You want to look like the picture of perfection on your wedding day, right? But let's face it: Weddings are super expensive to hold, and that's not even taking into consideration your dress, hair, and makeup.

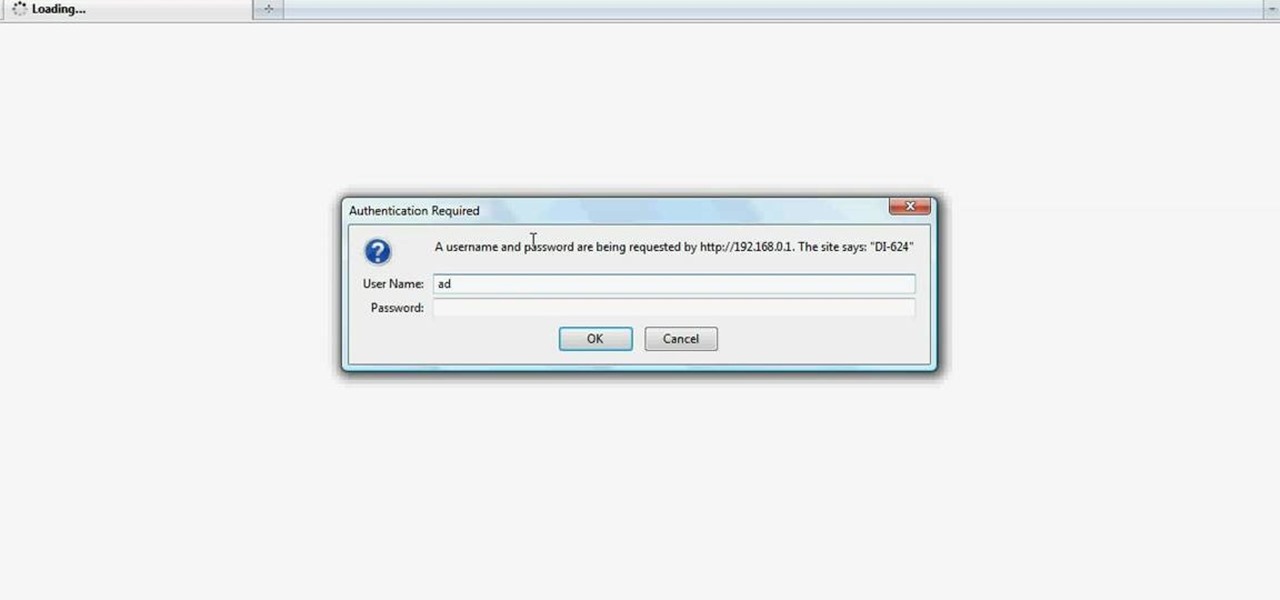
Want to test the security of your WEP WiFi wireless network? In this clip, you'll learn how to use the Backtrack Linux distro and the Aircrack-ng WiFi security app to crack a WEP key. The process is simple. For more information, including step-by-step instructions, and to get started testing the security of your own WiFi networks, watch this hacker's how-to.

In this clip, you'll learn how to use the BackTrack Linux distro and the Aircrack-ng WiFi security app to hack a WEP network. The process is simple. For more information, including step-by-step instructions, and to get started testing the security of your own WiFi networks, watch this hacker's how-to.

In this clip, you'll learn how to use the Backtrack 3 Linux distro and Aircrack-ng WiFi security app to crack the password to a WEP-protected wireless network. The process is simple. For more information, including step-by-step instructions, and to get started testing the security of your own WiFi networks, watch this hacker's how-to.
Interested in setting up a WiFi network in your home or office? This brief video tutorial from the folks at Butterscotch will teach you everything you need to know. For more information, including detailed, step-by-step instructions, and to get started configuring your own wireless network, take a look.

A wheel bearing doesn't have to be a costly fix for the mechanic. It could be a relatively cheap repair job for all you do-it-yourselfer types. There are different types of wheel bearings, but the type explained in this video, on a 1991 Ford Explorer, is a self-contained all-in-one assembly. If you have a '91 Ford Explorer, or a different vehicle with this kind of wheel bearing, then you're in luck… watch and learn.

Follow your dreams. That's the best advice anyone can give you, and Chief Ninja Padraig Hyland tells you just that with this motivational video.

In this video tutorial, viewers learn how to do an arresting technique for handling and restraining. As the opponent begins to punch you, grab the opponent's wrist with one hand. Then push the other arm under the opponent's bicep and under the armpit. Now pull the opponent towards you and push their arm to their back. Make sure you grab over the opponent's hand. Then use your knee to push against and opponent's hamstring and pull down their shoulder to throw them down on the floor. Continue l...

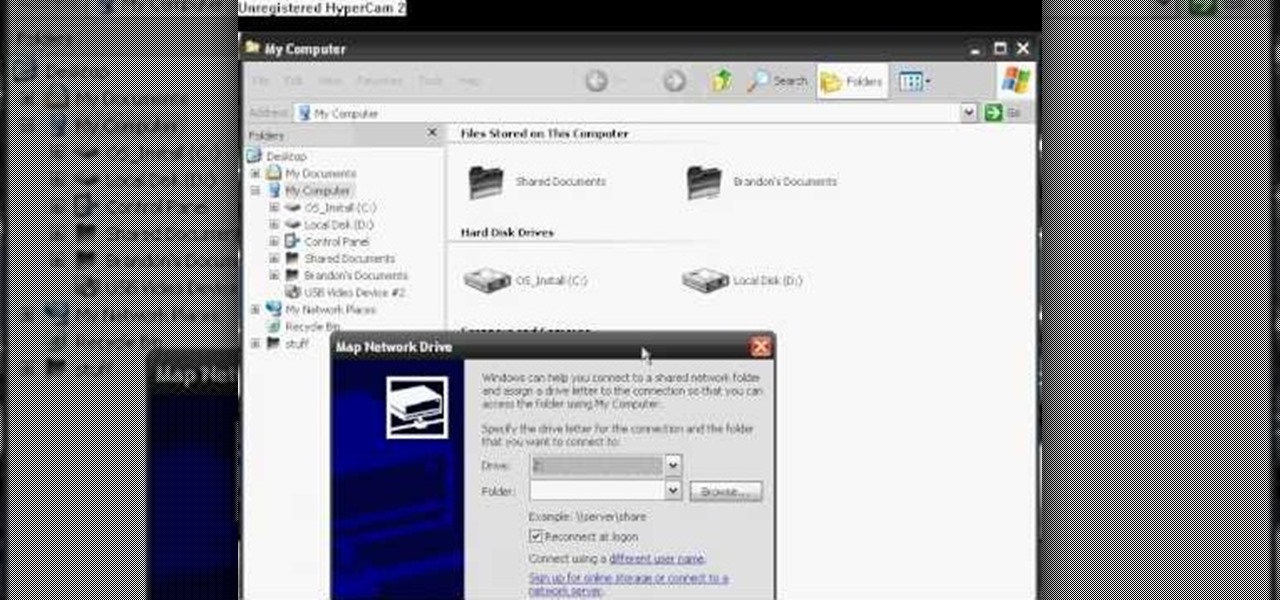
In this tutorial, we learn how to map network driers from a remote server. First, go to run on your start menu, then type in the id address or server name for what you want to access and press enter. Now, right click on the folder you want to map and click on map network drives. Choose any letter you want from the drop down menu, then click next to the "reconnect on logon" text. Click on the finish button, then open your newly mapped network drive from your computer. You can do this for any s...

In this video tutorial, viewers learn how to do the major outside foot reap in judo. This task is very easy, simple and fast to do. Begin by grabbing onto the opponent's arm and shoulder. Then step in towards the opponent and pull the opponent towards you. Now bring out your leg and sweep the opponent by push back their leg. This can be done on either right or left side. This video will benefit those viewers who are interested in martial arts and self defense, and would like to learn differen...

In this video tutorial, viewers learn how to do a Kyokushin/kickboxing low kick combination. Begin by making a low kick to the opponent's inner thigh and instantly punch/push to make distance. At the same time, position yourself to the opponent's side. Then perform a low kick on the opponent's front upper leg. Bend your knees when kicking for more power and prevent your opponent from closing in. This video will benefit those viewers who are interested in learning martial arts and self defense...

Learn how to create & secure applications with BIG-IP v10. Whether you're new to F5 Networks' popular network appliance or are a seasoned administrator just looking to better acquaint yourself with BIG-IP, you're sure to benefit from this free video software tutorial. For more information, including detailed instructions, take a look.

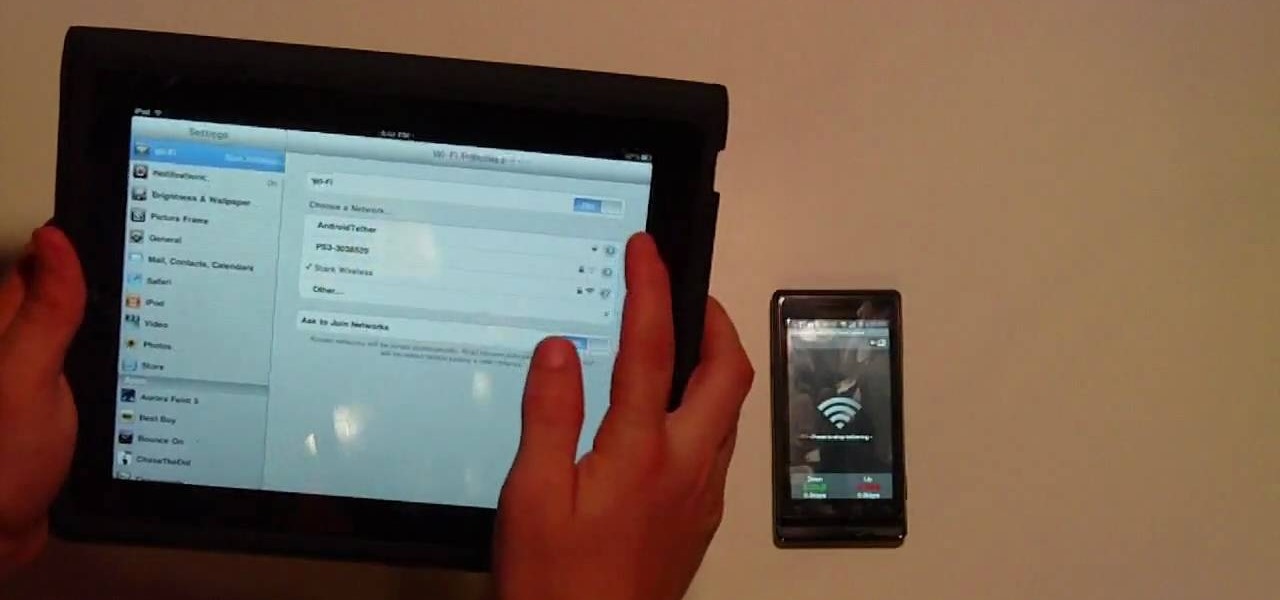
In this Electronics video tutorial you will learn how to tether a laptop to a Droid Smartphone for free Wi-Fi. For this you will need the android wifi tether application. Download the version for your device from here and install it. Then launch the app and press the icon to start tethering. In your laptop, go to settings and then to wi-fi. You will see a new network called android tether. Connect to the network and you will see that it works. As with any other network, you can change the nam...

This tutorial will walk you through the steps you need to map a network drive for file access in Windows XP. By mapping your network drive you will be able to store and access files offsite and make computing easier all around.

In order to prepare Cappuccino with your home espresso machine, you will need the following: milk, coffee, an espresso machine. Fill steamed milk container 2/3 full of milk. Submerge the milk underneath the spinner, before you turn it on. Allow it to steam the milk, until it is warm and frothy. Keep an eye on it, judging the consistency for your self. Remove, when the milk is warm and frothy. Turn the machine off, before you remove the cup. Clean your wand.

Want to set up a wireless network in your home or office? It's simple. So simple, in fact, that this free networking how-to presents a complete overview of the process in just over four minutes. Set up a WiFi network with this video guide.

Watch this video and learn how to protect your identity on the internet. This clip will help you learn how to blur out your face and alter your voice when posting videos on the web, where your identity is an important secret. Stay anonymous while portraying your opinions. This software can also be used to avoid release issues with strangers in the backgrounds of your videos. Preventing passers by from having there picture posted with your opinions opening you up for legal action. This can als...

The self-proclaimed "Flower God" was shopping the other day when he came across a vase that he could not resist purchasing. He shows us how to create a beautiful flower arrangement. He works with two different heights: a high plain and a low plain. He wires up some flowers so that they hold their shape better, clustering them down at the bottom. He then accents the low section with some Japanese Lanterns which project outward from the lower section. Next come the flowers for the height, tall ...

In this flash tutorial the instructor shows how to create a custom cursor. This is created using shapes and simple Action Scripts. First open the flash tool and create a simple shape. Then convert the shape in to a movie clip and add simple animation to it where it switches colors. Now create a new layer and add Action Script code as shown in the video. This Action Script code is a command to make the shape follow the cursor. Now the shape follows the cursor as the cursor moves and appears as...

In this tutorial the instructor shows how to convert a improper fraction to mixed number. In the example the instructor takes the denominator of the mixed fraction and writes it beside and keeps adding it self to the latest number and he keeps on doing that way generating a series until he reaches the value of the numerator. Now he counts the number of occurrences of the numbers in the series before the value of the numerator which gives the value of the whole number in the mixed fraction. No...

This lynda.com video tutorial shows how to use container fields with FileMaker Pro 10. When you want to create fields in FileMaker database you have the choice on what kind of fields you want to make. Many general fields are self explanatory like text, date etc., but there is a special kind of field called the container field. FileMaker Pro container field is a versatile data type in that it can store any kind of binary data. Container fields can be used to hold binary data in four broad clas...

Oftentimes female style and tradition in the Middle East leaves little room for self-expression. This is where makeup comes in. Women covering their heads and bodies can personalize their look by applying dramatic makeup to their faces. Check out this tutorial and learn how to create a beautiful, exotic makeup look. This look is dramatic and inspired by the beauty of the Middle East. It is not difficult to accomplish if you follow along with the step by step. Start enhancing that lovely face ...

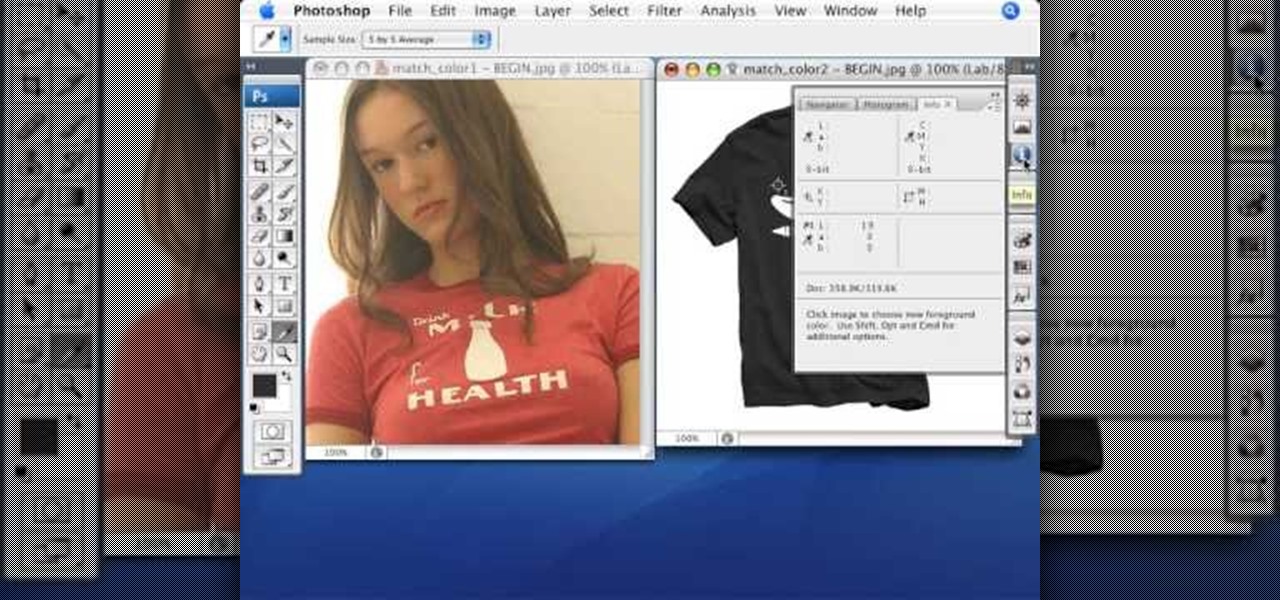
Match the color of objects on Photoshop. Take a picture of your self of one shirt that the shirt is on different color mean while choose the black tea shirt because it the traditionally one of the harder colors, change the image mode to the lab color for both images then use eyedropper tool and expose the info pallet select the neutral part of the image i.e. red. Hold down shift then we can see the icon changes then add contrast to it by hue saturation present in the layer pallet.

Do your presentation skills need a little work? Being in front of a crowd or some potential clients may be one of the hardest things you will ever do, but staying confident makes all the difference. Losing any bit of confidence will result in your presentation falling flat and killing your self-esteem, and perhaps even risking your job. So, being confident is a must.

EFT "tapping" is a self helping movement in a sequence of tapping across the hand, face, head, chest and arm that will allow you to alleviate a specific pain, problem or stresses in your life. This video shows you how to tap away your problems with acupressure.

Learn all there is to learn about yarn from Naztazia... watch this video tutorial to learn how to crochet spiral scrubbies with a pattern.

Learn all there is to learn about yarn from Naztazia... watch this video tutorial to learn how to crochet a Tunisian stitch or Afghan stitch.

Practice the left hook and jab/hook combi in boxing. These are basic and beginner techniques you must master to compete in the ring.

See how to choose a tattoo that’s right for you. A tattoo is forever – unless, of course, you want to go through the pain and expense of removing it. So think long and hard before you get one!

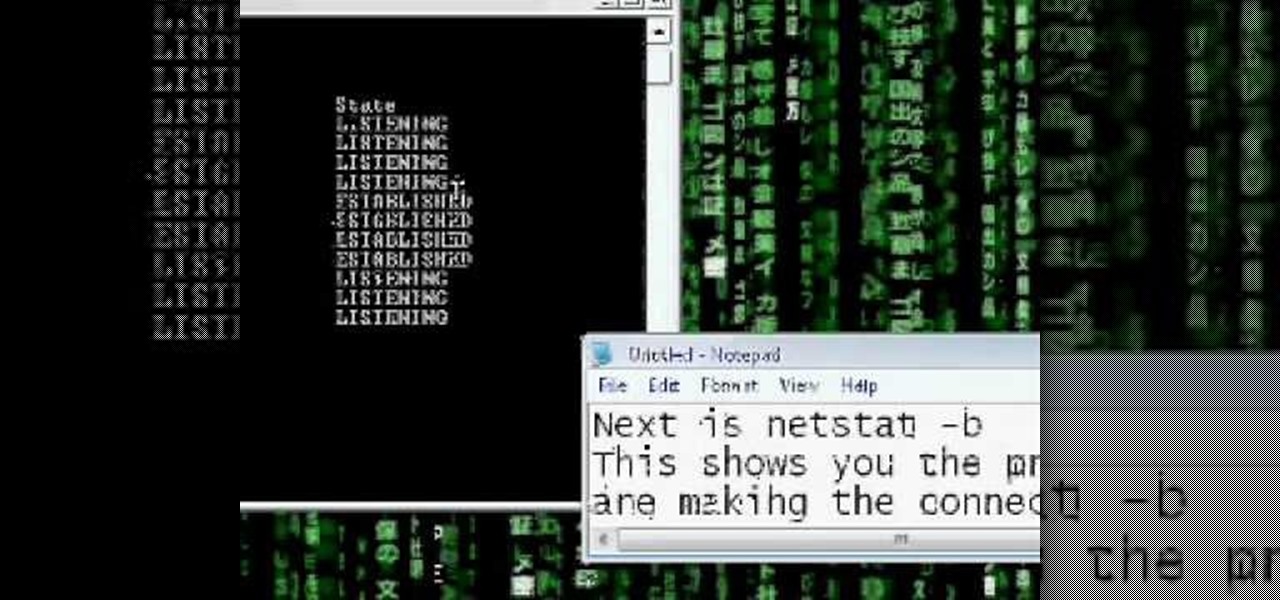
Netstat (network statistics) is a command-line tool that displays network connections (both incoming and outgoing), routing tables, and a number of network interface statistics. It is available on Unix, Unix-like, and Windows NT-based operating systems. This video tutorial presents a basic introduction to working with the netstat tool. Determine whether you've been hacked with this how-to.

Those born under the Taurus sign need to be handled with kid gloves. To trap a Taurus you will need a loyal nature, a strong sense of self image an a respect for money. Take the tie to look extra special for your Taurus since they pay particular attention to appearances. Learn how to use astrology advice in dating, by watching this how-to video. Pick up astrology tips on making a relationship with a Taurus work.

In the 3rd episode of thebroken Kevin and Dan show how to mod the original XBOX, the PS2, and the Gamecube. But the show kicks off with a couple 40z and some easy tips on how to crack windows passwords. Ramzi busts out with his best hacker tip yet, a self-destructing laptop! and what's it like for a hacker in jail? Kevin gets the details as he chats up hacker 1, Kevin Mitnick.

So you know how to setup a network in your home, but how do you go wireless? The Lab Rats, Andy Walker and Sean Carruthers show you how to setup a wireless (WIFI) network.

forget that half assed human foosball, this is the real deal. set up a giant foosball game- strap your selves to some kind of revolving polls to flip you upside down like real foosball; throw in some balls filled with nasties (dog anal gland juice is the most foul smelling substance known to man) and let the game begin!

This video tutorial is in the Computers & Programming category where you will learn how to secure your wireless internet connection. If you don't secure your wireless internet connection you are allowing others to enter in to your network. Open the set up CD and first change the network name from the default name to anything that you like. For this go to step 3 of 'naming your network', type in your network name and click 'next'. Then you enable security on the network by choosing 'WPA2'. Nex...

Since its release three years ago, Canon's EOS 5D Mark II has been the most sought out digital SLR for photographers everywhere. But it's also becoming a favorite amongst cinematographers, thanks to its compact size and high-def video recording mode, seeing action in everything from independent features to Hollywood blockbusters and even big network TV shows.

Although early attempts at consumer smartglasses have employed trackpads and handheld or wearable controllers for user input, its the gesture control interfaces of the HoloLens 2 and the Magic Leap One that represent the future of smartglasses input.

You may not know it, but the IPv4 address of your computer contains tons of useful information about whatever Wi-Fi network you're on. By knowing what your IPv4 address and subnet mask are telling you, you can easily scan the whole network range, locate the router, and discover other devices on the same network.

When it comes to attacking devices on a network, you can't hit what you can't see. Nmap gives you the ability to explore any devices connected to a network, finding information like the operating system a device is running and which applications are listening on open ports. This information lets a hacker design an attack that perfectly suits the target environment.

SSH is a powerful tool with more uses than simply logging into a server. This protocol, which stands for Secure Shell, provides X11 forwarding, port forwarding, secure file transfer, and more. Using SSH port forwarding on a compromised host with access to a restricted network can allow an attacker to access hosts within the restricted network or pivot into the network.