I've already covered how you can automatically save Snapchat photos and videos to your Samsung Galaxy Note 2, and how to take screenshots of Snapchats sent to you without the sender knowing, but there's one other thing about Snapchat that could use some softModding.

A free Wi-Fi hotspot can be a lifesaver. Whether it's because you have shitty reception, need faster connectivity, or just don't want to go over your monthly data plan, free Wi-Fi in public areas is greatly appreciated. While connecting to these free hotspots is fairly easy, finding them can become a whole nother issue. I've been in plenty of situations where I wasted my data plan instead of taking a few steps to the right, where free Wi-Fi would have been waiting for me and my Samsung Galaxy...
When the specs for Google's Nexus 4 came out, most critics were more than thrilled. A very fast processor, lots of RAM, a big display with very high resolution, and an 8MP camera made it the media darling of the smartphone world. It climbed the ranks of the best smartphones available, but couldn't quite reach to the top due to one reason—no 4G LTE. Samsung's Galaxy S III and Apple's iPhone 5 both come with 4G LTE, so why couldn't the LG Nexus 4? While there are many reasons, Google was stated...

The pumpkin is everyone's favorite cucurbit come Halloween time, and while there are only a few types of Halloween-friendly pumpkins out there, there is definitely no shortage of what you can do with them.

Do you own an HP printer? If so, it may be vulnerable to malware attacks. Researchers at Columbia University discovered that 25% of Hewlett-Packard printers have significant vulnerabilities that put your printer in danger from hackers—even your home. With a budget of just $2,000, researchers Salvatore Stolfo and Ang Cui were able to hack into the printers using remote firmware to install malware, and in some cases even cause the printer to catch on fire. The main issue is with the printer's c...

It seems like the EU is currently in the works of making "the production or sale of devices such as computer programs designed for cyber-attacks" illegal. So, if you're a network admin that uses WireShark or Metasploit, you better watch out!

Wouldn't it be nice to just sit at your buddy's house, plug into his network, and see exactly what he's doing? What if it was as easy as that? What makes packet sniffers like Wireshark such potent tools is that a majority of local area networks (LANs) are based on the shared Ethernet notion.

At Kaplan University, our main focus in developing our online MBA programs is career development. We believe the time and effort that is required to obtain a master’s degree online should be apparent the first day the student begins their new career. Earning an MBA could be a step in the right direction towards a fulfilling and satisfying career.*

+Guy Kawasaki is someone you should definitely circle on Google+ if you want to keep up with the social media world. He's always got interesting links, and he posts multiple times a day (you may want to drop him into a noisy people circle). He created this great graphic to help you decide which social network to choose: Facebook, Twitter, or Google+.

The group social networking application Fridge has been purchased by Google, and two of its team members will be moving to Mountain View to work on the Google+ team. Fridge, in addition to being a group social sharing site, has photo and event sharing features. The event and calendar-sharing are popular requested features for Google+ users.

This video gives you tips on how to use social networks to find new job opportunities. ..

Two trailers with the exact length in time, their audio is swapped and synchro magic occurs. Here is the Social Network trailer visuals with the Let Me Go Audio, then the Let Me Go visuals with the Social Network audio.

Here is the amazingly original social network trailer Here is a parody of that trailer done for ping. Its amazing what a single track of music can do to create the feeling of a trailer.

Here is the official trailer for "The Social Network" which is David Fincher's film about FaceBook. The official website for this movie is http://500MillionFriends.com

If you don't want to go through the hassle of setting up a formal network between two Macs, but still want to transfer files between the two, take a look at Airdrop. Airdrop is a built-in utility found in Mac OS X Lion (10.7) that will allow you to easily drag and drop files to another computer belonging to you or a friend.

How to... Remove A Very Tight Lid? Use Items You Have Around The House! Step 1Want to remove a very tight lid? Do you have a weak grip or arthritic pain in your hands? Have you already tried tapping the lid with a spoon? Thumping the bottom of the jar with the palm of your hand, and it still won‘t come off? An easy, quick way to remove a very tight lid is to put on rubber gloves! Yes. Ordinary household rubber gloves. Hold the jar in one hand, then use the other hand to twist the lid off. Thi...

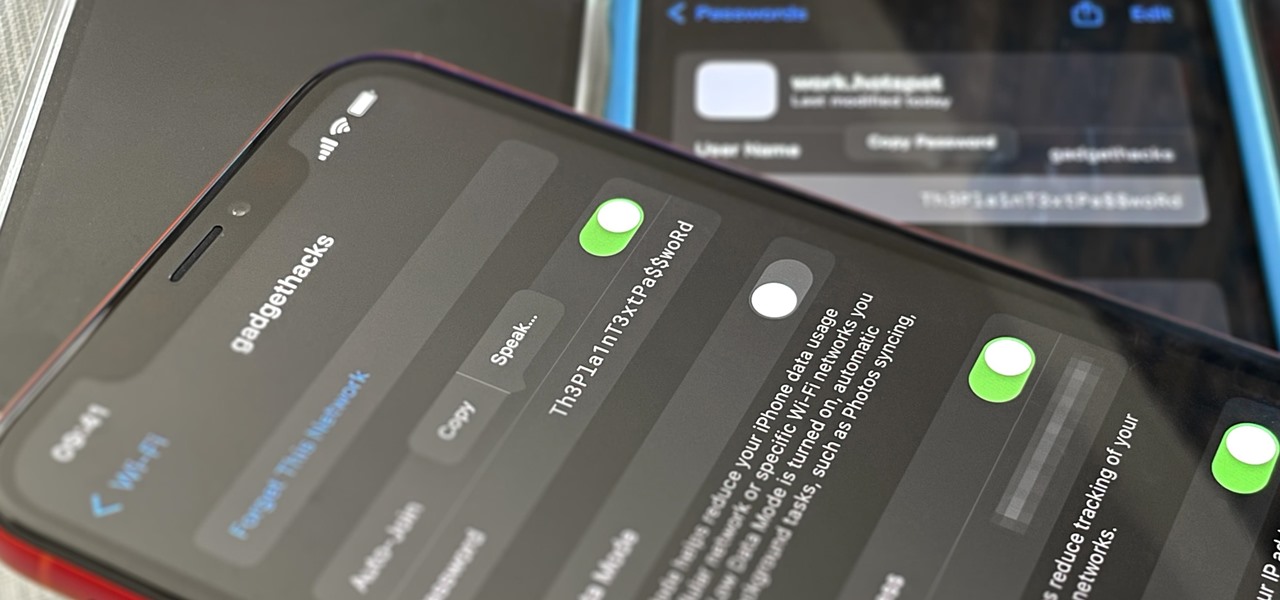
Your iPhone goes with you pretty much everywhere you go, and unless you have unlimited data on your cellular plan, you've probably connected to dozens of Wi-Fi hotspots over the years. Wi-Fi passwords are saved to your iPhone so you can auto-connect to the router or personal hotspot again, but finding the plain text password for a network hasn't always been easy.

One of the main goals of Google Wifi (and Nest Wifi after it) is to make managing your internet connections as simple as possible. A great example of this is how easy it is to prioritize one device and allot it more bandwidth when your network is bogged down with other traffic.

A virtual private network is a necessary part of your arsenal if you're insistent on surfing the web privately and securely on your iPhone. The App Store is littered with hundreds of different VPN services that encrypt traffic and mask your IP address, but what they all have in common are connectivity issues.

While augmented reality made more of a cameo appearance during Samsung's official grand unveiling of the Galaxy S10 line-up on Wednesday, it's the company's move into 5G connectivity that has huge implications for AR.

The most common Wi-Fi jamming attacks leverage deauthentication and disassociation packets to attack networks. This allows a low-cost ESP8266-based device programmed in Arduino to detect and classify Wi-Fi denial-of-service attacks by lighting a different color LED for each type of packet. The pattern of these colors can also allow us to fingerprint the tool being used to attack the network.

It only takes a few commands to manipulate a MacBook's secure HTTPS traffic and pluck login passwords out of the encrypted data. Let's take Facebook and Gmail hacking to the next level by intercepting Safari and Google Chrome web traffic in real time.

Nmap is more powerful than you know. With a few scripts, we can extend its functionality beyond a simple port scanner and start to identify details about target servers sysadmins don't want us to know.

The pending union between Prince Harry and American actress Meghan Markle is almost guaranteed to set the internet ablaze as millions tune in to experience the spectacle and pageantry of such a momentous event. If you've cut the cord and are wondering where you can stream the royal wedding for free, we've got you covered.

Hashes containing login passwords are transmitted between Windows computers on local Wi-Fi networks. By intercepting and decrypting these hashes using Responder and John the Ripper, respectively, we can learn a target's login credentials which can be later used to gain physical access to their computer.

The public leaks of NSA tools and information have led to the release of previously secret zero-day exploits such as EternalBlue, which was used in the notorious WannaCry ransomware attack. Despite multiple patches being released, many users have failed to update their systems, so many devices are still vulnerable to these now-public attacks.

The Watch Dogs video game series came out in 2014, enamoring audiences with the idea of a seemingly magical smartphone that could change traffic signals, hack web cameras, and even remotely control forklifts. This may sound like science fiction, but The Sonic uses a customized flavor of Kali Linux to allow you to unleash the power of Kali from any smartphone — all without the need to create a hotspot to control it.

Armis Labs has revealed eight vulnerabilities, called "BlueBorne", which put 5.3 billion Android, iOS, Windows, and Linux devices that use Bluetooth at risk. With it, hackers can control devices, access data, and spread malware to other vulnerable devices through networks. In this post, we will learn about the vulnerabilities, then look at how to find devices that have them.

Surveillance is always a useful tool in a hacker's arsenal, whether deployed offensively or defensively. Watching targets yourself isn't always practical, and traditional surveillance camera systems can be costly, lacking in capabilities, or both. Today, we will use motionEyeOS running on a Raspberry Pi Zero to create a small, concealable Wi-Fi connected spy camera that is both affordable and easily concealed.

When hacking into a network during a penetration test, it can sometimes be useful to create your own wireless AP simply by plugging a Pi into an available Ethernet port. With this setup, you have your own backdoor wireless connection to the network in a matter of seconds. Creating an AP is also helpful while traveling, or needing to share a connection with a group of people.

Hacking from a host machine without any form of proxying is reckless for a hacker, and in a penetration test, could lead to an important IP address becoming quickly blacklisted by the target. By routing all traffic over Tor and reducing the threat of malicious entrance and exit nodes with a VPN, we can configure Kali to become thoroughly private and anonymous.

Who pays for live TV anymore? Better question, who watches live TV anymore? With a ton of streaming services available, there's no room in our lives for things like schedules, commercials, or going weeks between episodes. (What is this, 2010?)

Most of us skip through documents like privacy policies and EULAs (end-user license agreements) because they're long and boring. But, as Congress just passed the SJR34 bill in early April, you're probably a little concerned about your personal data, so we summarized the privacy policies for major ISPs and mobile carriers in the US.

The Shadow Brokers, a hacker group known for its dump of NSA hacking tools in 2016, has just leaked their remaining set of data which implies that the NSA compromised SWIFT, the global provider of secure financial services, to spy on banks in the Middle East.

Copying files from a computer to your Android device has always been pretty straightforward—just connect the two devices with a USB cable, open your desktop file explorer, then move the files over. But what if you didn't need any wires at all?

So you're finally ready to head out on that big trip you've been planning for months, huh? It's an exciting time, but there are plenty of things you'll need to prepare before you head out. For instance, it's hard to imagine life without a smartphone these days, and with useful traveling apps like Google Translate and maps, you'll almost have to make sure that you have a working smartphone when you arrive at your destination.

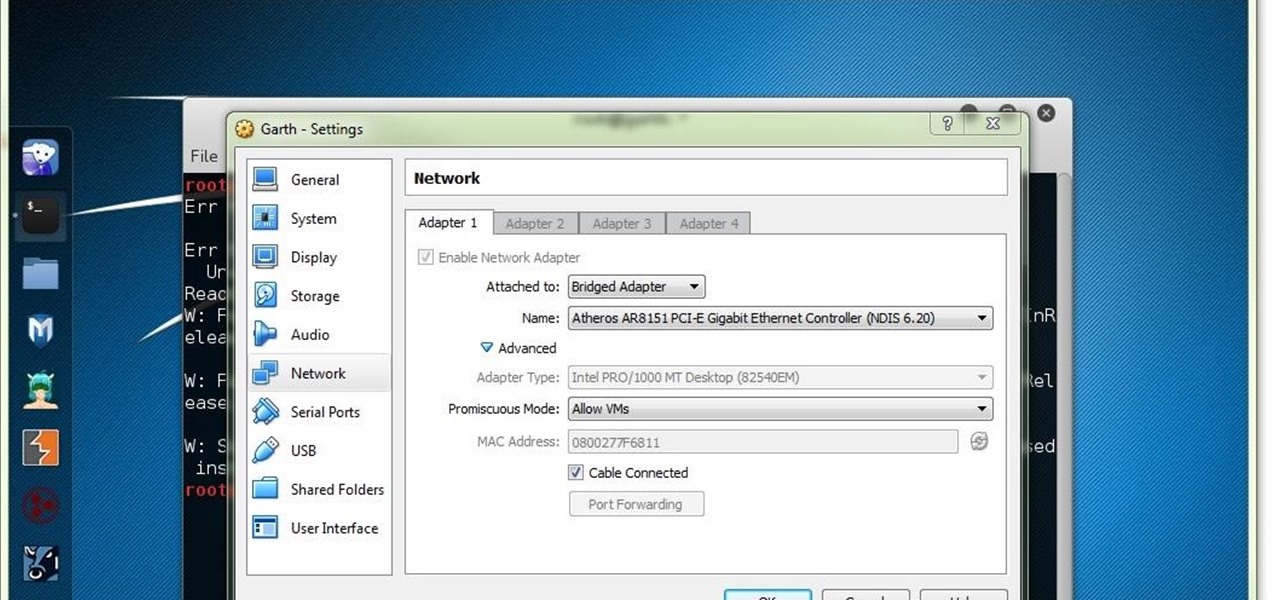
I have came across a lot of members on the forum that didn't have a clear idea of what port forwarding is and what it does. So...Let's get started...

Good day people, today we will examine some basic, for some people well-known attacks, also we will take a look at some advanced attacks.

Hello y'all! I apologize if this question has been solved somewhere else, but I have looked around on Google, Yahoo, and Null Byte and have not been able to find any working solutions.

Welcome back, my tenderfoot hackers! A number of you have written me telling me how much you enjoy the Mr. Robot series on USA Network. I am also a huge fan! If you haven't seen it yet, you should. It may be the best show on TV right now.