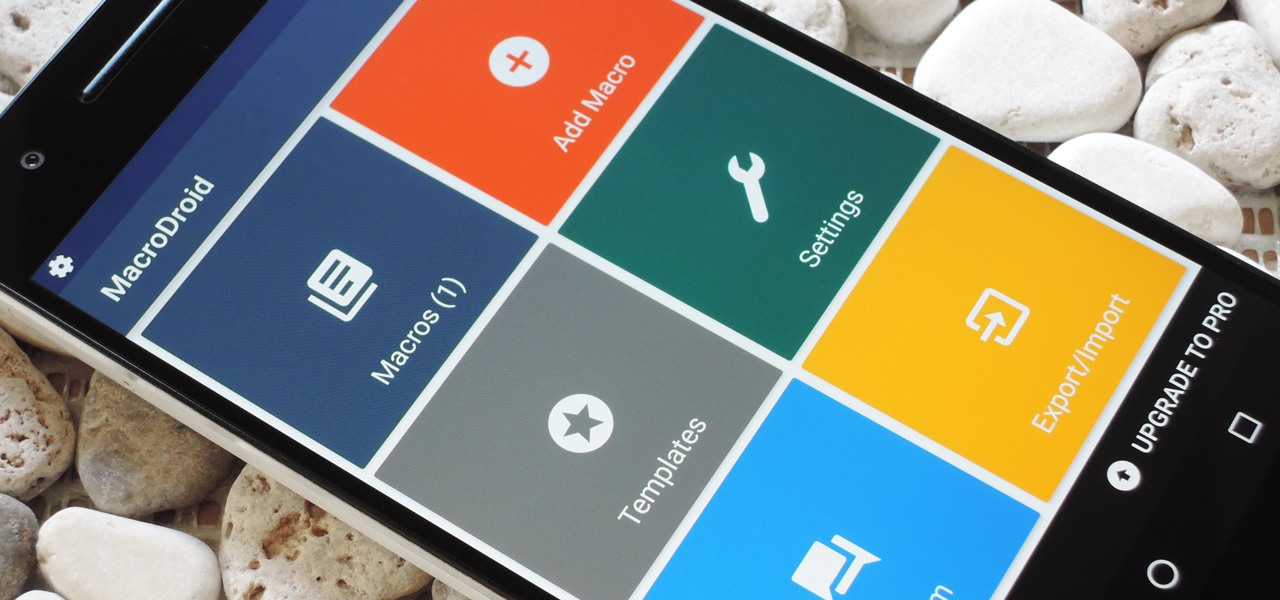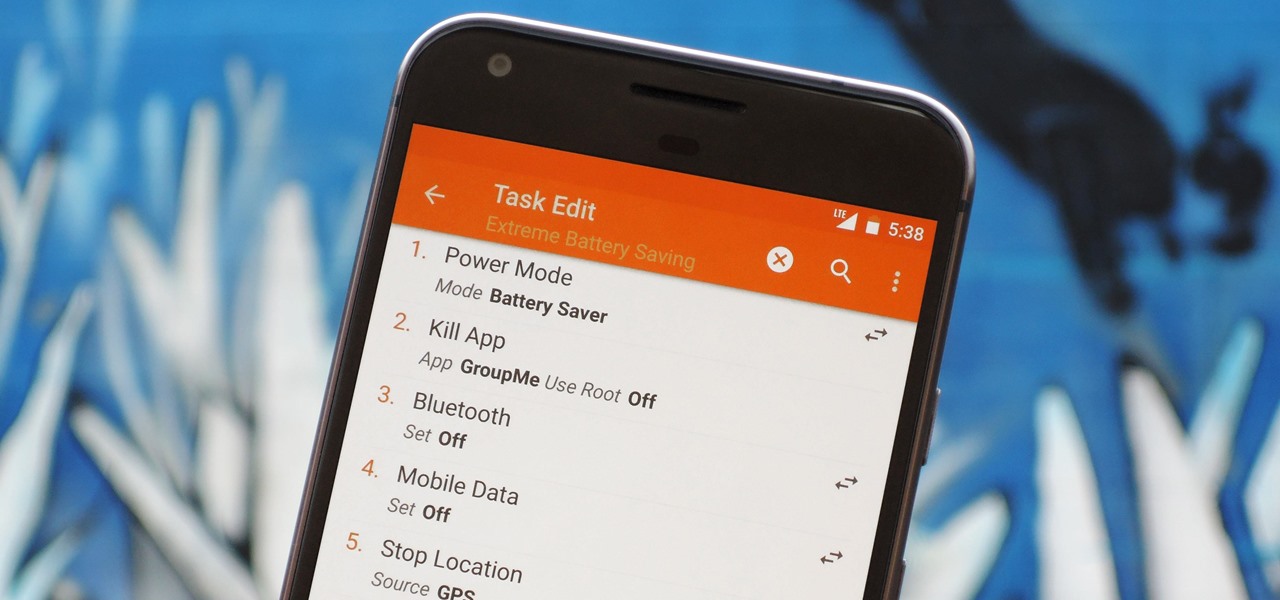
There are two core components to any Tasker automation: A profile and a task. Profiles are basically a set of conditions that must be met before Tasker will do anything. Tasks, on the other hand, are the actions Tasker will perform when your profile's conditions have been met. Think of them like triggers and actions, respectively. Or a cause and an effect.

The large, dome-shaped LiDARs that have become a fixture on driverless car prototypes are expensive and notably ugly. And yet, these unsightly devices should remain planted on driverless cars, even when they become available in commercial fleet services across the country in a couple of years.

Wherever there are people, the party is sure to follow. Well, a party of microbes, at least. That is what scientists at NASA's Jet Propulsion Laboratory have found after a 30-day microbial observation of the inflatable lunar/Mars analog habitat (IMAH).

Nvidia's decades-long development of graphics processor units (GPU) for PCs has given it a major leg up in the driverless space.

Bitmojis are not only a good way to personalize your Snapchat account, but also a really fun Snap addition to play around with. A bitmoji is basically like your little avatar, letting you design your mini-self whichever way that you desire.

A vulnerability in the design of LiDAR components in driverless cars is far worse than anything we've seen yet outside of the CAN bus sphere — with a potentially deadly consequence if exploited.

Look no further than Flint, Michigan, to discover the serious consequences of contaminated drinking water. Around the world, water polluted by pathogens and toxins sickens people or cuts them off from safe drinking water. Looking for a solution, researchers created tiny, swimming robots that pack a powerful punch against waterborne pathogens.

The Massachusetts Department of Public Health (DPH) issued a health alert for a Boston mumps outbreak, on Monday, June 5th, to healthcare providers and local boards of health. There have been 12 reported cases of mumps during the recent outbreak. The affected residents' symptoms occurred between March 24th and May 31st, and 10 of the 12 had symptoms after May 9th. There have been 35 confirmed cases of mumps in 2017 in Massachusetts, and "nearly 300" suspected cases in the continuing outbreak.

New statements from Apple make it clear that they do not believe a hacker, or group of hackers, breached any of their systems. This comes after a recent report from Motherboard that a hacker gang called the "Turkish Crime Family" is threatening to remotely wipe up to 559 million iPhones by April 7.

It's become a routine for many of us to ring in the New Year with pledges to finally get our budgets and finances under control. Unfortunately, it's also quite difficult to to keep those promises. Some of us will just dive into our resolutions and wing it as we move forward, which usually ends in failure. But even for those of us who plan carefully, obstacles along the way can spell doom for New Year's resolutions.

Maybe you've had a long day... or maybe you just want to treat yo' self. So you head to your local watering hole for some tasty, tasty liquor. Your current fave on the cocktail list is a drink of something strong with bitters; you don't know what bitters are, but damn if that booze isn't delicious.

While you can't turn art into a formula, the film industry has managed to come stupidly close. While many storytelling principles still stand across mediums, successfully crafting a compelling, immersive narrative in virtual reality requires a brand new rulebook. Through trial, error, and success, writer/director/editor Adam Cosco figured out the right rules to follow (and break) in "KNIVES"—his latest 360-degree short film. The film tells an old-fashioned tale of a woman, Kelsey Frye, strugg...

Whether you made the switch from iOS, or you came from a different Android device, there's a lot to learn about your new Galaxy device. Samsung does things a bit differently, and thanks to their TouchWiz interface, there are tons of added features to take advantage of—though some folks might find these extras to be a bit too much.

As a self-proclaimed chocoholic, any day with chocolate mousse in it is a good day in my book. And thanks to prominent chemist Hervé This, one of the founding fathers of molecular gastronomy, chocolate mousse is not only easy to make every single day—but only requires two ingredients.

Before you figure out how to strip the paint on your car to bare metal, you should should first ask the question, should I strip all of the paint off. Depending on the type of job you're doing, it may actually be better not to strip all of the paint off.

Caramel is delicious, but it can be a tricky flavor to incorporate into baking. Traditionally, caramel is a liquid, and that doesn't always suit dessert preparation since adding extra liquid to baked goods can ruin them. So how do you get that buttery, toffee-like flavor?

When it comes to Android automation apps, Tasker has never had much competition. But considering how difficult it can be for a novice user to get the hang of things, and factoring in Tasker's drab and complicated interface, there's definitely room for another developer to step in with a Tasker alternative.

Why, for the love of God, do people keep inventing ridiculous devices that make the simplest things more complicated in the name of convenience? This may be a rhetorical question that will forever go unanswered—because these crazy gadgets just keep rolling out, one after the other.

Hello people, I'm back for Part-3. In this part, as promised, we are going to create a client program and then we are going to test it with our server program made in Part-2.

Virtual reality is all the rage these days, especially with devices like the Oculus Rift, Gear VR, and HTC Vive hitting shelves lately. But before any of those fancy, expensive headsets ever made it to the market, Google came up with a thrifty and inventive substitute in the form of Google Cardboard.

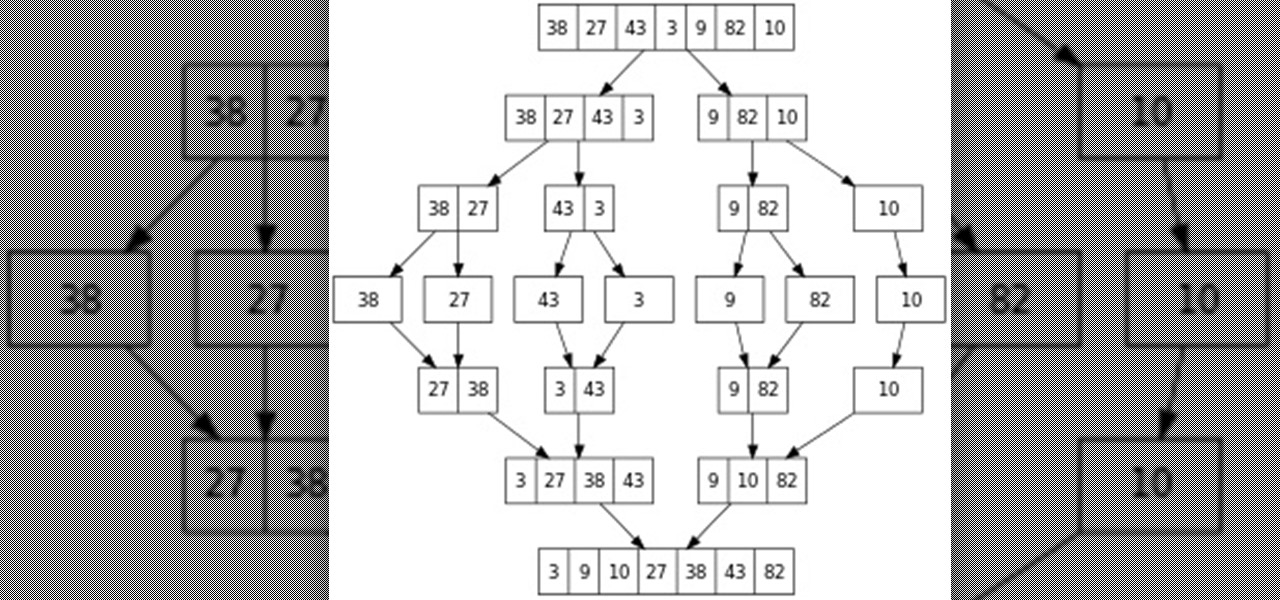
Hello everyone! This is part 7.0 of my Sorting series. I know, I said last time that there would be a 6.1, but not just yet!
In this Tutorial I will show you how you can use the frequency of letters to decrypt the famous Caesar cipher. I hope it is easy to understand and helpful for getting in touch with basic cryptanalysis. If you find any mistakes or have questions feel free to ask me. Finally I ask you to give me feedback which I will take into account for the next part.
Hey everyone. Only found the site a few days ago but really loving it. Been

This is the easiest cookie batch you'll ever bake, I promise. And no, take-and-bake cookie dough doesn't count. With this recipe, it'll take you less than 20 minutes to go from your sad, cookie-less life to cookies in your absolute favorite flavor... of cake.

I mentioned in one of my earlier articles something about ghost hackers, and very shortly stated a thing or two of what they do.

Welcome to an introduction on writing basic malware, an optional sub-series in which I expose you to malware and its technologies. This is written for those who wish to seek a beginning in malware analysis or enlightenment on the subject. We will be justifying the writing and covering types of malware.

Chestnuts are roasting on an open fire, which can only mean one thing: Christmas is nearly here. It's the time of year we're supposed to spend with family and friends, but usually we spend it stressing out over what to buy everyone on our list without going over budget, or shopping for decorations or holiday-friendly food items.

Welcome back! In the last iteration of how to train your python, we covered loops, today we'll be covering something that I wish I had learned about much earlier in my scripting career, errors. We all run into them, and they can be frustrating, but there is also a silver lining to them. Today, we'll be discussing why some errors are unavoidable, and what we can do when we run into them. Also, this article will be more of a concept and less of writing actual code, but the information is equall...

If you don't want to dress up as a vampire, witch, werewolf, or zombie again this Halloween, step things up a notch and go viral. There have been a ton of funny memes and absurd news since last October, so the only hard part is settling on the right one for inspiration for your costume.

Alcohol isn't exactly considered a healthy lifestyle choice; more often than not, it's associated with empty calories and bad decisions. But that doesn't mean there aren't a few benefits to drinking in moderation. In fact, gin is a liquor with a wealth of potential benefits to offer. So read on, and discover ten ways in which gin might actually be a good drink for you.

Reddit, the self-proclaimed "front page of the internet," continues to take a big bite of my free time each and every day, as well as millions of its other users'. The clicking and scrolling through page after page never gets old, but you could speed things up with a few browser extensions and double your Reddit knowledge in half the time. Here are my favorite extensions you can try out for the Chrome, Firefox, and Safari web browsers.

When I tried to set up an eviltwin for a MitM-constelation in kali 2.0, I couldn't provide internet to the victim. The origin was the brctl bridging. I have read many tutorials but all of them where explained in backtrack and older versions of kali. So i was searching for a solution without using brctl and this solution will be explained now. This will just work on unencrypted wireless-environments.

Man-in-the-Middle attacks can prove to be very useful, they allow us to do many things, such as monitoring, injection, and recon.

Whether you call them chickpeas, garbanzo beans, or Egyptian peas, these little morsels are one of my favorite snacks—when properly seasoned, that is. Being mild in flavor on their own, they're incredibly versatile and fun to experiment with. (They're also incredibly healthy.)

I was a vegetarian from age 6 until age 23. When I started eating meat again for the first time in 17 years, most people I knew (including me) expected me to be pretty conservative about it: chicken breasts, hot dogs, and all the other "basic" meats that everyone loves.

From our work life to our home life, we have an awful lot of projects, tasks, and activities that require more productivity than play. After working for an entire day in the office, no one wants to face even more that needs to be done at home.

So, we all probably know that when you run a trojan made by Metasploit, nothing will appear to happen. This is a sign for me to immediately check my Task Manager, but for an unsuspecting victim, it will just seem like a broken file. It is likely that they will delete this "broken file" once they see that it "doesn't work." In order to prevent this, we need to disguise the trojan.

Welcome back, my tenderfoot hackers! Have you ever wondered where the physical location of an IP address is? Maybe you want to know if that proxy server you are using is actually out of your local legal jurisdiction. Or, maybe you have the IP address of someone you are corresponding with and want to make certain they are where they say they are. Or, maybe you are a forensic investigator tracking down a suspect who wrote a threatening email or hacked someone's company.

Modern medicine utilizes cutting-edge technology more than ever, so it would only make sense that the powerful handheld computers we all carry around these days could play a big role in wellness.

From time immemorial, human beings seem to be at odds with one another. When these differences become so heated and unresolvable, it eventually erodes into physical violence. This violence has manifested into some of the most horrific exercises in human history, things which every school child is aware of and none of which we have to recount here. Although humans have been cruel and violent for a very long time, the 20th century may have epitomized that behavior. With two World Wars and many,...