
News: Self Healing Chair Picks Itself Up Off the Floor... Literally
For some reason I find this hilarious. This chair's got perseverance. Sure, he's slow, but it's worth the wait. More information at Robotic Chair.


For some reason I find this hilarious. This chair's got perseverance. Sure, he's slow, but it's worth the wait. More information at Robotic Chair.

This video demonstrates how to improve wireless network performance. From the people who brought you the Dummies instructional book series, brings you the same non-intimidating guides in video form. Watch this video tutorial to learn how to improve wireless network performance, For Dummies.
Oh how we love open source software. If it wasn't for Open Office, we never would have been able to write that seven-page English paper while on our friend's Microsoft Office-lacking laptop during an impromptu road trip to Mexico. And Ubuntu, an open source secure operating system, offers you similar convenience. A much more intuitive computer operating software than your standard Windows or Mac OS, Ubuntu is great if you know what you're doing.

With the economy as terrible as it is these days, obtaining any sort of job, from receptionist to screen writer, requires thorough networking.
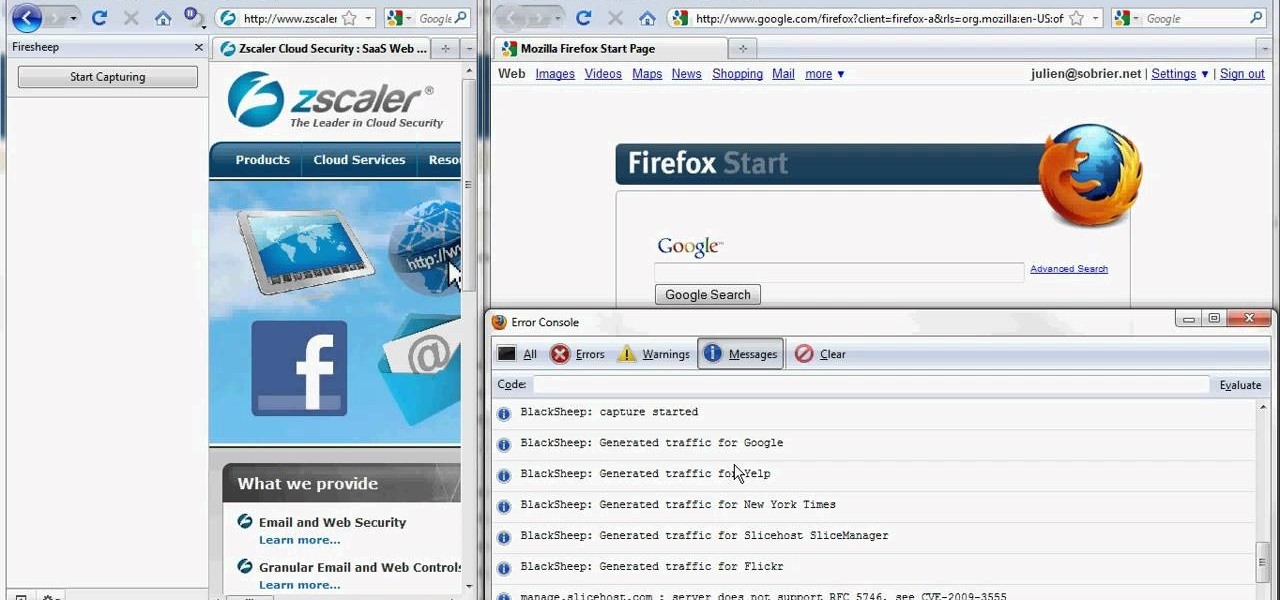
If you're scared of using public Wi-Fi networks with Firesheep out and about, then maybe you should fight back. Don't switch to another web browser— keep using Firefox safely with the help of a new Firefox Add-on that combats Firesheep's password stealing capabilities. It's called BlackSheep, and when installed and running, it will alert you whenever Firesheep is active on your network connection.
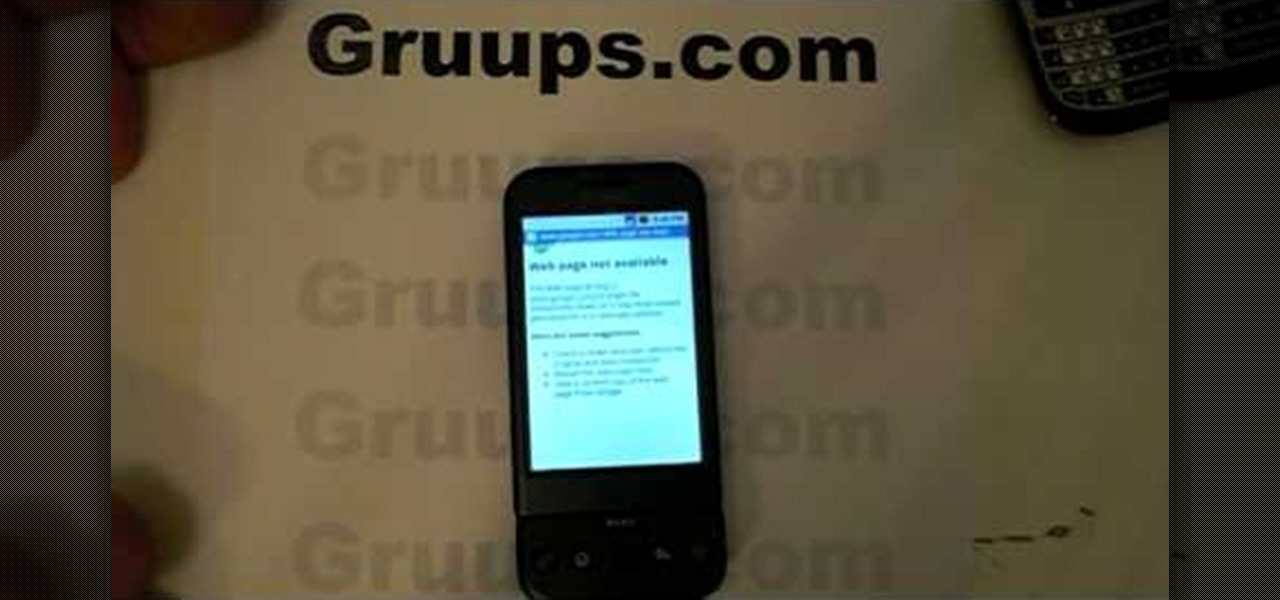
In this tutorial, learn how to save yourself the money you'd pay someone to unlock your Google G1 phone from T-Mobile and do it yourself in just a few quick minutes. This is actually a very easy process and this clip will walk you through the process step by step so you can freely use your phone on any network and not be limited to T-Mobile. This is also helpful if you wish to give away or sell your phone to someone on a new network.
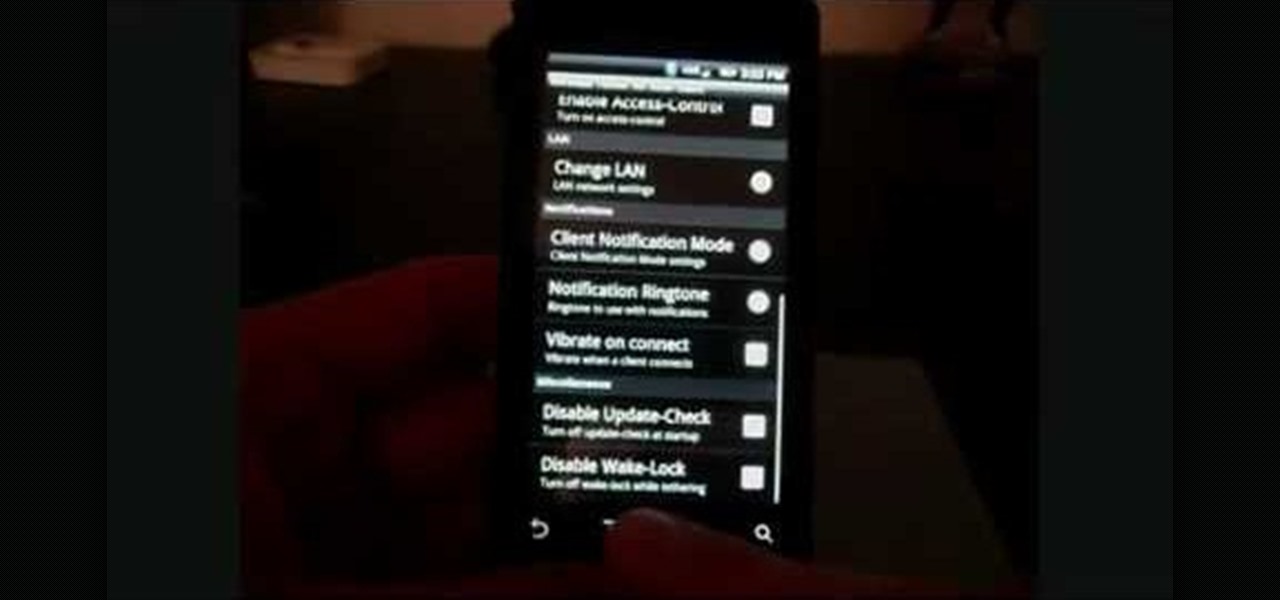
In this clip, learn how to tether your rooted Droid to a WiFi network and use it as a modem for your other Wireless devices. This process is pretty easy and only requires a network and that your phone be rooted.

In this culinary how-to from the Food Network's Ellie Krieger, you'll learn how to bake delectable, almost-healthy carrot cupcakes using whole carrots, lemon zest, canola oil, brown sugar, two eggs, 3 quarters of a cup of whole wheat pastry flour, 1/2 cup all-purpose flour, 1 teaspoon of baking powder, 1/2 teaspoon of cinammon, 1/4 teaspoon of nutmeg and a 1/4 teaspoon of salt.

Watch this video fashion design lesson to see who took second place in the Generation-t tee recon contest with how-to make a wrap shirt. All you need is two t-shirts and the steps, so follow along and get sewing.

Watch this fashion design lesson to see who took third place in the Generation-t tee recon contest with a how-to for making a no-sew fringe halter top!

This week Meg takes us back in time and shows us how to make an amazing Starburst mirror. Follow along with the home interior how-to video, and learn how to add a little vintage flair to your own home decor.

How to Use Your Mac as a Server: Turn your Mac Mini into a server! Yes, that's right, with a little know-how and a little spunk, you can turn an inexpensive Mac Mini computer into a server to provide services over you network. You won't even need the Mac OS X Server, just the Mac OS X Client, so there is no extra software to buy, just the Mac Mini and it's operating system.

In this tutorial Mike Lively of Northern Kentucky University shows you how to get started with Wireshark. Wireshark is a network protocol analyzer for Unix and Windows. It is used for network troubleshooting, analysis, software and communications protocol development.

In this video series, our expert Tres Tew will show you how to use a baton or bat for self defense. He will teach you about open and closed positions, how to draw the bat quickly and strike or block, and how to defang the cobra. Tres will also teach you how to defend against a charge, a cross slash, a shoulder grab, a front choke, cross grab, and wrist grab using a baton or bat.

In this video series, our expert Aikido master is able to show you and any woman how to easily and effectively defend against an assailant, man or woman, even when surprised. You will learn practical techniques like screaming and scratching as well as many others. Knowledge is power and by learning these techniques you will not only be able to fight off an attacker but you will also be more self confident and aware of your surroundings so as not to be a surprised victim. Who knows, these tips...

Wireless networks. Nowadays, everyone uses 'em, but most don't secure 'em. On average, I can drive up and down any block in my city and find at least one or two open or semi-open networks on any given day. With some changed MAC addresses for good measure, an attacker can use your network as a spring board for who knows what. When the police come a few days after, they are coming to your door—and not to talk about how nice your lawn is. Don't be that guy.

In my recent Darknet series, I attempted to connect the dots on the Deep Web. I covered the two largest anonymity networks on the Internet today, Tor and I2P. While my initial four articles were meant as an introduction, I ended up receiving a lot of interesting comments and messages asking the technical differences between the two. I'd like to thank all of you for letting me know what was on your minds, as you should always!

This is a video tutorial in the Video Games category where you are going to learn how to how to connect to Xbox Live without buying a wireless adapter for the Xbox 360. By using only an Ethernet cable and computer you can get onto Xbox live. On your computer go to start > network > network & sharing center > manage network connections. When you have 2 connections; one to wireless and one to local area connection, select both and right click and click on bridge connections. Your computer now r...

In this video tutorial, we learn how about the basics of setting up a simple wired network. It's easy. So easy, in fact, that this home-computing how-to from the folks at CNET can present a complete overview of the process in just over two minutes. For more information, including a complete demonstration detailed, step-by-step instructions, take a look.

In this clip, you'll learn how to find and connect to WiFi networks on a desktop or laptop computer running the MS Windows Vista operating system. For more information, including a complete demonstration of the process and detailed, step-by-step instructions, watch this home-computing how-to.

Not only can your T-Mobile G1 phone get Internet access by itself, you can also use it as a router or modem for your home wifi network. All you need is to download a single app from the market, install it, and you're ready to set up your home wifi network!
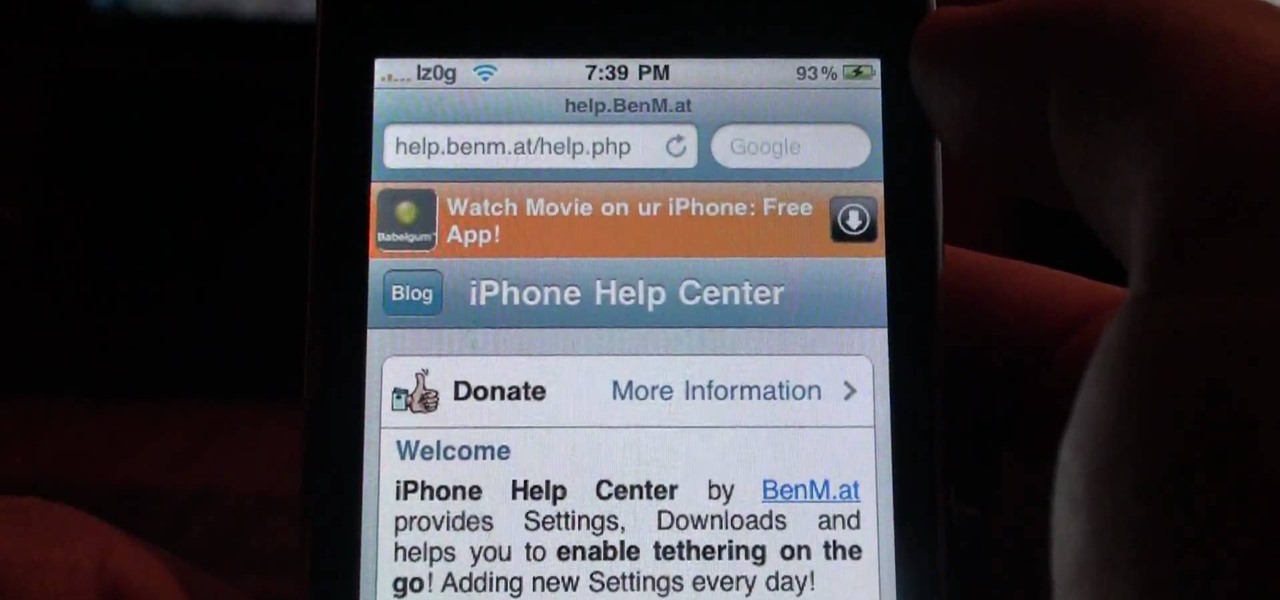
Go to Cydia and add a new source http://Cydia.xselize.com. Now search there for supreme preferences and install it.

Getting a Playstation Portable to connect to your wifi network can be tricky. If you own a Buffalo router, this tutorial walks you through the process to get your PSP connected to your home wifi network. Now you can check your email and surf the web on your PSP!

In this tutorial, we learn how to set up a Wi-Fi network with a Linksys router. First, go to your cable modem and remove the yellow Ethernet cable. After this, plug the Ethernet cable into the very first port of the router and plug the other end into your computer. After this, connect any other electronics you have with cables, then plug the router into the wall to give it power. Next, turn the power to the modem and router back on. When finished, you should see a new Wi-Fi network appear in ...
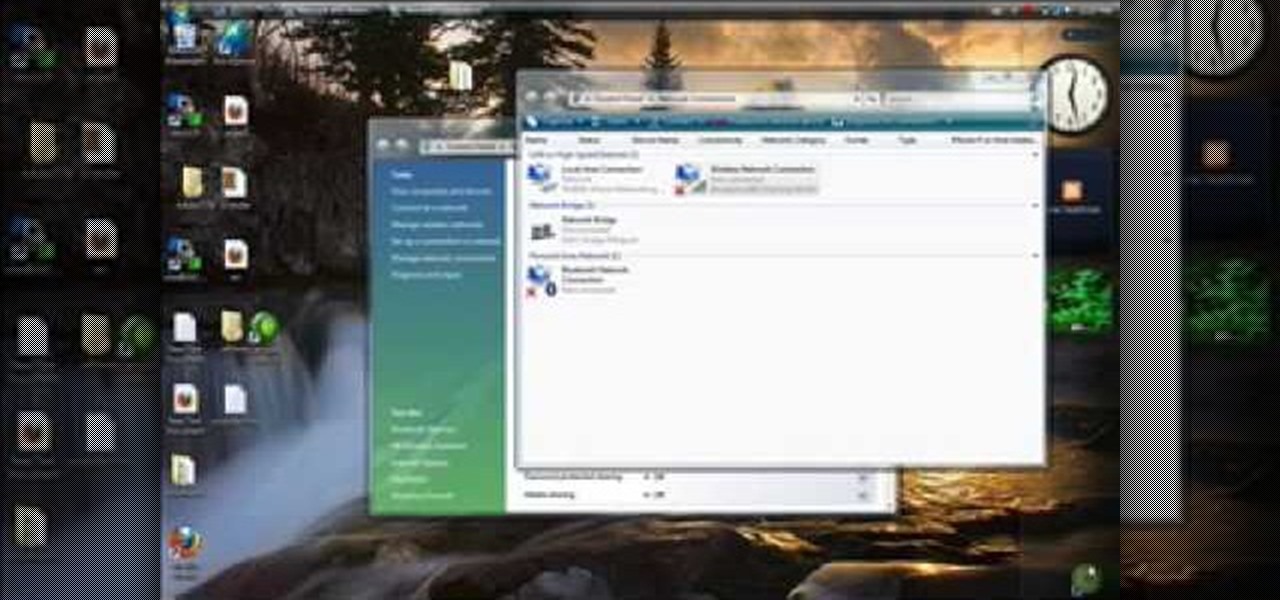
This tutorial gives a start to finish explanation of how to make an Internet Wi-Fi router with Windows Vista. With real time computer screen video and narrative, it is easy to follow along at home.
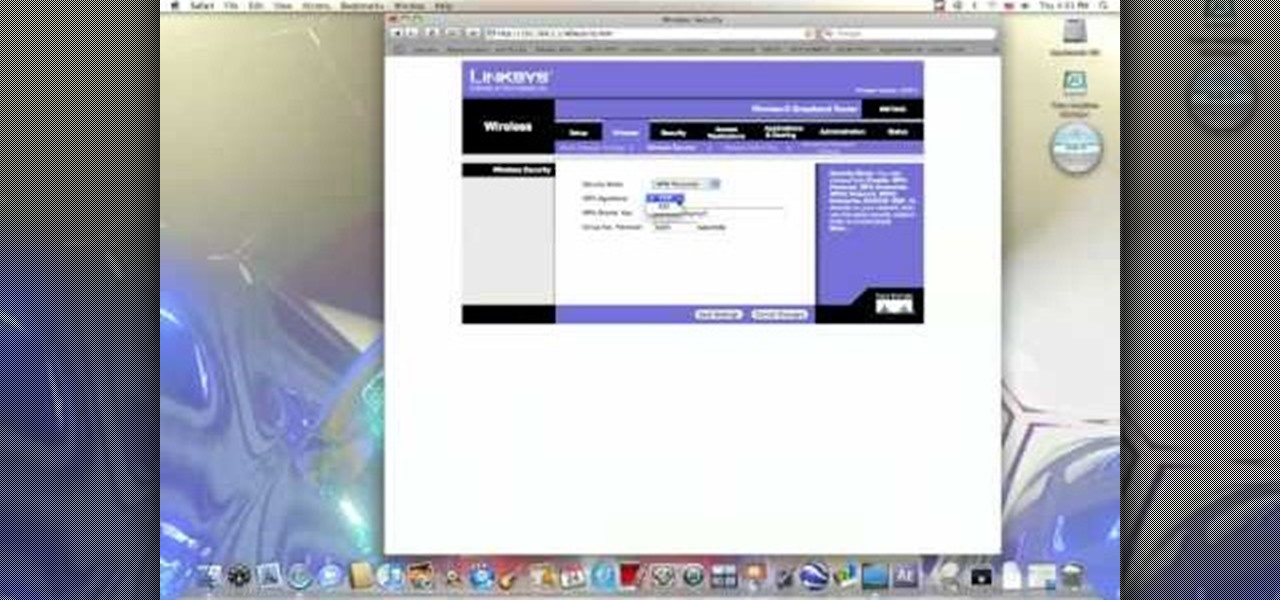
In this video from benjamoon we learn how to secure a linksys wifi network from a Mac. First type in your IP address in your browser bar which is 192.168.1.1 then press enter. If it asks for a password it is admin. Click on Wireless and here you can edit your name and who can access your wifi network. Under wireless security, go to WPA personal from the drop down menu. When you make your password, make it very challenging. He recommends just banging your hand against the keyboard, as long as ...

Google G1 users, want to switch your phone network? In this video, learn how to unlock the Google G1 HTC Dream Phone. All you need to complete this tutorial is your phone and a SIM network unlock pin code.

Just because you are using Linux, doesn't mean you have to be cut off from file sharing with those using a regular Windows PC. In this tutorial, learn how to share files between Ubuntu and Windows using a Samba local network. Samba is simple to use and can be obtained through your Synaptic package manager.
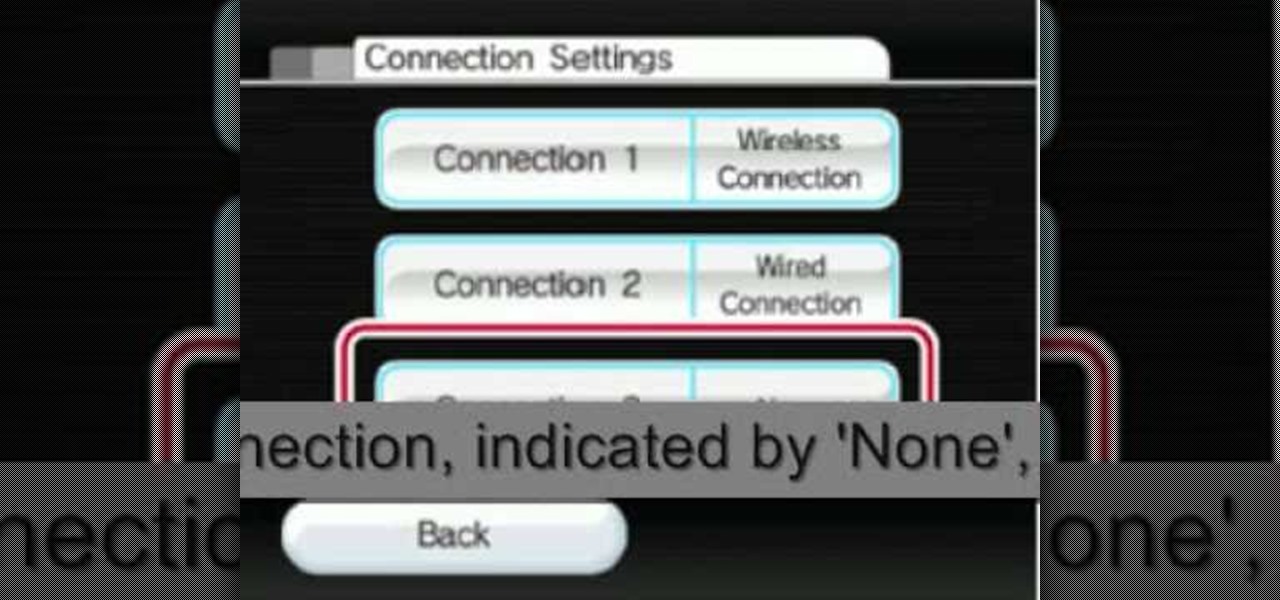
The video shows you how to connect the Nintendo Wii to an available wireless network. First, you have to turn the Wii on. When the menu screen appears, you then click on the "Wii button" in the bottom-left corner. Next, go to "Wii Settings". On the following screen, you have to use the blue arrow on the right to go to the second page of options and select "Internet". Go to "Connection Settings" and click on an "Open Connection". From here, go to "Select Wireless Connection" and then "Search f...

Take one end of the Ethernet cable and plug it in the back of the XBox, the other end of the cable you have to plug on your computer. On your computer go to Start and then go to My Network Places, now select View Network Connections. Right-click the Wireless Network Connection, and go to Properties. Select Advanced tab on top of the window and make sure the two boxes are checked, press OK to continue. Now turn on your XBox and go to Test XBox Live. Wait until the test ends and then you will b...
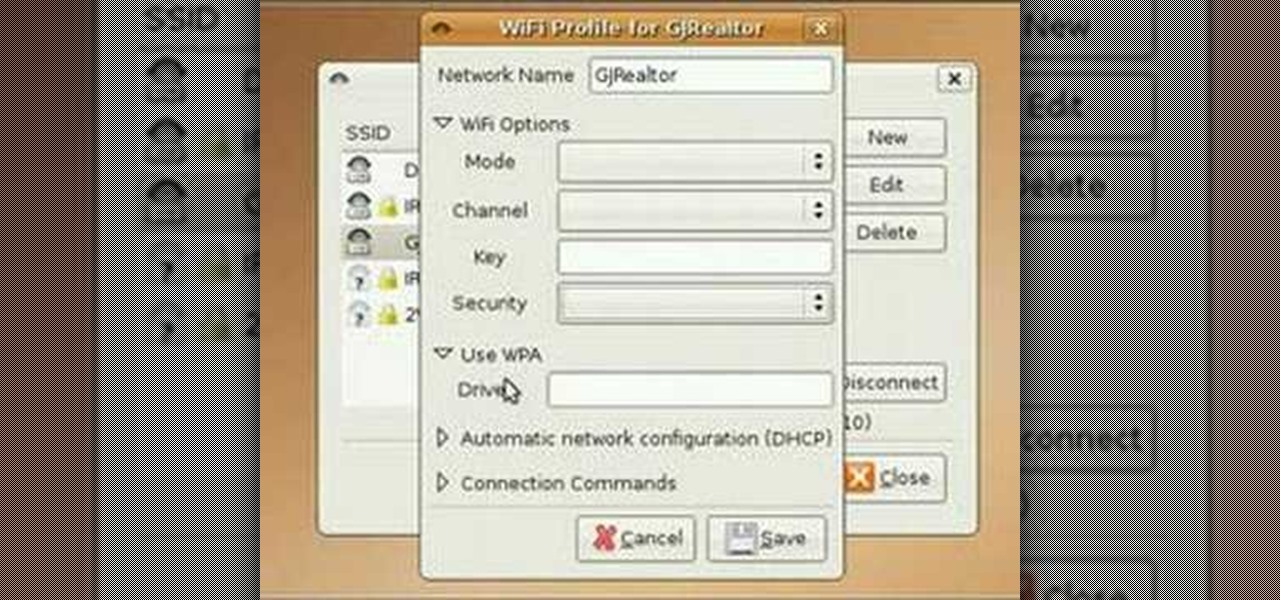
In this video tutorial, you'll learn how to use the WiFi Radar application to find wireless networks while running the Ubuntu Linux distribution. For more, and to get started finding and using wireless networks in Ubuntu for yourself, take a look!
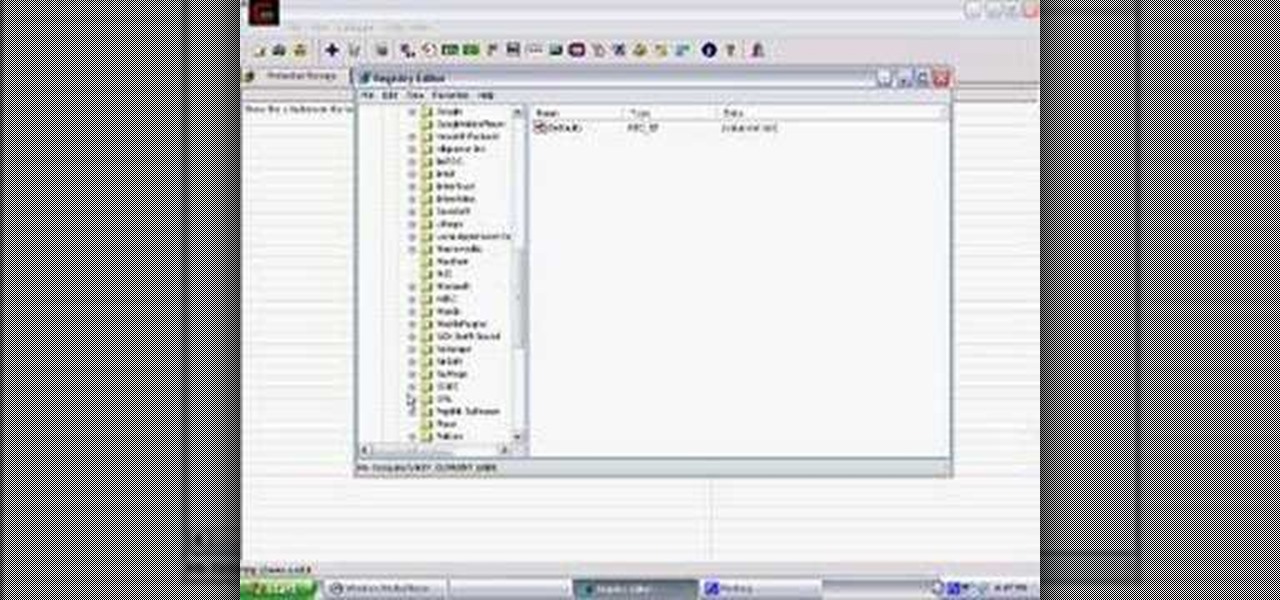
Hack a network computer by decoding Virtual Network Computing (VNC) hex passwords with Cain.

No, this yo-yo rig does not mean attaching your toy yo-yo to your fishing line. It's a specifically deigned mechanical reel that is designed to fish while you're home in bed. It's quite the reel, and worth a try. Wade Bourne of MyOutdoorTV shows you how to rig a mechanical yo-yo rig.

This video demonstrates how to connect a Mac to an ethernet network. From the people who brought you the Dummies instructional book series, brings you the same non-intimidating guides in video form. Watch this video tutorial to learn how to connect a Mac to an ethernet network, For Dummies.

From the people who brought you the Dummies instructional book series, brings you the same non-intimidating guides in video form. This is Mac for Dummies. Just watch this video tutorial to learn how to connect a Mac to an ethernet network, For Dummies.

A network Tarpit, sometimes know by the German word Teergrube, is a service or set of hosts that deliberately try to slow malicious network connections down to a crawl. The idea is to put up unused hosts or services on the network that respond to an attacker, but do things to waste their time and greatly slow their scanning (or spreading in the case of Worms). To follow along with this video tutorial, you'll need a package called LaBrea by Tom Liston and an unused IP address to tarpit. Set up...
Most of you are familiar with using Ettercap for attacking systems, but what about using it to find attackers? This tutorial will cover using Ettercap to find people sniffing on your network. The plug-ins we will be using are search_promisc, arp_cop and scan_poisoner. Have fun detecting network sniffers. Detect hackers on your network with Ettercap.

If you're a beginner to Chinese watercolor painter then you do have to do a little research and practice before you actually let your paintbrush hit the canvas. From using the right paint to the right brush, every single thing you employ for your art matters in the ultimate creation.
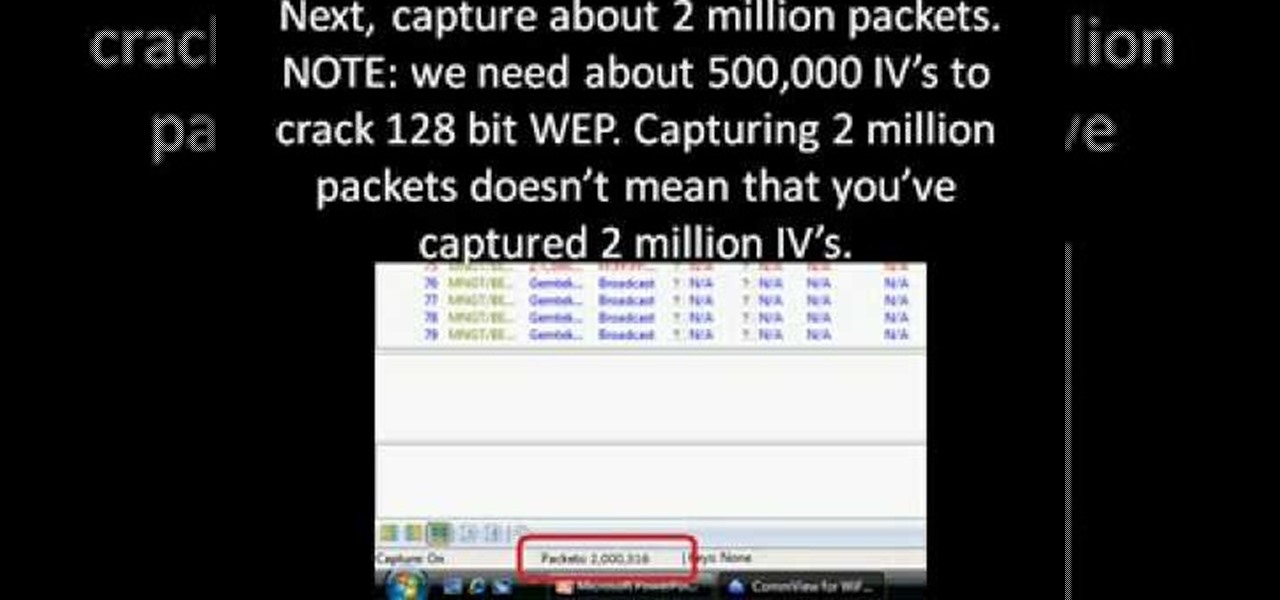
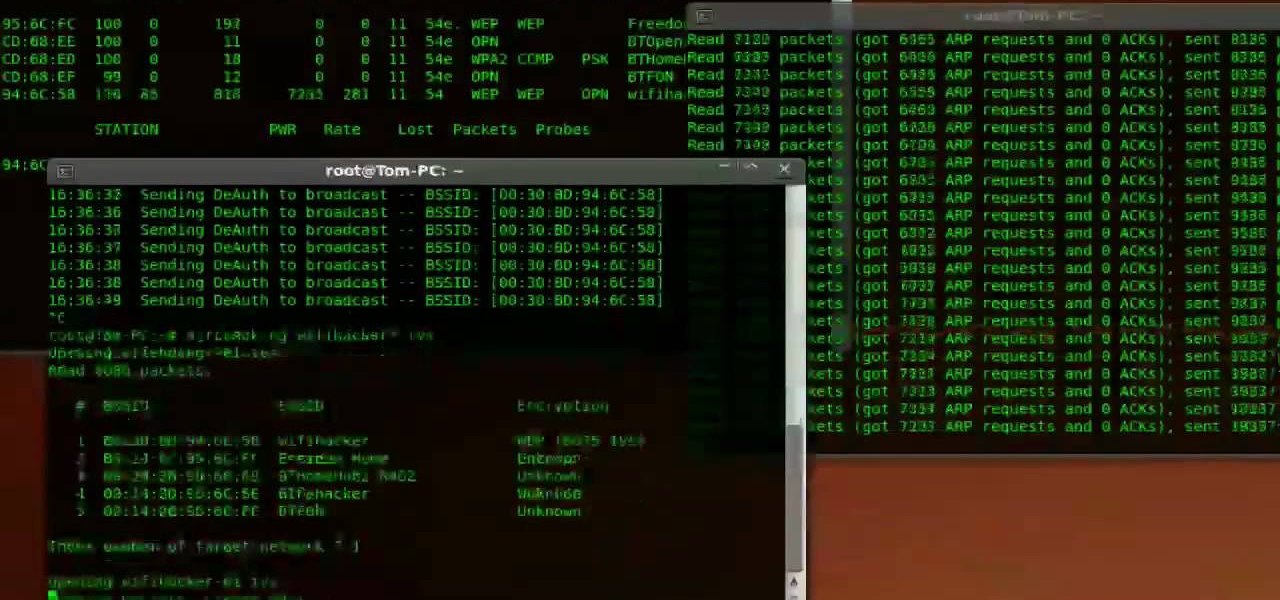
First you need to download Aircrack-ng and Second thing you need to download is CommView for Wi-Fi. Now you have to install CommView for Wi-Fi and then install the right driver.
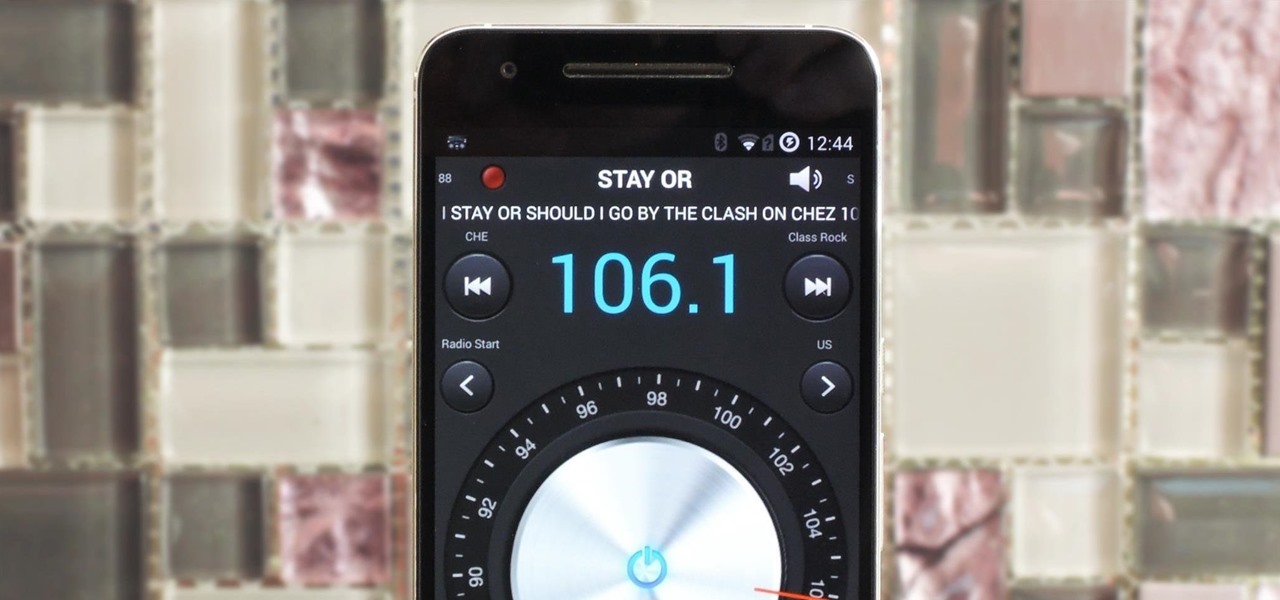
Android smartphones have all sorts of connectivity chips built in, including Bluetooth, Wi-Fi, GPS, NFC, and mobile data. But what about AM or FM radio, two of the most common methods of wireless communication?