Apple introduced iMessage effects in iOS 10, which offer creative ways to send messages to other iPhone users. These effects can either be applied to the screen, like seeing an explosion of confetti falling down the display, or to the message bubble itself. iOS 11 brings two new screen effects to iMessage, named "Echo" and "Spotlight," and they look like they'll be a fun addition to the current lineup.

With autonomous technology being developed so quickly, auto companies have begun working on the next step in driverless development, passenger safety. German automotive supplier ZF has begun giving this some thought and has come up with a new kind of airbag, one that could define safety features in autonomous vehicles.

It wasn't too long ago that Uber threatened to fire star engineer Anthony Levandowski. Eleven days to be exact. If Levandowski didn't turn over the documentation he allegedly stole from Google's autonomous car division, Uber informed Levandowski that they would take "adverse employment action." Today, The New York Times reported the ride-sharing firm has delivered on that threat. In a memo sent to employees Tuesday morning, Uber announced Lewandowski's official departure from the company "eff...

Sherif Marakby has returned to Ford as the VP of AVs & Electrification after a brief stint with Uber. Marakby's VP title will be effective June 12.

Mitochondria are known as the powerhouses of our cells because they generate energy to power them. But they also play a key role in the death of cells when they're damaged, infected, stressed, no longer needed, or at the end of their life.

The force is strong with this project. Colin Furze is a British YouTuber who is a self-proclaimed "garage inventor and video maker." In a recent collaboration with eBay, Furze created the "ultimate Star Wars project," an 18-feet-tall playhouse version of the AT-ACT from Rogue One: A Star Wars Story.

The best way to spread Christmas cheer is singing loud for all to hear, right? Wrong.

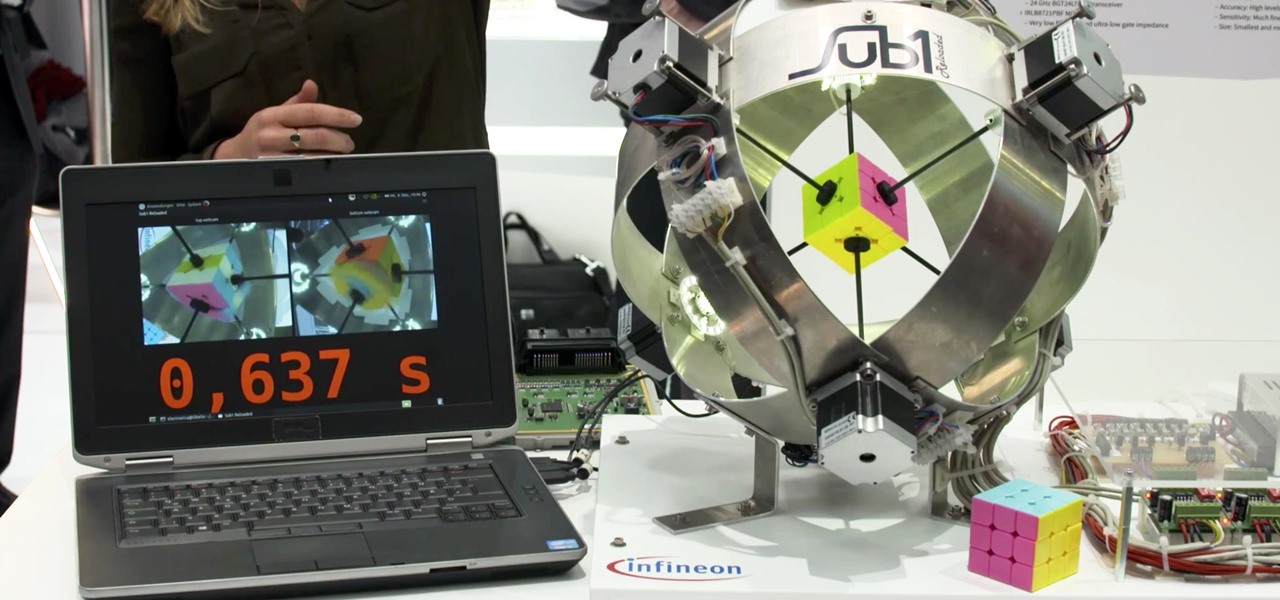
In December of last year, Australian Feliks Zemdegs broke the human world record for solving a Rubik's Cube with a time of 4.737 seconds. Well, this robot did it way, way faster by solving one in under 1 second. Don't tell me a robot takeover isn't real possibility.

We've seen plenty of good, bad, and weird things that have come out of the worldwide augmented reality game Pokémon GO, including murder and location-based bans, but nothing on a large scale. That was, of course, until Iran decided to ban the game country-wide.

Walking, talking, life-size holograms aren't just for staging Hatsune Miku concerts and reviving Tupac, Michael Jackson, and other fallen stars.

Virtual reality is all the rage these days, especially with devices like the Oculus Rift, Gear VR, and HTC Vive hitting shelves lately. But before any of those fancy, expensive headsets ever made it to the market, Google came up with a thrifty and inventive substitute in the form of Google Cardboard.

Computer cables tangle and get in the way, but Mobile Accessory Project hopes to solve that with CONNEX, a flat cable shaped like a credit card which expands up to 1.5 feet.

There may be worse feelings than sitting around waiting for food delivery, but I don't want to know what those are. Especially when your local delivery guy misses your address for the eighth time. But soon, Domino's Pizza will take that stupid human error right out of the equation in the form of a robot that's only 3 feet high.

If we go by the timeline set forth in Back to the Future Part II, Nike's new HyperAdapt 1.0 with adaptable lacing is at least a year late. But HyperAdapt will do more than just automatically tighten your laces—sensors in the sole of the shoe will provide a "tailored-to-the-moment" custom fit to maximize comfort and function while you jog, play sports, or navigate through hordes of aloof morons clogging the lanes at your local Trader Joe's.

Since it was released last fall, Super Mario Maker has offered us a glimpse into the minds of some of the most evil people on the planet. The game, for Nintendo Wii U, lets players create their own Super Mario levels using a deep list of objects, enemies, and green pipes, which can then be uploaded for anyone to play.

Google announced today that it's offering rewards to Android Pay users, and taking advantage of these deals could land you a free 2nd Generation Chromecast, among other prizes. The Tap 10 promotion is pretty self-explanatory: Tap to use Android Pay 10 times before February 29, 2016, and Google will give you a code to redeem a free Chromecast, free music, or both. You'll also be rewarded for Taps 1 through 9 as well. You'll receive a code for one music track from the Google Play Store for ever...

Welcome hackers. Hackacademic.RTB1 is vulnerable machine for training our skills.This machine can be download from free from here. There is many tutorial how to hack these machine but i did always be my self.
Hello Null-Byte community. First off: this my first post here on Null-Byte. Some of you may have already seen me in the comment section, to all others: Hi, I'm the new guy.

There are a lot of great tutorials on Null Byte using Python to create backdoors, reverse shells etc, so I thought it might be worthwhile making a tutorial on how to convert these python scripts to exe files for Windows victim machines.

Depending on your child's age, their first smartphone may be a little too open for them, or you, to handle. With essentially a world of information—both good and bad—available at their fingertips, it can seem like a huge hurdle to instill parental controls on their device.

With each day that dawns, there is a new, major hack that makes the news headlines. If you are paying attention, there are usually numerous hacks each day and far more that never make the news or are kept private by the victims. Every so often, a hack is so important that I feel compelled to comment on it here to help us learn something about the nature of hacking and IT security. This is one of those cases. Last week, the U.S. Office of Personnel Management (OPM) revealed that they had been ...

Snapchat developers insist that the app stay true to what its always been: a service for snapping and sharing self-destructing images. This belief is further hit home with their strict 31-character text limit, which some people refuse to abide by. Namely, Snapchatter Shayne Skellett.

Aside from the fact that it was the only game available on my cell phone at the time, I was really good at Snake. I still occasionally play it on my smartphone, but I've never been able to duplicate the same level of achievement as I once did.

During class or while at work, it can take an immense amount of self-control to resist navigating over to Reddit. The link-aggregator and meme-warehouse makes it too easy to kill time... most of which you should be spending on various other tasks.

I'm all about customizing my iPhone and making it as different as possible from everyone else's. While it's easy to change the wallpaper, swap keyboards, and hide apps on your home screen, there's not much else you can do aesthetically without jailbreaking, especially when it comes to the status bar and app icons.

Love or hate them, selfies are here to stay, and because of their rise in popularity, developers are clamoring to jump on the bandwagon. Most companies offer ways to add filters and share them, but few aim at changing the way the are taken.

Have a need for drama? Sick of doing kitchen prep and having no one appreciate just how much work you're doing? Then take a tip from a few seriously lazy cooks and peel a few pounds of potatoes in less than sixty seconds using a power hose, a bucket, a drill, and a cheap toilet bowl brush.

Since picking up your first crayon, chances are you've had a favorite, or dominant, hand. That hand gets you through the day, taking care of everything from writing to eating. If you've ever been forced to rely on your "wrong hand", you know how uncomfortable and unwieldy it feels.

John Frusciante, of Red Hot Chili Peppers fame, has just launched a new album, literally. His latest work, Enclosure, was loaded up on Sat-JF14 satellite inside the payload bay of the Interorbital Neptune Rocket on March 29th and launched into orbit.

You can easily level picture frames on your wall using your iPhone, but leveling the photos you actually take is a whole 'nother story. There are no built-in leveling tools in your stock Camera app, or in most camera apps for that matter.

With the Samsung Galaxy S5 all but assured to be showcased in a just a few weeks, we've got our hands on some fresh details of the upcoming flagship device.

So, I'm playing Injustice: Gods Among Us and whooping some serious superhero ass when out of nowhere I receive a stupid notification that ruins my game and subsides my thunder!

Ladies and gentleman, it's official—"Selfie" has been named Word of the Year by Oxford Dictionaries.

Instructions to make 3D origami of airplane similar to Airbus A380. It's self standing, made only with a folded paper (triangles). In video I tried to give instructions for every detail.

Welcome back, my fledgling hackers! The database is the hacker's "pot-of-gold," as it contains information that is very valuable to both the business and the hacker. In this, the second of my series on hacking databases, we're on the "hunt" for Microsoft's SQL Server. Although far from the most commonly used database (Oracle hold's that title), Microsoft's SQL Server is very often found in small-to-medium sized businesses. Even a few big businesses use it.

For the most part, transferring files from your computer to your Nexus 7 (and vice versa) is a simple process. Just hook up your tablet to your computer with the USB cable and transfer. However, most of the time you'll need additional software on your computer to do this, and then, of course, you need the USB cable.

Welcome back, my fledgling hackers! One of the first issues any hacker has to address is reconnaissance. Before we even begin to hack, we need to know quite a bit about the target systems. We should know their IP address, what ports are open, what services are running, and what operating system the target is using. Only after gathering this information can we begin to plan our attack. Most hackers spend far more time doing reconnaissance than exploiting.

In this short video tutorial, you will learn an easy technique on how to draw Chowder from the Cartoon Network series of the same name. For the full tutorial with step-by-step and speed control, visit SketchHeroes.

Learn how to draw Ben 10 from the famous Cartoon Network animated franchise. For the full tutorial with step-by-step drawing instructions and speed control, visit Sketch Heroes.