Samsung just began rolling out the Oreo Beta 2 to registered users of the Galaxy S8 and S8+. The update's changelog promises the inclusion of the October 2017 security patch. Unfortunately, after downloading the update, we've noticed this is not the case. Omission of the more recent security patch is notable in that it leaves devices vulnerable to several known exploits, such as KRACK.

Google released its "Android Security: 2016 Year in Review" report last month, and to no one's surprise, included its own flagship phones. However, one surprise on the list was the BlackBerry PRIV, which Google named one of the best Android devices for privacy.

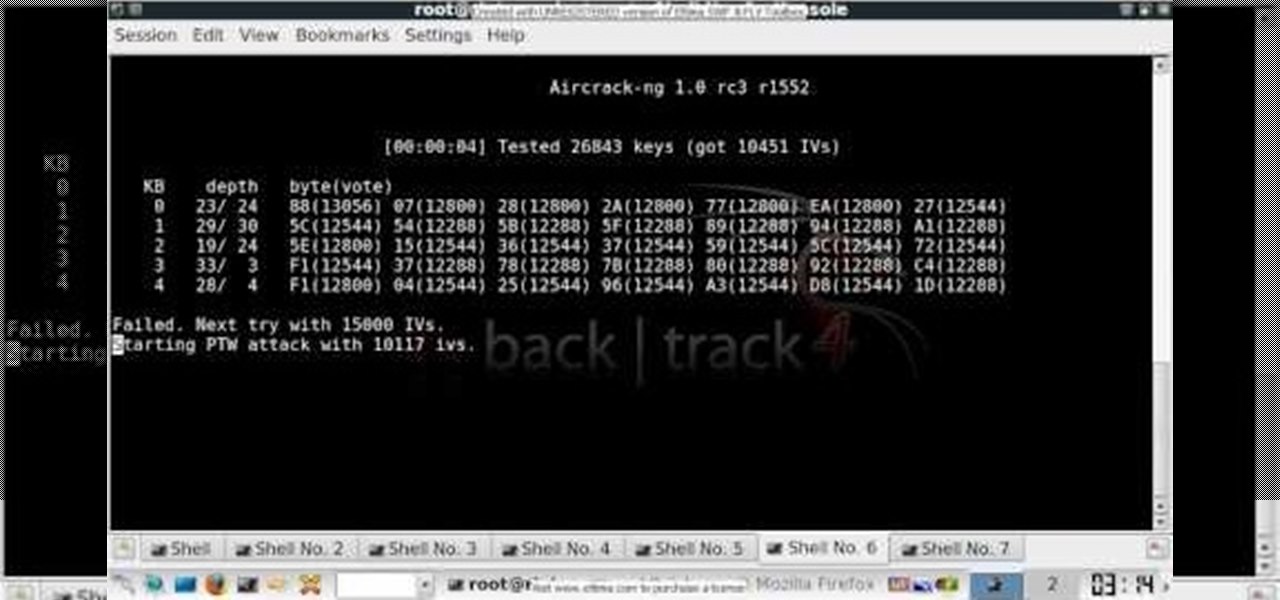
In this clip, you'll learn how to use the BackTrack Linux distro and the Aircrack-ng WiFi security app to hack a WEP network. The process is simple. For more information, including step-by-step instructions, and to get started testing the security of your own WiFi networks, watch this hacker's how-to.

Learn how to use the Backtrack Linux distro and the Aircrack-ng WiFi security app to crack a WEP key. The process is simple. For more information, including step-by-step instructions, and to get started testing the security of your own WiFi networks, watch this hacker's how-to.
In this clip, you'll learn how to use the Backtrack Linux distro and the Aircrack-ng WiFi security app to crack a 64-bit WEP key. The process is simple. For more information, including step-by-step instructions, and to get started testing the security of your own WiFi networks, watch this hacker's how-to.

In this clip, you'll learn how to use the Backtrack 3 Linux distro and Aircrack-ng WiFi security app to crack the password to a WEP-protected wireless network. The process is simple. For more information, including step-by-step instructions, and to get started testing the security of your own WiFi networks, watch this hacker's how-to.

In this clip, you'll learn how to use the Backtrack Linux distro and the Aircrack-ng WiFi security app to crack a WEP key. The process is simple. For more information, including step-by-step instructions, and to get started testing the security of your own WiFi networks, watch this hacker's how-to.

Starting with the Priv, BlackBerry's become an Android manufacturer. This move gives BlackBerry's phones access to Google's sizable app store, but it also presents several hurdles to keeping the security brand they've built intact.

The latest film addition in the American-produced Millennium series, The Girl in the Spider's Web, was just released on Blu-ray a few days ago. As you could expect, the movie has many hacking scenes throughout, just like the previous English and Swedish language movies centered around hacker Lisbeth Salander. Of course, with the quick pace of some scenes, the hacks can be hard to follow.

When it comes to cybersecurity, one layer isn't enough. A complex password (or one created with a password manager) does a good job of protecting your data, but it can still be cracked. Two-factor authentication strengthens this by adding a second layer of security, giving you even more protection against online threats.

In previous posts here, I have pointed out that hackers are in high demand around the world and in nearly every industry. Every military and espionage unit of every country is trying to hire high-quality, experienced hackers as fast as they can to hack their adversaries' computer systems in order to gain a strategic advantage and to spy.

Keep your possessions safe from thieves with these tips. You Will Need

Burglary is common, but is also quite preventable with these tactics. You Will Need

The last iOS software update was a modest one, but iOS 17.4 has a lot more for your iPhone, including changes to emoji, Podcasts, security, Safari, widgets, Apple Cash, CarPlay, and more.

Because of the way Google Play works, Android has a "bad app" problem. Google allows any developer to upload an app to the Play Store, regardless of if it works, how it looks, or whether or not it can harm users. Malware scanning happens primarily after apps are uploaded, and though Google has recently taken steps to safeguard users with its Play Protect program, you don't have to depend on them.

Most oil cooler kits cost $250 or more, but the guys at Poor Man Mods show you how to make your own oil cooler for only $60! Oil coolers are great security for longer lasting and better performing engines, especially high-performance engines and in warmer climates.

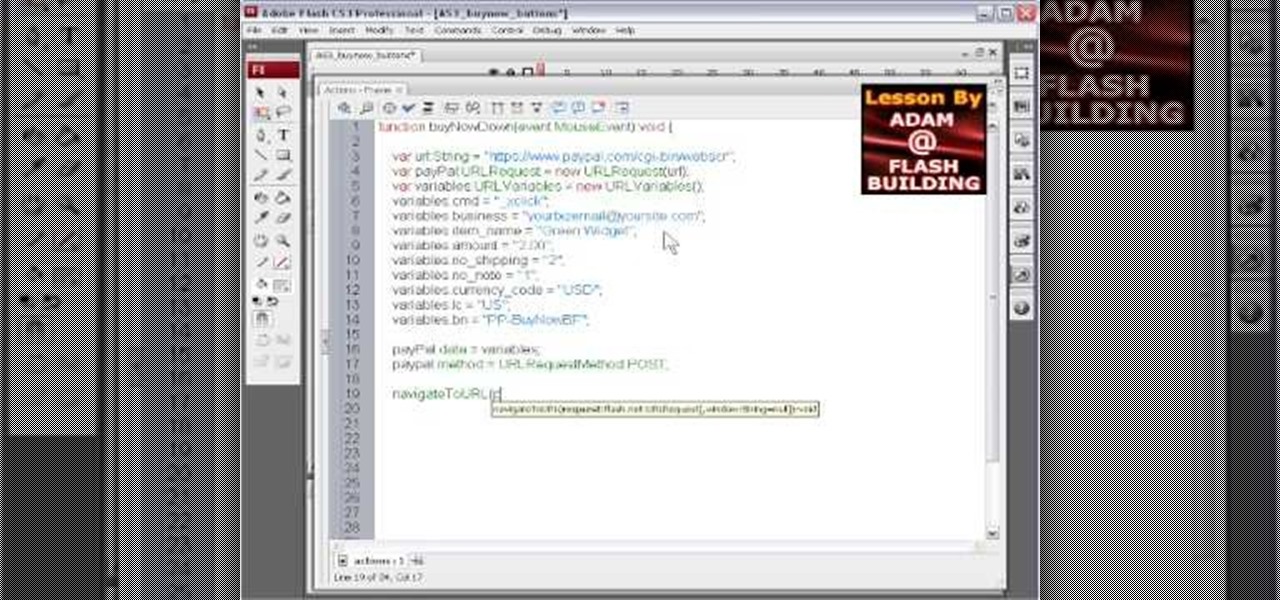
Add an extra level of security to your website by creating your own dynamic 'Buy It Now' button for PayPal-using visitors to your website. Coding this button is very easy, and you can even animate it to draw more attention to your webstore.

Deadbolts are a security lock which are usually put on exterior doors. Many saftey experts recommend increasing the strength of your home deadbolt lock. This quick tutorial teaches you how to make your deadbolt extra secure and increase the safety of your house.

Picking a secure password is not only important for protecting your privacy, it's also very easy. Provided, that is, that you know how to go about it. This free video lesson from CNET TV will walk you through the process. For more information, and to get started creating and using high-security passwords yourself, watch this video tutorial.

Need to install a pre-hung door? Lowe's has your back. A quality front door makes a positive first impression on guests... not to mention, a weathered and worn door can compromise your family's safety and security. In this video, learn how to install a new pre-hung exterior door with the following instructions from Lowe's.

iPod and iPhone home automation remote control using Girder is only an install away. Run the lights, heat, security system among other things in your space age home for the 21st century. Make your home a modern marvel with this app for iPhone.

In this installment from the Unorthodox Hacking series of Internet security tutorials, you'll learn how to get a shell on a Microsoft SQL Server (or SQL Server Express.) See how easy it is to obtain a shell in a Microsoft SQL database with this how-to.

In this installment from the Unorthodox Hacking series of computer security tutorials, you'll learn a number of methods for hacking Windows shares as well as means of mitigating those hacks. For detailed instructions on Windows shares, and what you can do with them, watch this helpful video guide.

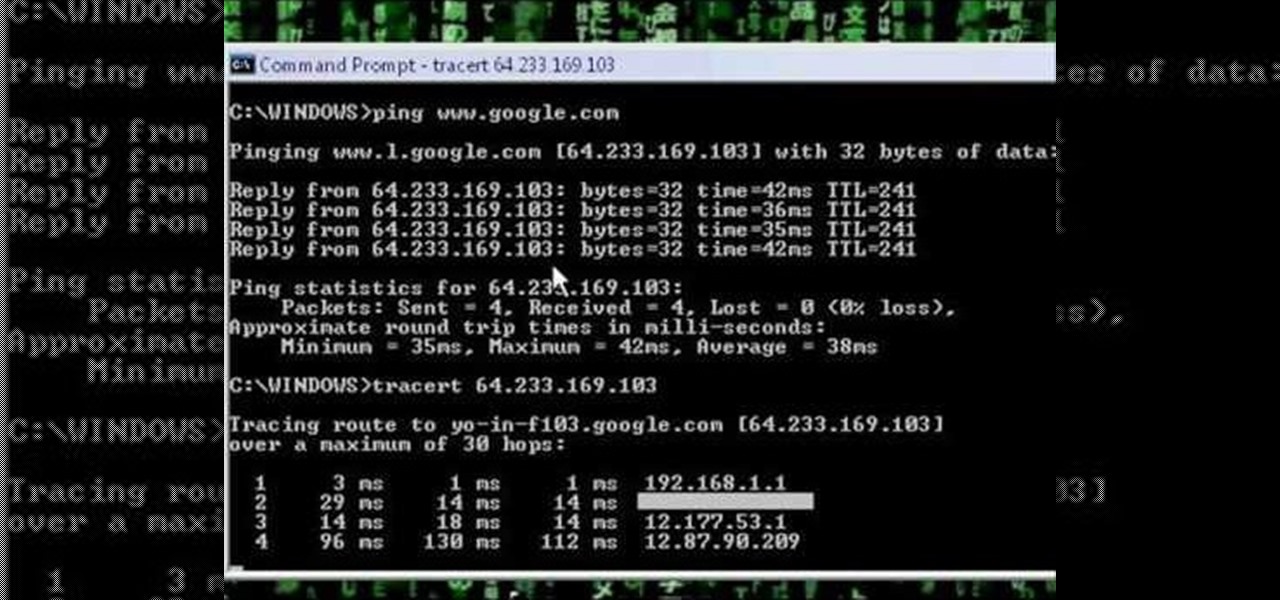
A network security tutorial on using ping and tracert to show th IP of a webserver, your own IP, your ISP's IP, who they connect to, and what computers your request goes through before reaching a destination.

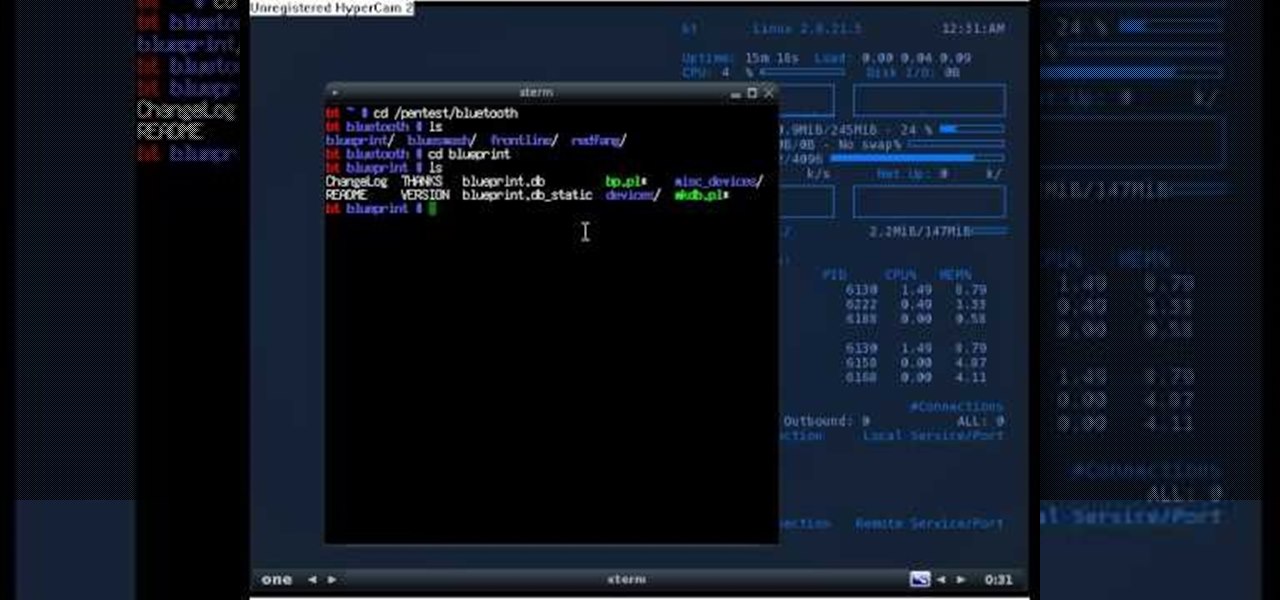
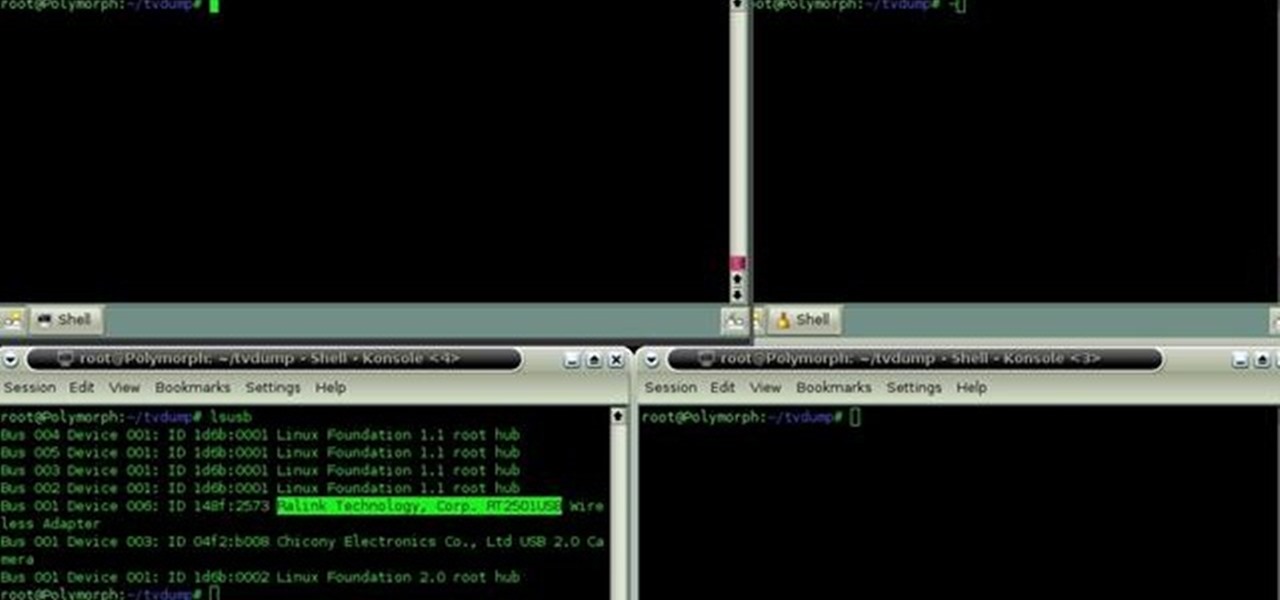
If you're new to the Bluetooth hacking world, here's a little background on using Linux BackTrack to hack a Bluetooh device: Linux Backtrack is a Live DVD device that offers security tools - like password crackers - that allow you penetrate networks.

Security is tighter than ever in U.S. airports. From the recent instigation of the hotly debated full-body scans and pat-downs to the TSA limiting every ounce of body lotion you bring, it's hard to make it through the security gates without some major airport hate.

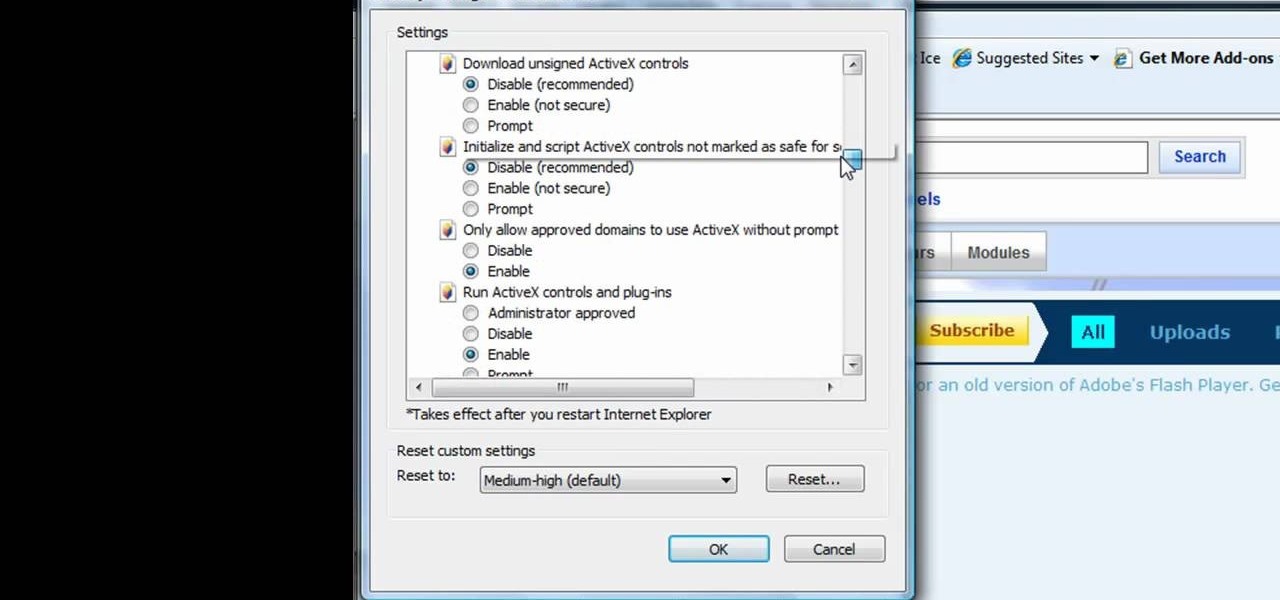
This tutorial shows us how to enable JavaScript in Internet Explorer. First, go to the top right of IE and click "tools". Then, click "internet options" and then go to the security tab. From here, select your security level that you want by clicking "custom level". Scroll down to the bottom and find the tab that says "active scripting" and make sure it's enabled. Click on "ok", then refresh the page that you are on. Now you should be able to watch videos and use anything that uses JavaScript ...

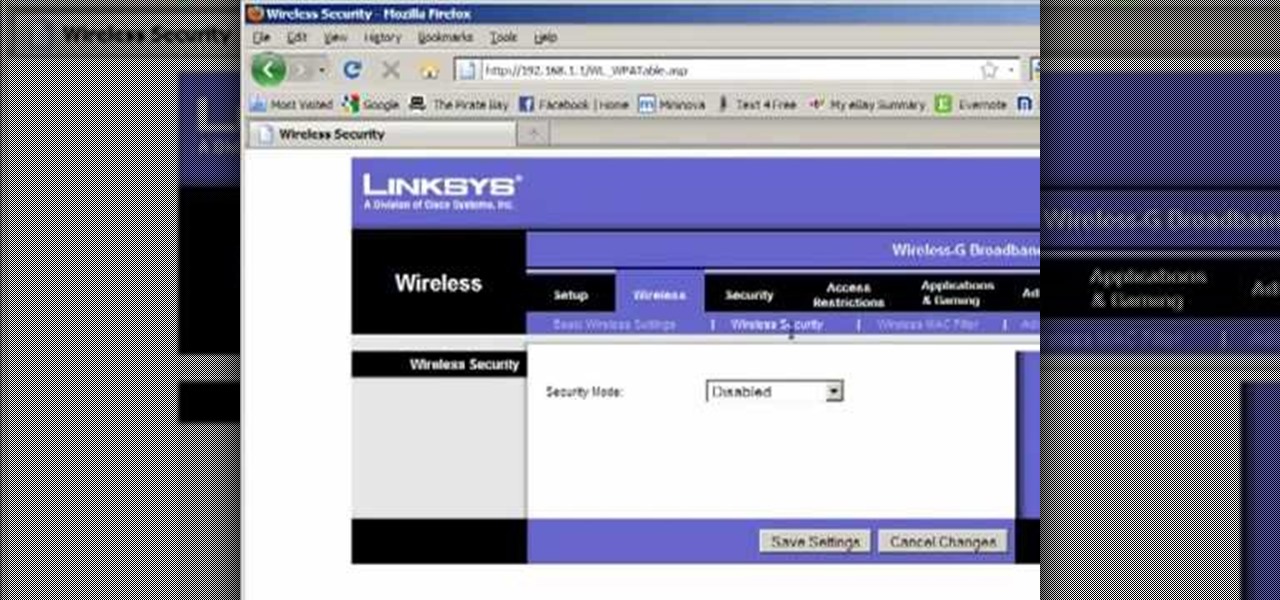
Most of the home wireless networks are not set up by professionals and hence they might lack in security features. People just set up the wireless networks by connecting the devices and powering them up and never care to apply security settings to the network. This may result in your wireless network being compromised by unwanted external entities. How ever you can do a web based configuration settings and secure your wireless network by password protecting it. This settings differ from the m...

Llewyn demonstrates how to configure your router for Wifi. Access the router by opening up your internet browser and typing in your router's IP address. That will bring up the router configuration page. Now, click on the wireless tab. You can set the wireless network mode to accommodate your computers. As a precaution, set the mode to mixed for greater flexibility. Set your wireless SSD broadcast to enable which will enable your wireless card to actually see the webpage and the internet. You ...

This video shows the method of getting past blocked sites and opening them using proxy servers. The method shown is useful when the sites are blocked using another site. In this case it is 'www.lightspeedsystems.com'. It can be done using proxy servers. In the case shown it is 'treesniff.com'. The URL is typed and we choose the option of 'Continue to this website'. Press 'No' for the security information. After this the page of the proxy server is displayed. Type the name of the website you w...

Hak5 isn't your ordinary tech show. It's hacking in the old-school sense, covering everything from network security, open source and forensics, to DIY modding and the homebrew scene. Damn the warranties, it's time to Trust your Technolust. In this episode, see how to program a USB development board for cheap.

Hak5 isn't your ordinary tech show. It's hacking in the old-school sense, covering everything from network security, open source and forensics, to DIY modding and the homebrew scene. Damn the warranties, it's time to Trust your Technolust. In this episode, see how to secure remote desktop.

Hak5 isn't your ordinary tech show. It's hacking in the old-school sense, covering everything from network security, open source and forensics, to DIY modding and the homebrew scene. Damn the warranties, it's time to Trust your Technolust. In this episode, see how to defend your hacker space with a USB missile launcher.

In this video tutorial, you'll find a step-by-step guide to how a n00b hacker (like you?) can get usernames and passwords easily through one of the security flaws of the Ethernet ADSL router. More than half of Internet users never change their default password which makes this "hack" easy. Take your time to read the text on the slide. For more, and to get started testing the security of your own Ethernet ADSL router, watch this hacking how-to.

You should feel relatively safe to watch and post videos on TikTok, but like with any online service, you're always at the mercy of hackers.

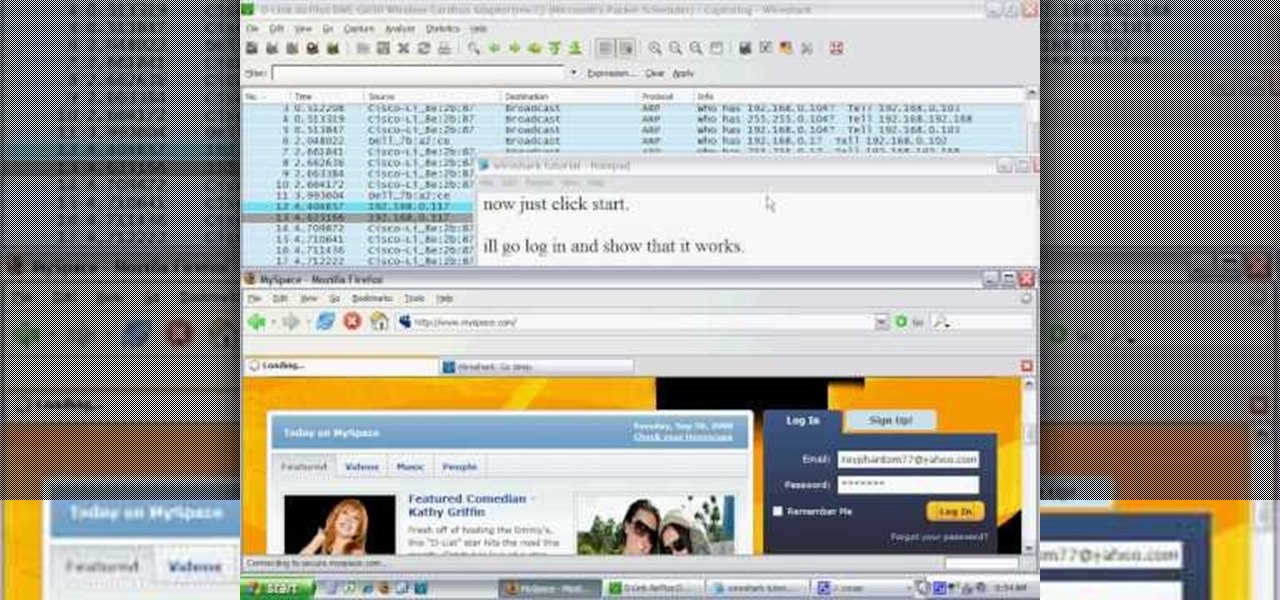
If you're trying to hack someone's wifi, a useful bit of software you may want to try is called Wireshark. Wireshark is a wifi packet sniffer, which is an essential step in actually breaking into someone's wireless system. Of course, this is illegal, so make sure you're only doing it to test a network's security, or for your own educational purposes. Check out the video, follow the steps and see how secure network is. Hack, hack, hack!

If you've recently upgraded you doorknob to an elegant Schlage Plymouth Handleset, then it's time to match your front entry locks and install a new electronic high-security Schlage Plymouth Keyless Entry Deadbolt. This keypad is great if you never want to lock your bottom handleset (or doorknob). Watch this step-by-step installation video to see how it's done! You'll need a phillips head screwdriver or electric drill. To see how to install the matching handleset, click here.

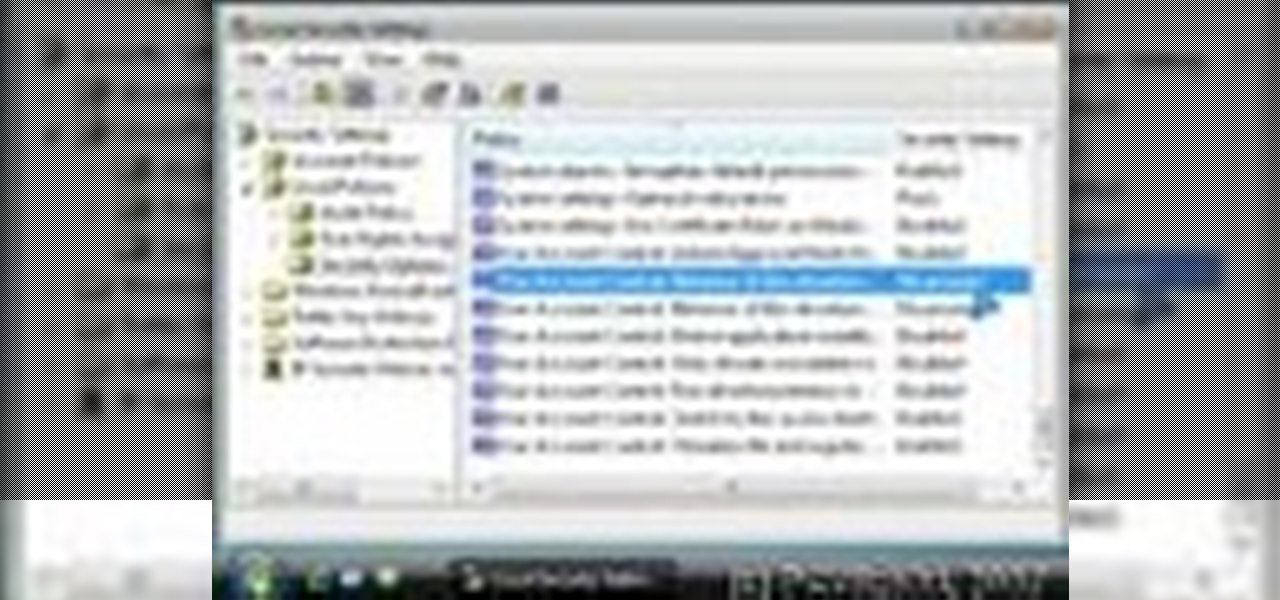
Why is Windows always asking you for permission before you do anything? Since when does Windows control your computer, and not you? Those user account control popups can be so frustrating, especially when it comes to simple tasks.

In this video, we learn how to protect your privacy while using Twitter. Your personal information can get stolen in an instant with the internet. With Twitter, when you are doing updates showing where you are and what you are doing, someone could try to find you and potentially create harm to you. To help you avoid situations like this, you need to go to the security settings of your Twitter account. When you go here, you can change the account so that it only allows people you want to follo...

In this tutorial, we learn how to use the notepad to get by school internet blocks. First, open up Notepad on your computer, then type in "<html>" "<body>", "iframe src=http://www.youtube.com", then "height=100%", then "width =100%". To finishe, type in "<iframe>>/body><html>". Save this as hack.html as all files. After this, open up your browser, then you should be able to go to the website that you wanted to go to! This is a great way to get around the security settings that your school has...