
How To: Back up your stuff for free with SyncBack
Use the free program SyncBack to automatically back up your important stuff to whatever medium you want.


Use the free program SyncBack to automatically back up your important stuff to whatever medium you want.
This is a very basic introductory video that teaches you how to successfully install Quartz Composer on your MAC OSX 10.5 Leopard. Quartz Composer is a node-based graphical data software that uses visual programming language. Built exclusively for use on the MAC OSX, it's a handy software for graphic designers.

This is a two part video tutorial explaining what Sony Vegas is, and how to use it! If you've just picked up this piece of software and have been wondering how to use it, hopefully this video will give you a hands on look at the program as well as a guide in exploring its various features.

This is a tutorial that shows how to make buttons with effects that will link you to web pages. The program is Adobe Flash CS3

This is a tutorial that shows you how to record your computer screen and save it as a video. This is useful for recording something you want to put online. The program I use is called SnagIt. This works for Vista and XP.
This week, Bre Pettis teams up with Mitch Altman and George Shammas to make a little 3x3x3 cube made of little LED lights that you can program with any kind of animation that you like.
This is a demonstration of how to use a software program to unlock your mobile phone and make it sim free. Enjoy your free call!

This tutorial demonstrates installing free HTML WYSIWYG Editor Software called Nvu so that you can get started with programming in HTML.
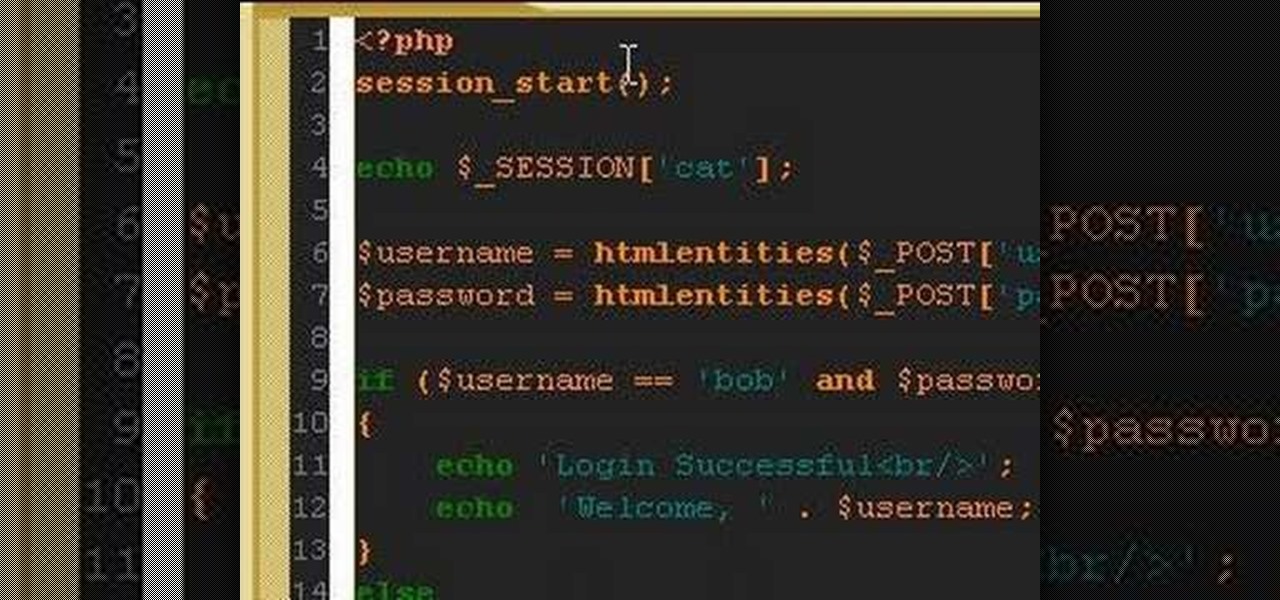
A PHP programming tutorial on creating login sessions to keep users logged in.

Learn all about your leopard gecko's eating requirements with this informative and easy-to-follow program that covers all the important topics of the gecko's diet, from vegetables, to vitamins, to mealworms, guided by Host Hillary Dupont and our senior herpetologist Ron Dupont.

Metacreations Bryce is a 3D terrain-generating application. You can build some beautiful landscapes, create animations, and even import 3D models from other programs.

How to program gravity effects in a Flash-base RPG.

In this tutorial will teach you how to program in Flash and ActionScript to move a character with the arrow keys and make him jump with the space bar.
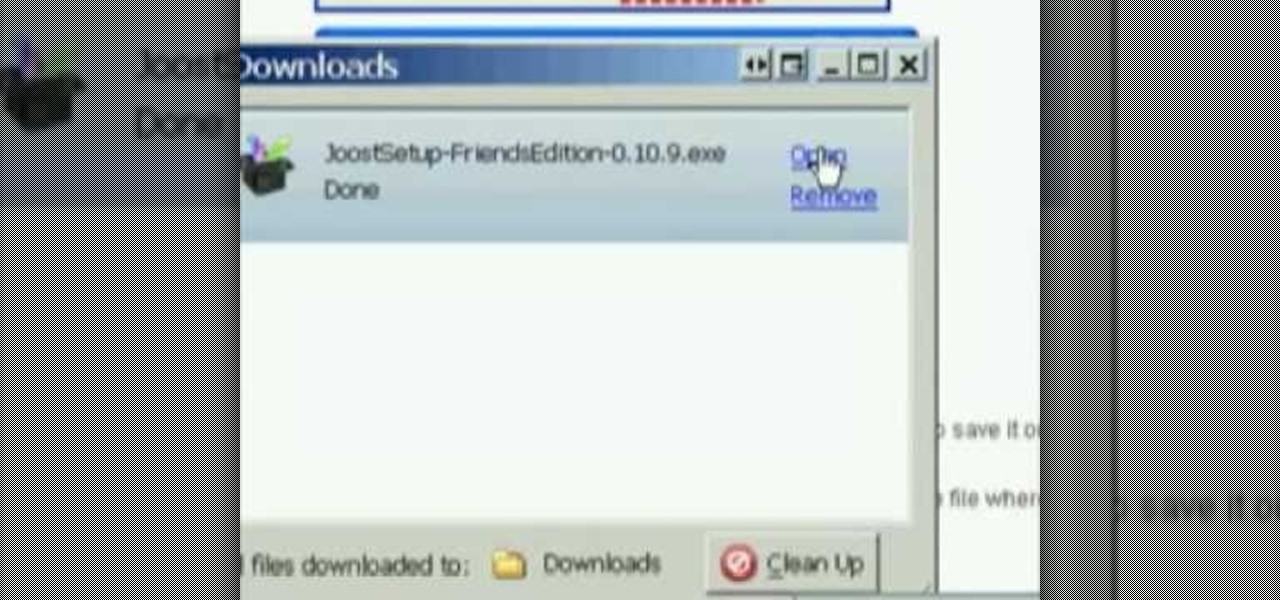
This video shows you how to download and play TV and movie files on your computer using two programs: Joost and Miro.

Bob and Brett show you two different record modes in your Pro Tools interface - Quick punch and the Transport window.

Bob and Brett show you how to add tracks to your Pro Tools program and how to use them. You are only as limited as your hardware!

Build power and speed with this Plyometrics workout video. These exercises should be done 2-3 times 3 times a week. Of course in order to lose weight with any strength training program it is important to also do cardio workouts at least 3 times a week.
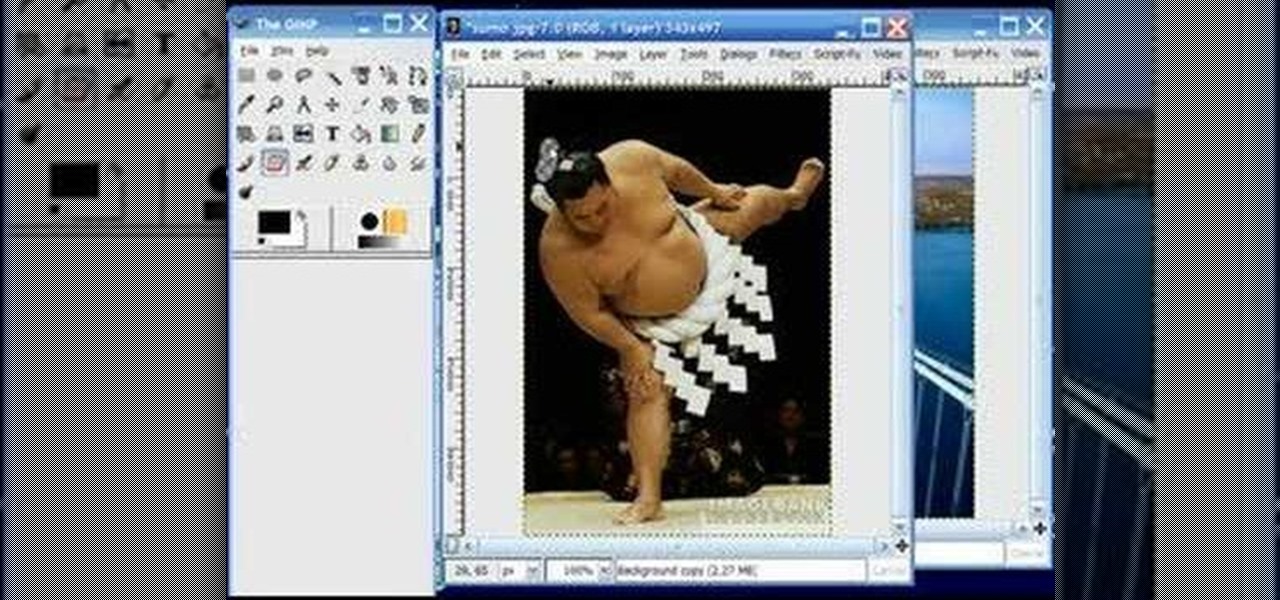
The GNU Image Manipulation Program, or GIMP, is a raster graphics editor application with some support for vector graphics. This video teaches you how to use the GIMP photo editor to edit a series of photos via layering. Learn to put a sumo wrestler over a bridge!

This tutorial explains how to use the free Hotkeybind macro. It allows you to open programs or insert text with a just a keystroke.

Jeff Schell shows you some of the options and configurations available when working with images that do not match the dimensions of your program monitor in Premiere Pro CS3. In addition, Jeff will introduce you to the 'Automate to Timeline" feature that helps you quickly create a photo montage or slide show with the click of a button.

Learn how to use Virtualdub - a free video editing program available online. Learn how to use Virutualdub to edit videos and convert video file formats.
This Pamie Demo shows how to setup, install and run a simple automation script. It shows you: how to install Pamie, how to create a Pamie test script to Automate a form using PythonWin IDE, how to write the script and how to run the test. The volume is really low so crank your speakers way up and make sure you have the proper Python and programs downloaded.

Going to the doctor can be an unsettling event for any child. This program is about preparing your toddler for a visit to the doctor.

Learning different coding languages can be difficult. You spend so much time mastering one and getting used to thinking along the channels you need for it that learning something new can sometimes be more difficult than starting from scratch. Starting from scratch, notably, is also difficult.

MATLAB, an acronym for "matrix laboratory," was created over 40 years ago to service the applied mathematics community. The powerful programming language now has over four million users worldwide and is of particular import to engineers, scientists, and economists.

Java is one of the world's leading programming languages thanks to its virtually endless array of applications. Since Java's initial release in 1998, this Open Source platform has become beloved by coders for its speed, flexibility, and dependability.
If you're a frequent Null Byte reader, chances are you're already up to speed with at least one or two programming languages or development platforms. But in a world that's becoming increasingly reliant on high-powered apps and responsive websites, knowing the fundamentals of just a few go-to programming languages isn't going to cut it if you want to be competitive and successful.

While SSH is a powerful tool for controlling a computer remotely, not all applications can be run over the command line. Some apps (like Firefox) and hacking tools (like Airgeddon) require opening multiple X windows to function, which can be accomplished by taking advantage of built-in graphical X forwarding for SSH.

While our time with the Protostar VM from Exploit Exercises was lovely, we must move on to bigger things and harder challenges. Exploit Exercises' Fusion VM offers some more challenging binary exploitation levels for us to tackle. The biggest change is that these levels are all network services, which means we'll write our first remote exploits.

When we are building programs that communicate over a network, how can we keep our data private? The last thing we want is some other lousy hacker sniffing our packets, so how do we stop them? The easy answer: encryption. However, this is a very wide-ranging answer. Today we're going to look specifically at how to encrypt data in Python with dynamically generated encryption keys using what is known as the Diffie-Hellman key exchange.

Gaining access to a system is always exciting, but where do you go from there? Root or bust. Sure, a compromised host is a great way to run a botnet, or do some other boring, nefarious thing—but as hackers, we want root. We also want to take the easiest path possible, search out low-hanging fruit, and exploit them. SUID programs are the lowest of the low-hanging fruit.

Hello fellow gray hat hackers, I wrote a program in python that helps me to fill up my proxychains.conf file, so I don't have to manually enter in the proxies. I figured I will give a little how-to of how I did it and maybe I could help some of you(hackers) out there to stay anonymous.

Greetings my fellow aspiring hackers,

Hello my anxious hackers, the week has started and here we begin a new series that I think will help many here and not only, for those that have the opportunity to follow our tutorials but they are not yet part of the community.

Hello, fellow grey hat hackers and aspiring coders. I'm back again with another python tutorial. Just that this one is gonna be a lot cooler ;-). We gonna make an encryption program, that well you know encrypts all the files on your pendrive or hdd or whatever you want....Also lots of thanks to DrapsTV. They have helped me a lot with Python and making awesome programs. The video is here:

This is a short explanation and tutorial on how to grab saved passwords from Google Chrome, ideally from a meterpreter session. The idea behind this is to understand how saved passwords work and how to keep them safe. Let's have some fun :D Understanding Google Chrome Saved Passwords

Hi nullbytes! I've been recently reading the whole Linux Basics for the Aspiring Hacker series and felt like it was missing some stuff I know, so I felt like sharing it with anyone who might find it useful too.

NOTICE: Ciuffy will be answering questions related to my articles on my behalf as I am very busy. Hope You Have Fun !!!

Welcome to the sequel to the latest post on writing 64 bit shellcode! This tutorial will assume that you are aware of everything mentioned in the last one, as I will try to make this tutorial void of formalities and straight to the point! If you have not read the last one, I suggest doing so unless you are familiar with basic assembly programming and system calls. This is by no means rocket science, so therefore I will simply repeat my TL;DR from last time before we get started, so that the a...

Welcome back, my fledgling hackers! In an earlier tutorial, I introduced you to probably the most popular scripting language for hackers, Python. To become a professional hacker, you need to have some scripting skills and Python is a good choice if you want to master just one. In this latest guide, I will expand your background in Python and offer you a tidbit of Python code to whet your appetite for all of the hacking to come.