Surfing: Hang Ten The ocean is a force of nature that refuses any effort to tame it. To throw one's self on the mercy of this beast is a courageous act. With the help of this trick guide, you can learn to harness that power and push your water-borne adventures to new heights. See how to

Surfing: Hang Ten The ocean is a force of nature that refuses any effort to tame it. To throw one's self on the mercy of this beast is a courageous act. With the help of this trick guide, you can learn to harness that power and push your water-borne adventures to new heights. See how to

There are two parts to the StormShield product: The server components (including the relational database and server) and the various agents that run on each endpoint. Among other things, the agent contains a host-based firewall and policy engine that can be customized to control applications and particular endpoint device features such as USB peripherals and registry entries. So watch this tutorial and learn how to protect your PC computer with SkyRecon's StormShield.
Oh, yeah. I was a skeptic, too. A few things are worth noting, though. 1) This stuff is cheap. You can get started on a project for very little money. Even advanced fabrication tools are reasonably priced.

forget that half assed human foosball, this is the real deal. set up a giant foosball game- strap your selves to some kind of revolving polls to flip you upside down like real foosball; throw in some balls filled with nasties (dog anal gland juice is the most foul smelling substance known to man) and let the game begin!

Self-storage may not be a new industry, but it is one that is rapidly reshaping its operations to suit a progressively more modernized customer base. In order to stay competitive with your self-storage facility, you'll need to keep an open mind, embrace current marketing trends, and most importantly, have a well-defined set of marketing goals. Your main focus should revolve around the following points:

SQL injection is a common web application attack that focuses on the database backend. WebGoat is a deliberately insecure J2EE web application maintained by OWASP designed to teach web application security lessons. I plan to use WebGoat for a few future videos. This first WebGoat video will show the basics of installing WebGoat and doing two of its SQL injection lessons. Hack websites with SQL injection and WebGoat.

Last year at CES, RealMax blew away the AR headset competition with a prototype AR headset surpassing 100 degrees field of view.

Cross-site scripting is one of the most common vulnerabilities found on the web today, with repercussions of this type of flaw ranging from harmless defacement to sensitive data exposure. Probing for XSS can be tedious and time-consuming for an attacker, but luckily there are tools available to make things a little easier, including Burp Suite, Wfuzz, and XSStrike.

Facing mixed reviews for the Magic Leap One, Magic Leap has already returned to the lab to improve on the device's successor.

Web 2.0 technology has provided a convenient way to post videos online, keep up with old friends on social media, and even bank from the comfort of your web browser. But when applications are poorly designed or incorrectly configured, certain flaws can be exploited. One such flaw, known as CSRF, allows an attacker to use a legitimate user's session to execute unauthorized requests to the server.

Command injection is a technique used by hackers to execute system commands on a server, usually via a web application or some kind of GUI. This can happen when an application provides some sort of functionality to the user involving the use of system commands. When the input is not properly sanitized, commands not originally intended to be run are allowed to be executed.

Now that we've had a chance to jump into the Lumin SDK documentation at Magic Leap's Creator Portal, we now have much more detail about how the device will function and utilize software than any single piece of content released by Magic Leap to date.

While self-driving cars appear to be as inevitable as augmented reality headsets, the auto industry and its technology partners likely have years of testing to complete and regulatory loopholes to jump through before self-driving cars hit most highways.

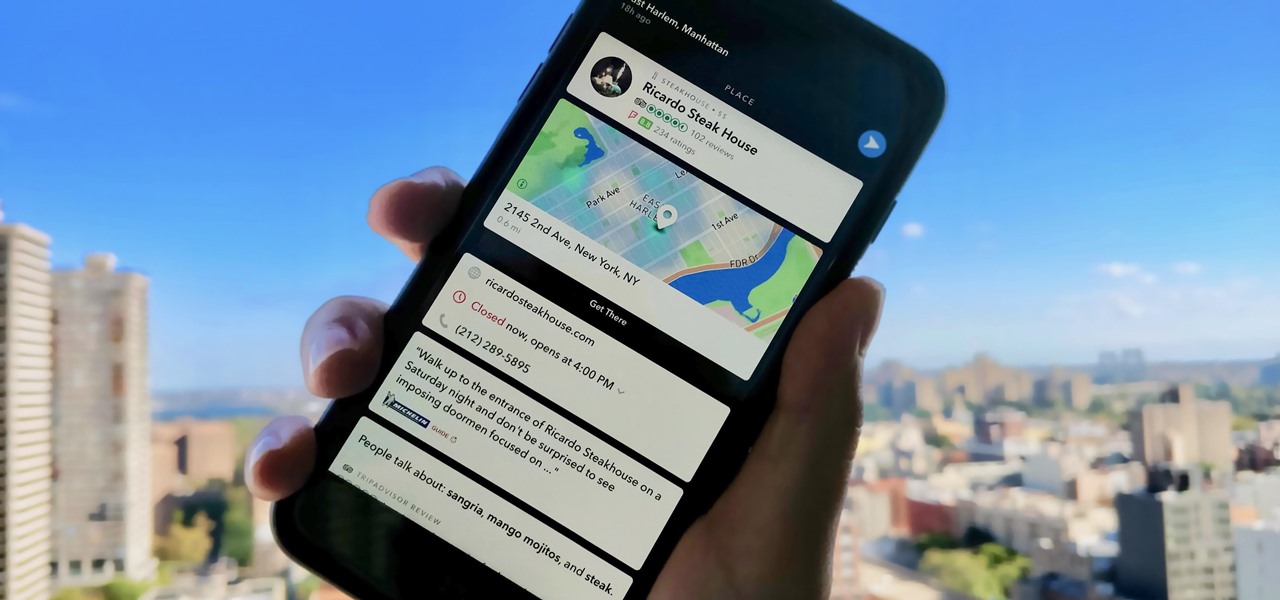
Not that long ago, Snapchat was an app with only one purpose — to send and receive self-destructing picture messages. The app has clearly grown since, adding many features that both adhere to its original function as well as ignore it. One of these new features is Context Cards. You may have heard about them, but what exactly are they?

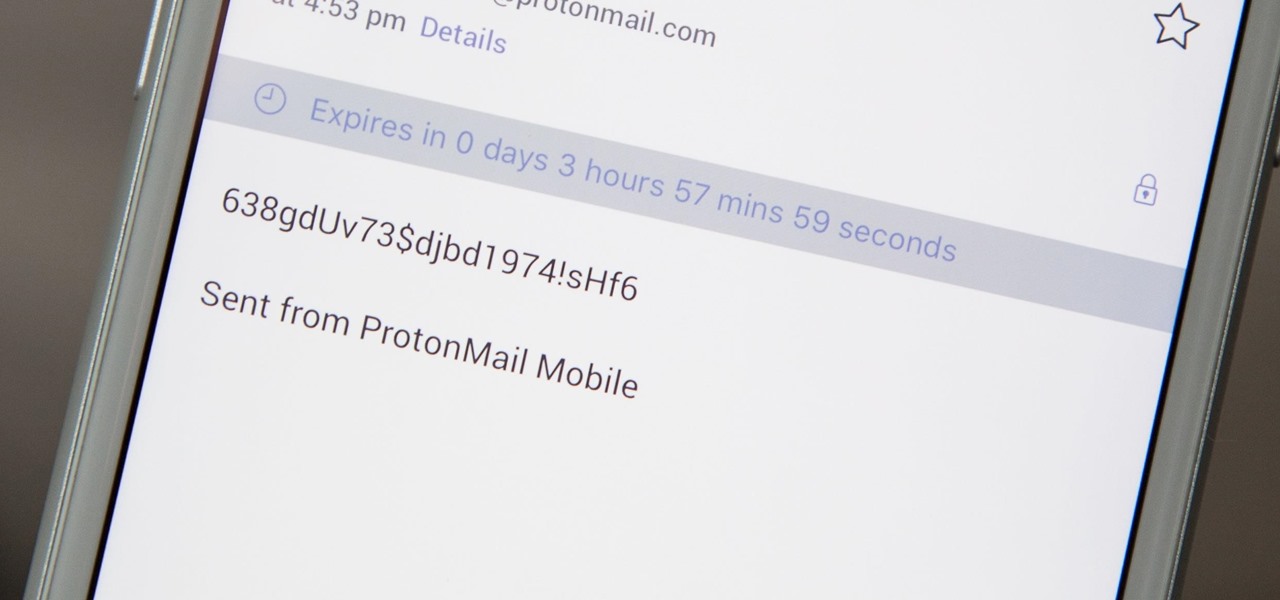
When you're sending sensitive information via email, it's best to do so with end-to-end encryption. Even better, set the email to destroy itself after a set amount of time for a little piece of mind.

All eyes will be on Tesla CEO and founder Elon Musk tonight to see if he is reveals details about the status of Tesla's challenged Autopilot at tonight's official Model 3 launch party.

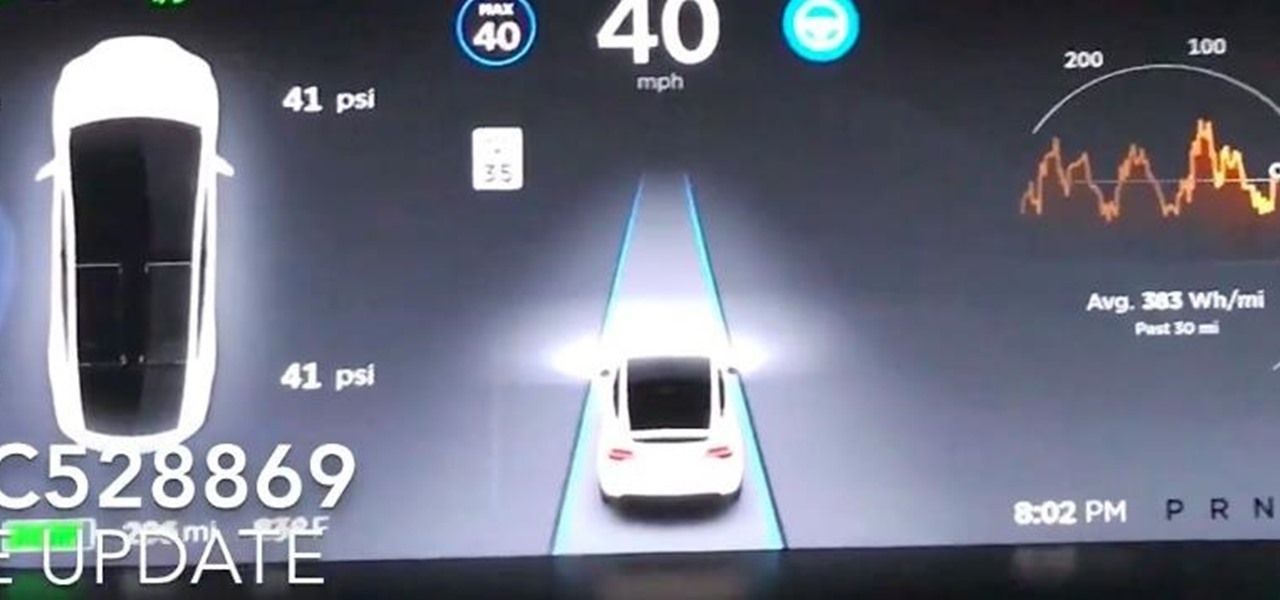
Some drivers give Tesla's Autopilot update released this week rave reviews, after version 8.1 has taken longer than expected to live up to Elon Musk's "smooth as silk" Tweet from earlier this year.

Volvo Cars' "all-electric" announcement last week was seen as a direct threat to Tesla's electric vehicle (EV) and driverless lead, but German auto giant Volkswagen (VW) says it is in a better position to challenge Tesla.

Uber's struggles are expected help Lyft get ahead in driverless development as it confirms its third partnership with autonomous tech company nuTonomy today.

The Cloud Security Alliance (CSA), a leading IT trade association, has published its first report on risks and recommendations for connected-vehicle security, ahead of when driverless cars are about to see volume production in the near future.

Stratford may soon become Canada's answer to Silicon Valley as the driverless car industry arrives. Potentially changing the character of the Ontario town known for hosting the Stratford Festival, a celebration of all things Shakespearean and stage-related.

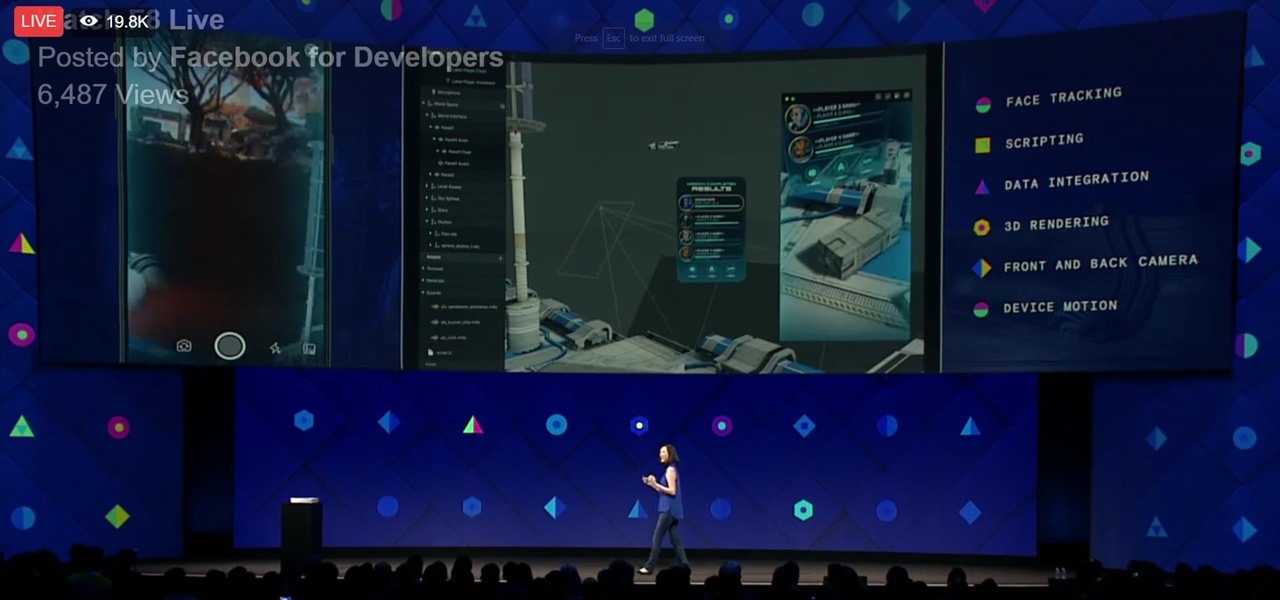
During his opening address on April 18 at F8, Facebook's developer conference, CEO Mark Zuckerberg launched the company's augmented reality platform centered on artificial intelligence-powered cameras.

Uber wants you to forget about cars and start thinking about fully autonomous flying as an alternative—a more "economically favorable" way of getting to your grinding nine-to-five.

Uber's driverless cabs began picking people up in Arizona in February, after its attempt at a pilot test in San Francisco. Now, one of these cars has been in an accident, and that's just the tip of the iceberg.

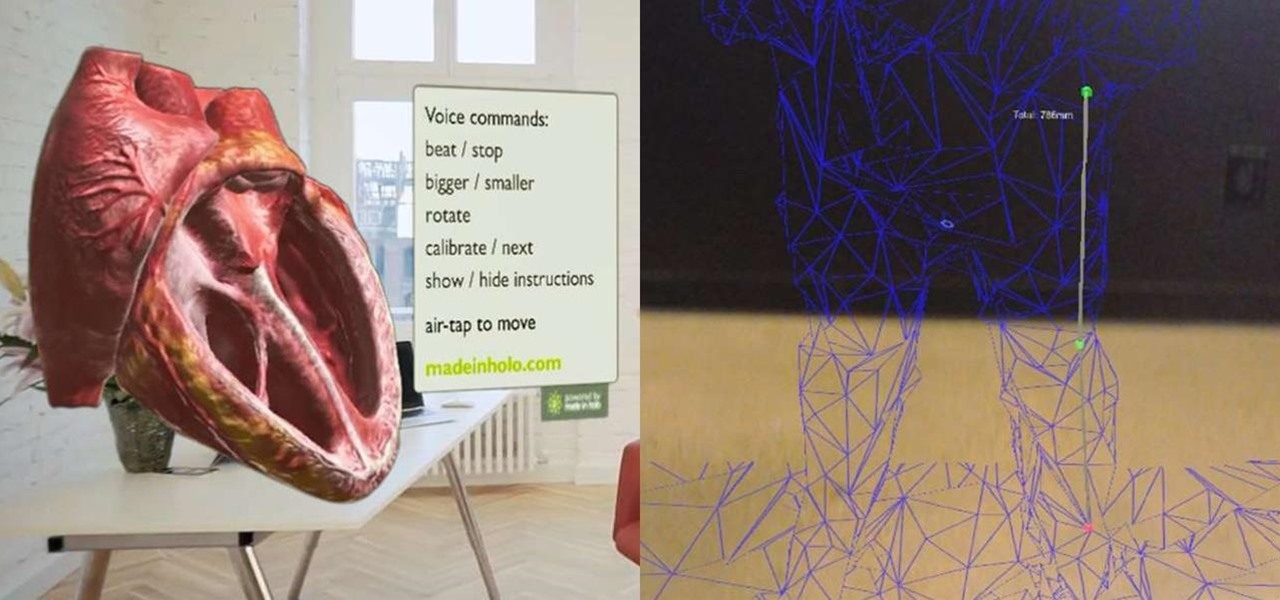
While all of my previous Have You Seen This? posts have all focused on individual HoloLens apps in the Windows Store, this time I'll be sharing a couple at once. These holographic applications are really simple in scope, so there is not a lot to say about them, yet they are interesting enough for me to want to share them with you.

In addition to trying to give Pokémon a life on the HoloLens, Sky Zhou, a founding member of mixed reality studio Matrix Inception, won Microsoft's Actiongram Fantasy Contest Quest last month for his video concept on slaying dragons. But fantastical creatures aren't the only thing Sky can whip up on the HoloLens.

A new contender has entered the mixed reality ring. San Fransisco-based Occipital has just released an "Explorer Edition" of Bridge—an iPhone-based mixed and virtual reality headset that uses their popular Structure Sensor. At a fraction of the cost of a HoloLens developers kit, this could be a place many curious people use to find their NextReality.

Welcome back, my tenderfoot hackers! As you should know from before, Snort is the most widely deployed intrusion detection system (IDS) in the world, and every hacker and IT security professional should be familiar with it. Hackers need to understand it for evasion, and IT security professionals to prevent intrusions. So a basic understanding of this ubiquitous IDS is crucial.

The produce section is full of fruits, both familiar and quite strange. Depending on the season, you may see giant, bright-green bananas on display next to the normal bananas that you know and love. No, those aren't super-unripened bananas—they're plantains, and they are definitely a different fruit altogether. However, once you get to know them a little better, you'll find that they're much more fun to cook with.

Welcome back to another episode of Java Tutorials, In today's tutorial, we'll be learning about what methods are, proper syntax when writing Methods, and why they are beneficial in a program's code.

Hello NullByte! This will be my first How To series.

Though you may scrub every inch of your kitchen, there are plenty of trouble areas that are nearly impossible to get clean: gunked-up tile grout, rust in the sink, and caked-on burners and grates on the stove. As far as burners and grates go, you're in luck, because there's a simple solution to returning even the grossest ones back to their original shine. The Key Is Ammonia

While shortcuts to your Camera and third-party apps like Snapchat are great for capturing fleeting moments, it still takes a few seconds to open them and snap a photo. That means you could potentially miss a great shot if you're not quick enough. But now there's a super-fast way to capture and send photos without having to waste time unlocking your device.

Each morning, we spend a significant portion of our time staring into the mirror. From choosing clothes and accessories to perfecting our hair, we try to make ourselves attractive. Yet catching others' attention doesn't have to rely on preening and primping. There's some truth to the maxim of beauty in confidence—all you need to make yourself more attractive is spray on your favorite scent.

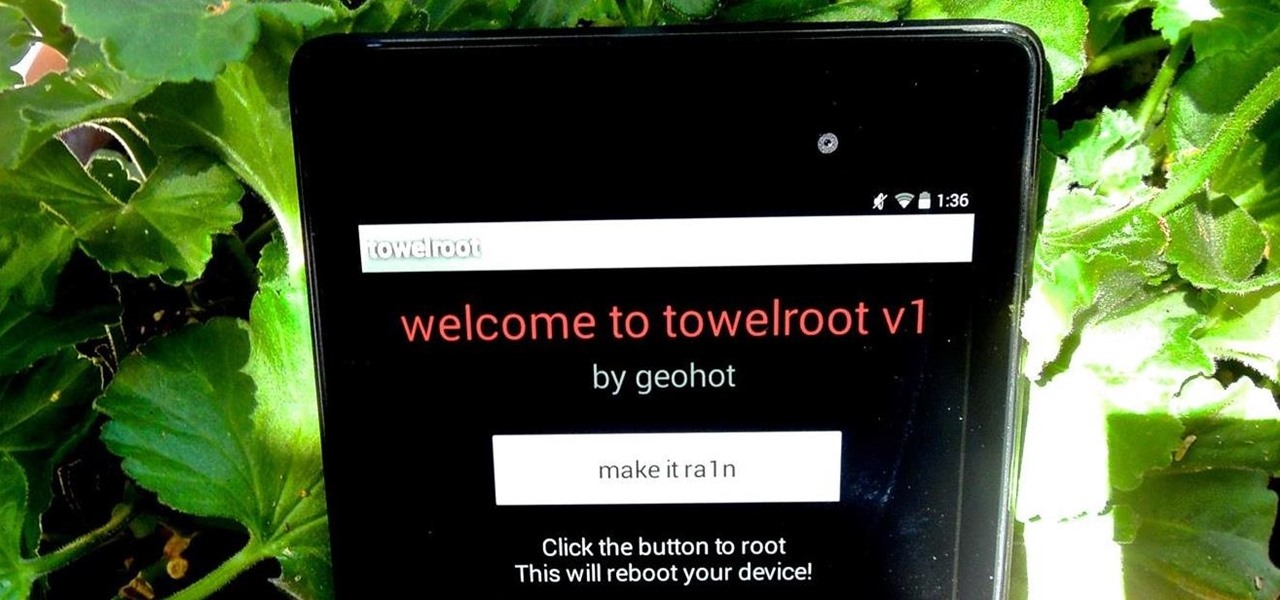
Rooting your Nexus 7 tablet is now easier than ever. Previous rooting methods required connecting your tablet to a computer and using any one of a number of programs and/or ADB commands. Now, it's as easy as downloading an app on your phone and tapping one button.

Welcome back, my greenhorn hackers! In a previous tutorial on hacking databases, I showed you how to find online databases and then how to enumerate the databases, tables, and columns. In this guide, we'll now exfiltrate, extract, remove—whatever term you prefer—the data from an online database.

I wonder if Best Buy has any Note 3's for sale?? When trying to figure out when something is in stock, we usually either check online or call the store to talk to someone. If certain products are out of stock the process might be tedious, with having to find phone numbers and calling several stores.

Whether it's because you have nosy family and friends or you're just cautious about losing your device, having a passcode on your Android smartphone is essential for protection. However, you don't always need or want a passcode, especially when you're home alone or in your car on the way to work.

Here are instructions to make an origami tarantula. Detailed visual instructions are on the video that contains a map and images of the origami.