Developers creating login systems know better than to store passwords in plain text, usually storing hashes of a password to prevent storing the credentials in a way a hacker could steal. Due to the way hashes work, not all are created equal. Some are more vulnerable than others, and a little Python could be used to brute-force any weak hashes to get the passwords they were created from.

Less than two months after launching its augmented reality platform for casual gaming and shared experiences, Snapchat is ready to make Snappables available to advertisers.

Less than two months since unveiling Project North Star, Leap Motion has released the reference design that will allow developers, makers, and even manufacturers to build their own augmented reality headsets based on Leap Motion's work.

As Facebook, Apple, Samsung, and others offer augmented reality selfie effects and content that challenge its platform, Snapchat has continued to innovate with its augmented reality capabilities.

If you have yet to receive your invitation to next weekend's royal wedding in the UK, then you can still experience part of the pomp and circumstance in augmented reality courtesy of ABC News.

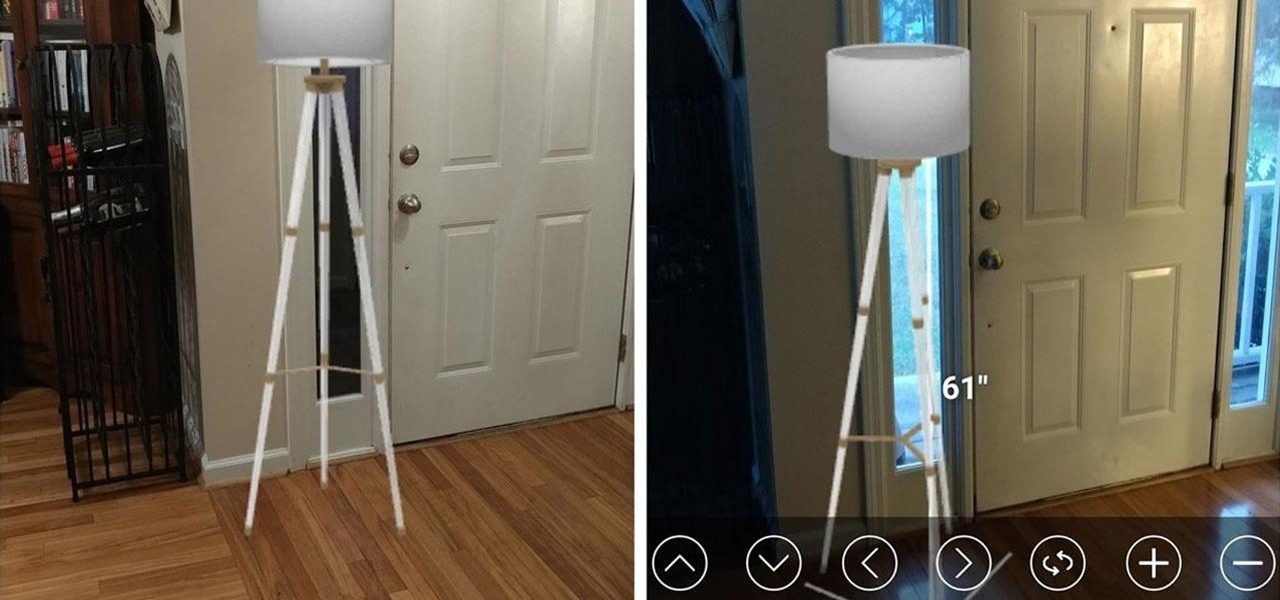
Microsoft's Monday keynote introduced the fourth generation of the company's Kinect sensor during Build 2018 in Seattle.

Last month, we told you about U2's new augmented reality-powered music tour. But if you don't have the means to travel to the show, the group recently revealed an inside look at what it will be like and what inspired the band to dive into immersive technology.

During Snap Inc.'s quarterly earnings report, released on Tuesday, the company disclosed that it snagged a revenue total of $230.8 million for the first quarter of 2018, an increase of 54% compared to last year, largely fueled by its augmented reality offerings and other advertising products.

If $200 was too much for you to get in on some Star Wars augmented reality action, Best Buy is now selling refurbished Star Wars Jedi Challenges sets for $79.99 and new ones for $99.99.

French automaker Renault is tapping into the promotional machine for Solo: A Star Wars Movie by deploying an AR experience through Shazam that's triggered via synergistic advertising.

While Apple usually sets the precedent for its consumers to follow, the iPhone SE returned the company's iconic smartphone to a small form factor, one that had been ditched by the iPhone 6 and beyond. However, it appears Apple is finished with 4-inch phones for good, as the iPhone SE 2 looks to be even larger than last year's iPhone X.

While Magic Leap may have plans to eventually introduce sign language translation for smartglasses in the near future, students at New York University have demonstrated that such a feat is possible today with a smartphone and a prototype app.

Update February 25: The Nokia 9 PureView was announced at Mobile World Congress! Read all of the official specs and details at our full rundown of Nokia's latest flagship.

It's human nature to wonder if the grass is greener on the other side. This is no more true than for people who use iPhones, and those who use Galaxy S phones. While iPhones were initially the gold standard for smartphones, Samsung's phones equal them in many ways and surpass them in others. If you use an iPhone and you're on the fence, here's the case for making the switch to a Galaxy S9 or S9+.

It's been a long time coming, but Tamagotchi has finally ditched its iconic toy egg and arrived as a mobile game. The new iteration is called My Tamagotchi Forever, and though it's currently only available in Canada, you can actually download the game anywhere and care for your very own virtual pet right now.

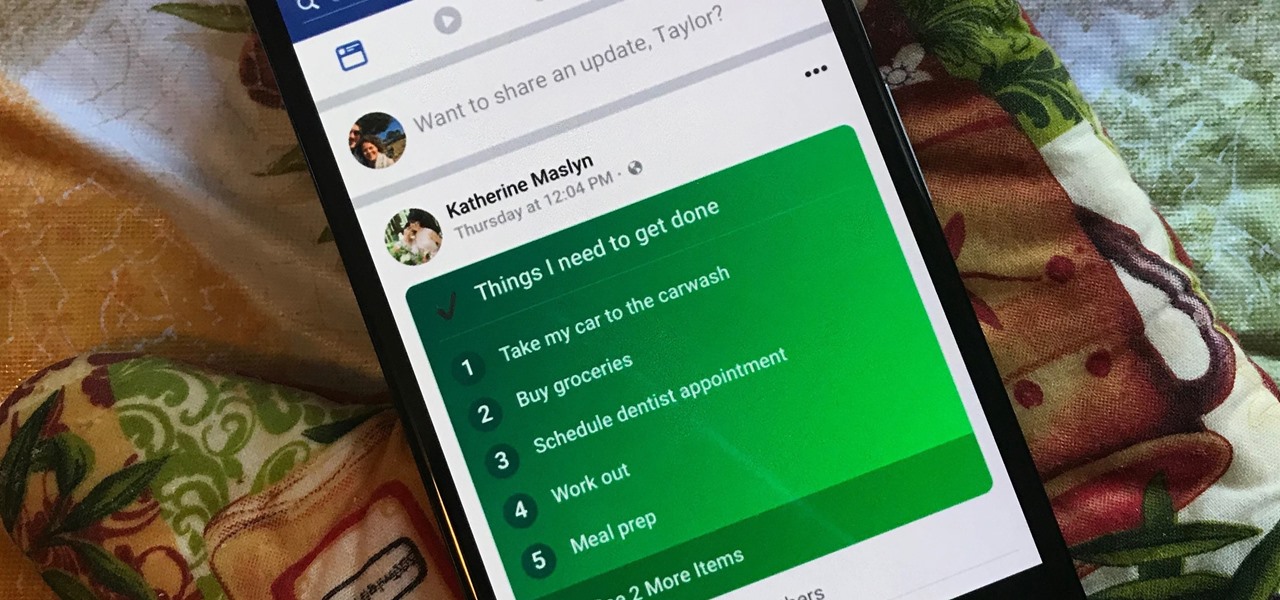
Facebook's status update box has received many new features over the years. You can go live, sell something, and even create a poll. But since all this was added, the status update box has been relatively stagnant. That's finally changing again with Facebook's newest addition: Lists.

After hosting millions of free 3D models online, Sketchfab is betting that augmented reality and virtual reality developers and creators will be willing to pay for premium 3D content.

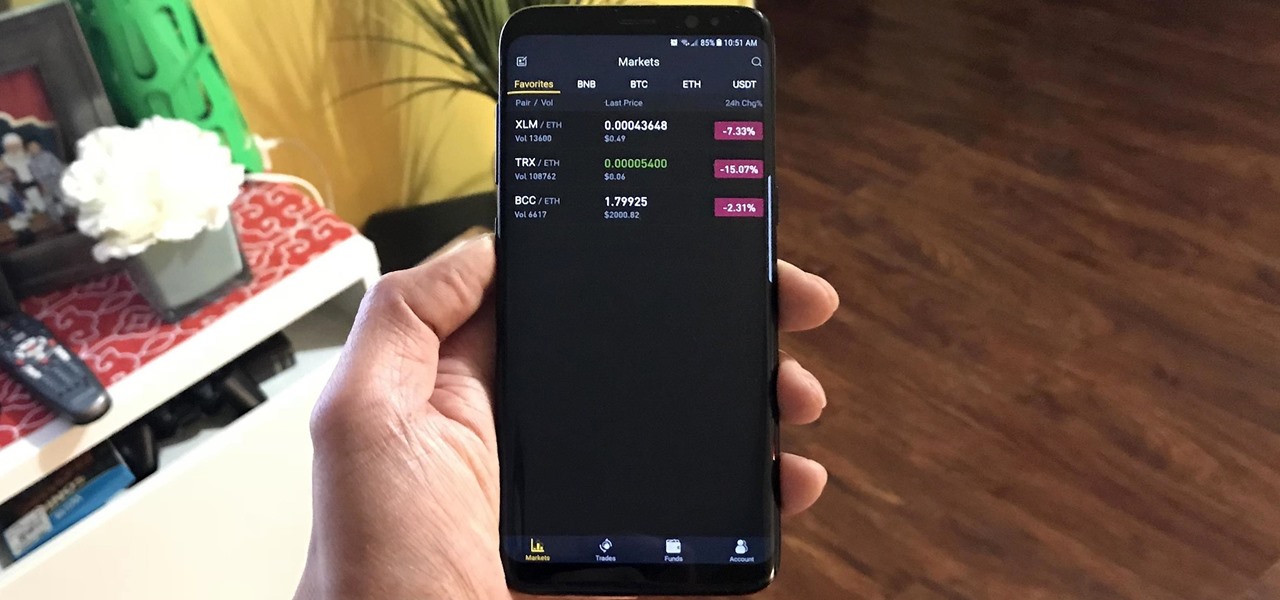
With the sheer number of alt-coins that you can buy and sell on Binance — Ripple (XRP), Stellar (XLM), and NEO to name a few — keeping track of coins you're interested in is a hassle. But with the tap of a button, you can mark trades and alt-coins that are on your radar for quick access on your Binance account.

For some, going to the dentist can be a terrifying experience, but a new use of augmented reality could go a long way toward making the trip feel more like it's worth the orthodontic angst.

The reveal of Magic Leap One: Creator Edition brought with it some insight into the path the device took from prototype to "final" design.

Just as the Transformers animated TV series of the '80s were basically half-hour commercials for toys, a new Transformers AR app for iOS similarly functions as a promotion for the latest installment in the film franchise.

If you're a regular reader of Next Reality, you're more likely to spread the joy of augmented reality than most others. But it can be difficult to introduce newbies into the AR fold if you don't give them exactly the right starting point in terms ease-of-use and affordability. But fear not, oh gift-giving AR pioneer, we're here to help!

Most of the free apps you'll find on the Play Store have ads. These ads are personalized — in other words, they're for products and services Google believes you might be interested in. The way Google knows about your interests is by collecting data from your smartphone, including your location and app usage. While personalized ads have their advantages, the collection of data is unsettling.

If you've ever wanted to be a graffiti artist, but you also frown upon vandalism, then augmented reality is for you.

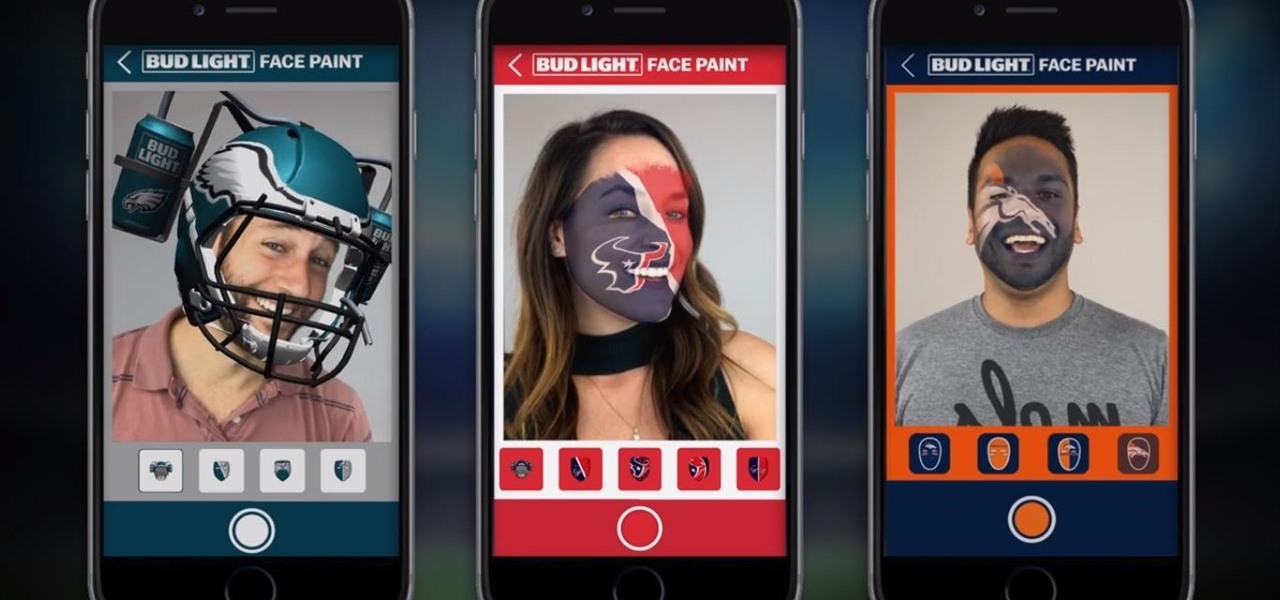
The bandwagon for NFL teams using augmented reality to engage fans isn't exactly full, but it is starting to get a bit crowded.

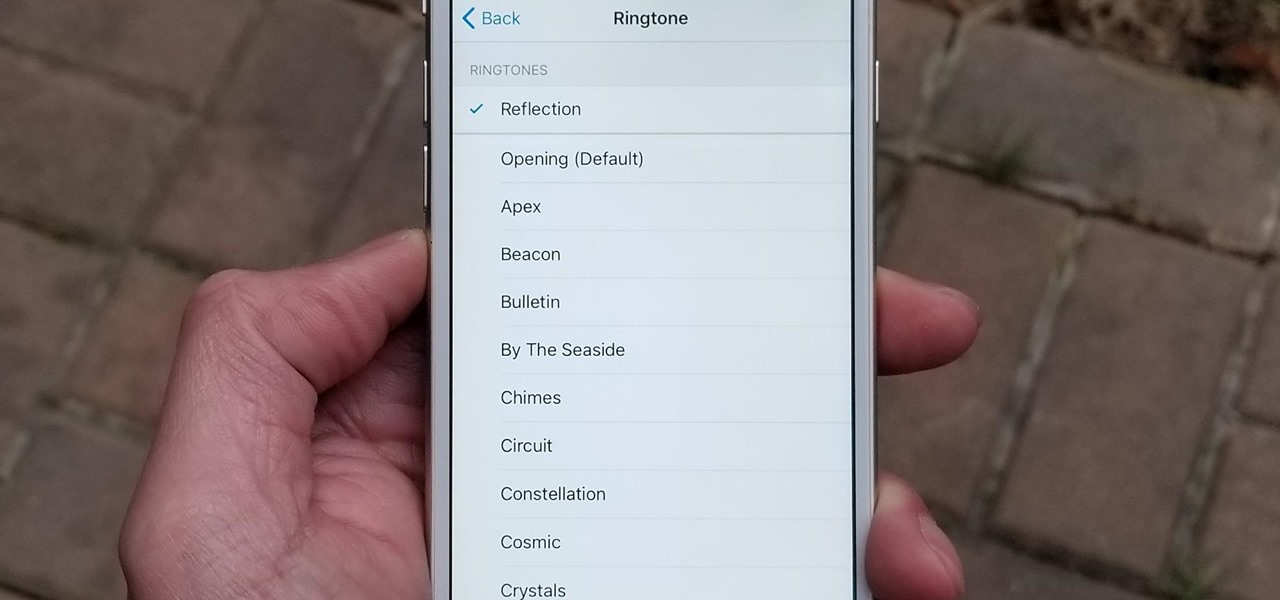
The new iPhone X sets itself apart from its predecessors not only as the first Apple smartphone to use an AMOLED screen, but also as the first iPhone to cost over $1,000. True to form as an exclusive device, Apple's latest flagship also features a distinct ringtone. With a little tinkering, however, you can make the new "Reflection" ringtone your very own, regardless of which iPhone you may have.

While unveiling various other gadgets, Google announced the Pixel Buds at their October 4th event in San Francisco. These wireless earbud-style headphones are particularly interesting thanks to their ability to offer real-time language translation via Google Translate when paired with a Pixel 2 or Pixel 2 XL.

While some companies like IKEA and Lowe's zig towards ARKit to entice shoppers, Target has opted to zag to broader appeal with an augmented reality see-before-you-buy tool for its mobile website.

Just in time for a new season of professional basketball, the National Basketball Association (NBA) has released a new app for iPhones and iPads built on ARKit that turns your driveway into a basketball court.

Investors are ready to throw their money at augmented and virtual use cases that demonstrate a business purpose and a return on investment.

Update 10/22: We were curious to see if the transparency was available when you activate the Pixel 2's automatic dark theme by setting a dark wallpaper, and we're happy to report that it is!

Today, anyone with a compatible PC can download the Windows 10 Fall Creators Update and experience Windows Mixed Reality.

The new iPhone X will be released on Friday, Nov. 3, in Apple Stores located in over 55 countries and territories. For those of you who would rather skip the in-stores lines that will start building well before the 8 a.m. local time openings, you can preorder the iPhone X on Friday, Oct. 27, starting at 12:01 a.m. PDT.

Every time you make a call or send a text, you're giving the recipient your phone number. This can be quite the security vulnerability, opening yourself up to scammers, spammers, and the feds. In this how-to, we'll look at what a burner phone is, why you might want one, and how to get started using a free second phone number on your regular smartphone.

Zenko Games makes no apologies for its influences. In fact, they cite them explicitly in their own promotional materials for Diamonst AR.

Technology and nature, typically thought of as opposites, are coming together in a new London exhibit.

Niantic has gotten themselves into a bit of a mess regarding their hit game Pokémon GO recently. The company hosted a fan fest in Chicago earlier this month that ended up being a complete disaster.

Faraday Future's all-electric super sports car concept attracted a lot of attention at CES earlier this year, but now it is struggling to replace key driverless engineers and program directors who left the company amid its recent financial troubles.

Lyft officially laid its stake in the ground to develop driverless fleets following its Friday announcement, but how fast it is catching up to ride-hailing competitor Uber's driverless initiative remains to be seen.

Russian phone customizer Caviar — you might have heard of the blinged-out iPhone 6s Pokemon GO phone they released a few months back — is taking on international relations with their newest product.