Ever wonder how all of those tiny chips and components can fit inside your laptop or smartphone? If you tried to squeeze them in there yourself, your laptop would quickly become too heavy for your lap, and your mobile phone would need wheels to stay mobile.
In this series on weaponized lasers, I'll be exploring the function, operation, strength and building instructions for three basic laser weapons; CO2, Diode, and Flashlamp. These laser types are just a few of many, selected because of their simplicity and basic construction (depending on your experience).

This is the third part of my electromagnetic pulse series (see Part One and Part Two). By now, I've covered the hardware and general concept of electromagnetic pulse generators, but how exactly do they disable electronics? How can an invisible field of energy have such a catastrophic effect on computers, cell phones, and most any other electronics? I'll be answering all these questions in part three of Making Electromagnetic Weapons.

Nikola Tesla In my opinion, one of the most neglected inventors of all time. The names Edison and Marconi come to mind as familiar, but Tesla? Most think of a car. Few know that Tesla is responsible for alternating current, florescent lights, radar, remote control, generators that preform efficiently, the spark plug, and many others. The U.S Supreme Court declared in 1943 that Tesla, not Marconi, was the true inventor of the radio.

Snapseed is a highly regarded and award-winning photo-editing app for iOS devices. Originating out of image manipulation specialist Nik Software in San Diego, Snapseed is Apple’s iPad App of the Year and, after using it for the purposes of this review, I believe it points to the future of image editing.

Welcome to Minecraft World! Check out our advanced tutorials and come play with us on our free server.

Halloween will be here in just over a week, which means next week these Scrabble Bingo of the Days will become more horrific. This week, there's just a few relevant Halloween seven-letter words for your Scrabble vocabulary, referencing witchcraft and one of the eeriest horror movies of all time, The Thing (not this year's version).

This week seems to have gone by in a flash. Maybe it was the three day weekend, but I don't think it accounts for the flurry of activity I've been seeing on Google+. Updates, debates, and new initiatives are unfolding every day, and the best part is that most of them are coming from outside of Google. People love Google+ so much that they want to evangelize to others about it. What more could Google+ ask for?

Since its release three years ago, Canon's EOS 5D Mark II has been the most sought out digital SLR for photographers everywhere. But it's also becoming a favorite amongst cinematographers, thanks to its compact size and high-def video recording mode, seeing action in everything from independent features to Hollywood blockbusters and even big network TV shows.

Facebook games are ostensibly all about connecting their players. Yet, in many ways they exist on an isolated island. That's one of the reasons traditional gamers and game franchises have avoided Facebook in the past. And all of the breakout hits so far on Facebook have been cheap PC game ripoffs from the 90s, like FarmVille and ports of other popular casual games.

In Google definitions a macro is defined as "a single computer instruction that results in a series of instructions in machine language". Basically a macro is a programming script that tells the computer what to do. You can tell a computer (via a macro) to move a mouse, click, type or do any task that a computer can do with automation. There are also many (primitive) computer viruses that are coded entirely in a macro script. There are many ways to create a macro script but I will only go ove...

Are you interested in selling your products at the local Farmers Markets? Many small mom and pop food crafters get started selling their artisan breads, homemade cakes, cookies, pies, biscotti, candy, seasoning mixes or regional barbecue sauces direct to customers who visit local farmers markets and farm stands. What better way to start than with those visiting the local farmers market; a captive audience expecting a wide variety of seasonal fruits and veggies; along with specialty products t...

Wondering why your inbox is looking a little threadbare? It may be that you've violated a few unwritten rules of email etiquette. Here are a few basic tips that the web-savvy know by heart.
Proposition 22 Prohibits the state from borrowing or taking funds used for transportation, redevelopment, or local, government projects and services. Initiative constitution amendment.

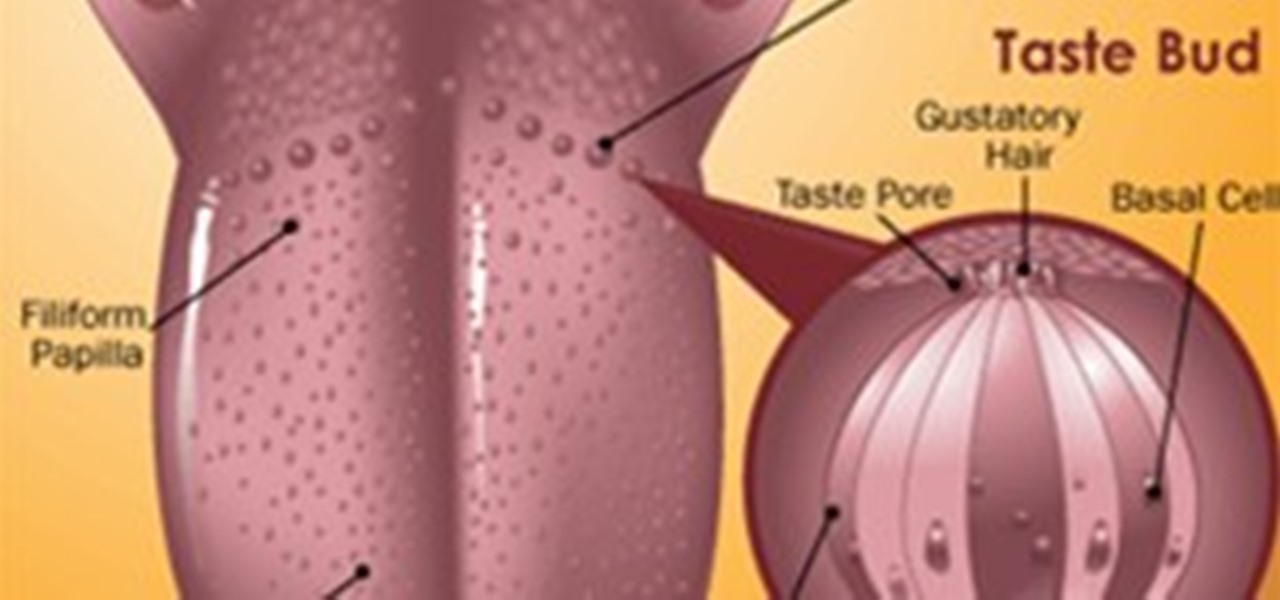
I have looked into this several times because I find it interesting to think about how the tongue works when making a recipe. I say "looked into" it because I wouldn't really describe it as research. How the flavors are going to be perceived can affect how you might want to layer the flavors in your dish. This information mostly comes from an artical in How Stuff Works website. There are several parts of the tongue that you need tobe familiar with when you study it.

Week 01 : 9/31 - 09/06 Read Chapters 1-2 of Creating Motion Graphics with After Effects
There's gonna be a rumble.... For this week's GJ article, I thought I would jump right into talking about a mortal-lock favourite of mine: West Side Story. If you haven't seen it (and a lot of folks havent - dudes especially) and you want a lesson in filmmaking craft from a bonafide master then you kind of owe it to yourself to rent this undisputed gem.

The SCRABBLE Brand trademark has been around since 1948, but video advertisements for the popular board game didn't appear until the start of this millennium. Although there may be a few SCRABBLE video spots out there that predate 2000, I haven't come across them.

Not long ago in Rome during a Master’s Tennis Tournament something remarkable happened. In a tightly contested game, American Andy Roddick challenged a linesman’s call on a ball hit by his opponent. The remarkable thing about this incident was that Roddick argued against his own interest. He insisted that the opponent’s ball had landed inside the line and that he, Roddick, should NOT be awarded the point. Spectators applauded as if they’d witnessed a miracle. Imagine! Sportsmanship in a profe...

At the beginning of every class, or almost every class, we do a series of exercises. The Japanese word for this sort of calisthenic exercise isundo. These exercises derive from the Goju style of karate created by Miyagi Sensei in Okinawa in the early part of the 20th Century. In devising these exercises Miyagi no doubt borrowed liberally from the Chinese, whose influence on the southernmost island of the Japanese archipelago was immense.

Have you ever gone on a long internet binge, researching and surfing mindless things, and thought to yourself: I wish I could make some money surfing the internet and sharing the (sometimes useless) information I had just acquired? Well, now you can!

Although the enterprise use cases for the Microsoft HoloLens 2 continue to impress, the arts community just can't stay away from the best augmented reality headset on the market.

We usually focus on augmented reality here, but when something important in VR happens, we highlight it as part of the overall immersive computing story.

The fight to wrest control of apps from Apple's revenue-focused grip just took a major turn in favor of Epic Games.

The beauty industry has increasingly relied on the powers of augmented reality to drive sales in recent years, and now that virtual "everything" is on trend due to the pandemic, yet another big player is entering the fray.

The ability to browse the web in coffee shops, libraries, airports, and practically anywhere else you can imagine is more than convenient, but convenience has risks. Using public Wi-Fi allows others to spy on you easily. Even your own internet service provider can see every website you've ever visited. Don't fall into the trap of protecting your identity, data, and devices after it's too late.

The modern remote workforce faces many challenges, but perhaps none is greater than organizing calls and syncing tasks. Many platforms are convoluted and difficult to manage. Team members get bogged down by administrative tasks instead of staying productive.

It looks as though the novel coronavirus and social distancing guidelines are here to stay for a while. So companies of all sizes and industries are scrambling to adapt to a new reality in which everything from morning meetings to large-scale presentations are done entirely online. It looks like this is going to be the new normal for the foreseeable future.

It is well documented that what you say and do online is tracked. Yes, private organizations do their best to protect your data from hackers, but those protections don't extend to themselves, advertisers, and law enforcement.

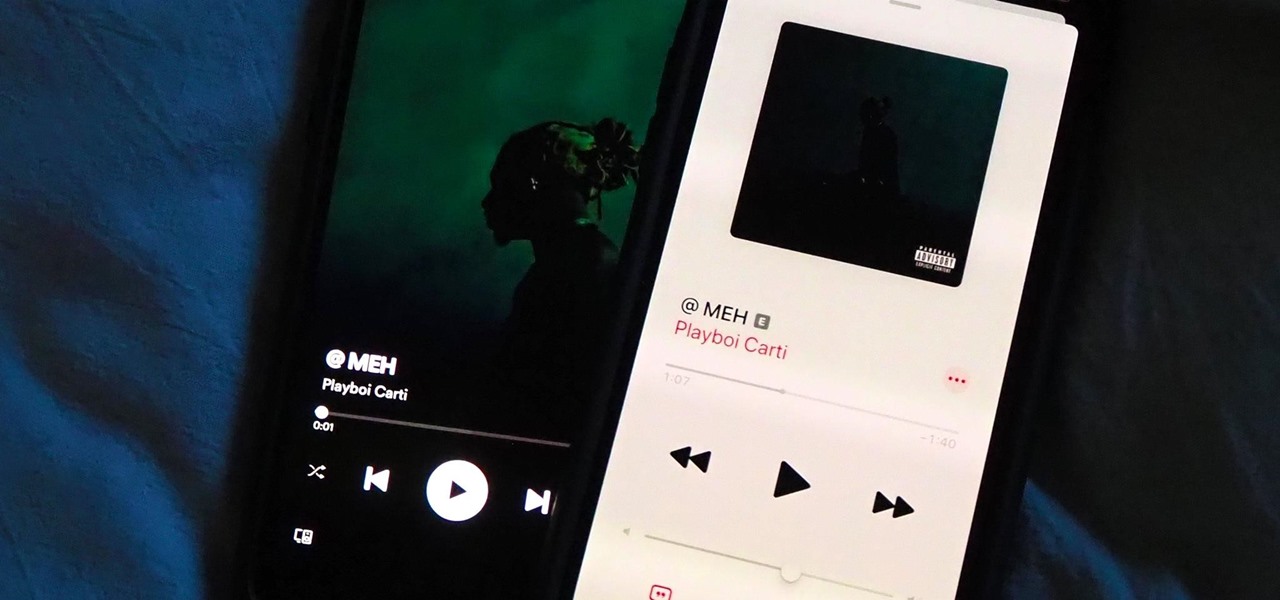
To share a song or album to family and friends, it's as easy as copying its link in the app and pasting that into a message. However, not everyone uses the same music streaming service, so a link to an Apple Music song won't do a Spotify, Tidal, Pandora, Deezer, or YouTube Music subscriber any good. If you're on an iPhone, though, there's an easy way to convert links from one service to another.

With more digital content than ever, the search feature on smart TVs is essential. But typing is such a terrible experience when you're forced to use voice dictation or peck around with the remote control. Thankfully, there's a better way.

People use browsers for all types of things, and in general, we trust a lot of personal information to them. That's why browsers are a perfect attack surface for a hacker, because the target may not even know they are infected and feed you all of the information you could want.

A modern iPhone is capable of running sophisticated, exquisitely-rendered games that rival titles on current-generation consoles. However, there is some value in classic video game titles, whether you grew up playing games on the Atari 2600, Nintendo Entertainment System, and Sega Genesis or not.

Every Galaxy S20 sold in the US — even the S20+ and S20 Ultra — simply can't be rooted. With the bootloader permanently locked, you miss out on the world of rooting and the customization it opens up, but modifications are still possible.

Whether you're trying to become an influencer or just want to share better photos and videos, the best camera to start with is your smartphone. It is likely the only camera you always have on you and it's probably capable of excellent pictures and video capture. But with a little help, it could definitely be better.

Web application firewalls are one of the strongest defenses a web app has, but they can be vulnerable if the firewall version used is known to an attacker. Understanding which firewall a target is using can be the first step to a hacker discovering how to get past it — and what defenses are in place on a target. And the tools Wafw00f and Nmap make fingerprinting firewalls easy.

SMB (Server Message Block) is a protocol that allows resources on the same network to share files, browse the network, and print over the network. It was initially used on Windows, but Unix systems can use SMB through Samba. Today, we will be using a tool called Enum4linux to extract information from a target, as well as smbclient to connect to an SMB share and transfer files.

In our comparison of the best gaming phones in 2019, the winner actually surprised us. A phone that most people don't know about from a brand you probably haven't heard of ended up as the clear winner. But how? Well, it ticked so many flagship boxes despite its midrange price tag.

Phishing is the easiest way to get your password stolen, as it only takes one mistake to log in to the wrong website. A convincing phishing site is key to a successful attempt, and tools to create them have become intuitive and more sophisticated. SocialFish allows a hacker to create a persuasive phishing page for nearly any website, offering a web interface with an Android app for remote control.

Since the Razer Phone's announcement in 2017, we've seen a new subgroup of phones emerge. Gaming phones are now a thing, leading to companies like ASUS creating phones that are thoroughly optimized for the mobile gaming experience. And with their second iteration, they perfected it.