Master Rafael Negron, 6th DAN Master Instructor, and Jessica Sherlock, 2nd Degree blackbelt. Hapkido is an eclectic Korean martial art that is literally translated as “the way of coordinating energy” or “the way of coordinated power.” Hapkido is ultimately used as self-defense and combines other skilled martial arts with common attacks. he main focus of Hapkido is footwork and body positioning used to employ leverage.
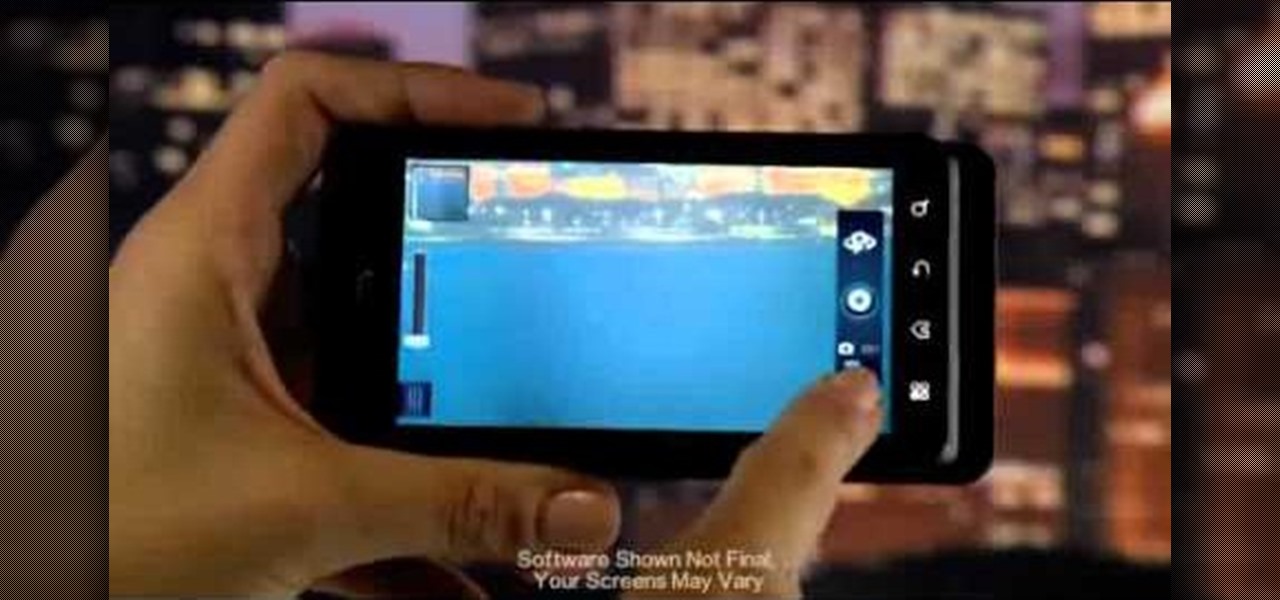
The Droid 3 smartphone from Verizon has a great camera perfect for taking beautiful photos. If you want to learn how to perfect your on-the-go photography, take a look at this tutorial from Verizon Wireless that features instructions on all the different settings in the Camera app on the Android device.

Have you ever found something in your suitcase that wasn't yours? Maybe it was, but you're almost certain it wasn't. Maybe a friend slipped something in your baggage before your departure flight? Maybe the TSA was playing a joke on you, since they have all the master keys for your approved travel locks?

If you're a medical student, you'll learn a lot from this video lesson on examining your patient's eyes. If the patient is having trouble seeing, like double vision, blurred vision, pain or any other problem, a proper eye examination is detrimental to properly diagnosing and treating him/her. You can also determine and potential problems which may arise bases on your family history. Watch to see the complete procedure outlined, which is great for any med student or doctor. Even nurses can ben...

Most won't know what the acronym HEENT stand for, but if you're a medical student, doctor or nurse, you know that it stand for head, ears, eyes, nose and throat. To perform a HEENT examination properly, you must know all the steps and techniques to diagnose your patient. This video lesson will outline the examination procedure, from start to finish, and shows you general palpation techniques and examining the temporomandibular joint, superficial lymph nodes, thyroid gland, eyes, ears, nose, m...

In the first part of this series, we took a factual and technical look at the history of the Internet. I explained how all of these wires and servers got here in the first place. Obviously, a firm did not just create and build the Internet around 1995! Now that we know how the Internet came to be, we can get into the really fun stuff—what the Internet looks like now! Well, that's not quite the network design I was talking about, but it does show what the Internet looked like back in 2007 befo...

If you read my article on the OSI model, you got a good overview on communications from that model's perspective, but how does that relate to TCP/IP? We're going to take it a step further, getting into the idea behind the two address concept. How does an IP address and a MAC address work together? If you want to hijack sessions and all sorts of lulz like that, you need to understand these concepts. Let's get into it, mates!

Jeremy at GamerTell shows us how to connect our X-Box 360 to the internet VIA Windows Vista and a Laptop Computer that is already connected to a wireless network. First we have to connect your laptop to your X-Box 360 using an Ethernet cable. Now we will turn on the Xbox 360. Make sure you are on the correct TV Input or channel. Now go to your laptop and Click on the start button on your laptop and find control panel. Once your in control panel select Network and Internet. Now we will select ...
Living Life- everyone knows how to do that right? Right everyone does know how to live life, but not everyone knows how to live life to it's fullest. Living Life to its fullest can be hard, when there is all these other obstacles in your life. But with a little guidance, motivation, and self confidence anything you set your mind to can almost magically happen. Ok now that that has been said; your wondering how can I get more guidance, motivation and self confidence. Well to do that you must g...

The Process & Form Of Brian Craig- Wankiiri By Adam Reeder

Life has always been complex and challenging. The challenges today are just different than what they were in the past. Nowadays instead of hunting and scavaging for food and living in the elements we’re bombarded with suggestions and demands from our highly sophisticated societies. How is it possible to find harmony amidst what are often contradictory messages?!

When you look at the top corner of your phone, what do you see? Upon upgrading to Android 11 or iOS 14, you'll see either "5G," "5G+," or "5G E" if you're connected to the right network. But what exactly do these symbols mean? They indicate not only if you're using 5G, but also what type you're connected to.

When learning Wi-Fi hacking, picking a compatible Wi-Fi network adapter is the first step to learning to crack Wi-Fi passwords.

For the most part, Google Wifi and Nest Wifi systems take care of themselves. But there are still a few manual features that might come in handy, like being able to check on network activity to see which devices are using the most bandwidth when your connection gets bogged down.

Sniffing packets over a network is an easy way for hackers to gather information on a target without needing to do much work. But doing so can be risky if sniffing packets on an untrusted network because a payload within the packets being captured could be executed on your system. To prevent that, Sniffglue sandboxes packet sniffing to provide an extra layer of security.

One of the most common web application vulnerabilities is LFI, which allows unauthorized access to sensitive files on the server. Such a common weakness is often safeguarded against, and low-hanging fruit can be defended quite easily. But there are always creative ways to get around these defenses, and we'll be looking at two methods to beat the system and successfully pull off LFI.

Auditing websites and discovering vulnerabilities can be a challenge. With RapidScan and UserLAnd combined, anyone with an unrooted Android phone can start hacking websites with a few simple commands.

An augmented reality system developed by Lyft might make it less awkward for drivers to figure out who they are supposed to pick up.

Many popular IoT devices have terrible security. For instance, a hacker who's on the same Wi-Fi network as a Sonos speaker can assume direct control over the device's behavior. If an IoT device doesn't secure the messages used to control it over a network, it's easy for somebody to write a few Python scripts to make it do whatever they want.

The company behind augmented reality's first real gaming hit, Pokémon GO, is quietly making moves toward supporting the rapidly growing smartglasses space that may one day move its content away from smartphones and tablets and onto AR lenses positioned on your face.

On Tuesday, Blue Vision Labs, one of three Google-backed companies working on AR Cloud platforms, announced its acquisition by ride-sharing company Lyft.

When Pokémon GO developer Niantic launches its Real World Platform for augmented reality gaming, it will run over 5G speeds courtesy of T-Mobile parent company Deutsche Telekom and the edge servers of its MobiledgeX subsidiary, the companies announced today.

The newest version of macOS has arrived. While everyone's mind is being blown by Mojave's groundbreaking new Dark Mode, we'll be taking advantage of its insecure file permissions to establish a persistent backdoor with a self-destructing payload that leaves little evidence for forensics.

The new iPhone XS and XS Max have more issues than just their hefty price tags. Customers have only had the phones for a handful of days, but some are already complaining of cellular and Wi-Fi connectivity issues on both models. If your experience is the same on your XS or XS Max, there are steps you can take to get your iPhone reliably back online.

The first few minutes after gaining access to a MacBook are critical — but where do we begin? Using tools built into macOS, we can develop an in-depth understanding of running background processes, detect antivirus software, locate sensitive files, and fingerprint other devices on the network. All of this can be done without installing additional software or modifying any files.

As Android bug bounty hunters and penetration testers, we need a properly configured environment to work in when testing exploits and looking for vulnerabilities. This could mean a virtual Android operating system or a dedicated network for capturing requests and performing man-in-the-middle attacks.

Design flaws in many routers can allow hackers to steal Wi-Fi credentials, even if WPA or WPA2 encryption is used with a strong password. While this tactic used to take up to 8 hours, the newer WPS Pixie-Dust attack can crack networks in seconds. To do this, a modern wireless attack framework called Airgeddon is used to find vulnerable networks, and then Bully is used to crack them.

On Tuesday, at the Geneva International Motor Show, Volkswagen gave the world an early peek at a futuristic autonomous concept car that includes a virtual AI host embodied in an augmented reality interface.

Until self-driving cars become mainstream, augmented reality might be the next big technology to hit your dashboard.

When the Super Bowl airs, every other TV network puts on reruns because no one wants to face that juggernaut for ratings. The launch of a new iPhone is the Super Bowl of the tech world, with the launch of the iPhone X being the biggest one yet.

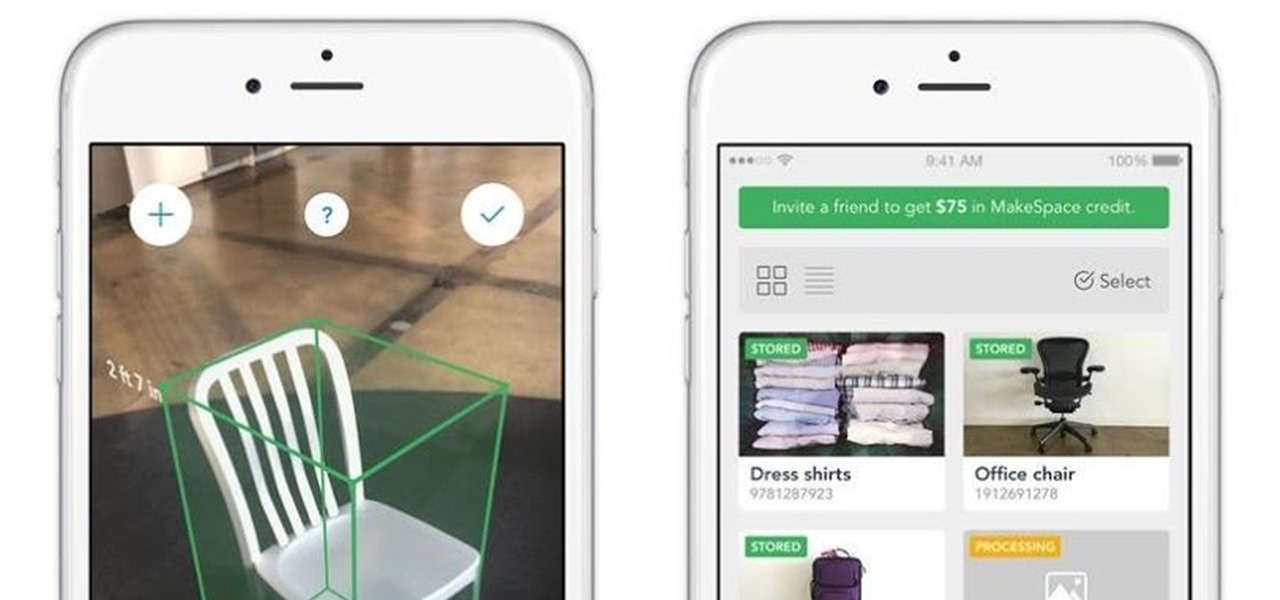
In many ways, the latest version of the MakeSpace iPhone app, now updated with ARKit, makes it the bizarro world IKEA Place; instead of measuring your living space for new furniture, it measures your furniture so you can move it into storage.

The status of Uber's driverless program remains a big unknown amid the company's recent woes, but a reported multibillion-dollar shot in the arm by Japanese tech giant Softbank could change all that.

A man-in-the-middle attack places you between your target and the internet, pretending to be a Wi-Fi network while secretly inspecting every packet that flows through the connection. The WiFi-Pumpkin is a rogue AP framework to easily create these fake networks, all while forwarding legitimate traffic to and from the unsuspecting target.

Most carmakers now agree with Waymo that piloting driverless cars is best left to the machine — with no meddling from the human.

Savor this moment: we've got a confirmed number of sales for the Google smartphone. We say this because unlike most hardware manufacturers, Google refuses to share official sales numbers for their phone. Instead, during earning reports they simply bundle the product under Alphabet's "Other Revenues", leaving us in the dark about how successful the product is.

The $25 million development alliance Jaguar Land Rover's mobility unit InMotion has formed with US-based ride-share firm Lyft reflects how the British luxury carmaker is leaning towards a fleet service business model for its driverless offerings.

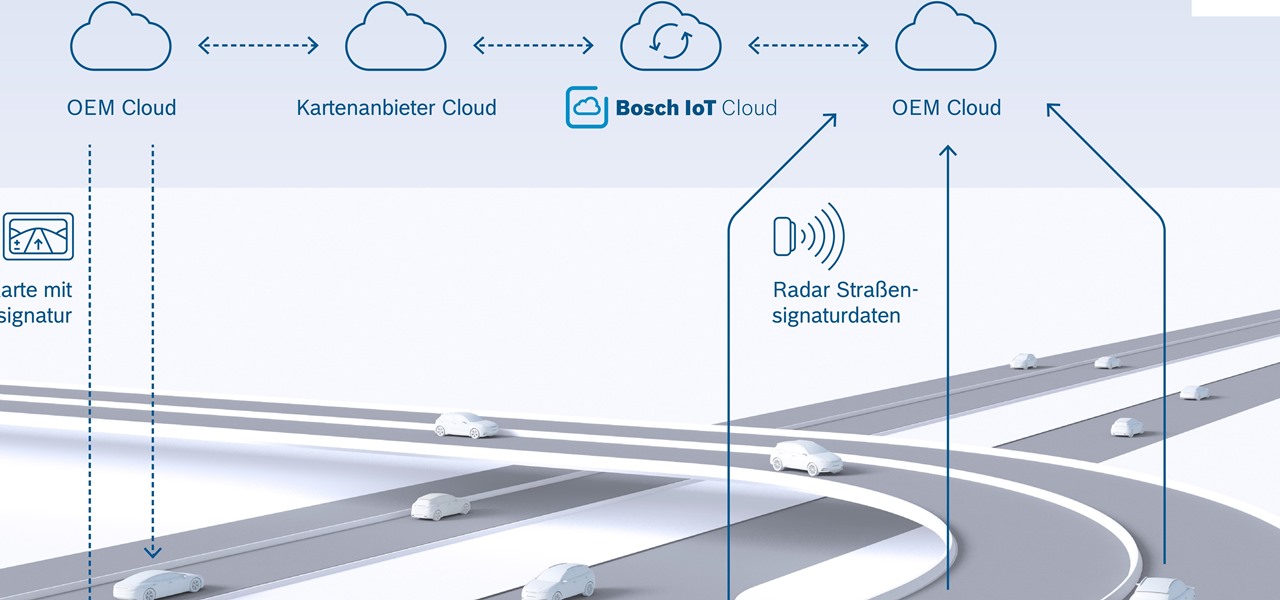
New "radar road signature" technology from Bosch will be used to create maps for high-accuracy self driving. The new map is the first to use radar signals for a localization layer.

The common thread between this week's Brief Reality stories is that augmented reality is beginning to prove its worth as a technology that improves workflows and processes. From customer service to healthcare to manufacturing, augmented reality is helping companies improve productivity.

Paris, girl, you are awesome, but you did not invent the selfie. If you want to spread this #newmarketingterm to the media masses, then go right ahead. It's your brand, your career, and you got the opportunity. People will listen. No one really cares about who invented the silly thing anyway. Though I got to say, the original king of the selfie did seem like one pretty chill dude ...

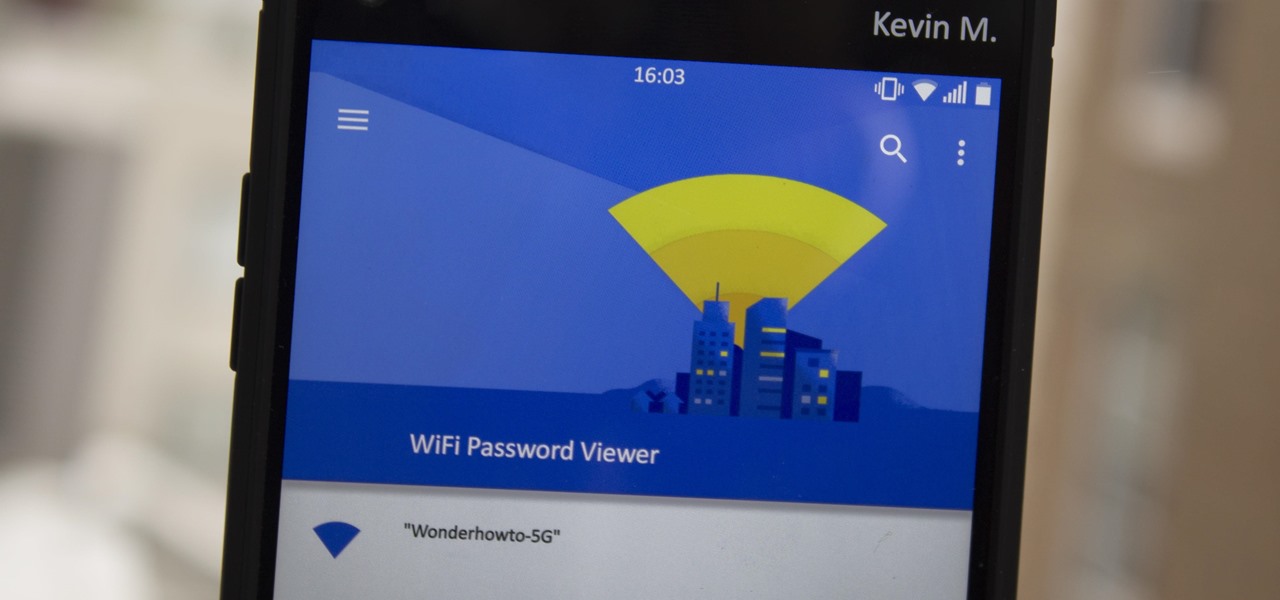
Have you ever gone to a friend's house and not asked for the Wi-Fi password? Probably not, and the same can likely be said of any friends that come over to your place. But the actual act of sharing Wi-Fi passwords is still incredibly clunky, and it's particularly hard if you have a nice and secure password with uppercase and lowercase letters, numbers, and symbols.