Hi guys, this is going to be kinda like a follow up to my previous post on hacking facebook with the remote keylogger. If you haven't seen that post I suggest you do. So like you can click here. Anyway let's move on.

In part one of this tutorial we found out that your English teacher is a paedophile, by using a Man in the Middle attack to intercept his internet traffic.

Welcome back, my hacker novitiates! In an earlier tutorial, I had introduced you to two essential tools for cracking online passwords—Tamper Data and THC-Hydra. In that guide, I promised to follow up with another tutorial on how to use THC-Hydra against web forms, so here we go. Although you can use Tamper Data for this purpose, I want to introduce you to another tool that is built into Kali, Burp Suite.
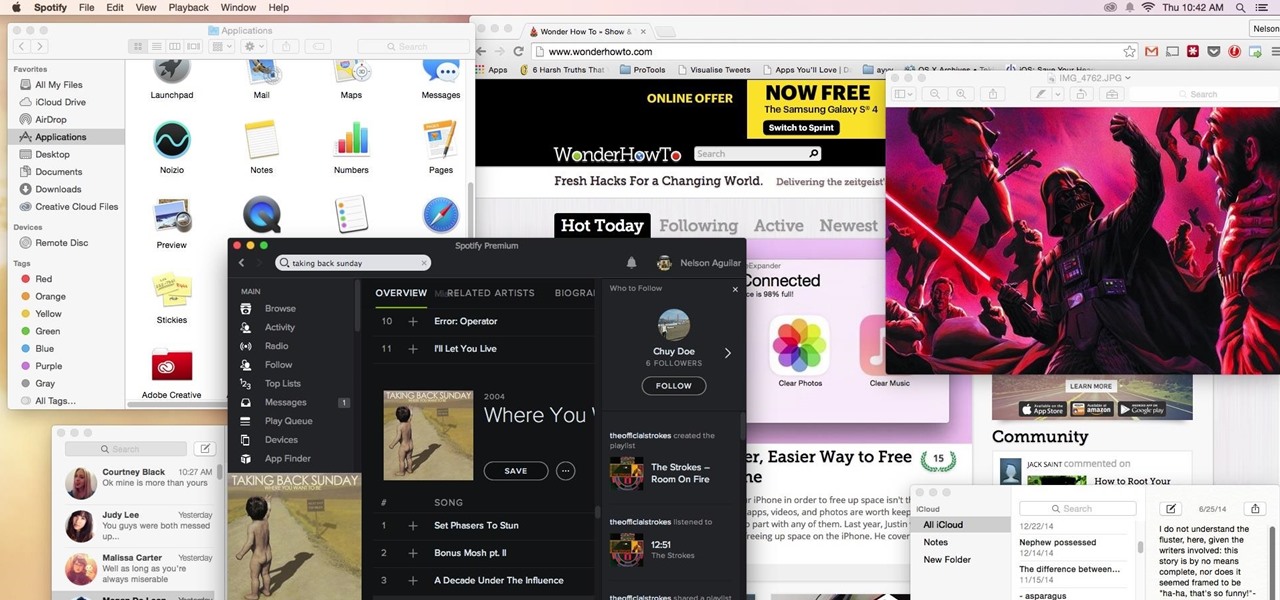
Normally, if you want to close all of the open apps on your Mac, you'd have to either quit them all one by one or restart, shut down, or log out while making sure to deselect “Reopen windows when logging back in." The latter option is great, but it doesn't always work in Mac OS X, and what if you don't want to restart, shut down, or log out?
During class or while at work, it can take an immense amount of self-control to resist navigating over to Reddit. The link-aggregator and meme-warehouse makes it too easy to kill time... most of which you should be spending on various other tasks.

Korean electronics giant LG maintained a large presence at CES 2015. While their TVs and home appliances were heavily showcased, my interest was primarily on one device—the new LG G Flex 2 Android phone.

Not too long after getting a new device, you probably start installing any and all apps that seem fun and interesting. But after having used the device for a considerable period of time, those extraneous apps begin to take their toll.

Unless you've been living under a rock for the past five years, you've at least heard murmurs of Google's self-driving car, with Big G even getting California and Nevada to sign off on legislation to allow these motorist-less vehicles on the road. But now, Google is showing off their in-house manufactured vehicle, as opposed to the Prius' that doned their hardware in the past. And it's...well, it's something.

Closing apps in iOS 6 was different that what is now in iOS 7. Shown in the video below is the old clumsy way of closing apps on the old iPads.

Lenovo brought out the big guns for CES 2014, with the Vibe Z showcased as the Chinese company's' first foray into the LTE smartphone space. Slated for a February release, the ultra-thin and extremely light smartphone will certainly be in the running for top smartphones of this very new year. Photo via CNET

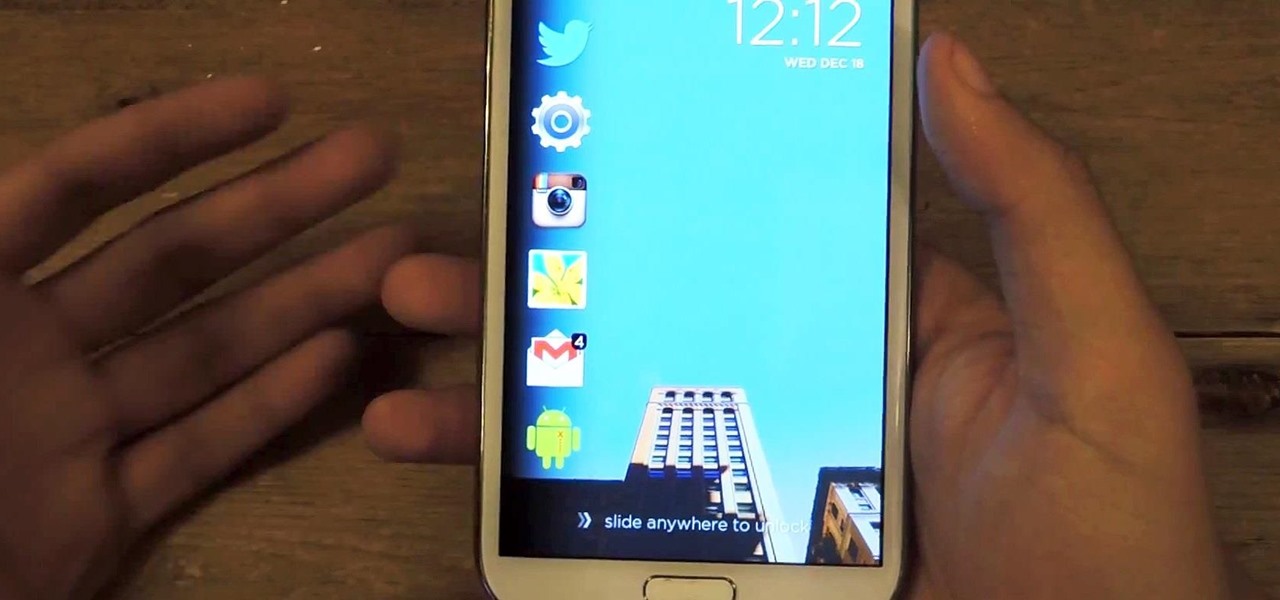
Not particularly good looking, TouchWiz's lock screen adequately supplements the clunky and almost cartoonish-look of the infamous user interface on the Samsung Galaxy Note 2. While there are hundreds of lock screen options in the Google Play Store, I've never quite discovered one that I've thoroughly enjoyed, due to the obfuscation from so many options.

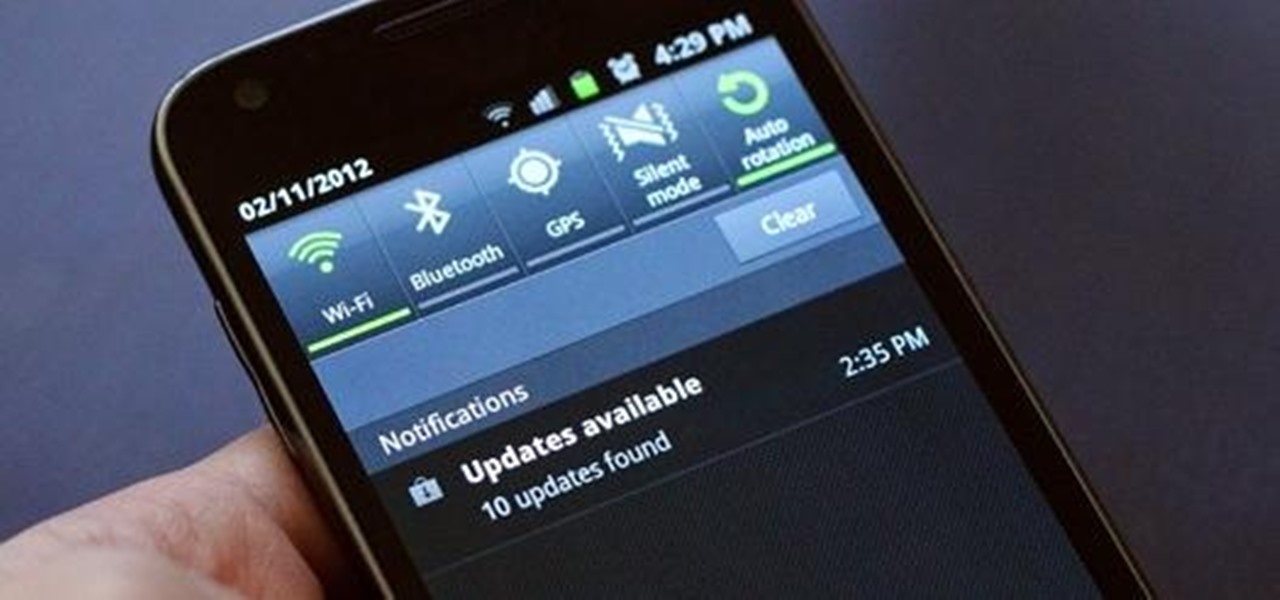
With the Google Play store on your Android device, it's a relatively easy process to check all of your application updates. All you have to do is launch the Market app, go to the My Apps section, and from there you'll be able to see all of the available updates for your applications, which should be positioned at the top of the list. The problem with this process is that many times, you'll go days or weeks and quite possibly even months without checking the Google Play application market, lea...

What do Justin Bieber, Kim Kardashian, Chris Brown, Rihanna, and Soulja Boy all have in common? They suck at Instagram.

A little confused on how to delete applications on your iPhone you don't want? Your iPhone 3G might have applications that are taking up too much space that you rarely use. In this iPhone tutorial, learn how to delete applications and free up some space on your 3G iPhone. Delete applications from the iPhone 3G.

This video demonstrates how to turn Windows Vista to Windows 7 for free. Make sure that you are running your PC on a Windows Vista OS. First, unlock your taskbar by right-clicking on it and unchecking the option. The space where your smaller application icons are located can now be made wider. Re-lock your taskbar once done. You can also right click and select View>Large Icons to make the icons look bigger. You can also download a free application at RocketDock which will make your Vista task...

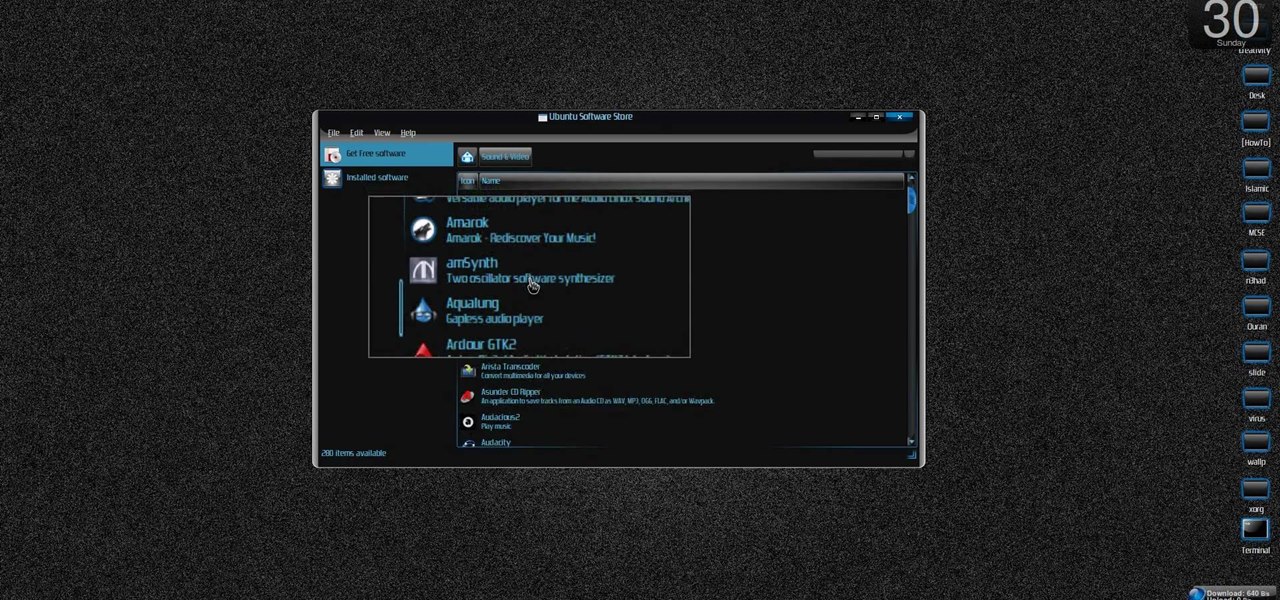
New to Ubuntu Linux? This computer operating system could be a bit tricky for beginners, but fret not, help is here. Check out this video tutorial on how to install the Ubuntu Software Store on Ubuntu Linux.

Check out this informative video tutorial from Apple on how to set up iChat to text, video or audio chat with friends. iChat is an application that's part of every new Mac. It lets you stay in touch with friends and family in fun innovative ways.

Watch this video tutorial from the Polish Guy to see how to clean a car taillight with Autosol Polish. In this demonstration we use Autosol Polish to clean and restore a car tail light. The tutorial includes detailed work instructions and best practices.

In this video tutorial, Chris Pels shows how to use the ASP.NET IIS Registration Tool to configure ASP.NET. First, see how file extensions are mapped to ASP.NET in the IIS Manager on a global and web-site-by-web site basis. These script maps provide the basis for configuring individual ASP.NET applications to run under a specific version of the .NET Framework. Next, see how aspnet_regiis.exe, the IIS Registration Tool command line utility, is specific to each version of the .NET Framework and...

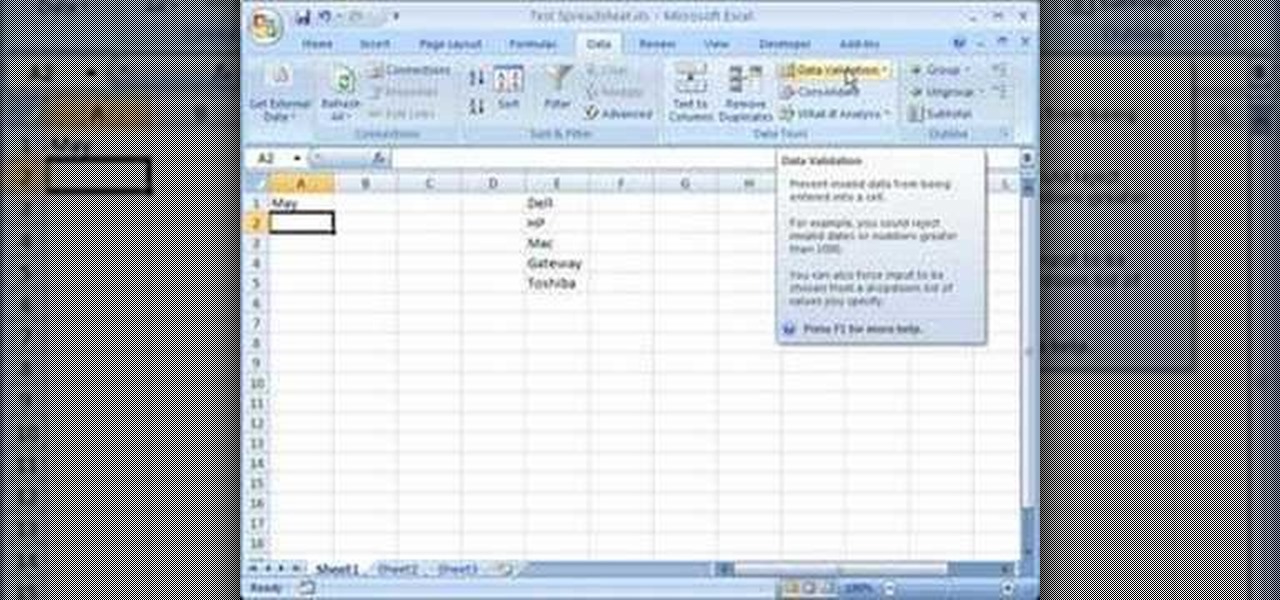
This video is a tutorial on how to create drop-down menus in Excel 2007. Select a cell on your spreadsheet and click on the “Data” tab. Go to the “Data Tools” section and select “Data Validation”. In the window that opens select "Allow" and choose "List". You will create a list of the values you want to allow. Type in the values, separated by commas, and click OK. Now you will see your selected cell has an icon to right that indicates there is a drop-down menu containing the value...

This how-to video is about demonstrating the Leidenfrost effect with methyl alcohol and a penny. To demonstrate the Leidenfrost effect the following items are required:

Make your eyes look bigger and brighter by lengthening your lashes. You Will Need

Those old cell phone and laptop batteries staring you in the eye? Don’t worry, recycling them is easy.

Learn this great tip for folding a t-shirt into a compact, self-contained unit for efficient storage.

Here's another demonstration on how to combine harmony and melody into a self-contained solo piece. This time you'll be playing "Pearly shells" on the ukulele.

Wonderhing how to get started writing C# applications? This video offers a tour of the various features in Microsoft Visual C# 2005 Express Edition, and will help you become familiar with the tool, and get started writing -- and understanding -- your first application. To get started writing C#, take a look! Write your first C# application in Visual C#.

Learn how to use the variety of applications available in he Avid Xpress Studio and Xpress Studio HD suits to author, edit, and output professional quality video projects. Applications covered include Avid 3D, Avid FX, Avid PT LE, and Avid DVD. Use Avid Xpress Studio.

Apple has pulled quite the headscratcher in anticipation of its big iPhone unveiling next week. Its latest iPhone update, iOS 13.0, is just on the horizon, going through eight beta versions so far. And yet, before that software's official release, the company has started beta testing iOS 13.1, with no explanation why. And the second public beta for iOS 13.1 is now out, so let's see what's new.

When Apple takes the stage next week, we have no idea what version of iOS it will release. For months it seemed like a given that we would, of course, see iOS 13 seeded to our iPhones. Now, we aren't sure if Apple will tout iOS 13 or iOS 13.1, since the latter is now the focus of its beta testing. In fact, 13.1's second developer beta is now available to download and install.

One of the best ways to improve your skills as a hacker is to learn to combine different avenues of attack to achieve success. What if it were possible to get a victim to connect to our machine and execute a chosen payload on our behalf? This is indeed possible with the almighty Metasploit and the aid of a technique known as command injection.

Wound infections don't usually enter the blood and become systemic, spreading the infection throughout our bodies, and there's a good reason for that: Our bodies actively work to prevent it, according to research that discovered a new use for a protein first discovered decades ago.

The Drug Enforcement Agency (DEA) has been purchasing spyware from the Milan-based Hacking Team and its US subsidiary Cicom USA since 2012. Public records reveal invoices between Cicom USA and the DEA that have ranged between $22,000 to $575,000 from 2012 to 2015.

Could the technology that powers games like Pokémon GO be used for surgery in the near future? Researchers at the University of Maryland think so.

Welcome back, my tenderfoot hackers! One key area on the minds of all hackers is how to evade security devices such as an intrusion detection system (IDS) or antivirus (AV) software. This is not an issue if you create your own zero-day exploit, or capture someone else's zero-day. However, if you are using someone else's exploit or payload, such as one from Metasploit or Exploit-DB, the security devices are likely to detect it and spoil all your fun.

Welcome back, my novice hackers! In this third installment of my Hacking Web Apps series, we will look at the authentication of web applications. Remember, there are many ways to hack web applications (as I pointed out in my first article), and cracking authentication is just one method.

The dock has been a staple of Mac OS X since its creation and not much has been needed to improve its functionality, but when you add theming to the mix, you can run into some issues.

Incorporating features such as CarPlay, UI enhancements such as the new call screen, and several bug fixes, iOS 7.1 was the first major update to Apple's operating system since iOS 7 was released in June of last year.

This time it's serious. Really. The largest web security vulnerability of all time went public on Monday, April 7th, 2014, resulting in widespread panic throughout the Internet as system administrators scrambled to secure their websites from the OpenSSL bug known as Heartbleed.

With the the general computer users understanding of Information security rising (at least to the point of not clicking on unknown links), and operating system security getting better by default. We need to look for new and creative ways to gain a foothold in a system.

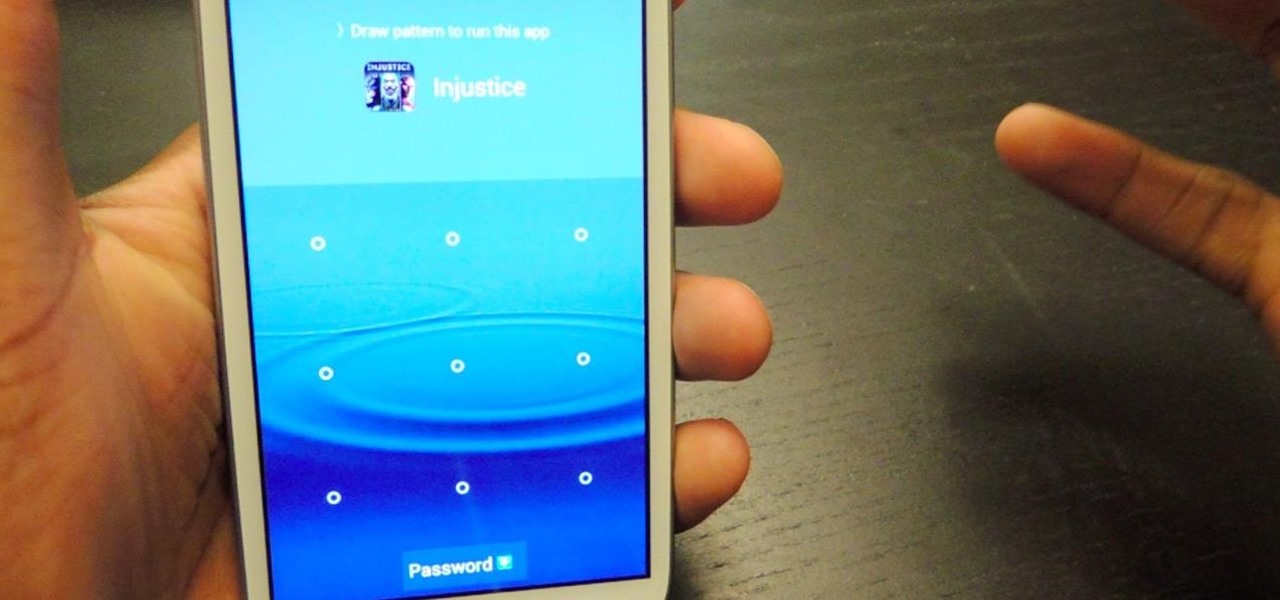
Keeping unwanted clowns off on my Samsung Galaxy S3 is priority number one. I've shown you how to snag a picture of people opening your apps and how to lock your screen for whenever you hand off your phone, allowing them to access only the page you left open.