Back in the '80s, I was just a kid with a LEGO hobby. I remember building castles and floating boats, spaceships and monster trucks, even a working LEGO train powered by battery, lights and all.

Riding a bike is a great way to get exercise and as means to getting around but incorrect bike assemble will make for a bad time. Double check all your work and make sure everything is lubed up and fastened before taking your bike out for a spin.

The makeup artist Julia presents this tutorial in partnership with VSP vision care in order to demonstrate makeup tips for people wearing glasses or contact lens.

There's definitely some malware-ridden apps on the Play Store. When it comes to the third-party apps you've connected to your Google Fit account, some have a crazy amount of permissions they have no business accessing. For example, you probably don't want a heart monitor app having access to your personal location data.

Magic Leap took years to launch, but when it did, the company managed to quickly become the leading rival to Microsoft's HoloLens (at least when it comes to experimental immersive experiences).
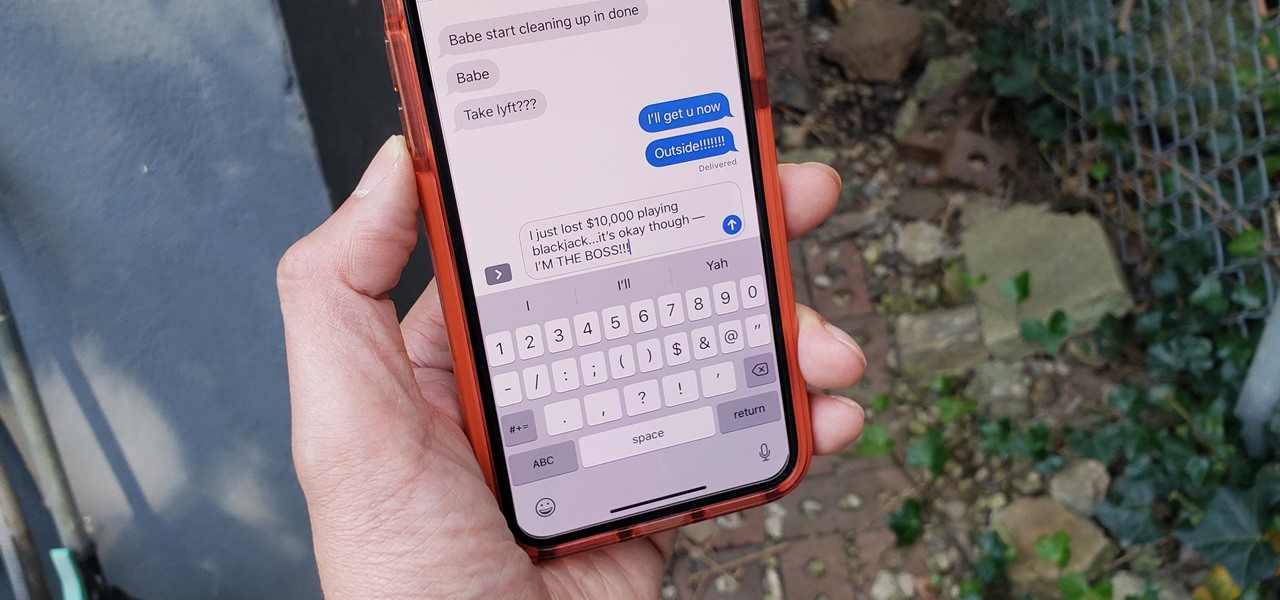
There's something about alcohol that compels you to contact people. Most of the time, the drunken calls or messages you send out will have you cringing hard tomorrow morning. But if you have a jailbroken iPhone, you can help prevent this potential embarrassment with a free tweak.

Unlike some of the popular app lockers out there, a nifty app fittingly named App Hider completely erases apps, files, and their associated footprints from your smartphone. Think of App Hider as a micro-OS within your smartphone's system. This miniature ecosystem can operate copied apps independently, thus giving it an unprecedented layer of privacy and freedom within your handset.

In an effort to raise awareness regarding the impact of emissions on the environment, Snap has partnered with the United Nations Environment Programme to use augmented reality to show how much ocean levels will rise over the next 80 years.

Websites are often misconfigured in ways that allow an attacker to view directories that are not ordinarily meant to be seen. These directories can contain sensitive information such as private credentials or configuration files that can be used to devise an attack against the server. With a tool called Websploit, hackers can scan targets for these hidden directories without difficulty.

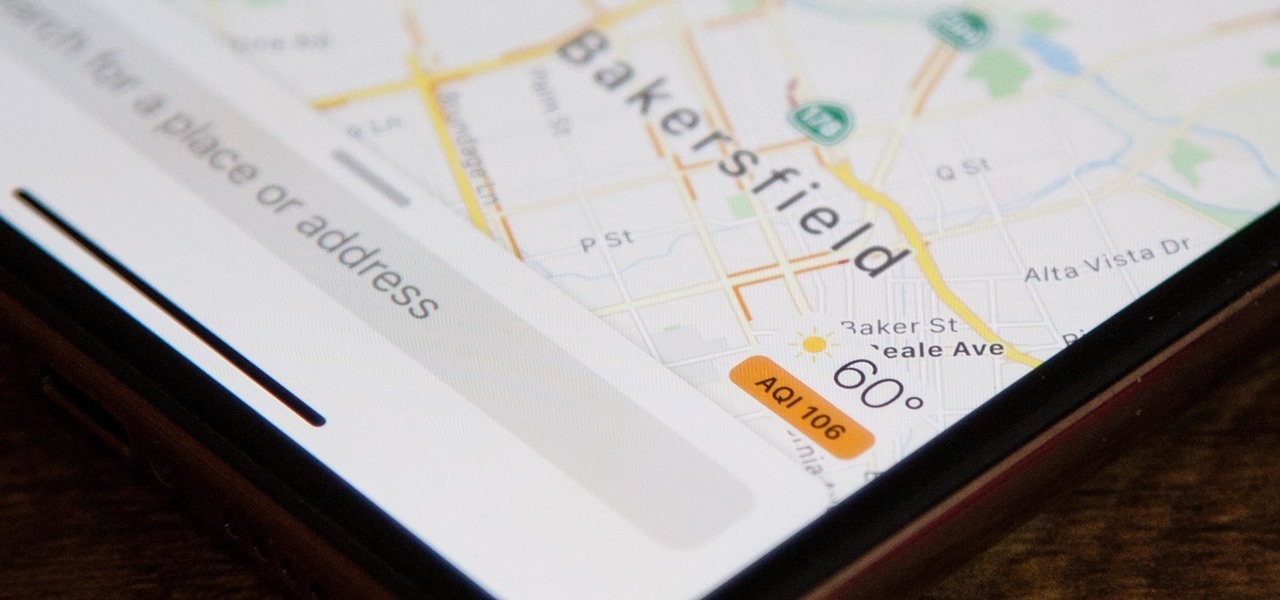
While the United States, in general, doesn't have the worst overall pollution, the air quality can drastically change from one day to the next. If you're particularly sensitive to pollutants in the air, there are apps that show how clean or polluted the air is in your area, as well as in cities you plan on traveling to, but Apple's making those apps less relevant with a new feature in Apple Maps.

A simple security flaw can allow an attacker to gain a strong foothold with little effort on their part. When a web application permits remotely hosted files to be loaded without any validation, a whole can of worms is opened up, with consequences ranging from simple website defacement to full-on code execution. For this reason, RFI can be a promising path to obtaining a shell.

The first few minutes after gaining access to a MacBook are critical — but where do we begin? Using tools built into macOS, we can develop an in-depth understanding of running background processes, detect antivirus software, locate sensitive files, and fingerprint other devices on the network. All of this can be done without installing additional software or modifying any files.

With the rise of website encryption (TLS), sniffing passwords from network activity has become difficult. However, it's still possible to quietly exfiltrate a target's network traffic in real time to extract passwords and sensitive information. Pertaining to macOS, there are two methods for retrieving traffic from a backdoored Mac.

Transferring hundreds of screenshots, webcam recordings, keystroke logs, and audio recordings between your VPS and a local Kali machine can be tricky. Services like Dropbox don't always have the best privacy policies and suffer data breaches just like any other website. To mitigate these risks, we'll use a secure, open source, and decentralized alternative.

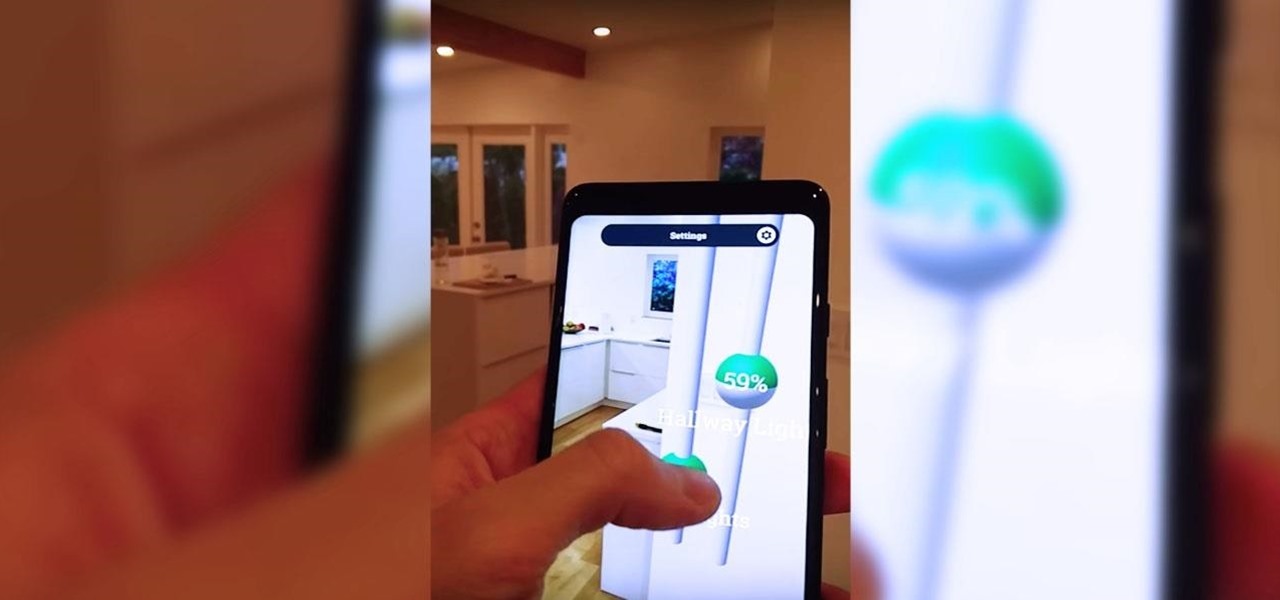
Voice-activated digital assistants from Amazon, Apple, and Google currently have the upper hand for home automation integrations, but a new augmented reality mobile app promises to give homeowners and renters visual control over their connected appliances.

Two-factor authentication (2FA) is a great way to add another layer of security to sensitive third-party apps and websites like Venmo. However, before iOS 12, to log into a particular 2FA-secured app or site on your iPhone, you'd have to memorize or copy the SMS code from Messages, then jump back in a timely manner to log in. Apple's latest iOS version streamlines this process.

As Facebook, Apple, Samsung, and others offer augmented reality selfie effects and content that challenge its platform, Snapchat has continued to innovate with its augmented reality capabilities.

Passwords stored in web browsers like Google Chrome and Mozilla Firefox are a gold mine for hackers. An attacker with backdoor access to a compromised computer can easily dump and decrypt data stored in web browsers. So, you'll want to think twice before hitting "Save" next time you enter a new password.

When a photo or video is just too sensitive to leave laying around in your Photos app, you'll want to either delete it for good or hide it away in safe, secure location on your iPhone. As for the latter, Apple actually has a few tools available to make photos and videos hidden — even password-protected — on your iPhone.

When it comes to augmented reality smartglasses, for now, it's still a mostly enterprise world, since the form and function of most are more acceptable on a job site versus your local cafe, and the still high price tags are far more palatable to major companies rather than individuals.

As the level of data being generated grows exponentially, past the Information Age and into the coming Hyper-Information Age of immersive computing — as resistant as many of us are to the idea — personal data security is becoming a necessary consideration in our everyday lives. Recognizing this, Mastercard, Qualcomm, and Osterhout Design Group have teamed up to show what secure shopping could look like in the very near future with iris authentication.

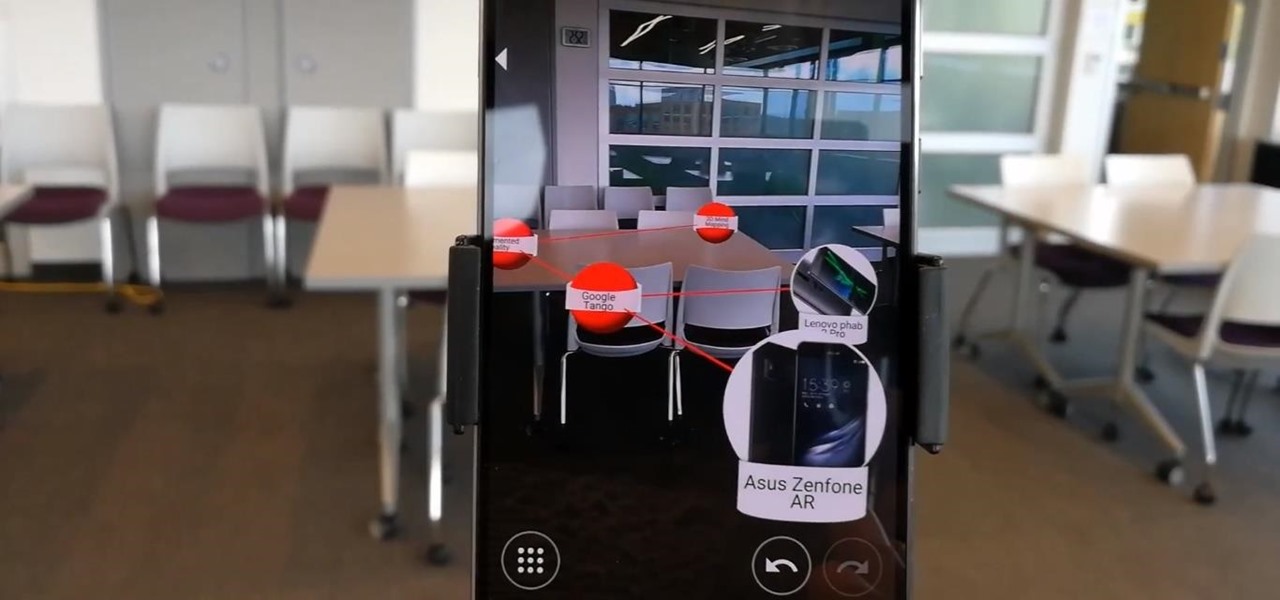
When Google announced its ARCore augmented reality toolkit for Android as its answer to Apple's ARKit for iPhones and iPads, the question from many observers was, "What about Tango?"

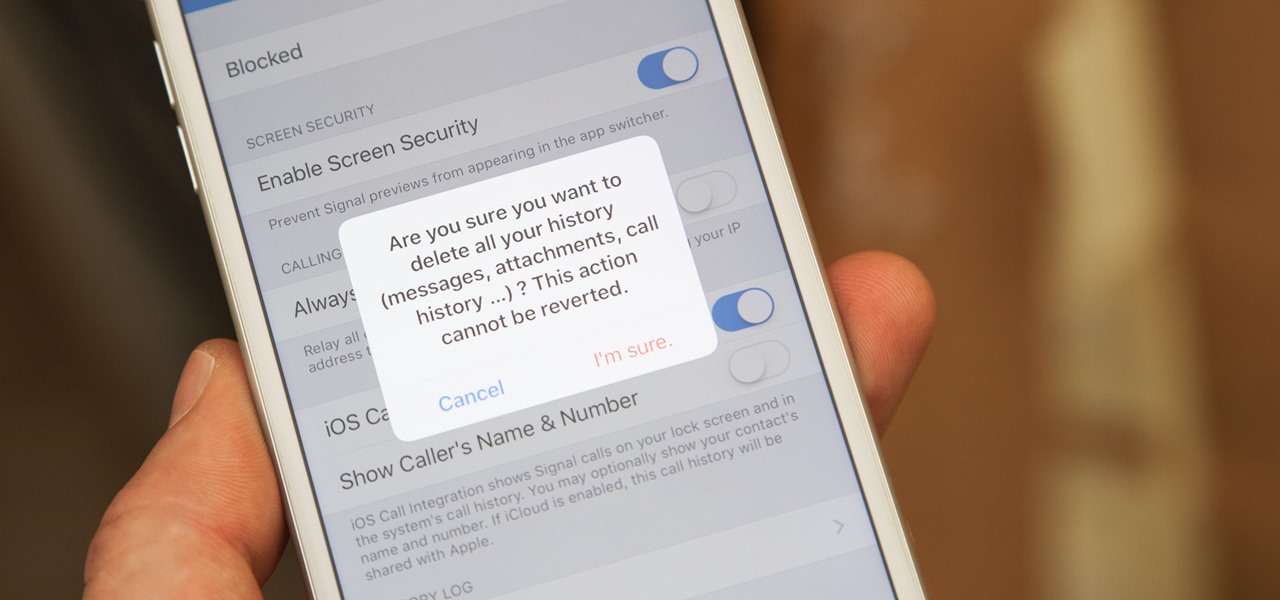
If thieves, hackers, law enforcement, or other would-be enemies should ever gain entry to your smartphone, they could also access conversations you've had in Signal Private Messenger. To better secure your encrypted communications, you can password-protect the whole app and its contents — but only on Android. Even then, it's necessary to perform data deletion on a periodic basis, if not immediately.

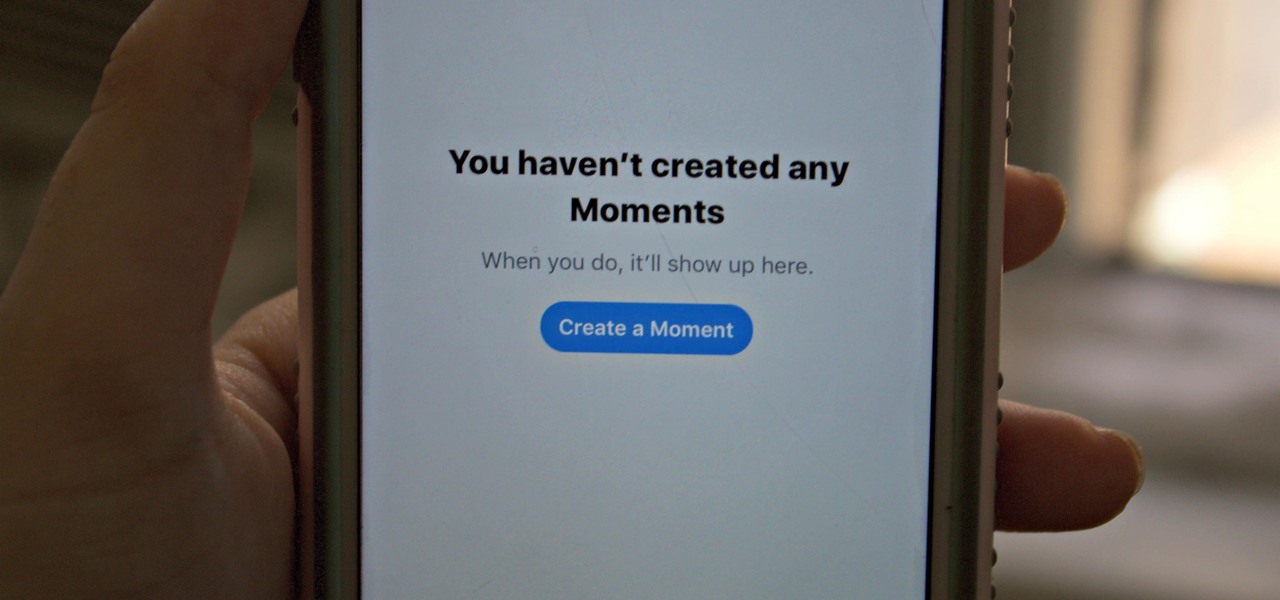
Twitter's Moments feature stitches together multiple tweets into a slideshow-esque story. This is particularly cool for you to keep up with major things that are happening in the world without having to follow and search for a ton of people to figure out the scoop.

Peach trees and other related plants are susceptible to the devastation caused by fire blight, a contagious bacterial disease. Once contracted, infected trees have to be burned to contain the disease and prevent spread to nearby trees. Increasing resistance to antibiotic treatment has sent scientists in search of alternative ways to deal with the bacteria and prevent its catastrophic damage.

Tuesday gave us what I am dubbing a "patent dump." Can you blame me? The U.S. Patent Office released 56 patents from Apple. 56! Among them, there are patents confirming Apple is working on embedded Touch ID, edge-to-edge displays, and a 3D camera system (surprise, surprise). Some of those things we've heard rumors on for some time, but what is new is one of the patents hidden amongst the bunch, describing an Apple-made avatar system. One whose end-goal is to reflect your current emotional sta...

Malware attacks on mobile phones are reaching an all-time high and it looks like companies like Samsung are doing all that they can to prevent any unwanted hackers from accessing its sensitive user data.

Call them what you will—moss piglets, water bears, or by their real name, tardigrade—but these intriguing tiny creatures can come back from the brink of death. They can survive boiling, deep freezing, UV radiation, completely drying out, and even a trip to space—without the benefit of being in a spacecraft.

A new study has found that up to half of people who think they have a penicillin "allergy" can still receive the drug, and other antibiotics with similar structures, without any negative reactions to the meds. Why? Because they're not really allergic, doctors say.

A scary piece of malware just got a lot more terrifying this week. Security firm Comodo reports that "Tordow," a banking Trojan first uncovered in September 2016, received a massive update this December.

Swipe keyboards such as GBoard, SwiftKey, TouchPal, and Swype are handy for quick one-thumbed typing on an iPhone, but Microsoft upped the game with its experimental Word Flow Keyboard. In short, the keyboard fans out to occupy the natural range of your thumb, where you can type or rely on predictive swiping.

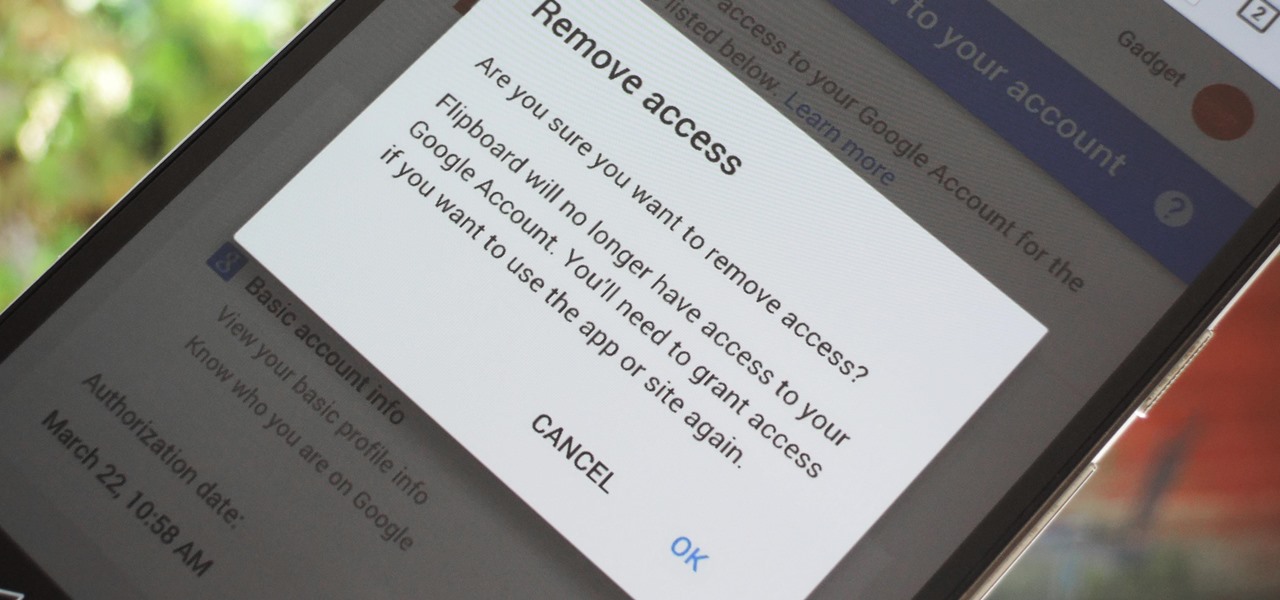
Many apps and services that are available for Android can only work if they have access to your Google account. While you're setting up one of these apps, you'll see a popup that says something like "This app would like to access your Google account," and the options are "Accept" or "Cancel." Of course we tap "Accept" here to ensure that the app will work properly, but what are the long-term repercussions of doing that?

If you like having Siri available to answer a quick question every now and again but don't want everyone who picks up your iPhone to also have access to your personal assistant, there's an easy way to disable her from working on your iPhone's lock screen. This is also something you can do if you're always activating Siri accidentally in your pocket.

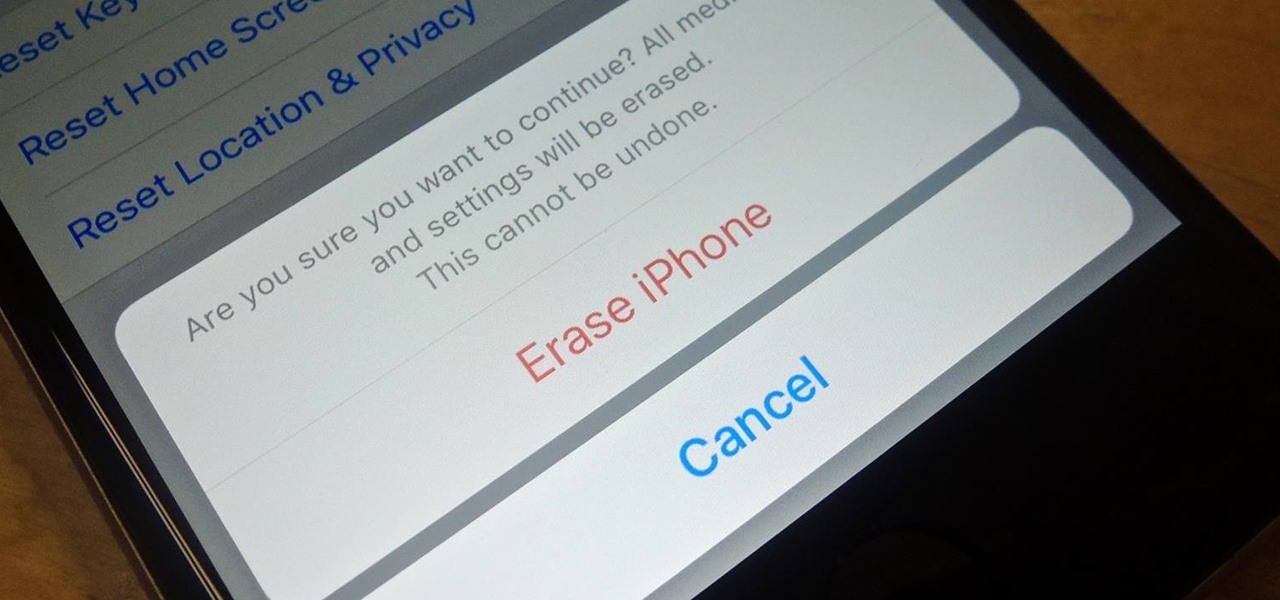
Before you sell your old iPad, iPhone, or iPod touch to a buddy or a company like Gazelle, it's vital that you wipe the entire device of all its content; including sensitive material like contacts, messages, pictures, and videos. There are two easy ways to wipe your iOS device, so let's show you how to do it using iTunes or directly from the device itself.

While it took Apple a damn-long time to finally include widgets in iOS, I do admire their implementation. Accessible from within any screen by pulling down the Notification Center (or, more correctly, the "Today" view), the home screen remains clean and minimal, which some of you with Android devices might appreciate—despite any Apple hatred you may have.

Well, first things firsts, it's been awhile! I'm sorry the series has been dead for a little bit, but I recently hit some personal relationship issues and needed to take some time to think. But, now that it's all said and done, the dust can settle and we can start training again!

Last time in how to train you python, we covered the basics of variables and output. While we were covering variables, we talked briefly about strings. "String" is just a fancier way of saying "Word". A string is simply a set of characters encased in quotations, this lets python know that it is a word. Sometimes when we do things with strings we'll need to change them in order to do something. Python is case sensitive, for example "Null-Byte" is not the same as "null-byte". This is where mani...

Like its predecessor—and probably every device in the future—the Samsung Galaxy S6 comes with a fingerprint scanner that allows for a more secure lock screen, web sign-ins, and account verification. But unlike its brethren, the sensor on the S6 has been vastly improved. No longer does it require a clumsy swipe—all you have to do is place your finger on it for less than a second, much like Touch ID on iPhones.

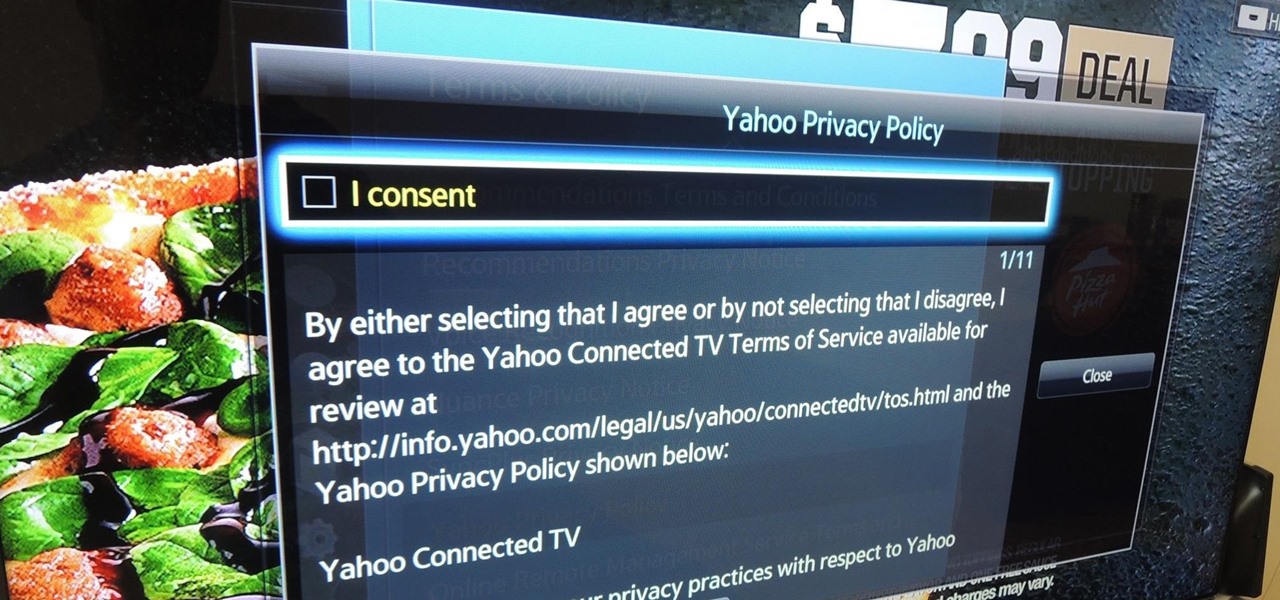
Televisions used to be great for just one thing—watching TV. But a more connected world brought with it Smart TVs, devices that can access the web, stream Netflix, and even mirror your smartphone's display. And with this level of connectivity, OEMs like Samsung saw it fit to place targeted and interactive ads on your screen.

I've been lucky enough to never be a victim of street crime, but I have read and seen too many articles and videos to completely rule it out as a possibility. You can do some things to prevent it, but if your life suddenly turns into a scene from Friday the 13th, you'll want to be prepared with some sort of way to let others know you need help. This is where Shake2Safety comes in, a free Android app from Phontonapps.