
Waymo Was Right: Why Every Car Maker Should Skip Level 3
Most carmakers now agree with Waymo that piloting driverless cars is best left to the machine — with no meddling from the human.


Most carmakers now agree with Waymo that piloting driverless cars is best left to the machine — with no meddling from the human.

Uber's driverless car program lead has quit after just one year working for the ride-hailing company.

Most of us skip through documents like privacy policies and EULAs (end-user license agreements) because they're long and boring. But, as Congress just passed the SJR34 bill in early April, you're probably a little concerned about your personal data, so we summarized the privacy policies for major ISPs and mobile carriers in the US.

When we talk about driverless technology, the go-to companies are usually Waymo, Uber, or Tesla. However, traditional automakers like Ford and GM are also staking claims to the driverless and advanced driver assistance spaces.

Ask anyone that works on the development of driverless vehicle technology and there is a very good chance that AutonomouStuff will have supplied something to their project.

I've seen my fair share of heartbreaks when it comes to used phones. As a repair tech, I often had to try and help out customers who bought used handsets which turned out to be useless, either because it was stolen or not working on their carrier's network. More often than not, there was very little I could do. To help you from being stuck in the same situation, here are some tips to prevent you from getting scammed out of your hard earned money when buying a used handset.

There was once a time when everyone scoffed at the turmeric tonic tea sold at the coffee shop I work at. Funny, because as of recently, we seem to be selling out. How can this be explained? Beyoncé must have been spotted buying turmeric beverages on the cover of some celebrity magazine. That's got to be the only way to explain its sudden popularity, right?

Augmented, mixed, and virtual reality are all a little bit different, but as many expect—including Metavision—the continuum of our next realities will converge and give us one head-mounted display (HMD) platform that can do it all. If Vrvana, a Canadian company building AR and VR headsets, succeeds, that convergence could begin as early as next year.

The biggest corporation we know today is called Google, I bet you've heard of it yeah? How Google Tracks You:
Hello everyone! This is my first attempt at a tutorial here. There are a couple great assembly tutorials here, and I wanted to toss my coin in the fountain.

Hello NullByte, it's mkilic! This time I'm here with the C.H.I.P from NTC. Although it is not too popular, the C.H.I.P is a brand new micro computer. It is very similar to the Raspberry Pi or Beaglebone Black. The key difference with this particular board is its cost and size. The C.H.I.P only costs $9 and measures 2.5 x 1.5 inches. In addition to this, the C.H.I.P has built in 802.11 b/g/n Wifi and Bluetooth 4.0. Considering these great specs, what could a Hacker use this for? Step 1: The In...

Hello there, reader! If you've clicked on this How-to then it means you are interested in learning some C programming or just generally curious about what this page has to offer. And so I welcome you warmly to the first of many C tutorials!

Cheap Chinese knockoffs have been around for ages, but recently, skyrocketing demand has led to a massive influx of counterfeit smartphones. Sellers on Craigslist seem to have no trouble getting ahold of these fake devices, then passing them off as the real deal and turning a solid profit before vanishing into thin air. This type of scam tends to happen even more frequently after Apple launches a new iPhone or Samsung debuts a new Galaxy.

Task Manager got revamped quite a bit in modern versions of Windows. First introduced in Windows NT 4.0, it's become pretty popular among more advanced users. In Windows 10, Task Manager is not just a task manager anymore, it's also a system monitor, startup manager, history viewer, user controller, and the list goes on.

Programming is an essential thing in hacking/pentesting, and at times, I do not feel that it is being addressed enough here, at Null-byte. I understand that this is a forum dedicated for hacking, but I'll address some of the stuff I feel is muy importante about programming. I am not a professional programmer, but I do have experience and I do want to share some of the stuff professionals have taught me.

Apple just showed off iOS 9 and its new features at WWDC 2015, including multitasking support for iPads (finally!), a new Low Power Mode to save battery, local area search and transit directions in Maps, a highly improved "Proactive" Siri, a better Spotlight search, new apps, and so much more.
Hello and welcome to my article. I have made this article for anyone who wants to become a hacker, and wants to know how to get started.

Hi everyone! In the previous part of this series, I introduced one way to hijack a program's execution flaw, though I only showed you how to crash the program and left you with a little mystery to solve. Today we are giving the solution of that and then introducing shellcode usage and remote command execution.

Hi everyone! Last time we finished analyzing the assembly representation of our vulnerable piece of code (have I ever told you it is vulnerable?). This time we are going to introduce some fundaments about exploitation by demonstrating how to crash a program's execution. If that sounds lame, next time we will see how this crash can in fact be useful to control the program's execution, achieving remote code execution!

Cheese might be one of the most satisfying snacks around, whether you prefer a slice of snappy Irish cheddar or a creamy, rich portion of Brie. It's been called "dairy crack" by a respected physician and for good reason: eating cheese produces casomorphins, which effect the human body like opiates. It also contains trace amounts of actual morphine.

When it comes to getting your computer and smartphone to work well together, there's no service more robust and capable than AirDroid. For years, it's been the go-to tool for users looking to transfer files between their devices or access contact lists and call logs from their computer.

Having a dust- and water-resistant phone is truly useful, but it comes with a price. In order to achieve this functionality, Samsung had to literally plug up any holes in the Galaxy S5, and this included the charging port.

Apple announced the successor to Mac OS X Mavericks at their Worldwide Developer's Conference 2014, and it's called Yosemite. Named after California's Yosemite National Park, it will be available as a free upgrade from the Mac App Store for everyone this fall.

It's officially the holiday season, which means everyone will soon be traveling home to spend time with loved ones. And anyone who has any knowledge whatsoever of computers knows what else that means—family members left and right asking you to fix their various technical woes.

Welcome back, my greenhorn hackers! Now that we're familiar with the technologies, terminology, and the aircrack-ng suite, we can finally start hacking Wi-Fi. Our first task will be to creating an evil twin access point. Many new hackers are anxious to crack Wi-Fi passwords to gain some free bandwidth (don't worry, we'll get to that), but there are so many other Wi-Fi hacks that are far more powerful and put so much more at risk than a bit of bandwidth.

As a former English major, I have a love/hate relationship with many books. And when I saw that this NFC-enabled charging dock project included a little book mutilation, I was suddenly more interested. Now, for those of you who have nothing against books, this is still a great project to add some style to your tech devices.

In this article, I'll be continuing my series on microcontrollers. If you haven't read part one, I'd recommend heading over there and reading it!
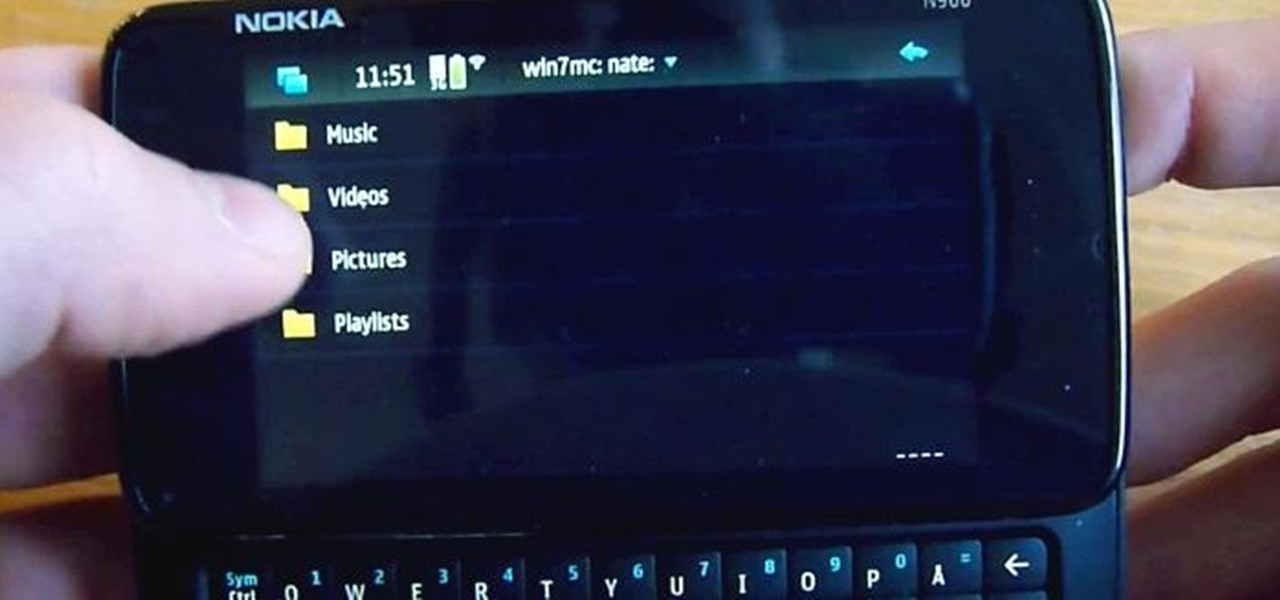
Having access to your computer from your cell phone is an extremely useful feature. Whether you need to edit documents or send files that are on your home desktop, or you simply want to watch movies you have saved on your computer, access is key.
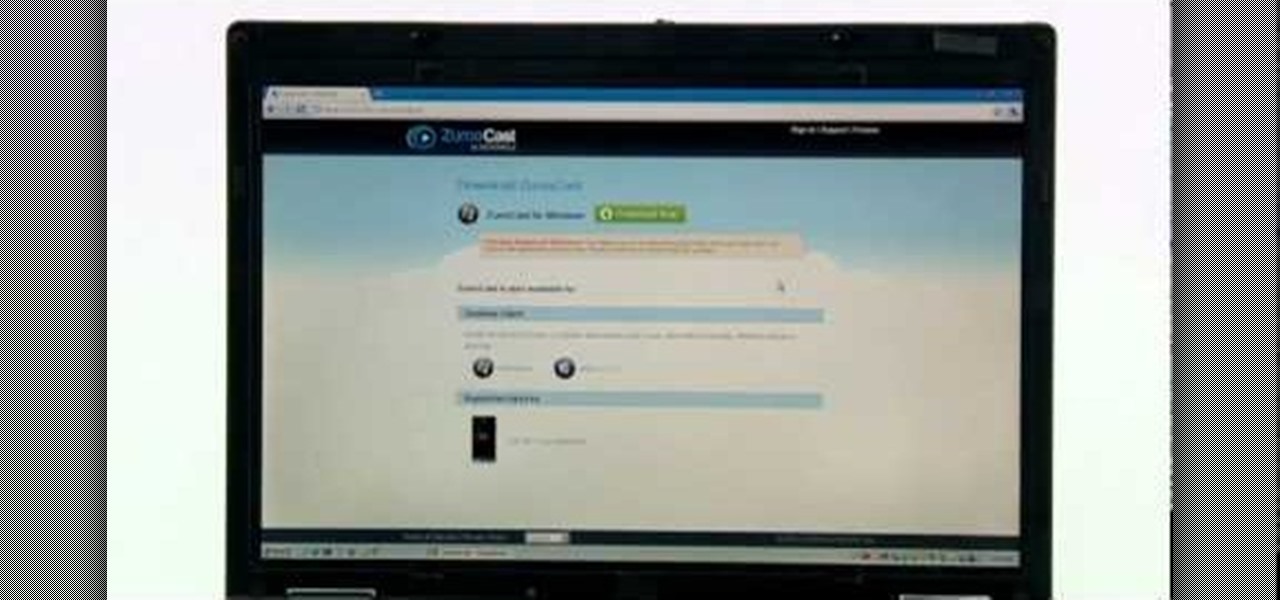
The Zumocast app allows you to stream music, movies, or pictures directly from your work or home computer to your Droid Bionic smartphone. The Android device can also access documents or other files located on your PC using the program. This Motorola support video will walk you through the process.

Here at Wonder How To we've seen a look of "how to look like so-and-so" makeup videos. Lots of them are good, but this one, which teaches you how to look like super sexy siren Gem from "Tron: Legacy," truly takes the cake.
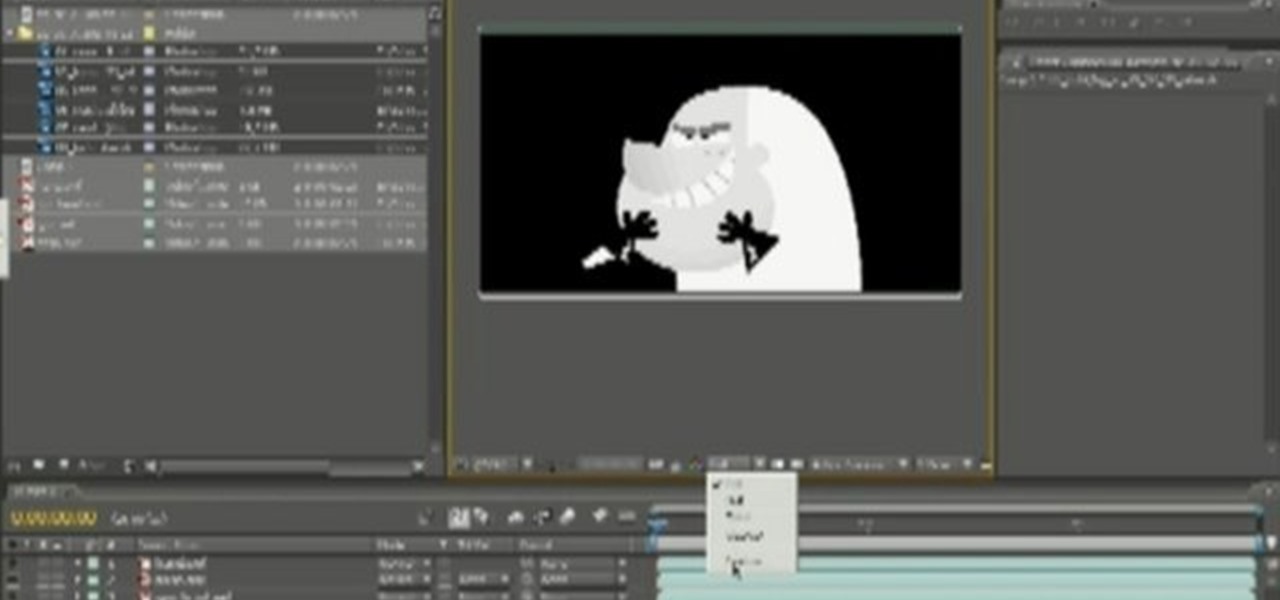
Here's a useful technique for any animator to be able to pick up - give your anaglyph animations a 3-D look. To replicate this, you will need Flash, After Effects and Photoshop, or programs that can accomplish similar animation tasks.

In this video, you'll learn how to convert format files accurately and for free in two different ways. You can use a program called Format Factory, which you can download here, or you could use a website called Zamzar.
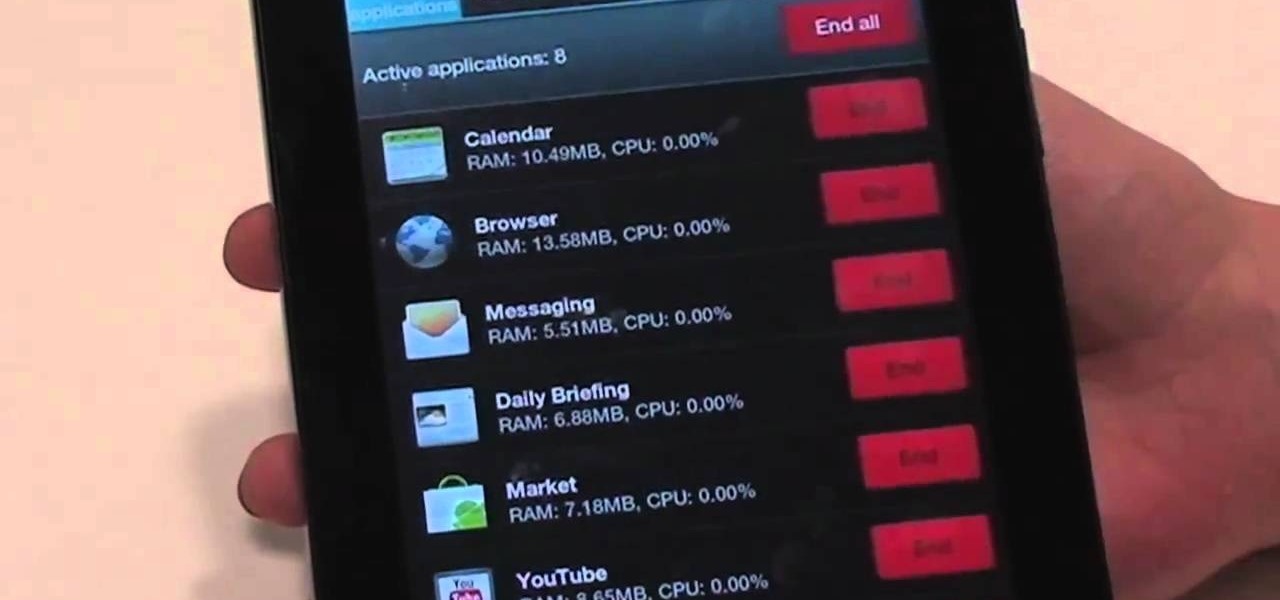
Nobody likes a wasted battery. That's why it's important to make sure you close all of the running Android apps that you don't need. On the new Samsung Galaxy Tab, it's easy to eliminate those battery-draining apps via the Task Manager. See how to access it and how to clean up the mess!

Want a professional way to deliver your video blog presentation without relying on notes or having to memorize every line? All you need is some paper and a CD case, and either a smartphone or a laptop to set up your own free teleprompter program.

This tutorial shows you how to use your favorite drawing or art program (like Photoshop or GIMP) to create your own digital painting of Raiden, a character from the popular video game Metal Gear Solid. After creating the basic sketch, this video shows you how to create your own painting.

Don't hunt for that icon, make any Windows program you want launch at the stroke of a key. For more information, including detailed, step-by-step instructions on how to create your own custom keyboard shortcuts on a Microsoft Windows PC, watch this helpful home-computing how-to from CNET.

In this clip, you'll learn how to convert a Microsoft Windows desktop or laptop computer into a personal web server (or webserver) with XAMPP, an Apache distribution that compes preloaded with PHP and MySQL. Whether you're new to the PHP: Hypertext Preprocessor scripting language or are a seasoned web developer merely looking to improve your chops, you're sure to find benefit in this free video programming lesson. For more information, including detailed, step-by-step instructions, take a look
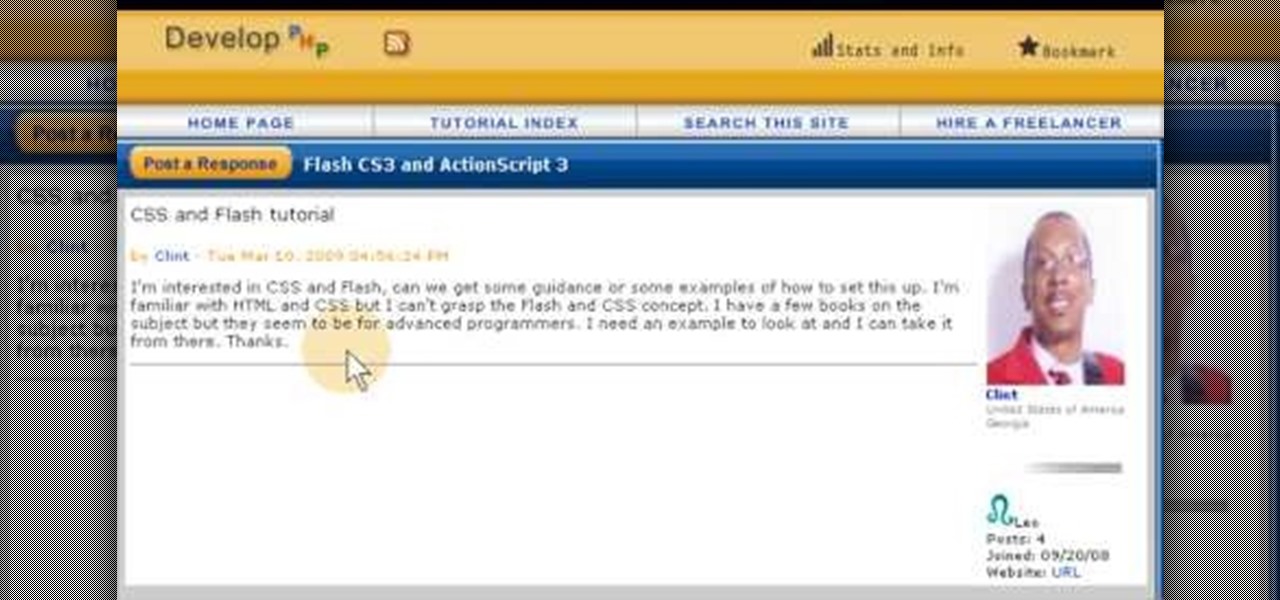
A style sheet can ensure a uniform appearance for your website, as it gives you the ability to standardize font appearance, layout and spellings of unusual words on your website. This tutorial shows you how to create a style sheet and then import it into the Adobe Flash CS5 program using ActionScript 3.
For first time users of Dreamweaver, this tutorial shows you how to begin designing your own new website. Start from creating a new site entirely, and then set up the program and your website to look exactly how you want it.

This video covers the Expo plugin in Ubuntu Linux, which is similar to the Exposé feature in Mac OS X. The Expo feature can be found in the Advanced Desktop Effects Manager. Once you enable it and tweak the options, you'll be able to view multiple workspace areas at once and manipulate your running programs between them. Check out all of the other desktop effects.