
How To: Hunt Down Wi-Fi Devices with a Directional Antenna
If you've ever wanted to track down the source of a Wi-Fi transmission, doing so can be relatively easy with the right equipment.


If you've ever wanted to track down the source of a Wi-Fi transmission, doing so can be relatively easy with the right equipment.

So you want to know what that person who is always on their phone is up to? If you're on the same Wi-Fi network, it's as simple as opening Wireshark and configuring a few settings. We'll use the tool to decrypt WPA2 network traffic so we can spy on which applications a phone is running in real time.

With a tiny computer, hackers can see every website you visit, exploit services on the network, and break into your Wi-Fi router's gateway to manipulate sensitive settings. These attacks can be performed from anywhere once the attacker's computer has been connected to the router via a network implant.

A long-standing request for the iPhone has been a way to quickly browse and connect to available Wi-Fi networks and Bluetooth devices without having to dig through the Settings app. With iOS 13, Apple has finally built this essential feature into Control Center, giving you quick access to wireless settings from anywhere, including the lock screen.

Automating port scanners, directory crawlers, and reconnaissance tools can be complicated for beginners just getting started with Kali Linux. Sparta solves this problem with an easy-to-use graphical interface designed to simplify a penetration tester's tasks.

NetBIOS is a service that allows for communication over a network and is often used to join a domain and legacy applications. It is an older technology but still used in some environments today. Since it is an unsecured protocol, it can often be a good starting point when attacking a network. Scanning for NetBIOS shares with NBTScan and the Nmap Scripting Engine is a good way to begin.

While the technology companies continue to drive forward with autonomous vehicles, Nissan's vision of the future of self-driving automobiles lies in a cooperative experience between human and machine, facilitated by augmented reality.

Wi-Fi devices are continually emitting "probe frames," calling out for nearby Wi-Fi networks to connect to. Beyond being a privacy risk, probe frames can also be used to track or take over the data connection of nearby devices. We'll explain how to see nearby devices emitting probe frames using Probequest and what can be done with this information.

Your home has walls for privacy, but Wi-Fi signals passing through them and can be detected up to a mile away with a directional Wi-Fi antenna and a direct line of sight. An amazing amount of information can be learned from this data, including when residents come and go, the manufacturer of all nearby wireless devices, and what on the network is in use at any given time.

Plants all around us capture sunlight every day and convert it to energy, making them a model of solar energy production. And while the energy they make may serve the needs of a plant, the process isn't efficient enough to generate power on a larger scale. So, scientists from the University of California found a way to treat bacteria with chemicals that turned them into photosynthesis machines, capable of generating products we can convert into food, fuels, and plastics.

To hack a Wi-Fi network using Kali Linux, you need your wireless card to support monitor mode and packet injection. Not all wireless cards can do this, so I've rounded up this list of 2019's best wireless network adapters for hacking on Kali Linux to get you started hacking both WEP and WPA Wi-Fi networks.

Self-driving car models and fleets get most of the media attention, but it is the suppliers that design and make the technologies underpinning the driverless revolution, says Guillaume Devauchelle, the vice president of innovation and scientific development for leading tier-one supplier Valeo.

Quanergy CEO and founder Louay Eldada is, by any standard of measure, a pioneer in the development of LiDARs for driverless vehicles.

Ford's appointment of Jim Hackett as its new president and CEO reflects how the company is largely pinning its long-term survival hopes on its driverless business. Following his previous role as head of Ford's Smart Mobility division, which overseas Ford's autonomous driving activity, Hackett will help the company take a more self-driving direction as a whole.

Uber's year is going from bad to worse, and they may be subject to a potential criminal probe in the ongoing Waymo legal battle.

Those of us with modern smartphones know that 4G LTE networks have provided us with a phenomenal experience. One light years beyond what we had access to before. For some time, AT&T has been teasing its dive into the next iteration of network speeds, agonizingly doing so without any specific dates for when they would actually deliver. But today, AT&T confirmed what they call the "5G Evolution," and it's available now.

Well, well, well. Uber, we knew you were investing a ton of money into creating self-driving taxis and flying cars, but what we didn't know is that you were already testing out your driverless vehicles on the streets of New York City.

Baidu's self-driving car unit has had a tough week. Today, the company's leading artificial intelligence (AI) expert, Andrew Ng, announced in an optimistic blog post that he would be leaving the Chinese search engine company to pursue AI research on his own.
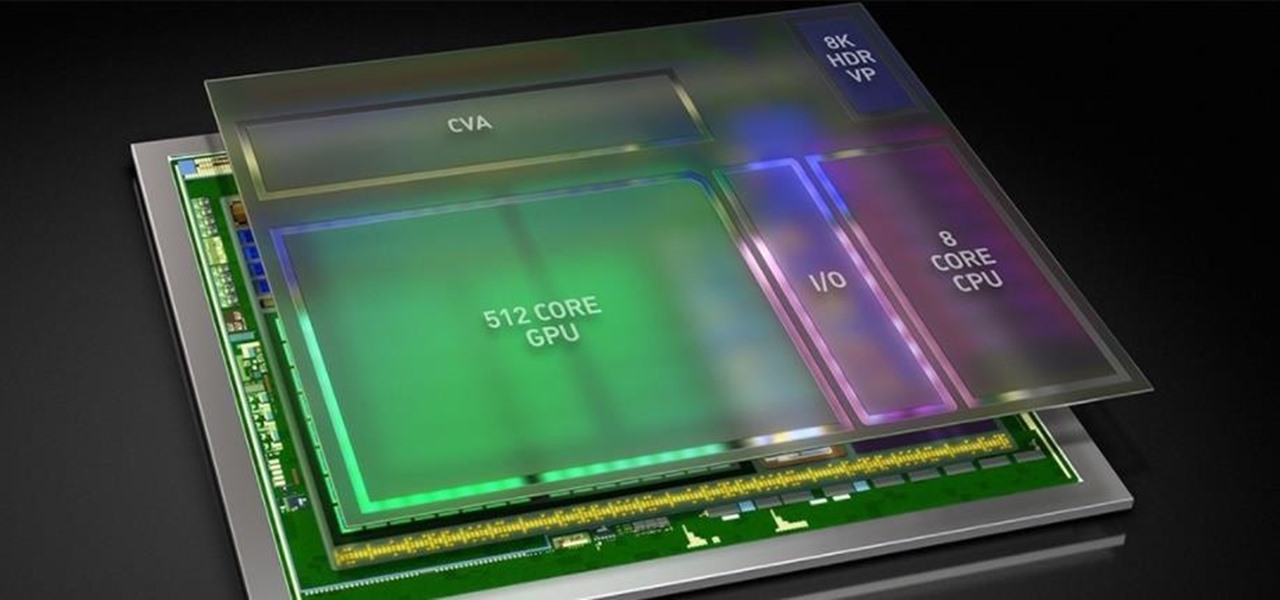
As Intel steps up their investment in driverless technology with a $15 billion acquisition of Mobileye, so have automotive supplier Bosch and NVIDIA teamed up to manufacturer driverless car systems with the much-awaited Xavier chip.

The technology driving the automated vehicle revolution relies on the car's ability to see and understand the world around it.

This year's SXSW festival had a plethora of news and discussion about autonomous cars, but perhaps none was more exciting than the NIO EP9. The car was first shown off in November in London when it ran the Nürburgring Nordschleife track in record time.

Disengagement report numbers for self-driving car testing in 2016 on public roads in California were just released, and the biggest point we can make about them is that Waymo is very far ahead of their competitors in almost every metric.
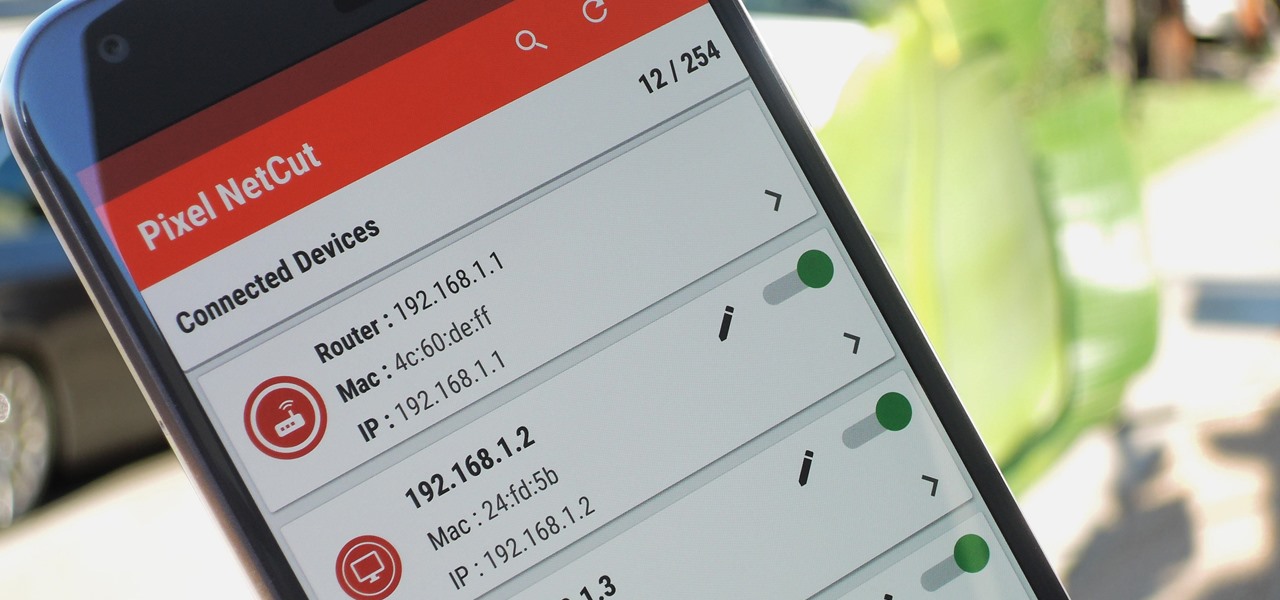
Let's say you gave your Wi-Fi password to your neighbor a while back, under the assumption that they'd only use it while they were at your house sharing stuff via Chromecast. But now, your connection is slower than it normally should be, and you have this sneaking suspicion that the dude in apartment 3C is flat-out piggybacking off of your home network.

I've seen my fair share of heartbreaks when it comes to used phones. As a repair tech, I often had to try and help out customers who bought used handsets which turned out to be useless, either because it was stolen or not working on their carrier's network. More often than not, there was very little I could do. To help you from being stuck in the same situation, here are some tips to prevent you from getting scammed out of your hard earned money when buying a used handset.

Welcome back my networking geeks. In this part we are going to keep discussing about IP Addressing and I hope after you finish reading it you will become an IP wizzard.

Once you connect all of your devices to your Wi-Fi router at home, you'll never need that long, complicated Wi-Fi password ever again, right?

As mobile devices become more and more popular, service providers have unfortunately resorted to capping data. What this means is that, depending on the plan you have with your ISP, you could have limits placed on how much data you can use for a set period of time. Once you've hit the limit, your ISP could drastically slow down or throttle your internet speed or charge you outrageous overage fees.

There are few things that make me smile more than ice cream… or bread! So why not combine them for double the happiness? We've discussed the art of making ice cream bread before, but not everyone has the time (or, let's face it—the patience) to bake bread in the oven, no matter how few ingredients the recipe may take.
Relentless in its fury, the iOS text messaging exploit that exploded onto the scene late last week seems to do more damage than initially reported.
The internet is forever. When you put something out there, it can easily be re-shared, floating from server to server indefinitely with no way of taking it back. It's a scary thought when you consider that a young adult's grandchildren will one day have access to their drunken party pics.
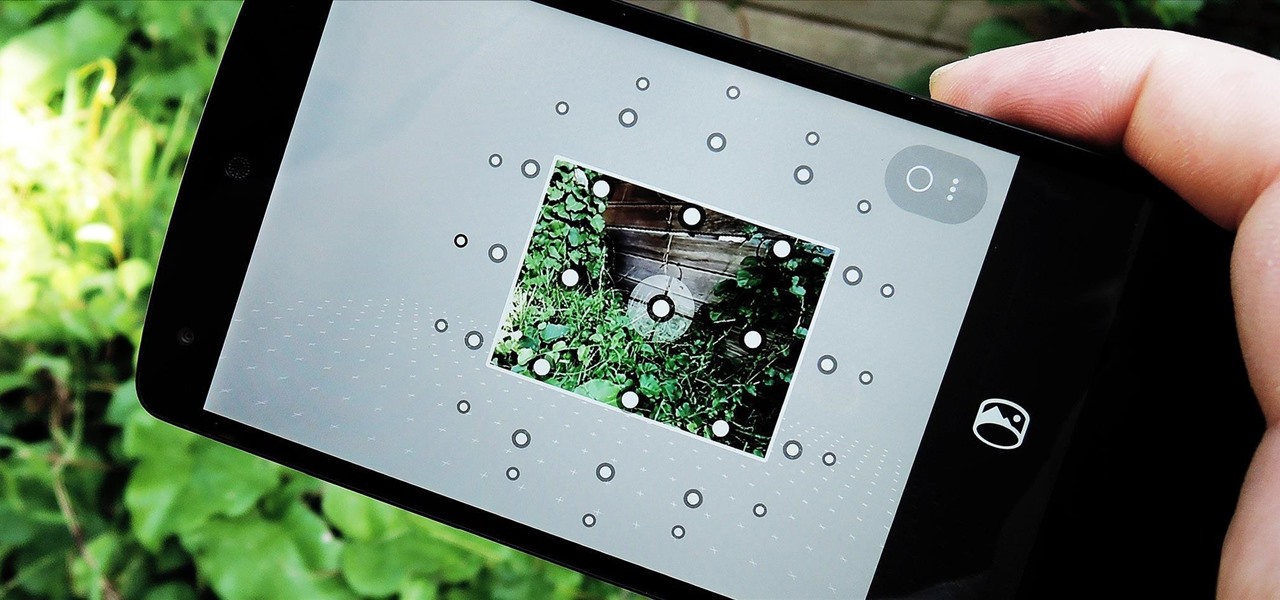
Just over a month ago, Google made its camera app available to all devices running Android 4.4 and higher. Originally exclusive to Nexus devices, the app got a UI overhaul and a new Lens Blur mode, but lost some features in the transition.

Someone does't really like you. I don't know who or where they are, but they exist. If you want to change that, simply ask them to do you a favor.

The outstretched arm, the perfectly positioned angle, the shot and the subsequent array of tinkered saturation, contrast and shadows. In almost every car, changing room, or Starbucks, these string of events happen—you might know it as the selfie.

Point-and-shoot cameras are practically extinct these days now that every new phone on the planet has a camera built right in. This makes the smartphone market highly competitive, because the camera specs and features are a big selling point.

Welcome, my neophyte hackers!

BUD (Block Update Detector) switches can essentially take the place of a regular switch like a lever or a button, but instead of having a "usable" function like pressing the button or flipping the lever, BUD switches trigger when a block next to a piston changes states.

I'm constantly searching for a homemade pizza dough that tastes good but isn't too challenging to execute. In other words, a recipe that doesn't require any arcane "dough whispering" skills. However, my hunt may be coming to an end thanks to one celebrity chef's concept.
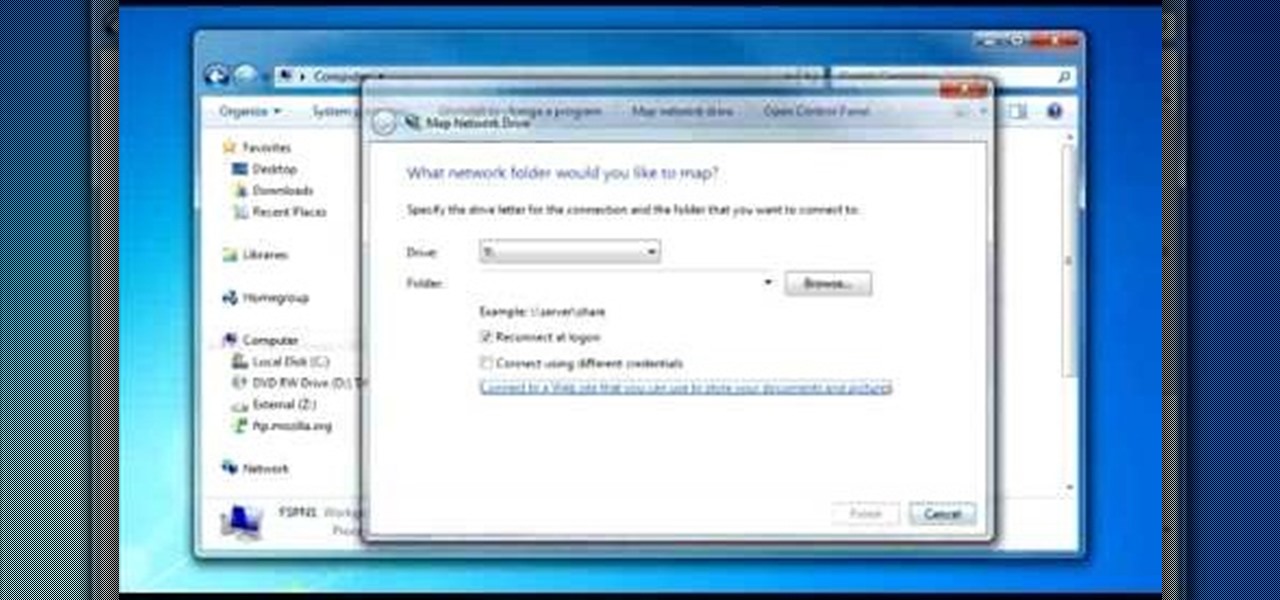
To do that click on tools in windows explorer and choose map network drive. Now click on "connect to a web site that you can use to store your documents and pictures" and then click on next and next. Now you have to type your internet or network address for example you type ftp://ftp.mozilla.org. This is a public server and it does not require a user name or password. Now click on next and there make sure you selected "log on anonymously" but if your server require a password then you have to...

What's the easiest way to adjoin two fishing lines? The blood knot. And no, you're not going to cut yourself, that's not why it's called the "blood" knot. It's also referred to as the Barrel knot, and is usually used for monofilament nylon lines. Wade Bourne of MyOutdoorTV will show you how to tie the blood knot.
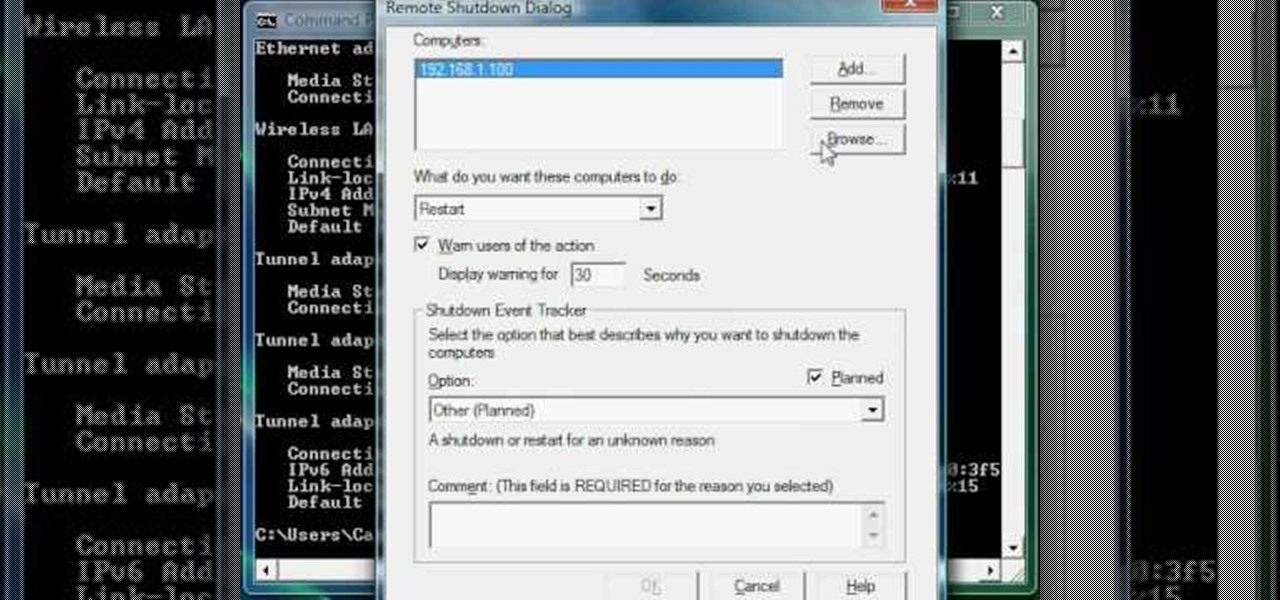
Now you can find your IP address if you need it and you don't know it, it very easy. Or if you have problem with a person on the internet, now you can discover who that person is. You can find her/his IP address and after that you can find her/his real name. But after you find the IP that you were looking for, you have to check if the person who own this computer is in your network, because if you want to find his/her name, the program works only if the owner is on your network. So if you are...