more information, including detailed, step-by-step instructions, take a look.

In this clip, you'll learn how to use the VSN plug-in to encrypt email in Microsoft Outlook. It's easy! So easy, in fact, that this helpful how-to can present a complete overview of the app in just over five minutes. For more information, including detailed, step-by-step instructions, take a look.
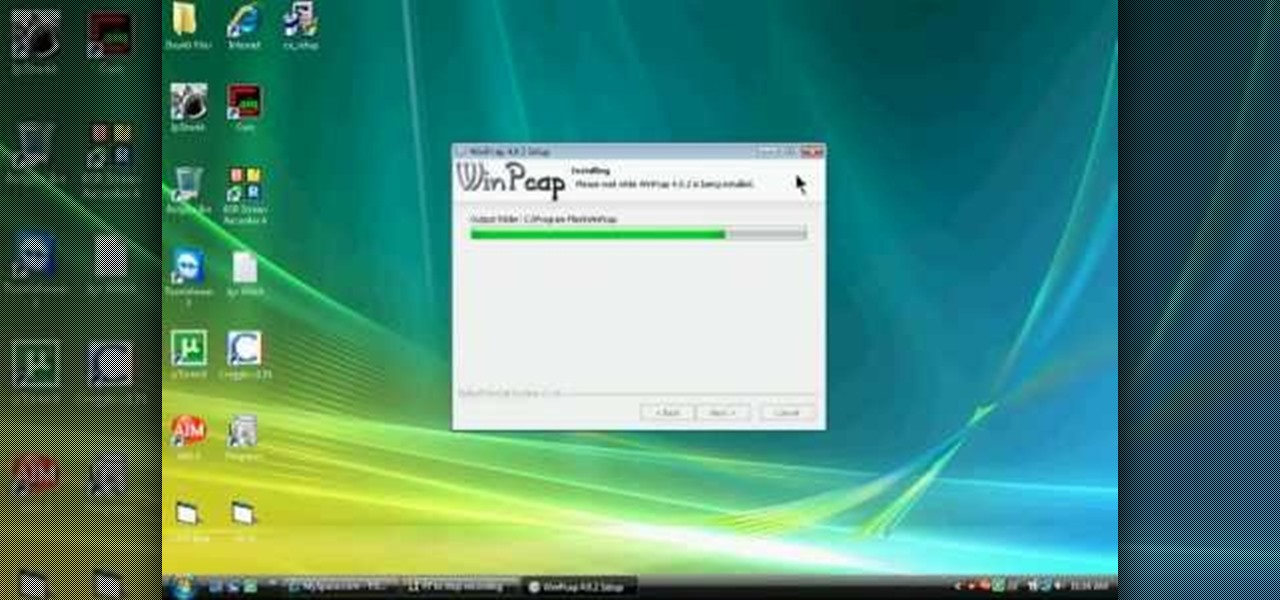
First you have to install program, called 'Cain and Abel'. Then, you will be automatically asked to install 'Win Pcap' and you should do that. After installation you have to click on 'Cain and Abel' program icon with right mouse button and start it as administrator. Then push blue plus sign to scan Mac addresses. After scanning go to the bottom of program window and press APR tab. Then push blue plus icon again. When table appears push first option in first square and first option in second a...

Hi everyone. I'm relatively new here and I have learned a great deal from many of you already and would like to try and give a little something in return.

Hi fellows! I finally decided to join this forum, which I find very interesting and has some great contributions into the tech and security space, appreciate it!

Four key Syrian military officials including Defense Minister Gen. Daoud Rajha and President Bashar al-Assad’s brother-in-law Assef Shawkat, who served as his deputy, were killed at a top-level meeting in central Damascus. Syria's top security ministers slain in Damascus bombing — RT.

Apple just released iOS 13.5.1, the latest update for iPhone, on Monday, June 1. The update comes 12 days after iOS 13.5, which introduced COVID-19 exposure notifications, a Group FaceTime update, and Face ID improvements when wearing a mask.

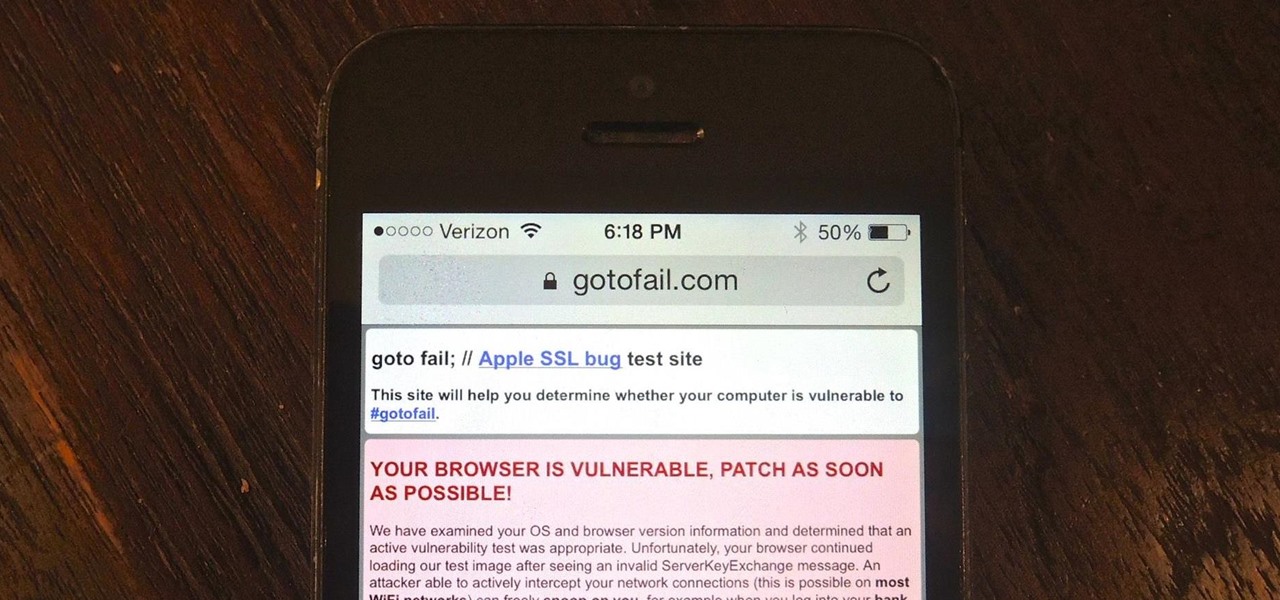
Apple released iOS 7.0.6 last week, an update to fix a serious security flaw that allowed hackers to not only capture sensitive user information such as bank statements and passwords, but also modify that same data on secure HTTPS sessions.
While following a tutorial on python recon tools, I found a new way to access the command prompt on a school network. While there are other ways of bypassing security, it's nice to learn use Python's OS library.
Fascinating, although admittedly highbrow, discussion on the history of cryptography from the BBC. If you are outside of the UK and don't know how to access BBC content you need to spend a bit more time browsing the Null-Byte forums ;-) http://www.bbc.co.uk/programmes/b06mtms8

Hey Everyone! Welcome to my post. We have seen a numerous GUI Tool in kali linux. Armitage, wireshark, Burpsuite etc,. Lets see an another GUI tool.

Papercraft guns are the new origami. The new origami for boys, that is. WonderHowto and YouTube are chock full of paper gun tutorials. Many models are simple, but some are impressively realistic, not to mention functional. My personal favorite (unfortunately no tutorial) is the homemade Desert Eagle .50 cal by YouTube user Changmobile.

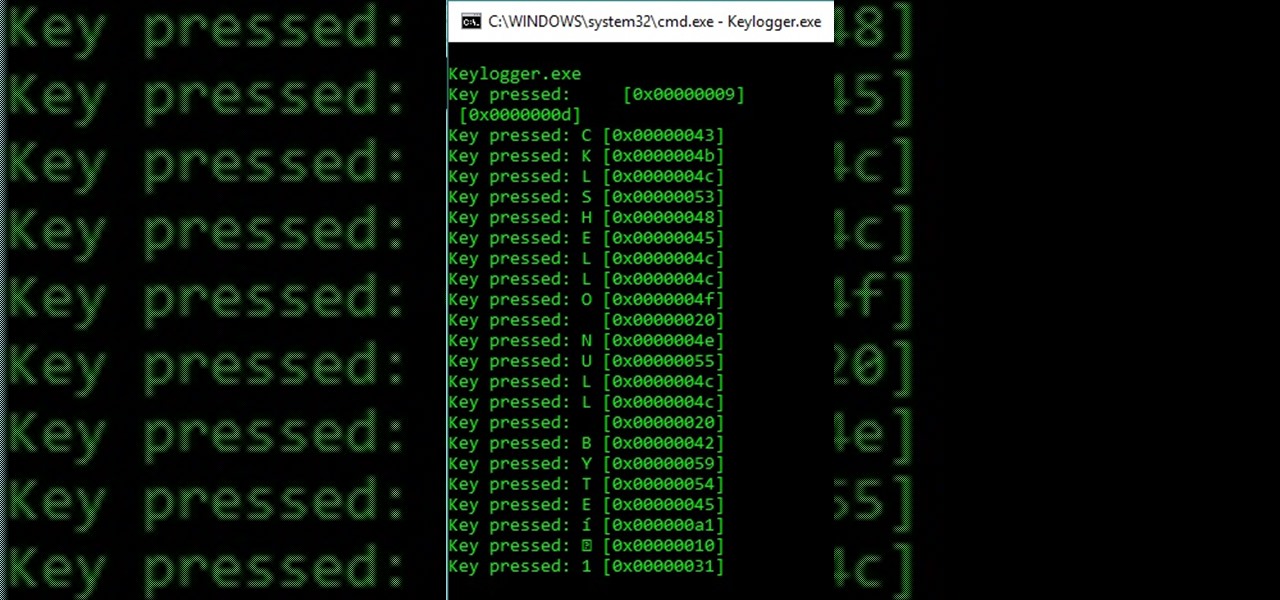
Yo yo yo, what's goin' on my devilish fiends? Have you come here to learn how to make a keylogger for malicious intent? You sly fox! But in all seriousness, this article will cover quite a simple method for creating the most basic of Windows keyloggers. You're in for a surprise! Let's dive right in!

Okay guys and gals, this will be a quick tutorial on using the incredibly helpful man pages. What Are Man Pages?

The HP 2710p business notebook has a number of innovative security tools to make sure your data stays where you want it.

In this tutorial, learn about applying and removing security options in Acrobat 9. For more Adobe software tutorials from Layers Magazine, search Layers Magazine on WonderHowTo. WonderHowTo indexes all Layers Magazine tutorials for Illustrator, InDesign, Photoshop, Acrobat, After Effects, Premiere Pro, Dreamweaver and Flash.

The Ironkey is a high security thumb drive designed to provide strong AES encryption, tamper resistance and other security services. Some of the topics covered will include: How is the drive mounted without admin privileges in Windows? How is it mounted in Linux? How does the "Self Destruct" feature work? What is Secure Sessions? How is the Ironkey better than just using Truecrypt? For answers to these questions, take a look. Use the Ironkey High Security Flash Drive.

This hour-long hacking tutorial looks at the Nmap security scanner. In particular, this Nmap tutorial looks at port scanning concepts, TCP three way handshake, stealth scans, idle scans, bounce scans, version detection, OS detection, NSE/LUA scripting and firewall logs. To get started using Nmap, watch this video tutorial. Use the Nmap security tool.

Installing a deadbolt is a relatively quick and simple do-it-yourself project. You can make your home much safer – and less attractive to thieves --- with a little effort and a few simple tools.

People sometimes ask me about the IT industry here in the states. These folks are usually either trying to get into a certain field, or looking to switch or move into another one. Right now, you may currently be a Computer Science major that will be graduating shortly and are interested in the current state of IT security.

Waiting in line at the airport can be a drag, but here are a few tips for catching your flight hassle-free. See how to get through airport security in a snap from this how-to video. Airport Security Tips - Fly Through Airport Security Video.

Have an HTC smartphone? Chances are that some of your stored personal data has been hijacked by malicious apps on your device. Android apps that have permission to access the Internet, which is pretty much every ad-supported app out there, can snag valuable information such as email addresses, location history, phone logs, text messages, and more.
The department of Homeland Security released a list of 'words and phrases' it uses to search social media for terrorism, and whatever else they decide they are looking for that day. Read some of these. A few are obvious "bomb, nuke" and some "target, event" are just down right vague. More reasons to watch what you do on the Internet. You are not the only one watching!

Anonymity is something that doesn't exist today. Everything you do in the world is tracked, from the purchases you make to surfing the internet—even taking pictures on your iPhone. Everything you have ever said and done on the internet is still there—somewhere. This is called caching. For example, when a site is down, you can view its cached page on Google.

The end of Daylight Saving Time means two things: a little less light and, as a result, a little less security. This CCTV lamp will give you more of both. And in the nick of time! We fall back to Standard Time at 2 AM on Sunday, November 7th. Better get building!

Backtrack 5 is a Security Essentials Backtrack is a suite of tools to help with Penetration of any Network, Unix, Linux, or Microsoft Based. Backtrack 5 is good for WEP & WPA hacking and penetration testing.

To decipher my password, you need to know my mother's maiden name, where I was born, and what I had for breakfast on August 12th, 1996 (trick question, I was in a food coma).

Cool world. Check it out and post your ideas to the forum.

I've seen numerous tutorials on how to create a "strong" password. This makes me laugh. These titles imply "one" password, which is wrong in and of itself. A person should have many passwords, all different, and all extremely long. People may ask how they're supposed to remember lengthy passwords and why their current password isn't good enough. Well, I'm going to show you.

When you're out and about in the dangerous world of Wi-Fi, it's hard for the average computer user to stay protected, or even know what being protected entails. Little do most people know, Windows 7 has a built-in security that few people take advantage of: a VPN (Virtual Private Network) server and client.

From Boing Boing, a highly amusing photo gallery of illegal goods seized by airport customs officials in Australia. Some are fairly typical, but others really make you wonder... Yes, I'm most definitely talking about the tropical fish skirt lady.

As many of you know Windows is not the most secure Operating System in the world, but then again no OS is really secure if the user doesn't know how to protect themselves. Later I will show you how to lower the risk even more on your (the user's) end.

Middle-aged man goes through the tools and process to install a security chain to a door. Tools include a door chain, screwgun, hammer, chisel and other listed tools. Step-by-step video explains thoroughly how to accomplish the chain installation. Mount a security chain to a door.

If you're an avid programmer or developer, your time is likely spent creating apps and perhaps the occasional website. And while these go-to coding endeavors are exciting and occasionally lucrative, more and more coding pros are turning to careers in cybersecurity and ethical hacking — thanks to the high pay, flexibility, and unparalleled opportunities.

Ethical hacking is a useful skill that can make you stand out in the field of cybersecurity. Whether you're just entering the field or are already established and are looking to stay current, learning the fundamentals of the white hat is an essential skill for your professional development.

This is Part II in the Lockdown: The InfoSecurity Guide To Securing Your Computer series. Before beginning, check out Part I. This article will cover using alternate software to increase your security and will provide you with some information about websites and programs that test a computer's security. It will also guide you to software you can install or follow so you know what programs need to be updated on the computer. Lastly, I will talk about some features that should be disabled when ...

This is a two-part series to locking down the computer to provide maximum protection. Even though this guide will sound intrusive, we are talking about reality here. Extreme measures must be taken to protect our computers, especially when we have confidential documentation or do internet banking, which many people do. We all have to use electronic devices at some stage, whether it be for business or personal use.