
How To: Do basic moves in women's self defense
In this video series, learn some basic self defense moves for women. Our expert, Chemin Allderdge, is a third degree black belt that specializes in teaching self defense classes for women.


In this video series, learn some basic self defense moves for women. Our expert, Chemin Allderdge, is a third degree black belt that specializes in teaching self defense classes for women.

In this video series, watch as health specialist Carolyn Waygood teaches how to give a partner self breast exam. Learn the different techniques for self checking your breast for tumors, how to give a male on female breast exam, a female on female breast exam, breast physiology, tools used to give breast exams, and ways to make breast exams fun for couples.

In this video series, our expert Tres Tew will tell you all about self defense using a knife including how to select the right knife, basic knife fighting moves, and how to defend yourself with a knife. he will also show you how to defend against a downward stab, a strait stab, a downward slash, an angled slash, and a cross slash.

For preschoolers a rhyming song with hand movements. Singing songs with your child is wonderful for many reasons. The most important reason is that singing is it is fun and children love to sing. Songs are great for increasing vocabulary and pronunciation. Using hand and body movements with songs and rhymes helps preschoolers learn to control their bodies. There is even research that has shown that children who are actively involved in music do better in reading and math when they start schoo...

Ever wanted to know how to disable an attacker? The trick to getting away from an assailant – even one who's bigger and stronger than you are – is to hit 'em where it hurts.

If you haven't had a pile of pipe and fittings to play with before, it's hard to see what is so cool about a plain, plastic pipe. All it does in the house is carry the poop away. Really, who cares?

Giveaway Tuesdays has officially ended! But don't sweat it, WonderHowTo has another World that's taken its place. Every Tuesday, Phone Snap! invites you to show off your cell phone photography skills.

West LA Seido Karate-do embeds its personal protection program into its on-going classes. Private instruction in this aspect of Seido can also be arranged with Kyoshi on an individual basis.

Does your network begin to crawl right around the time your sinister-looking next-door neighbors get home from work? Do you harbor suspicions that one or more of them may be stealing your Wi-Fi? It's easy to find out. And equally easy to give freeloaders the boot. In the guide below, we'll show you how to secure your wireless connection in three easy steps.
A macOS computer can reveal a lot of information about the owner, including which Wi-Fi network they have permission to access. With an Arduino-based attack, we'll use a five-dollar setup to inject a rogue Wi-Fi network and steal the list of trusted Wi-Fi networks, allowing us to see where the computer has been.
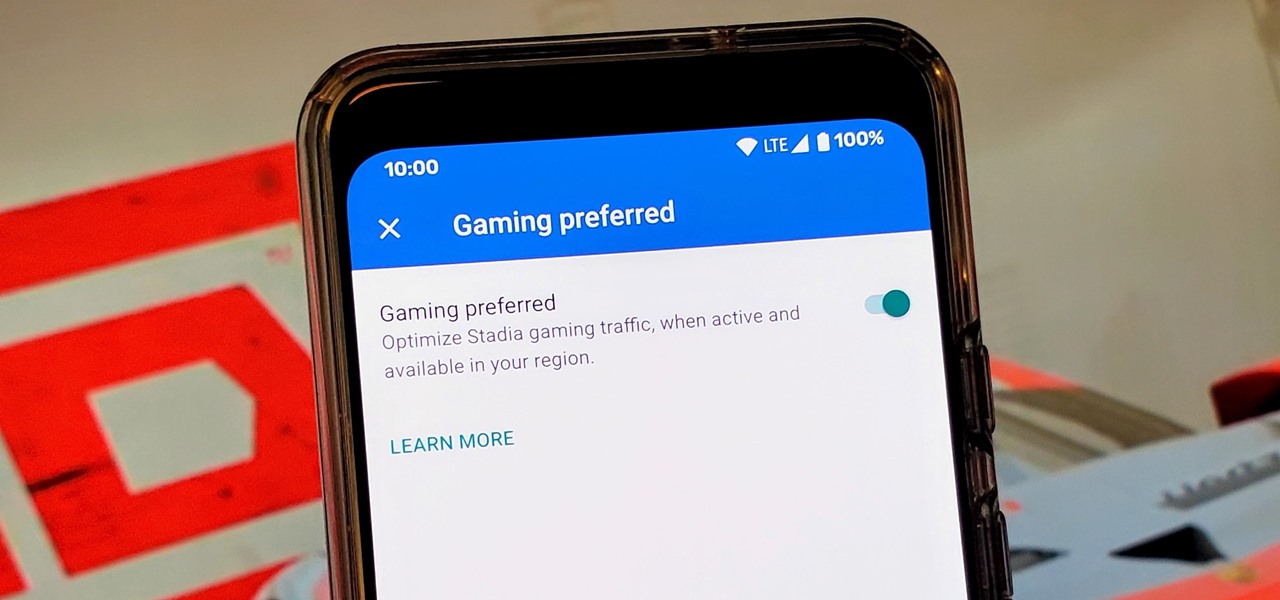
Although not quite as common today with the always-connected world we live in, you still might be having bandwidth wars in your home right now. If the internet connection in your area is mediocre, you know the feeling well. Google Stadia recommends having a 25 Mbps connection for playing in 4K, so you can expect to need at least that much to maintain a smooth, high-quality gaming session.

Just like Apple and Google, Facebook has been working to develop computer vision shortcuts designed to give mobile apps augmented reality superpowers.

It's common for IoT devices like Wi-Fi security cameras to host a website for controlling or configuring the camera that uses HTTP instead of the more secure HTTPS. This means anyone with the network password can see traffic to and from the camera, allowing a hacker to intercept security camera footage if anyone is watching the camera's HTTP viewing page.

Cracking the password for WPA2 networks has been roughly the same for many years, but a newer attack requires less interaction and info than previous techniques and has the added advantage of being able to target access points with no one connected. The latest attack against the PMKID uses Hashcat to crack WPA passwords and allows hackers to find networks with weak passwords more easily.

Wi-Fi tools keep getting more and more accessible to beginners, and the LAZY script is a framework of serious penetration tools that can be explored easily from within it. This powerful and simple tool can be used for everything from installing new add-ons to grabbing a WPA handshake in a matter of seconds. Plus, it's easy to install, set up, and utilize.

Electronic warfare tactics work by jamming, disrupting, or disabling the technology a target uses to perform a critical function, and IoT devices are especially vulnerable to attacks. Wireless security cameras like the Nest Cam are frequently used to secure critical locations, but a hacker can surgically disable a webcam or other Wi-Fi connected device without disturbing the rest of the network.

The next frontier for AR hardware is the consumer headset, and tech companies of varying size and tenure are working hard to strike the right mix between comfort, cool factor, and cost. How these companies handle the hype and flow of information vary wildly.

Networking is built largely on trust. Most devices do not verify that another device is what it identifies itself to be, so long as it functions as expected. In the case of a man-in-the-middle attack, we can abuse this trust by impersonating a wireless access point, allowing us to intercept and modify network data. This can be dangerous for private data, but also be fun for pranking your friends.

Not only has there been difficulty finding consensus on a name for driverless, autonomous, self-driving, or automated vehicles, there is also the issue of what we actually mean when we say a vehicle is self-driving, automated, and so on.

Welcome back everyone! In the last training session we covered basic file input and output. We're going to leave this topic for a bit and start on something that will change the way we write scripts, classes.

Greetings aspiring hackers. I have observed an increasing number of questions, both here on Null-Byte and on other forums, regarding the decision of which USB wireless network adapter to pick from when performing Wi-Fi hacks. So in today's guide I will be tackling this dilemma. First I will explain the ideal requirements, then I will cover chipsets, and lastly I will talk about examples of wireless cards and my personal recommendations. Without further ado, let's cut to the chase.

In this Video I will show you how to make a ice pack with your loose change.

When I tried to set up an eviltwin for a MitM-constelation in kali 2.0, I couldn't provide internet to the victim. The origin was the brctl bridging. I have read many tutorials but all of them where explained in backtrack and older versions of kali. So i was searching for a solution without using brctl and this solution will be explained now. This will just work on unencrypted wireless-environments.
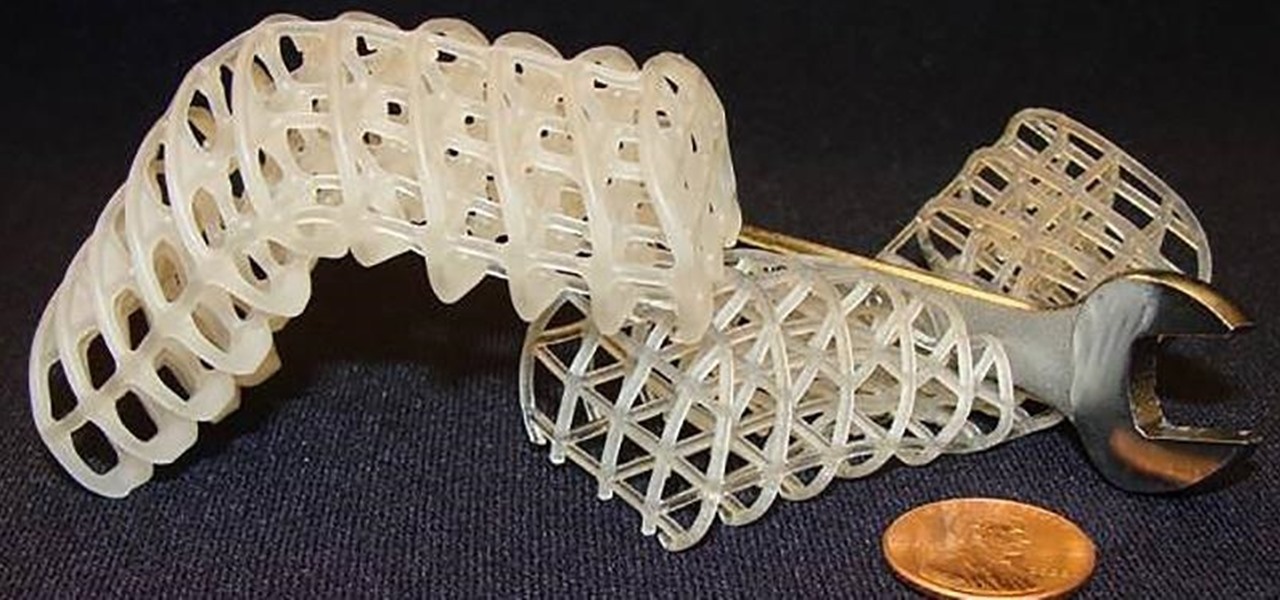
Say goodbye to the age of metal robots—C-3PO and K9 are a thing of the (future) past! Anette Hosoi, Professor of Mechanical Engineering and Applied Mathematics at MIT, and her former graduate student Nadia Cheng, have created a robotic material closely resembling human skin.

Parrot, a company that specializes in personal drones, has recently come out with new products that'll make those '90s robots look as dated as lava lamps and tie-dye.

Whether it's because you have nosy family and friends or you're just cautious about losing your device, having a passcode on your Android smartphone is essential for protection. However, you don't always need or want a passcode, especially when you're home alone or in your car on the way to work.

One of the first things most people ask for when staying with a friend is the password to the Wi-Fi network. Even if you trust your friends to the end of the earth, a super secure password can be a pain to share with them, especially if it's just a bunch of random characters.

I want to talk about growing up with burden of acne. I frequently receive comments and private messages about kids being bullied for having acne, this is not right. Everybody is beautiful in their own way and you should never let the haters put you down! Love yourself =)
Want to be the John (or Jane) D. Rockefeller of Restaurant City? Watch this video tutorial to learn how to hack Restaurant City with Cheat Engine 5.5 (02/04/10).
Want to share Internet connectivity between two computers without a wireless network but have an extra CAT5 ethernet cable? You're in luck. This home networking how-to will show you what to do to get your machines talking not only to one another but the web at large.

Self disclosure forms friendships with active listening and sharing, telling others about yourself, your thoughts, fears, and goals. Learn how to improve self disclosure and trust in this free communication video series.

In this instructional video series, our expert will show you how to give yourself a wonderful and relaxing massage in the comfort of your own home.

Grand master Ike Bear shows us how to use Kung Fu fighting for self defense. Part 1 of 19 - How to Do Kung Fu fighting for self defense.

What You Need: 6-9 empty chip bags

InfoWorld has some expertise advice for the new Windows 7 operating system from Microsoft. Now that Microsoft has made the Windows 7 beta available for public download, many people are trying to figure out what's new and different. And many others not willing to risk their PCs by installing a beta OS are curious, too.
An old blog that I hope to reincarnate in the near future...What do you think so far? (excuse the self promotion)

Captured with Nokia E5 . and I used Baable free from nokia apps

capture using k850i.

Taken with an iPhone 4S with Camera+.

Taken with an iphone 4. App used, camera +.