
News: Inside Bitcoin - Part 2 - Cryptographic Hashes
If you haven't read the last article, feel free to stop by and give it a read, but abstaining from reading it will not, for the most part, be detrimental to your understanding.


If you haven't read the last article, feel free to stop by and give it a read, but abstaining from reading it will not, for the most part, be detrimental to your understanding.
T-Mobile's "Uncarrier" initiative has done wonders for my wallet and my data usage. Before I had to deal with being throttled down to 2G speeds after passing my data limit, but thanks to their unlimited data plans, I'm free to use as much LTE data as I possibly can. The only downside is, when sharing data through a mobile hotspot (tethering), T-Mobile imposes a 5 GB limit (which was recently upped to 7 GB for some).

Hi there again, aspiring hackers (and veterans as well)! I'm going to explain how to perform a dictionary attack on a WPA/WPA2 protected network with Wifite. Please note that this doesn't work with WPA Enterprise For that end, you'd have to use an Evil Twin to get the "Enterprise" auth attempt, and then crack it.

Rumors have had Google making a foray into the mobile carrier world for quite some time, but today, the Mountain View tech giant finally made things official. The new service, dubbed Project Fi, will be a Mobile Virtual Network Operator, or MVNO, that uses existing Sprint and T-Mobile cell towers.
Collaborating with other people can be a pain, especially if you have to share one device between the entire group. Usually when you're creating a new design or trying to edit a mockup, you end up hunched around a single screen or end up emailing revisions back and forth, which can be difficult when you're short on time.

UPDATE 5/21/15

Sling TV, the new over-the-top TV streaming service from DISH Network, is the first to offer live programing for cord cutters. Available for $20 a month with no contract, Sling TV is the easiest way to end the reliance on cable and satellite subscriptions for getting your content as it airs.
iTunes Radio, Apple's answer to Pandora, provides endless hours of free music streaming, but like other so-called "free" services, every now and then you're going to hear some ads. While you may not be bombarded with them, they can definitely kill the vibe when you're jamming to your favorite stations.

Ever use an open hotspot on your Note 3, only to find out that it's severely restricted to what sites you can access? While getting online with free Wi-Fi is great for those who have a limited data plan, when that one site you absolutely need to visit is blocked, you're left frustrated and sent back into the Wi-Fi menu for another access point.

Remember the feeling you had the moment you removed your shiny new Nexus device from its packaging and booted it up for the first time? You swiped through the app drawer at lightning speed and thought to yourself, "This is the last Android phone I will ever need, they just aren't going to get any better than this."

While FIFA may be one of the most corrupt organizations in the world (depending on who you talk to), that won't stop millions of us from tuning in this Thursday, June 12th, to watch the first game of what's going to be a month-long World Cup affair.
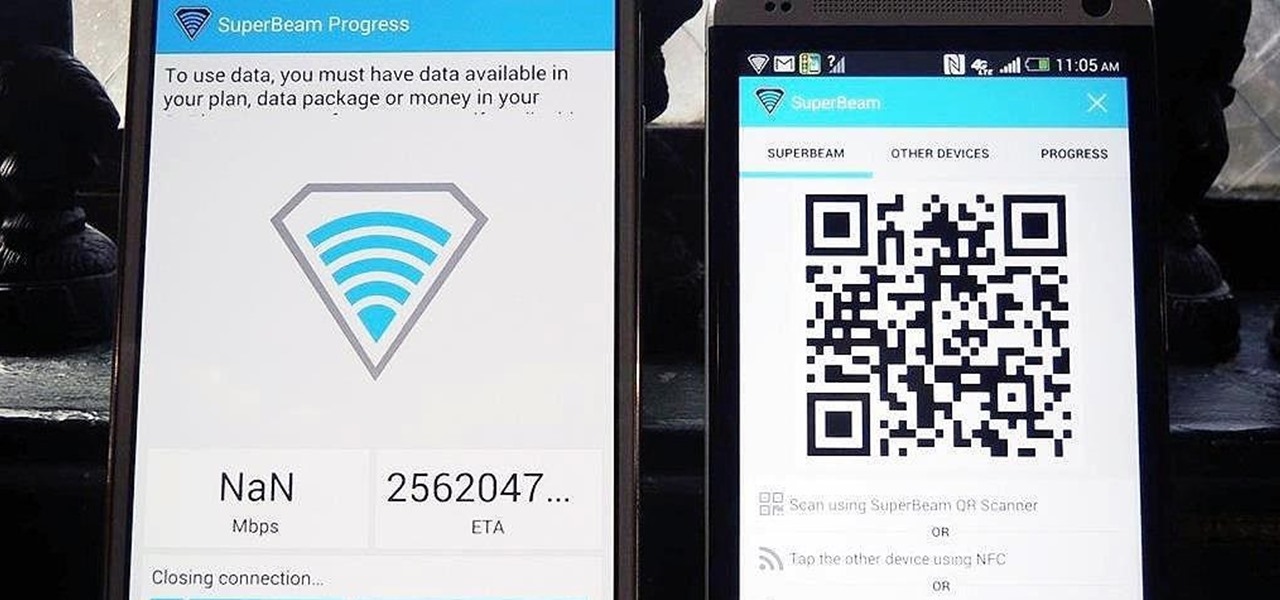
Sending and receiving files between Android devices has no shortage of options—Bluetooth, email, MMS, and Wi-Fi are just a few of the more popular ones that we use.

I have Verizon, America's largest 4G LTE network, as my cell service provider, but there are times when I find myself with a pretty shitty signal, rendering my upload and download speeds substantially slower than usual.

Welcome back, my neophyte hackers! Have you ever had a neighbor that you're certain is up to no good? Maybe you've seen him moving packages in and out at all hours of the night? Maybe you've seen people go into his home and never come out? He seems like a creep and sometimes you hear strange sounds coming from his home? You know he's up to no good, but you aren't sure what it is exactly.

Welcome back, my novice hackers! In a recent tutorial, I showed how the SNMP protocol can be a gold mine of information for reconnaissance on a potential target. If you haven't already, I strongly suggest that you read it before progressing here, as little of this will make much sense without that background.
Even if you have the fastest internet connection in the world, it's not going to be fast if your Android device isn't optimized to use all of the bandwidth. I have pretty fast speeds at home, but every now and then my web surfing on my Nexus 7 tablet is halted in its tracks—for seemingly no reason.

Video: . Optimize your Marketing with a Mobile Website

It doesn't really matter what kind of cell phone you have—battery life is one of the most important features for any electronic device. We've written tons of articles on how to get better battery life from your Android, iPhone, Kindle, and more, but we've never really covered Windows Phones before—until now. The Nokia Lumia 920 and other devices running Windows Phone 8 suffer from battery problems just like any other mobile device. So, if you've got one in your hands that can't seem to make i...
When LinkedIn first arrived on the scene, I thought it was a great resource for staying connected and getting in touch with those people in your desired career path. Keyword: Thought. Like most businesses, money and shareholders seem to have taken over the driver's seat, pushing the company towards a business-first, users-second approach.

Imagine you're in Paris and you need to get to Versailles. Looking around for directions, you come to a cold realization—you do not speak a lick of French! How are you going to get to Versailles and what happens if there is a detour? It will be a difficult struggle, and you'd probably get lost and eventually fail. This is why it's important to know some of the country's language before taking that trip in the first place.

In the last article, we left off with the Tor network and its hidden services. As I mentioned, Tor is not the only option in the game, and I want to offer a general introduction to I2P.

Originally made as portable convenience locks, padlocks are known for their cheap, simplistic and relatively secure design. Their construction is made up of a body, shackle and locking mechanism, with the shackle typically assuming a "U" shape to be easily linked to things like fences and chains.
In my early life I was deeply impacted by the work of physician and psychoanalyst John C. Lilly. I still have my dog-eared copies of The Mind of the Dolphin (1967) and Programming and Metaprogramming in the Human Biocomputer (1968). Lilly's work, with dolphins and the development of the sensory deprivation tank, has formed the basis of movies, music and television productions.

Here at Null Byte, we've spoken a lot about securing and anonymizing traffic. This is a big deal. With all of today's business taking place electronically via computers, we need to be secure when on-the-go. A lot of businesses don't even train their employees to secure their computers to protect from various threats. Here are a few things that should always happen when doing business on computers:

Social networks like Facebook and Google+ are great for staying connected with family, friends and coworkers—even fans. But sharing and communicating with practically anyone in the digital realm has alienated us from most of the flesh-and-blood beings we see everyday—our neighbors. How well do you know your neighbors?

MIMESIS n pl. -MESISES or -MESES mimicry MIMETIC adj 61 points (11 points without the bingo)

SSH is what is referred to as the Secure SHell protocol. SSH allows you to do a plethora of great things over a network, all while being heavily encrypted. You can make a remote accessible shell on your home computer that gives you access to all your files at home, and you can even tunnel all of your traffic to keep you anonymous and protected on public Wi-Fi. It has many great uses and is a must have tool for your arsenal. It was designed to replace the insecure Telnet protocol, which sends ...
ISOPLETH 63 points (13 points without the bingo) Definition: a type of isogram [n]

Electronic Arts is the biggest game publisher in the world, and have been for years. And yet, their only successful internally developed games nowadays are the EA Sports mega-franchises like Madden. Most of their success has stemmed from their ability to buy other companies on their way up, squeeze the creativity out of them, and then sell them to someone else or just let them go. This week they made their largest acquisition ever when they purchased PopCap Games for $750 million upfront—as m...

You're sitting in your favorite café enjoying a hot cup of joe, then you open up your laptop or turn on your tablet computer to get to work, but as always you get sidetracked and head straight for Facebook. Someone just tagged you in a photo, so you check it out, then you see it out of the corner of your eye—your Facebook picture digitally displayed on the wall in a nice, neat digital photo frame.

Giveaway Tuesdays has officially ended! But don't sweat it, WonderHowTo has another World that's taken its place. Every Tuesday, Phone Snap! invites you to show off your cell phone photography skills.

Giveaway Tuesdays has officially ended! But don't sweat it, WonderHowTo has another World that's taken its place. Every Tuesday, Phone Snap! invites you to show off your cell phone photography skills.

BEST PICTURE, ACTRESS, DIRECTOR, FILM EDITING, CINEMATOGRAPHY: I would go to the ballet all the time if it was this cool!

It looks like Sony is adding some cool features to their upcoming portable game system called NGP (Next Generation Portable).

The point of any workout is to stress your body and initiate an adaptive training response. Period. What are appropriate levels of stress necessary to achieve the adaptive response? In terms of the cardiovascular system, studies have shown that it usually takes about two minutes to get the heart rate into the training zone. Once there, the heart shows an adaptive response after five more minutes of training in the zone. Total minutes needed to get an adaptive response from your heart? Seven.

Laser gun + killing mosquitoes = lots of little boy fun, but what's it all about? Quite possibly the most entertaining, thrilling, and well, downright life-saving presentation at this year's TED conference was Intellectual Ventures' mosquito death ray.

This how-to is aimed at the uncynical, bright-eyed outsider who wants to become a television producer…the talented person who believes he or she has the ‘it’ to crack Hollywood. The ‘Sammy’ who just arrived in 90210.

Firefox's hidden advanced menu gives you several ways to tweak the way it works under the hood. Here are a set of settings to change to get it to browse faster than ever.
HOW TO CAPTURE STREAMING MEDIA many websites stream songs and videos

What is it about the fantasy of the treehouse? Escapism. Other worldly, bird-like elevation. Beauty and peacefulness. Backwoods simplicity (although in some cases, truly elaborate works of fine architecture). Whatever the draw is, I'm dying to have my own treehouse in the woods, and I'd gladly take any of the examples below.