
How To: Turtl - Encrypted Cloud Notes
Hello Everyone! I wanted to share a free and open source note taking tool that I've been using for quite some time now.


Hello Everyone! I wanted to share a free and open source note taking tool that I've been using for quite some time now.

You would think that with each major iOS update, there'd be fewer ways to bypass the lock screen. Unfortunately, Apple's developers have consistently failed every year since 2013 in this department, leaving open lock screen exploits for iOS 7, iOS 8, and now the latest iOS version, iOS 9, with each exploit being discovered within days of the OS release.

A four-digit passcode is what protects your iPhone, and the sensitive material within it, from strangers or nosey friends. Four digits are the only thing preventing someone from snooping through your pictures and posting them online for the public to see, and that's if you even have passcode security enabled.

Lending someone your phone to make a call is always an awkward situation, as you closely monitor them to make sure they stick to a phone call rather than wandering off into private applications like your photo or messaging apps. You don't necessarily want to eavesdrop on their conversation, but trusting people with your phone is difficult, especially if you have some risqué or embarrassing pictures stored on it.

Adding to the recent recent slew of bugs and issues within iOS 7, it now seems that emails sent with attachments are not encrypted, despite Apple's claims that they are.
The sensors in your mobile device are integral for gaming (try to beat my Temple Run 2 score), as well as many of the basic Galaxy S3 features like Smart Stay and other fancy additions. But sometimes those sensors can become overly sensitive or just downright unusable.

I don't like paying for repairs, and I don't like purchasing extended warranties. When one of my gadgets break, I perform emergency surgery and try and fix it myself. It doesn't always go well, but I've managed to resuscitate a few iPhones, an HDTV, an Android tablet, multiple MacBook Pros, and other gadgets seemingly on their deathbeds.

Here are instructions to make origami bat. You will need 383 black, 47 brown, 3 white and 2 red triangles. In the video below you'll see a map.

Sometimes the best place to hide something is where people least expect it, so in this project, we're making a super secret safe that only you'll know about.

Live wallpapers are part of what make Android's features so unique and wonderful, making your homescreens come alive and much more interesting. The wallpapers are extremely customizable and interactive, many times sensitive to swipes, finger-tapping, and other multi-touch gestures—Ditalix being one of the frontrunner apps in the field. The only problem with these live wallpapers is the toll it takes on the device's battery. While not all live wallpapers kill the battery, there are many of the...

When it comes to your smartphone, you don't have to be a cheater to want a little privacy. I don't even like people playing Temple Run on my mobile because I don't want anyone beating the achievements I've been working on getting myself.

Thanks to its open-source platform and easy-to-use hardware and software, there's literally thousands of Arduino projects detailed online for anyone to make—a magic mirror, DIY polygraph machine, and hotel-hacking dry erase marker just being a few examples. Hell, you can even make the Daft Punk helmet.

UPS offers a four-step guide to prepare packages for shipping. These instructions include shipping advice on packaging materials and proper labeling that can help items arrive safely and on time. And when you are ready to ship, UPS Internet Shipping guides you through the required address fields. Packaging solutions made easy. That’s logistics.
When it comes to live wallpaper for your Android device, the choices are pretty much limitless. Anything from a planet's elliptical orbit around the sun to a school of fish swimming across your screen are just a click and a download away. With the advancement of smartphones, live wallpapers have greatly improved. What once used to be a bit of snow falling down the screen has now evolved into very complex animations, with some that are even susceptible to your interaction with them.
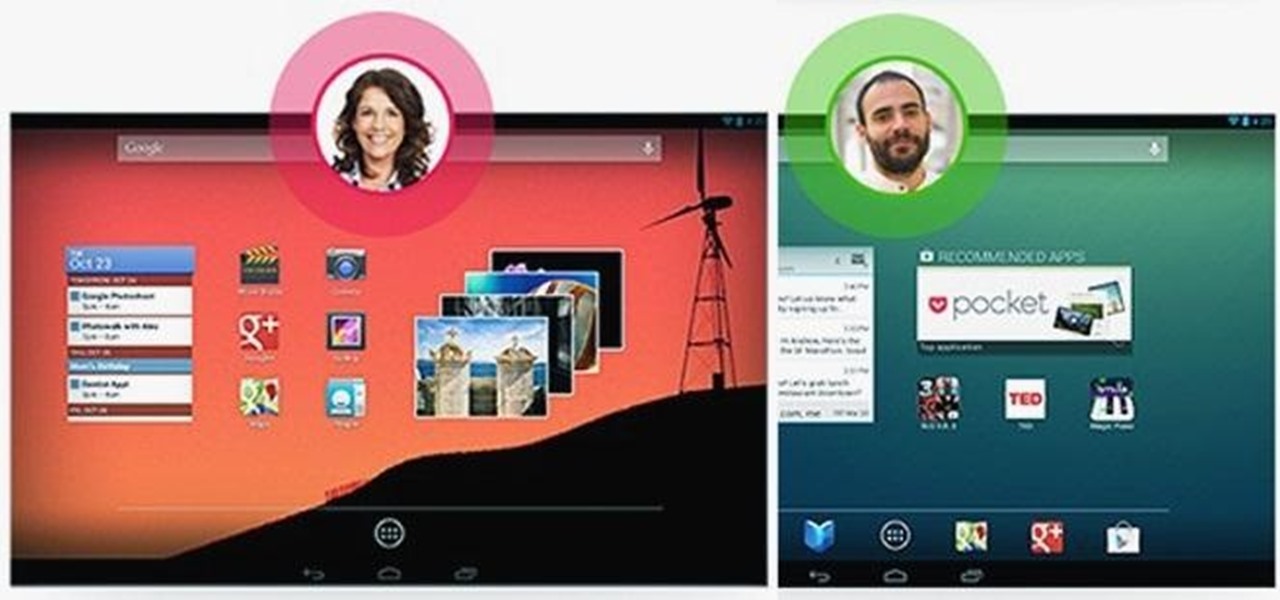
The most recent update for Android's Jelly Bean has some pretty cool new features, like better panoramic photos, gesture typing, and wireless sharing. From a security standpoint, though, the best new feature is the ability to add multiple users to one device. You can create up to 8 different accounts on Android tablets like the Nexus 7 or Nexus 10, so besides saving time hiding or protecting sensitive data, it could also save you some money. You can share a device with your family, kids, or s...

Who needs to go to bartending school when you've got the Inebriator to mix your favorite drinks for you? Want a cosmopolitan? No problem. Press a button. Want a tequila sunrise? Sure thing. Press a button. As long as you've got a good supply of liquor and mixers, the Inebriator is at your command. So, what exactly is this Inebriator thing? Well, it's a robotic bartender that can automatically pour 15 different pre-programmed cocktails. With 9 different liquors and 7 mixers on board, it's got ...

From dynamite to lasers to LEDs, you can make graffiti with a lot of different things. Parisian artist Antonin Fourneau has added water to that list. He created this incredible LED wall that lights up wherever it's touched by water to create what he's dubbed "Water Light Graffiti," which can be simply described as being an LED Buddha Board.
Systm is the Do It Yourself show designed for the common geek who wants to quickly and easily learn how to dive into the latest and hottest tech projects. We will help you avoid pitfalls and get your project up and running fast. Search Systm on WonderHowTo for more DIY episodes from this Revision3 show.

"Always be strapped," says Techno-Guru Lloyd. Word! Techno-Guru Lloyd of My Home 2.0 tells you how to stay safe while working with sensitive electronics and circuitry.

Learn how to follow proper netiquette rules. You may be a model of decorum in person, but a bonehead online. Check out how much you know about Internet manners.

Your tooth is throbbing, your head is pounding, and the oral surgeon can't see you until this afternoon. You'll need something to take the edge off until the good doctor can fit you in.

While we haven't covered Amazon Web Services, or AWS, on Null Byte before, Amazon's cloud computing platform is ripe for attack by hackers, pentesters, and cybersecurity researchers. It's also an excellent cloud hosting service to build or use vulnerable-by-design AWS setups and frameworks.

If you store important, sensitive information on your iPhone in Notes, you'll want to be more careful. When Notes syncs across your iPad and Mac via iCloud — devices that family members or coworkers may share — you run the risk of having your notes read, edited, and deleted by other people. Such a catastrophe is easily avoided.

As penetration testers, we sometimes need to securely store customer data for prolonged periods. Bruteforce-resistant, vault-like containers can be created with just a few commands to protect ourselves from physical attacks and unintended data disclosures.

Our future technology has a lot of amazing possibilities, and few have more promise than augmented and mixed reality headsets. But these advancements come with several concerns over privacy, and if we don't understand them, we may lose control of our own data without even knowing.

hello my dear colleagues, I made a visit to nullbyte and found that there is not a complete tutorial about the google dorks, so I felt the need for this tutorial, and seeing that there are many newbies around, so here's a tutorial that will teach you how to use google to hack.

Jennifer Pompa suggests that the 20" easiXtend Elite is the extension to start with. It's an 8 piece extension made with human hair that's not been too processed and so looks very natural. Jennifer is wearing a Kim Kardashian look with flowing curls. The extensions can be purchased as Extensions. Blow dryer, flat iron or curling can be done to these extensions because it's real hair. The extensions come in many colors but also can be dyed to match your hair. To remove them, Jennifer unclips t...

There are three main types of exfoliates : the mechanical ones with the little scrubby beads; enzymatic ones made from the acids of fruits such as pineapple or papaya; and AHA’s (Alpha-hydroxy Acids).

This video is about how to get rid of pimples. It's a nightmare to wake up and discover a big, red pimple right on your face. Here are some tips to help you out. 1. Do not touch, or try to squeeze or pop the pimple. This can cause pain, redness, swelling, and even infection. If you keep doing it another possible problem that can develop is scarring which can be permanent. 2. Wash your face gently with a mild, medicated soap and water (the water should be warm, but not too hot). Do this for 30...

This android can talk, listen,and, with some tuning with a voice recognizer software, it will open and close many different applications.

Every good illustrator knows the advantage of using a Wacom tablet with Adobe Illustrator. When you plug in a Wacom tablet it doesn't automatically set your tools to be pressure sensitive. Terry White will show you how to set your brushes to really take advantage of your new tablet.

Unlike some of the popular app lockers out there, a nifty app fittingly named App Hider completely erases apps, files, and their associated footprints from your smartphone. Think of App Hider as a micro-OS within your smartphone's system. This miniature ecosystem can operate copied apps independently, thus giving it an unprecedented layer of privacy and freedom within your handset.

Websites are often misconfigured in ways that allow an attacker to view directories that are not ordinarily meant to be seen. These directories can contain sensitive information such as private credentials or configuration files that can be used to devise an attack against the server. With a tool called Websploit, hackers can scan targets for these hidden directories without difficulty.

A simple security flaw can allow an attacker to gain a strong foothold with little effort on their part. When a web application permits remotely hosted files to be loaded without any validation, a whole can of worms is opened up, with consequences ranging from simple website defacement to full-on code execution. For this reason, RFI can be a promising path to obtaining a shell.

The first few minutes after gaining access to a MacBook are critical — but where do we begin? Using tools built into macOS, we can develop an in-depth understanding of running background processes, detect antivirus software, locate sensitive files, and fingerprint other devices on the network. All of this can be done without installing additional software or modifying any files.

With the rise of website encryption (TLS), sniffing passwords from network activity has become difficult. However, it's still possible to quietly exfiltrate a target's network traffic in real time to extract passwords and sensitive information. Pertaining to macOS, there are two methods for retrieving traffic from a backdoored Mac.

Transferring hundreds of screenshots, webcam recordings, keystroke logs, and audio recordings between your VPS and a local Kali machine can be tricky. Services like Dropbox don't always have the best privacy policies and suffer data breaches just like any other website. To mitigate these risks, we'll use a secure, open source, and decentralized alternative.

Passwords stored in web browsers like Google Chrome and Mozilla Firefox are a gold mine for hackers. An attacker with backdoor access to a compromised computer can easily dump and decrypt data stored in web browsers. So, you'll want to think twice before hitting "Save" next time you enter a new password.

When a photo or video is just too sensitive to leave laying around in your Photos app, you'll want to either delete it for good or hide it away in safe, secure location on your iPhone. As for the latter, Apple actually has a few tools available to make photos and videos hidden — even password-protected — on your iPhone.

As the level of data being generated grows exponentially, past the Information Age and into the coming Hyper-Information Age of immersive computing — as resistant as many of us are to the idea — personal data security is becoming a necessary consideration in our everyday lives. Recognizing this, Mastercard, Qualcomm, and Osterhout Design Group have teamed up to show what secure shopping could look like in the very near future with iris authentication.