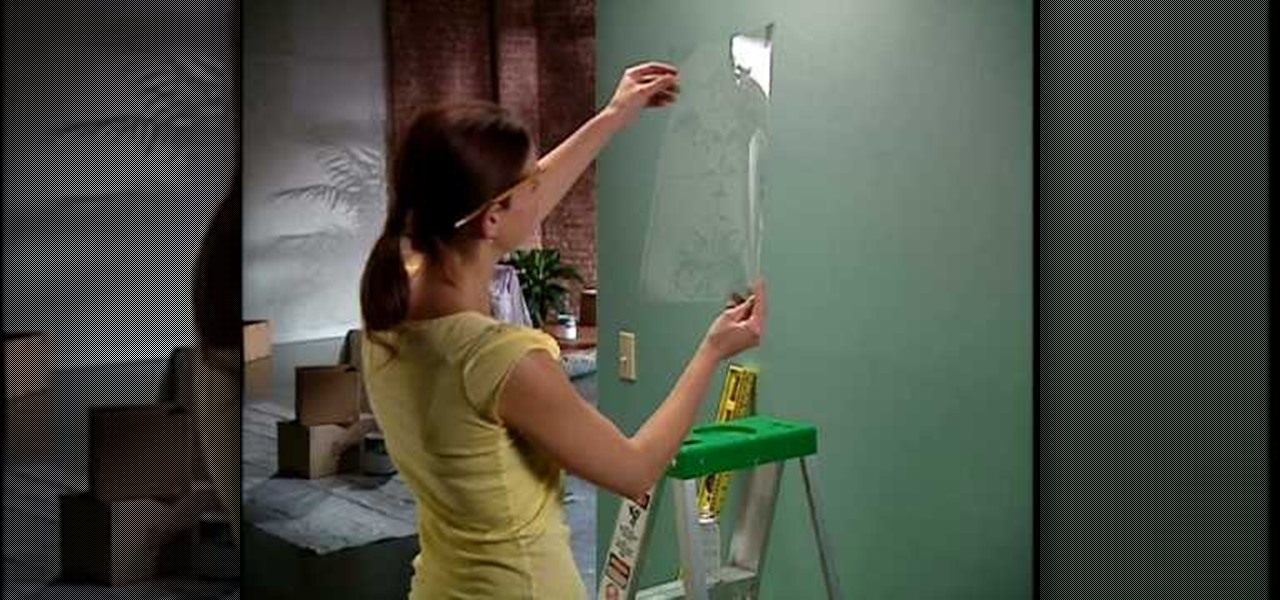For a neat, decorative edge finish, convert the piping flange to a self-finished facing, thereby eliminating the need for a separate facing or a lining. This video will show you just how to do all-in-one piping and facing with a thick and thin version. Make sure to click the RealPlayer or Quicktime link to start the video. Do all-in-one piping and facing.

See the key milestones your 8-month-old, now in his ninth month of life, is likely to reach -- such as crawling, imitating, self-feeding, and figuring things out. Know what to expect during the 9th month of your baby.

Martha makes a spring Good Thing: a honey bunny bookmark, featuring a photo of a child as the bunny's face. You will need thick paper, self-seal laminate sheets, scissors or utility knife, white chenille pipe cleaners, wire clippers, hole punch and photo. Make a honey bunny bookmark.

In this clip, we learn a basic digital photography workflow, one which will enable you to enhance your favorite digital photos with both ease and speed. (Note: To follow along, you will need to have the application installed. Learn how to download and install the Mac App Store here.)
Update: If you're running iOS 7 or higher, you'll want to check out the new way to fully close your background applications.
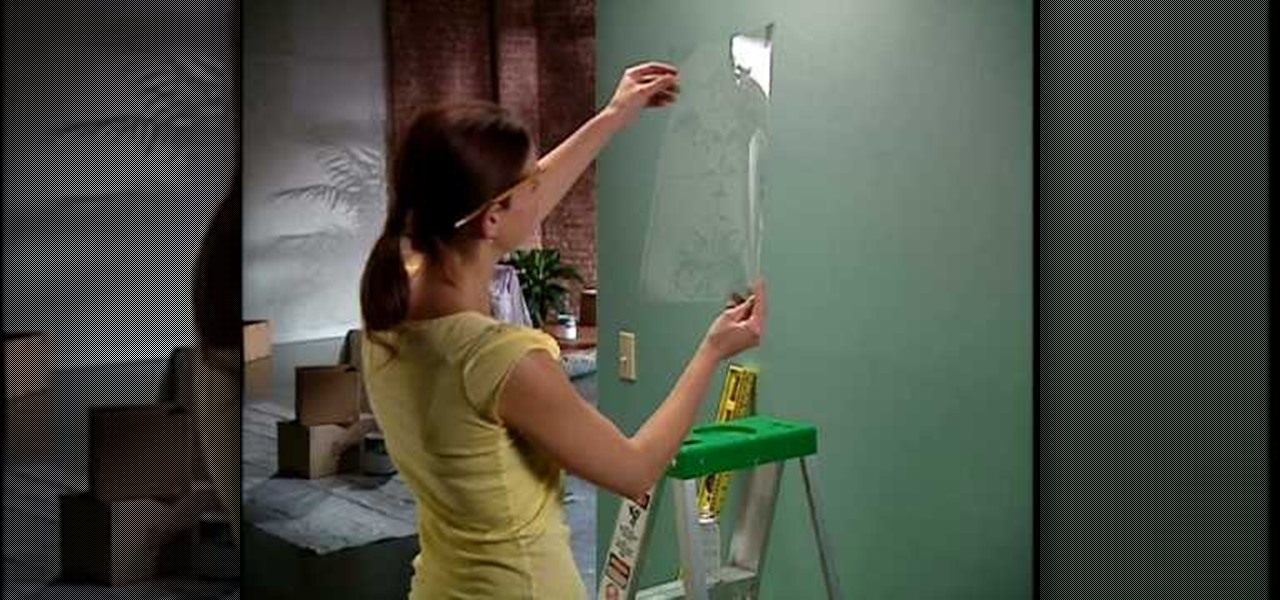
This is a step by step tutorial on stencil painting your walls, brought to you by The Home Depot. Beginning with a brief description of the art of stenciling, you are then shown the materials you will need to proceed. Next, you are shown how to prepare your room and surfaces. The goal will be to use a single stencil in multiple positions. The stipple method of application is stressed to achieve a multi-dimensional application. Two colors are used to give the added dimension of shadow to the i...

Check out this informative video tutorial from Apple on how to do more with the Sidebar in the Mac OS X Finder. Learn about the Sidebar devices, the Sidebar shared, the Sidebar places, and the Sidebar search for. Mac OS X. It's what makes a Mac a Mac.

Check out this informative video tutorial from Apple on how to use the basics of the Mac OS X Finder. Learn about the Finder basics, the Sidebar, view buttons, and Quick Look. Mac OS X. It's what makes a Mac a Mac.

Check out this informative video tutorial from Apple on how to organize your Mail in Mac OS X's Mail. See how to sort messages with rules, create smart mailboxes, and comlpletely organize your mail. Mac OS X. It's what makes a Mac a Mac.

Check out this informative video tutorial from Apple on how to use the basics of Mac OS X Mail. See how to set up mail with your email accounts, compose messages, add attachments, view attachments with Quick Look, and search through Mail. Mac OS X. It's what makes a Mac a Mac.

Check out this informative video tutorial from Apple on how to use Mac OS X Mail to its fullest. See how to filter out junk mail, use data detectors, and view RSS feeds in Mail. Mac OS X. It's what makes a Mac a Mac.

Right out of the box, iPhone is incredibly easy to use. If you want to get the most out of every feature, you’ve come to the right place. This video tutorial straight from Apple will teach you how to use the keyboard on the Apple iPhone 3G. The iPhone redefines what a mobile phone can do.

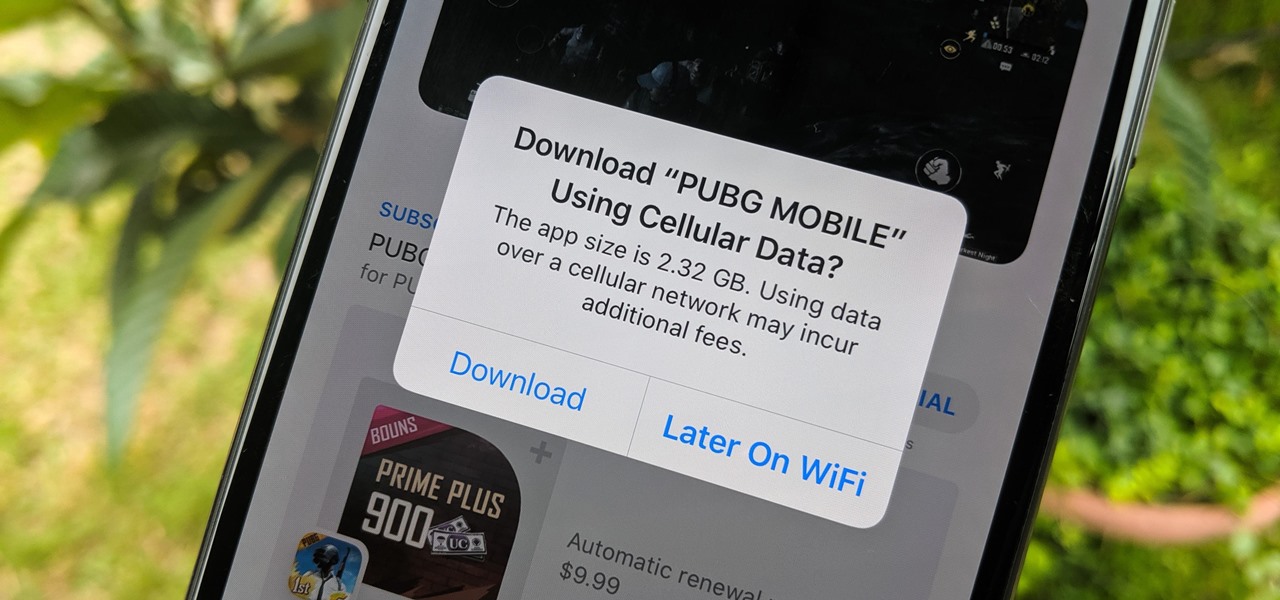
When there's a new game you want to play or app you need to use, but a Wi-Fi network isn't available, you can always download it over cellular data. If the size of the app is too large, however, you may not be able to on your iPhone. But that changes in iOS 13, which finally gives control over cellular data downloads in the App Store.

Nmap is more powerful than you know. With a few scripts, we can extend its functionality beyond a simple port scanner and start to identify details about target servers sysadmins don't want us to know.

Despite the launch of ARKit a year ago, and ARCore this year, a true killer app has not arrived for either platform, that's according to the head honcho for one of the leading development environments for 3D applications.

Know thy enemy — wise words that can be applied to many different situations, including database hacking. It is essential to performing adequate reconnaissance on a system before even thinking about launching an attack — any type of attack — and this is no different for SQL injection.

Even though HIV rates declined 18% between 2008 and 2014, 1.1 million people in the US are living with the infection. Part of that is because HIV is treatable, but not curable.

German groups ZF Friedrichshafen AG and HELLA are collaborating to add to their autonomous portfolios with camera and radar development.

Researchers are putting driverless shuttles on campus next year at the University of Michigan and the rides are free for students and teachers.

Stakeholders in the driverless industry are anxiously awaiting changes the US Department of Transportation (DOT) is making to self-driving vehicle guidelines.

The US Department of Transportation says it is actively completing a previously promised revision of voluntary guidelines for driverless vehicles originally drafted by President Obama's administration.

Waymo has done a lot of things over the course of their driverless journey, but their solution to little birdies pooping all over a self-driving car's LiDAR system is definitely our favorite.

Volvo is joining the autonomous vehicle race. In a video released Tuesday, the company showed off its concept for a driverless garbage truck, adding themselves to a growing list of manufacturers pledging to work in the self-driving field.

The east coast is becoming a hotbed for driverless. Sure, the west coast has all of its fancy tech companies testing self-driving cars, but we've got the goods too. Uber has brought the technology to Pennsylvania and will soon do the same in Toronto. (Stratford, Ontario, has plans to test out driverless too!) And today we got some great news: Governor Andrew Cuomo just approved of driverless testing in New York.

As much as you try to safeguard your personal information, you may have made a small mistake by giving your phone number to the wrong entity, and now you're being bombarded with dozens of spam calls every day. To help parse your call log and reject the proper numbers without answering or trudging through voicemail, a good reverse phone lookup app is needed.

Apple staff will be put through their paces now that the company's "Automated System" for driverless cars is in motion.

Download a popular, legit app from the Google Play Store. Decompile it. Add malicious code. Repackage the app. Distribute the now trojan-ized app through third-party Android app sites. This is how advertising malware Ewind, what Palo Alto Networks calls "adware in applications' clothing," infects Android users.

Upskill, an enterprise software developer for industrial augmented reality applications, recently received an influx of funding and a major vote of confidence from two of their top customers.

When we talk about driverless technology, the go-to companies are usually Waymo, Uber, or Tesla. However, traditional automakers like Ford and GM are also staking claims to the driverless and advanced driver assistance spaces.

At the moment, it would be safe to say that demand for devices running Tango, Google's augmented reality smartphone platform, is relatively low among consumers. Kaon Interactive, a B2B software company who has built more than 5,000 interactive applications for use at trade shows, remote sales demonstrations, and other customer engagements, is betting that there is a market for the devices in sales and marketing.

Uber resumed its pilot program for driverless cars after one of its autonomous vehicles crashed in Tempe, Arizona last weekend.

The modern age of techno-dating has made an interesting landscape for social interactions when there is some modicum of romance (or lust). For those of us born before the internet evolved into the prolific monster it has become, we first met our love interests face to face. Today, however, apps like Tinder have changed the introductory stage, for better or worse.

Facebook Messenger is getting ready to roll out a Snapchat-esque feature that will let users send messages that self-destruct after a certain amount of time, so you'll have an extra level of security when you need to send sensitive financial information or, more likely, risqué texts or images.

Hello everyone. I've recently made the annoucement of the Null Byte suite of tools, and we've covered how to download and install it. Now it's time we cover how to submit a tool for inclusion into the suite. It's relatively simple, but we need to get a few ground rules out of the way.

Welcome back, my tenderfoot hackers! In this series, we are exploring the myriad of ways to hack web applications. As you know, web applications are those apps that run the websites of everything from your next door neighbor, to the all-powerful financial institutions that run the world. Each of these applications is vulnerable to attack, but not all in the same way.

As a Mac and Sasmsung Galaxy S6 user, I quickly realized that the two devices don't play well with one another out of the box, and using ADB commands to record my Android's screen isn't as simple as it is would be with a Windows PC.

While screenshotting a received Snapchat has never been a hard thing to do, saving one without being noticed is a completely different story. Previously, you would have to have either a rooted Android or jailbroken iOS device to save one of those self-destructing messages undetected, but one particular app has opened this trick up to the masses.

Welcome back, my aspiring hackers! Many of you have installed Kali Linux as a virtual machine (VM) using VMware or VirtualBox, while others have installed Kali (or BackTrack) in a dual-boot system. The drawback to installing these hacking systems as a VM is that it then requires an external wireless adapter (your wireless adapter is piped through the VM as a wired device, eth0), but it makes for a great place to test your hacks while honing your skills.

As this generation continues to evolve, we become more involved with social media. For example, you may have a Facebook, Twitter, and a Google+ account, and be heavily involved in using all three, but the constant switching between sites, logins, and conversations can get very tedious.

Humans in general are great at keeping things about themselves private, from feelings to personality traits. While smartphones and social networks are making these secrets more open, narcissists have and always will love being out in the open with everyone's attention on them.