In this Photoshop tutorial the instructor shows how to automate white balance. Normally there is a good chance that a group of photos were taken in a particular environment and if there was a white balance defect it would have affected all those pictures. So you will need to automate white balance correction to apply it to all those pictures at the same time. Take a group of photos which has white balance so that you can apply the technique on them. To do this go to Window actions and create ...

This android can talk, listen,and, with some tuning with a voice recognizer software, it will open and close many different applications.

Every good illustrator knows the advantage of using a Wacom tablet with Adobe Illustrator. When you plug in a Wacom tablet it doesn't automatically set your tools to be pressure sensitive. Terry White will show you how to set your brushes to really take advantage of your new tablet.

Tasktutorial teaches you how to create a sound on/off button using Flash. Name the first layer Actionscript. Go to frame 1, then window - actions. Add stop(); Go to frame 2, then window - actions. Add stopallsounds(); Create a new layer and select the text tool. Write off on. Change the color to black. Select the text and hit CTRL + B to break apart the letters. Select off, hit F8 and select convert to button. Name it off. Do the same for on, but name it on. Double click to open the off butto...

Unlike some of the popular app lockers out there, a nifty app fittingly named App Hider completely erases apps, files, and their associated footprints from your smartphone. Think of App Hider as a micro-OS within your smartphone's system. This miniature ecosystem can operate copied apps independently, thus giving it an unprecedented layer of privacy and freedom within your handset.

Websites are often misconfigured in ways that allow an attacker to view directories that are not ordinarily meant to be seen. These directories can contain sensitive information such as private credentials or configuration files that can be used to devise an attack against the server. With a tool called Websploit, hackers can scan targets for these hidden directories without difficulty.

A simple security flaw can allow an attacker to gain a strong foothold with little effort on their part. When a web application permits remotely hosted files to be loaded without any validation, a whole can of worms is opened up, with consequences ranging from simple website defacement to full-on code execution. For this reason, RFI can be a promising path to obtaining a shell.

The first few minutes after gaining access to a MacBook are critical — but where do we begin? Using tools built into macOS, we can develop an in-depth understanding of running background processes, detect antivirus software, locate sensitive files, and fingerprint other devices on the network. All of this can be done without installing additional software or modifying any files.

With the rise of website encryption (TLS), sniffing passwords from network activity has become difficult. However, it's still possible to quietly exfiltrate a target's network traffic in real time to extract passwords and sensitive information. Pertaining to macOS, there are two methods for retrieving traffic from a backdoored Mac.

Passwords stored in web browsers like Google Chrome and Mozilla Firefox are a gold mine for hackers. An attacker with backdoor access to a compromised computer can easily dump and decrypt data stored in web browsers. So, you'll want to think twice before hitting "Save" next time you enter a new password.

When a photo or video is just too sensitive to leave laying around in your Photos app, you'll want to either delete it for good or hide it away in safe, secure location on your iPhone. As for the latter, Apple actually has a few tools available to make photos and videos hidden — even password-protected — on your iPhone.

Chis Lacy's Action Launcher is easily one of the best third-party home screen apps for Android. If you're interested in the basic feature set of this impressive app, check our our overview of the top five launchers on Android. Today, we're taking an in-depth look at the brand new Adaptive Folders feature included in the latest update.

As the level of data being generated grows exponentially, past the Information Age and into the coming Hyper-Information Age of immersive computing — as resistant as many of us are to the idea — personal data security is becoming a necessary consideration in our everyday lives. Recognizing this, Mastercard, Qualcomm, and Osterhout Design Group have teamed up to show what secure shopping could look like in the very near future with iris authentication.

If you're like me, you change your wallpaper often. After maybe a week of looking at the same picture, you just have to have something different. Depending on the new wallpaper, you may spend another hour changing the background color of folders, the app drawer, and even Quickpage to match your overall theme. But you probably don't want to spend that much time tweaking your layout every week, so let me show you a way that reduces the time from an hour to a few seconds.

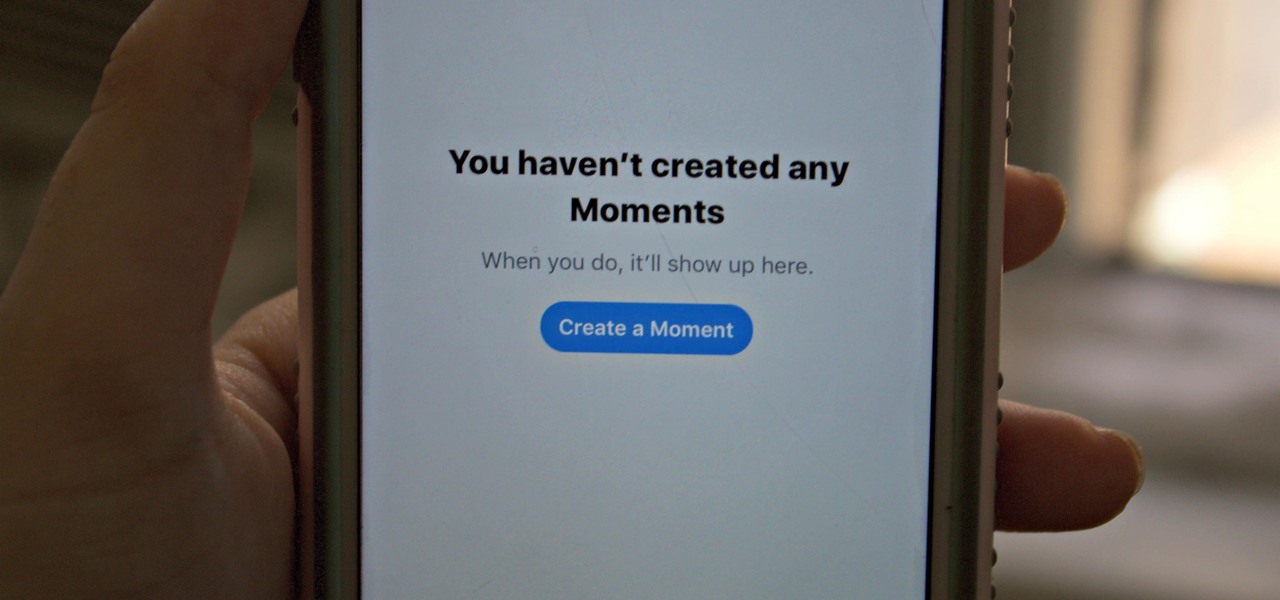
Twitter's Moments feature stitches together multiple tweets into a slideshow-esque story. This is particularly cool for you to keep up with major things that are happening in the world without having to follow and search for a ton of people to figure out the scoop.

Peach trees and other related plants are susceptible to the devastation caused by fire blight, a contagious bacterial disease. Once contracted, infected trees have to be burned to contain the disease and prevent spread to nearby trees. Increasing resistance to antibiotic treatment has sent scientists in search of alternative ways to deal with the bacteria and prevent its catastrophic damage.

A new study has found that up to half of people who think they have a penicillin "allergy" can still receive the drug, and other antibiotics with similar structures, without any negative reactions to the meds. Why? Because they're not really allergic, doctors say.

Mobile gaming still isn't on par with video game consoles or PCs, but we've come a long way from Snake. Modern games running on the latest smartphones boast downright impressive graphics—even more so when you consider how compact the system has to be in order to fit in people's pockets.

Welcome back everyone! In the last training session we covered basic file input and output. We're going to leave this topic for a bit and start on something that will change the way we write scripts, classes.

Last time in how to train you python, we covered the basics of variables and output. While we were covering variables, we talked briefly about strings. "String" is just a fancier way of saying "Word". A string is simply a set of characters encased in quotations, this lets python know that it is a word. Sometimes when we do things with strings we'll need to change them in order to do something. Python is case sensitive, for example "Null-Byte" is not the same as "null-byte". This is where mani...

With all of the personal data that's stored on our smartphones, it's of vital importance that we have some sort of lock screen security enabled. One of the Galaxy S5's killer features is obviously the fingerprint scanner. It makes the process of dealing with a secure lock screen a bit easier than typing in a password or PIN.

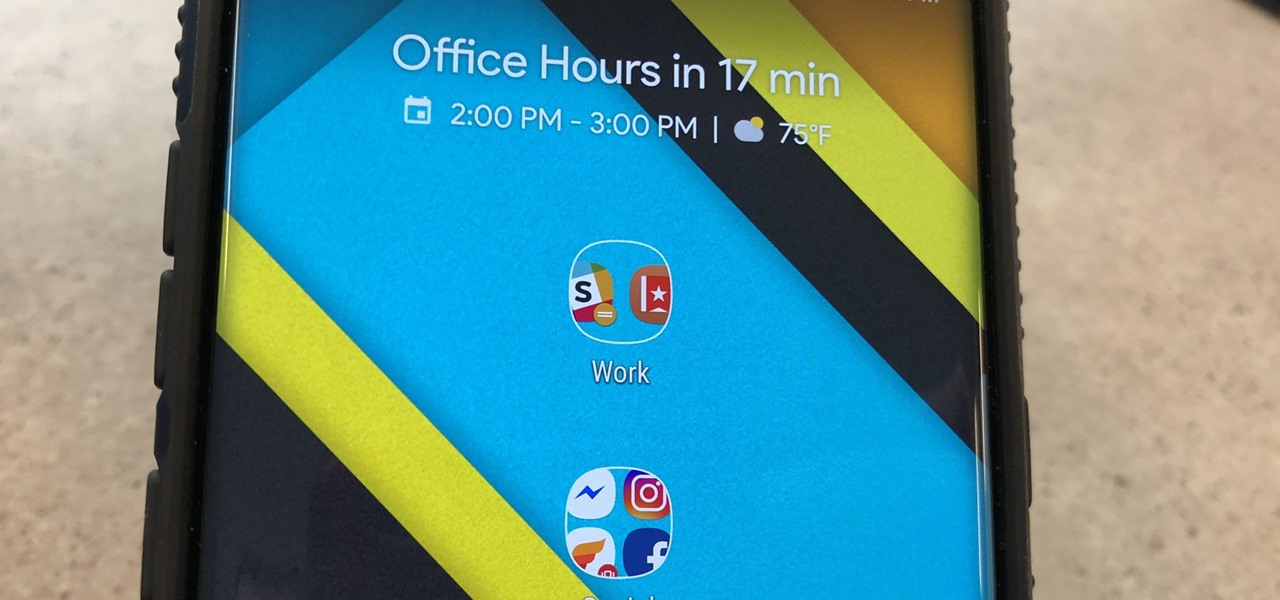
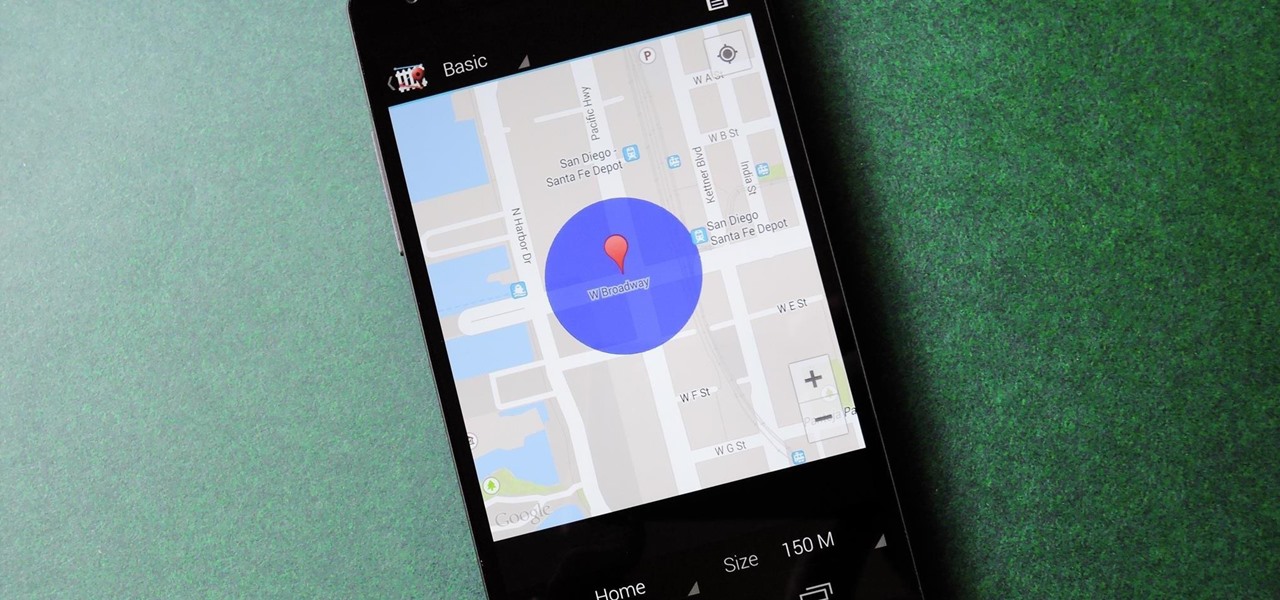
We live, work, and play in drastically different environments, so it only makes sense that we'd want our Nexus 5 smartphones to automatically adapt to our needs when in certain locales at certain times.

You've seen it a million times. You try to do something on your Android device and a box pops up asking you which app you'd like to use. You could try Photos, Gallery, Drive, Picasa Web Albums...the list is fairly extensive sometimes. And what's worse, after that you have to select "Always" or "Just once". Add it all up, and that's three taps to do something you thought would take just one!

The Samsung Galaxy S5 was just officially announced at Mobile World Congress. The new flagship device will be available worldwide beginning April 11, 2014, including all major U.S. and international carriers. With over 200 million Galaxy devices sold to date, the S5 doesn't stray too far from the trend, at least not aesthetically. We've still got a high-grade plastic shell with perforated back covers, and four color choices at launch. Our highlights of the release event are as follows.

Welcome back, my budding hackers! As you know, I firmly believe that to be a true professional hacker, you need to be proficient in Linux. This is for a number of good reasons.

Change object colors via ActionScript in Flash 8

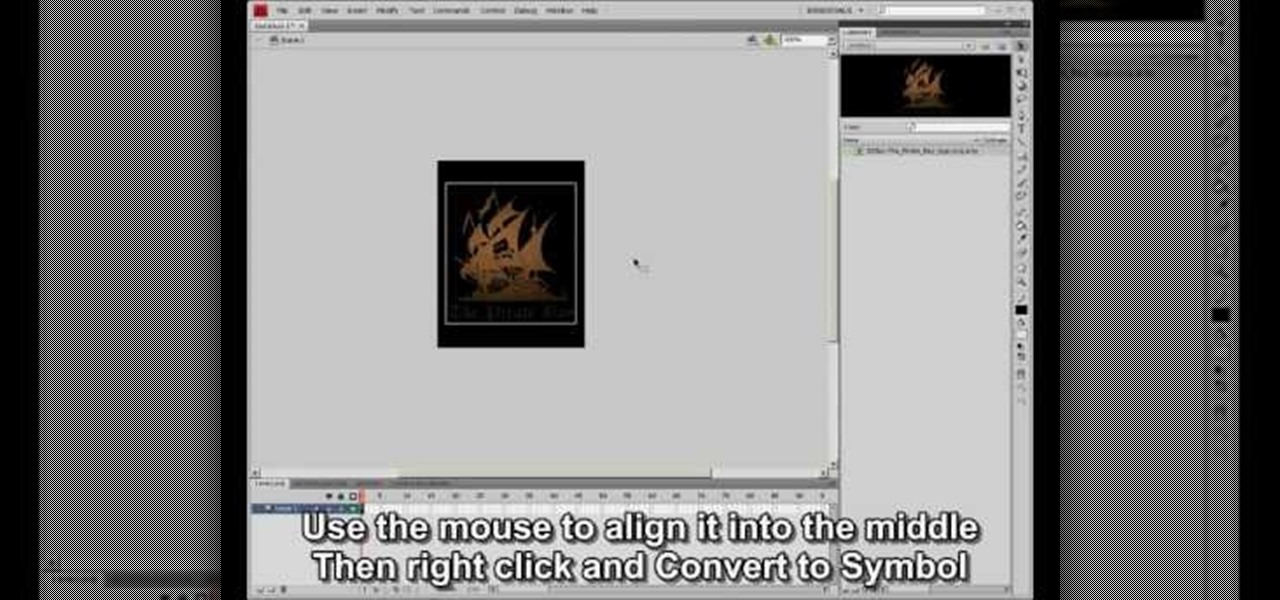
This video shows how to make a rotating SWF logo in Photoshop. Choose any desired logo that will be used later in the SWF file. Save the logo to the desktop. Use any kind of editing pogram. Make sure we only have what we want showing the area coloured with small squares is invisible. Open any version of Adobe Flash. Create a new "Actionscript 2" file. Then set workspace size to 240X320 and background color to match the picture we choose before. Make sure we select Flash Lite 2.0. Then go to F...

In this how to video, you will learn how to re-size any image in Photoshop to submit to Alamy. You will need the file to be 48 megabytes and uncompressed. First, open the image in Photoshop. At the bottom, you will see the current image's file size. Now go to image and image size. Increase the size by two or by five percent. Make sure re-sample image and constrain proportions are selected. Make sure bicubic smother is selected at the bottom of the window. At the top of this window, you will s...

When shooting action shots such as runners, bikers, cars, or sports shots, a cool effect that you will see in a lot of professional photography where the person is nice and clear, but the background is blurred to give the intention of being in motion and having a lot of speed. A slow shutter speed is a part of it to capture the image while still showing motion in the photo. In this video you will get tips on how to create the panning effect that will create the desired effect.

This achievement can be earned on the Outlaw to the End downloadable cooperative mission in Read Dead Redemption. To get the Dodge This achievement, start a private match with a friend on the Herd mission. Once the mission starts, select the bolt action rifle and the rolling black rifle. Use the bolt action as your primary weapon, and shoot the TNT crate next to the tent on the righthand side. Quickly switch over to your rolling black rifle. Have your teammate use one of the repeaters to weak...

With the "Thor" movie coming out in 2011 and the actors recently debuting a five-minute trailer at Comic-Con, fanboy buzz about this Norse comic book hero has officially reached fever pitch. Guys like the story - the son of a king cast down to earth as punishment, who seeks to redeem himself while falling in love with a human nurse - while gals like the fantastically ripped men.

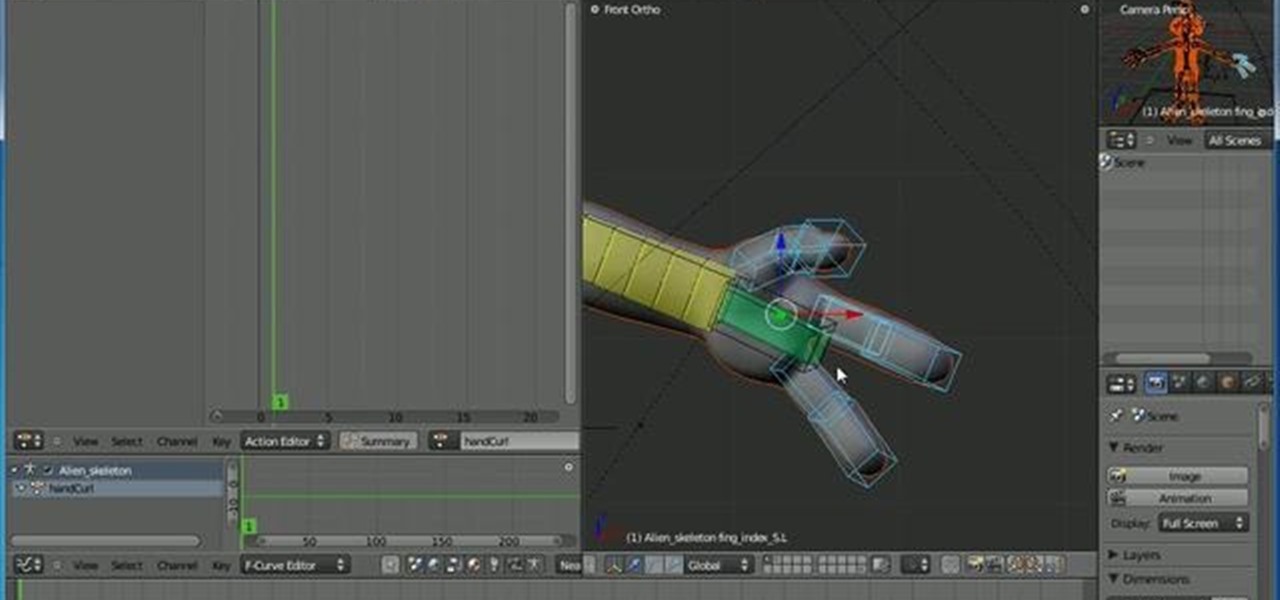
This Blender tutorial discusses how to set up action contraints, where you can use a bone to control things like finger curl/expand, or something more advanced, like facial expressions. Whether you're new to the Blender Foundation's popular open-source 3D computer graphics application or are a seasoned digital artist merely on the lookout for new tips and tricks, you're sure to be well served by this free video software tutorial from the folks at CG Cookie. For more information, including ste...

If you own the action game Captain America: Super Soldier and you're interested in unlocking a few of the achievements, look no further than this video made by the Achievement Hunter folks. They'll let you know what you need to do to unlock 'Grace Under Pressure', 'And They All Fall Down', and 'Friendly Fire'.

Back in the '80s, I was just a kid with a LEGO hobby. I remember building castles and floating boats, spaceships and monster trucks, even a working LEGO train powered by battery, lights and all.

Now that you've beaten the Executive Order mission in Call of Duty: Black Ops, it's time for mission 5— S.O.G. This two-part video will give you all the knowhow for beaten this level and moving on to number 6. Watch all of the gameplay action in this complete walkthrough! Then check out all of the other Call of Duty: Black Ops tutorials and walkthroughs on WHT for more warfare action!

Interested in installing actions for use in PSE 8 on your Apple computer? This clip will teach you what you need to know. Whether you're new to Adobe's popular raster graphics editing software or a seasoned professional just looking to better acquaint yourself with the program and its various features and filters, you're sure to be well served by this video tutorial. For more information, including detailed, step-by-step instructions, watch this free video guide.

Riding a bike is a great way to get exercise and as means to getting around but incorrect bike assemble will make for a bad time. Double check all your work and make sure everything is lubed up and fastened before taking your bike out for a spin.

The makeup artist Julia presents this tutorial in partnership with VSP vision care in order to demonstrate makeup tips for people wearing glasses or contact lens.

"Shamanism: Other Worlds" explores the ancient spiritual Amazonian enlightenment drug Ayahuasca. This documentary investigates Ayahuasca and its use largely as a religious sacrament. Those whose usage of ayahuasca is performed in non-traditional contexts often align themselves with the philosophies and cosmologies associated with ayahuasca shamanism, as practiced among indigenous peoples like the Urarina of Peruvian Amazonia. The religion Santo Daime uses it. While non-native users know of th...

This is a video walkthrough of the "Prologue: Financial District" level in Mirror's Edge for the Xbox 360.