
How To: Get Natural, Sparkling White Teeth on the Cheap
You Want White Teeth Without Expensive Over-The-Counter Products? Here's An Inexpensive, Effective Solution.


You Want White Teeth Without Expensive Over-The-Counter Products? Here's An Inexpensive, Effective Solution.

Collision Repair Related Careers When you think of a career in collision repair you probably think of a body repair or paint technician. However, there are a lot of related careers that collision repair can lead to. For Example, you can work in auto parts stores, dealerships, insurance companies, paint representatives, trainers, etc. In this article we are going to examine a career as an auto estimator.

When you are at the beach, pick a victim or friend that is lying down on a towel on the sand. When they get up to use the restroom or for a drink, remove the towel and dig a hole where the towel sits.


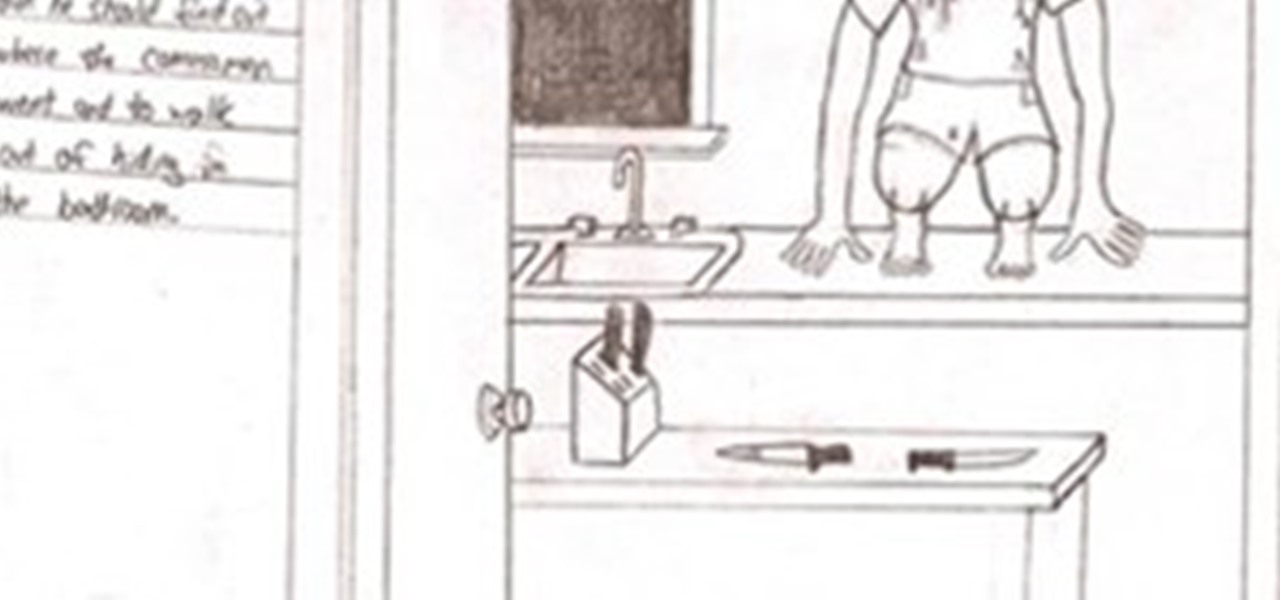
In the first part we differentiated the two types of control, mental and physical. In part 2 we will dig deeper into Physical crowd control and analyze examples that are present today.

You've probably seen those deep-web images floating around on the Internet. Usually, it goes something like this: There is a towering iceberg and the deeper the underwater portion extends, the more “hidden” and “exotic” the content is described to be. Sometimes these images are accurate to a point, but most are just making things up.

Now that you have your two-letter words down and have practiced your skills, it's time to move on to another important part of Scrabble gameplay—the opening move. There's a well known adage that states, “The player going first will win 54% of the time—all other things being equal."

Now that you can invite anyone you want to Google+, the floodgates are open. If you've been bummed out about not being able to share the joys of Google+ with your friends and acquaintances, make use of that handy envelope icon the right side of your stream page. Just enter the email addresses of the people you want to invite, and hit the "Invite" button.

Do you know how wonderful toothpaste is? Here's the scoop. If you've hung pictures or other thing on the wall that required a molly or anchor bolt, and you have to move them and you have holes exposed in your wall. Well "FEAR NOT", toothpaste to the rescue. You will need household items like - toilet paper, or paper towel, or paper napkin, or Kleenex tissue, a utility knife, hammer putty knife, sponge, primer/sealer, paint of your choice and of course the toothpaste.

Large, sweaty men are usually the first thing that comes to mind when you hear the word football, but for this video, we're not talking about the guys on the playing field, we're talking about the guys in the fishing boat, the kind of guys who like to use a "football jig".

Are you tired of wasting diamonds and iron on creating hoes? Are you looking for a fun way to farm melons? Or do you simply want to show off to your friends? This tutorial will go over how to make a jaw-dropping semiautomatic melon farm. Not only will you be the talk of the server, but you'll have infinite melons for life!

Welcome to Minecraft World! Check out our tutorials, post to the community corkboard, and come play on our free server!

Etching your own circuit boards is tons of fun, but etching requires strong chemicals to dissolve the copper plating on blank circuit boards. The normal ferric chloride solution works well, but can be expensive and leaves permanent stains. Luckily, we can whip up our own etchant at home with everyday chemicals! Better yet, our new etchant will turn an eerie green color rather than the dull brown of ferric chloride.

The community here on Null Byte has always been great and helpful in sharing their know-how, even before I took up admin duties in this World. I jumped at the chance of leading Null Byte because I enjoy teaching and informing people on all of the important need-to-know things out there, but more so than that—there is a deeper reason.

Injection is an attack vector that involves breaking out of a data context and switching into a programming context through the use of special characters. These characters are significant to the interpreter being used, but not needed for the general user input being asked for.

Giveaway Tuesdays has officially ended! But don't sweat it, WonderHowTo has another World that's taken its place. Every Tuesday, Phone Snap! invites you to show off your cell phone photography skills.

I've been unreasonably excited about Dungeon Defenders (NOT DUNGEON DEFENDER!) for almost a year. Playing it at PAX did nothing to damper that enthusiasm. I had a chance this week to speak with co-founder/development director Jeremy Stieglitz and marketing diretor Philip Asher from Gainesville, Florida based developer Trendy Entertainment to find out a little more about the game, and how it came together.

The manual that's included with the Canon EOS 5D Mark II is a great starting point for learning the camera, but it's definitely not the only place you should be getting your information from if you intend to master your 5D Mark II. If you don't have the manual, you can download a copy of it here from Canon's website. It's great for learning the basics of the camera, but sometimes it can be vague and hard to follow. In order to capture the full potential of the 5D Mark II, you need to go a lit...

Last week, I demonstrated how to go a little deeper into your Google+ profiles, photos, and introduced cross-posting. This week, I'm highlighting a bunch of different unofficial resources that have sprung up that will help improve your Google+ experience, and give you the latest updates on Google+ Photos.

After the media outcry of Google Buzz's privacy issues, Google has set its goals on making the privacy parameters of Google+ simple to learn and as explicitly manageable as possible. No small feat.

There’s no point to playing all of the different tower defense games available today. Most adhere to the original formula, so playing 2 or 3 really good ones (like those mentioned in my previous post) would be more efficient.
Synopsis: Tell one guy that a girl that one of the other guys knows just had some sketchy demonic encounter/satanic experience at some Wicca gathering she went to last night while she was trying to get answers from the past. Then say she’s incredibly creeped out right now and is home alone tonight so they are going to seize the opportunity(while she’s still scared) and have him dress up as Satan himself and go to her house late at night and “appear” to her in her bedroom. (Don’t be overly des...

A game labeled as 'educational' usually spells its death among hardcore gamers. The educational game genre is mostly intended for children, and games that appeal to children often lack the sort of widespread appeal that makes them commercially successful.

Wireless networks. Nowadays, everyone uses 'em, but most don't secure 'em. On average, I can drive up and down any block in my city and find at least one or two open or semi-open networks on any given day. With some changed MAC addresses for good measure, an attacker can use your network as a spring board for who knows what. When the police come a few days after, they are coming to your door—and not to talk about how nice your lawn is. Don't be that guy.

No doubt you've seen some of the hack logs being released. One part that stands out over and over again is the heavy database usage. It used to be early on that virus and hackers would destroy data, usually just for lulz. However, with the explosive commercial growth of the Internet, the real target is turning into data theft. You should learn how this happens so you can protect yourself accordingly. Let's take a look at what makes this possible and dare I say, easy.

I am writing this quick post in response to the recent earthquakes and tsunamis that are affecting Japan. As soon as the news broke, and we began to hear of tsunami warning for our area, I immediately realized how under prepared I was for a natural disaster. The thing that drove this point home even deeper was the number of people asking me for advice on what they could do to prepare for the possibility that we are hit by one of the resultant tsunamis. Many thoughts raced through my mind, and...

Wouldn't it be nice to just sit at your buddy's house, plug into his network, and see exactly what he's doing? What if it was as easy as that? What makes packet sniffers like Wireshark such potent tools is that a majority of local area networks (LANs) are based on the shared Ethernet notion.