This is hardcore, serious hacking at its best. So it goes without saying that you probably shouldn't be attempting this computer hack unless you've successfully shut down your friend's computer at school using Command Prompt and sent out a fake virus to loved ones.
Hello I have now asked for help a few times, so I figured I should contribute with what I can offer as of right now, which is many valuable sites if you need to look someone up.

There's really nothing safe about transmitting sensitive information electronically, but even if it gets there safely without being seen by prying eyes, there's no guarantee what happens to it once it reaches its destination. And let's face it, there are some things that you just don't want floating out there forever. So what can you do? Whether you want to send an email, a text, or a link, there are ways to send messages that self-destruct so that once they're read, they immediately vanish. ...

Have you ever had a burning sensation when you urinate? Low fever, back pain, and maybe cloudy urine? Male or female, it could have been a urinary tract infection. If it lasted long enough, the chances are good you went to the doctor for help. For about 20% of women, standard testing for a UTI does not reveal the presence of infection-causing bacteria, even though bacteria may be causing their symptoms. Well, a new test may provide better answers.

There are three main types of exfoliates : the mechanical ones with the little scrubby beads; enzymatic ones made from the acids of fruits such as pineapple or papaya; and AHA’s (Alpha-hydroxy Acids).

A facial massage can rejuvenate and soothe. Make sure your hands are clean to begin with. A lot of people don't like oil, having oil in their hands and putting it on their face, or they might be allergic to it or sensitive. So have a nice clean set of hands and starting with just saying hello to the head. Learn the art of giving massage in this health how-to video.

This video tutorial shows how to mount a large Chinese rice paper painting. Rice paper is extremely fragile and prone to tearing, thus requiring a technique sensitive to it's structure. Learn how to mount a large Chinese rice paper painting by watching this instructional framing video.

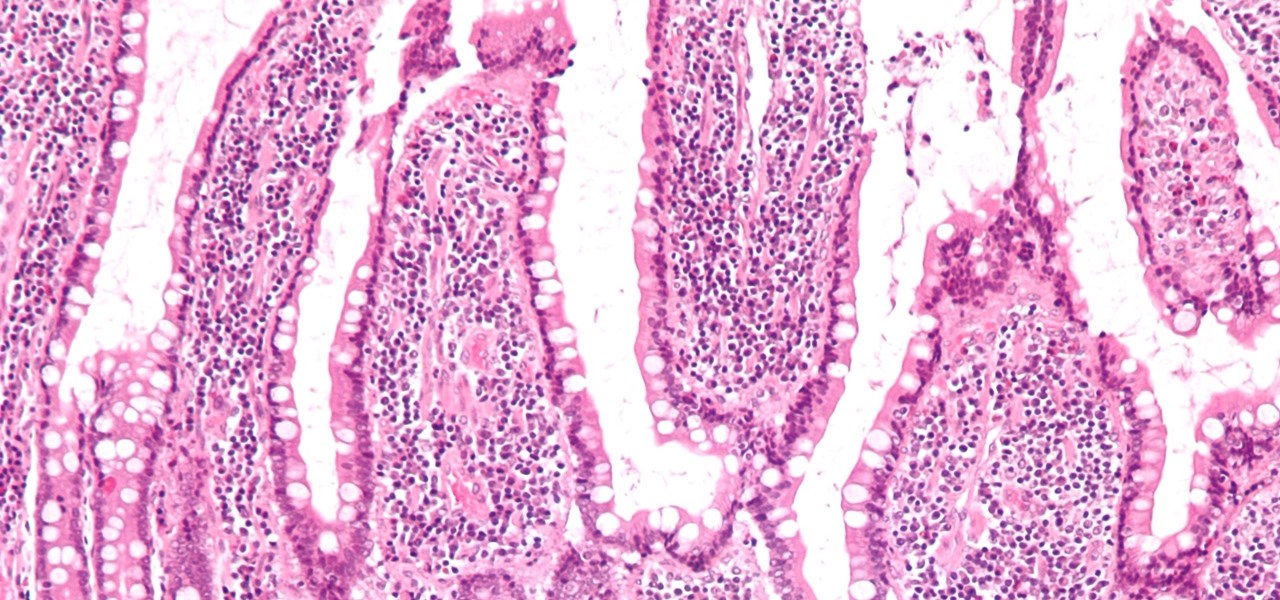
If the all the fingerlike projections in our gut were flattened out, its surface area would be 100 times bigger than our skin's. It's so large that the actions of just a small part of it can impact our health. A new research study has found that enterochromaffin cells in the intestinal lining alert the nervous system to signs of trouble in the gut — trouble that ranges from bacterial products to inflammatory food molecules.

Welcome back, everyone! In this lesson, I'm going to go over the use of the echo function and variables, as well as basic syntax.

Adding to the recent recent slew of bugs and issues within iOS 7, it now seems that emails sent with attachments are not encrypted, despite Apple's claims that they are.

I went to get my boat ready for the summer and discover that my engine block was cracked. I looked online to find the cost of a new block to be way out of my range so I decided to see if I could repair the cracked block. Cast iron is very sensitive to heat and I do not have the skills to weld cast iron. So I decided to see if JB Weld would repair the block or not. To discover if it worked or not, watch the video below.

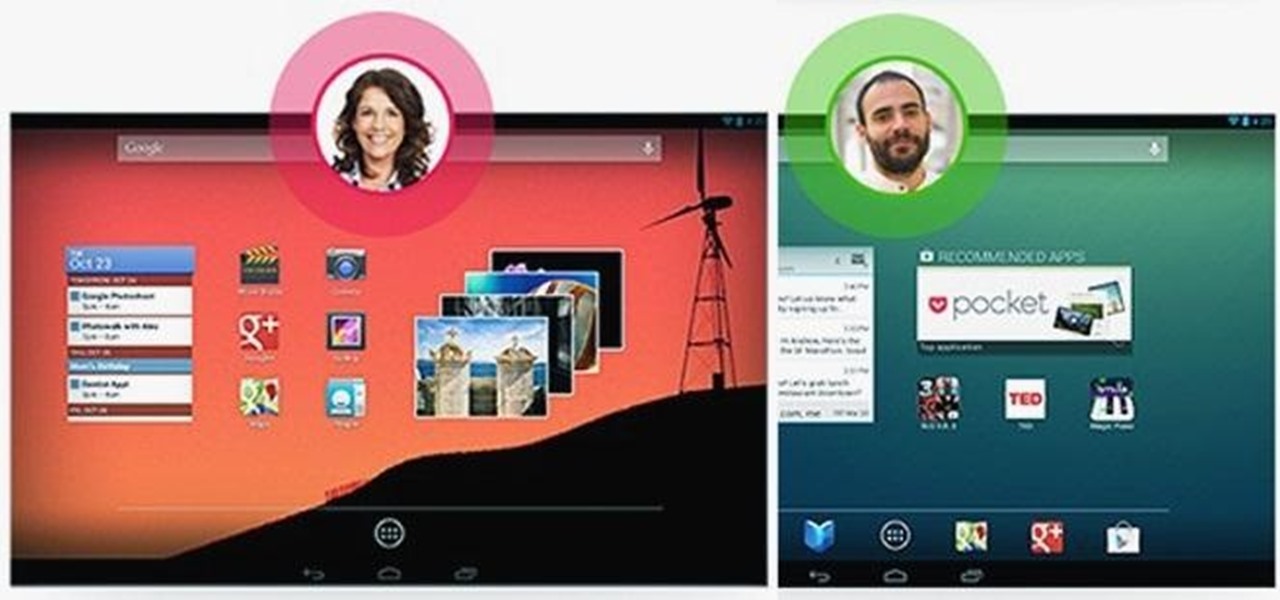
The most recent update for Android's Jelly Bean has some pretty cool new features, like better panoramic photos, gesture typing, and wireless sharing. From a security standpoint, though, the best new feature is the ability to add multiple users to one device. You can create up to 8 different accounts on Android tablets like the Nexus 7 or Nexus 10, so besides saving time hiding or protecting sensitive data, it could also save you some money. You can share a device with your family, kids, or s...

Sometimes we need to share screenshots, but don't want to reveal the entire screen. This usually requires some editing that isn't typically easy to do on a smartphone. BlackBerry recognized this issue and created a tool called Redactor that makes it easy to hide your data before sharing.

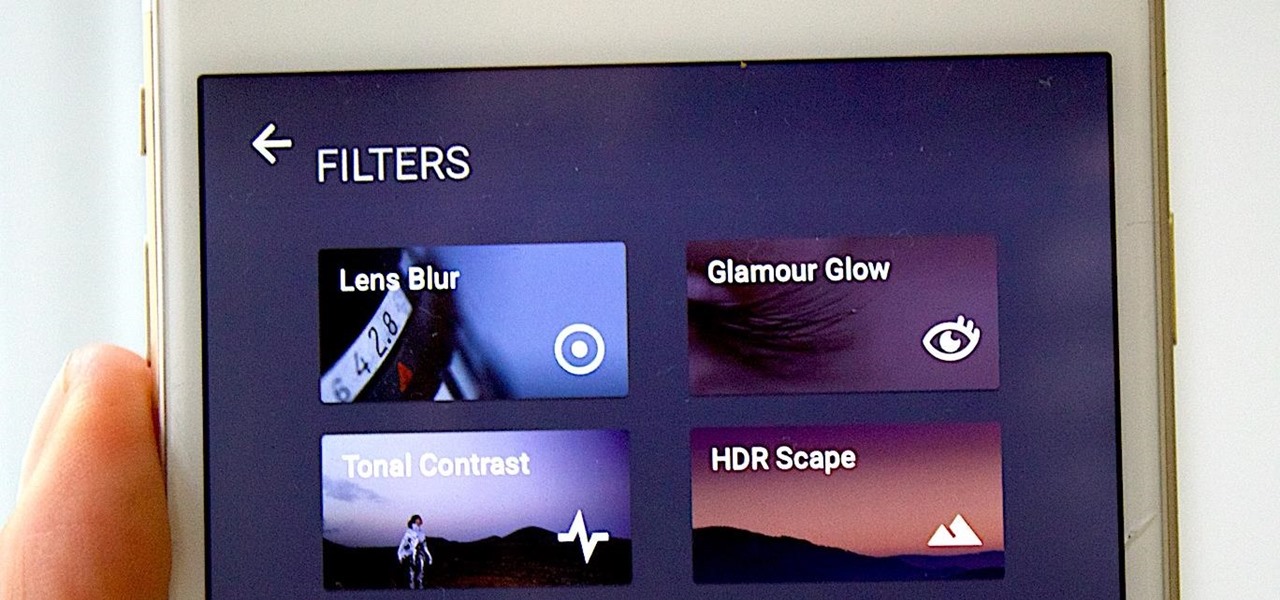
There are many different ways and many different apps that allow you to censor a racy photo and then share it to Instagram or Facebook. If you're in a time crunch and don't have the time or the patience to deal with something like Photoshop, then Snapseed is a great and easy app that will blur out your raunchy images in a quickie.

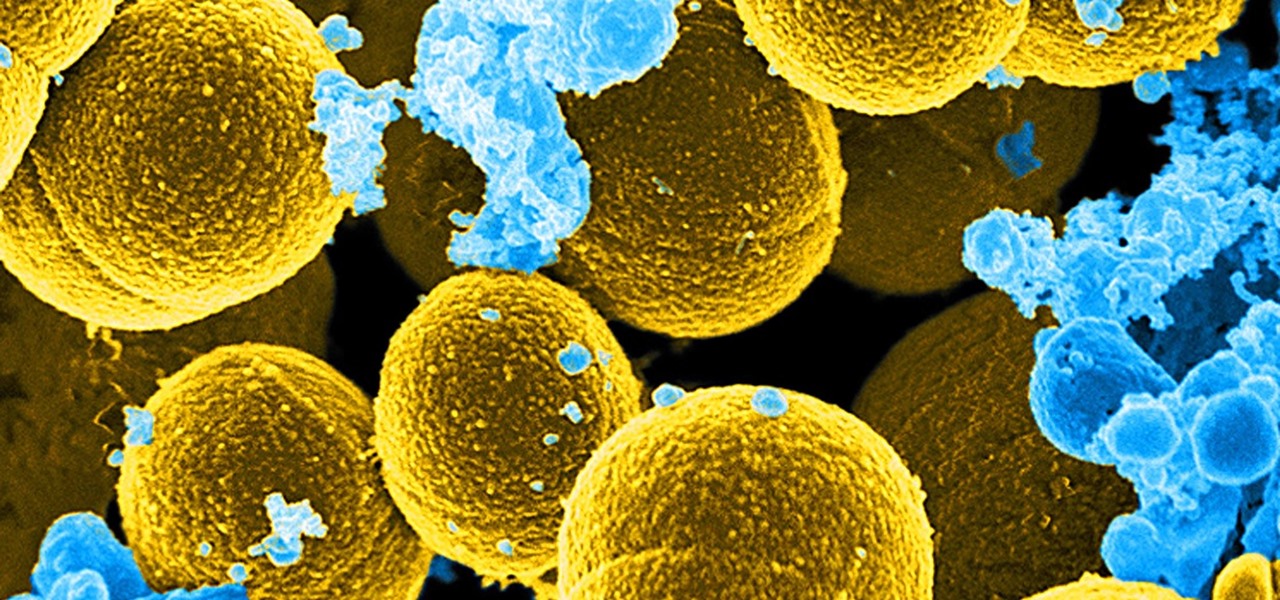
For once there is good news — surprising news, but good news — in the fight against antibiotic-resistant organisms. A recent study found that Staphylococcus aureus bacteria is becoming more sensitive to some key drugs used to treat it.

GitHub is an extremely popular site that allows developers to store source code and interact with other users about their projects. Anyone can download public, open-source files on GitHub manually or with Git, and anyone can fork off someone's project to expand or improve it into its own project. It's a really great site for programmers, developers, and even inspiring hackers.

If history holds true, we'll see the iPhone 7 arrive this September, and just like many times before, there are already a ton of rumors about its features. As usual, many claims are pure speculation, but there are some trustworthy reports and lots of good information we can use to make some educated guesses regarding Apple's upcoming flagship.

If you've switched ROMs before or flashed quick mods on your Android device, you've probably used TWRP or another custom recovery to install them. But another great purpose for flashing through a recovery is to install your own custom .zip file filled with everything a fresh ROM needs—namely, all your apps.

With all of the personal data that's stored on our smartphones, it's of vital importance that we have some sort of lock screen security enabled. One of the Galaxy S5's killer features is obviously the fingerprint scanner. It makes the process of dealing with a secure lock screen a bit easier than typing in a password or PIN.

Welcome back, my budding hackers! As you know, I firmly believe that to be a true professional hacker, you need to be proficient in Linux. This is for a number of good reasons.

Learn how to follow proper netiquette rules. You may be a model of decorum in person, but a bonehead online. Check out how much you know about Internet manners.

This video will show you how I changed my NAT Type from type 3 to type 2. Part 1 of 3 - How to Change your PS3 NAT Type 3 to NAT Type 2.

When using face unlock on the Pixel 4, your lock screen notifications are bypassed by default to help you unlock your phone instantaneously. This is different than Face ID on the iPhone, which shows the lock screen until you swipe up, but only shows notifications when you've been authenticated. If you want to do it Apple's way, there are settings you can adjust on your Pixel.

If you're concerned about someone accessing your OneDrive files, you may want to upgrade your protection by enabling fingerprint or Face ID unlocking. Your sensitive information deserves to be protected, and now you can do so easily. Worry no longer — if you need to let someone else use your phone, with a password-protected OneDrive, sneaky file grabbers will be out of luck.

The addition of a new research mode for Microsoft HoloLens will enable researchers and developers to tap into a wider range of data collected by the device's sensors.

HTC is working on another flagship device that's expected to be released in mid-April. After the disastrous reception of the recently released HTC U Ultra and HTC U Play, this new model could be the true HTC 10 successor we've all been waiting for.

Got some seriously sensitive information to keep safe and a spare-no-expenses attitude? Then the new Solarin from Sirin Labs is the smartphone for you and your $17,000.

Good day to everyone, today I will present some basic and advanced concepts that targets sophisticated attacks on the social basis, also I will write about some steps that can prevent this attacks from occuring, basically we will examine Social Engineering from the angle of attacker and victim, some people who are interested in security and work for middle-sized companys can learn and use something interesting from this post.

What you probably don't know is when you remove a file on your system, it is actually still saved, and not entirely removed. Let me tell you how to get rid of it completely.

Greetings, hackers and friends! I know it has been a while since I posted a tutorial, and hopefully I can make up for that by posting a series.

With troves of sensitive information, like receipts and password reminders, hiding in your email, your inbox can become a sort of Holy Grail for hackers—or anyone with your password. Although my crazy ex-girlfriend had no hacking experience, using my email login, she was able to find a lot of account information with just a general search for "password" in my inbox.

Did you know that your face shows others how much alcohol you drink? Whether you've never had a sip of booze with those around you or you're known as the party animal of the group, the genes that shape your appearance also show others just how much you enjoy liquor. Pinpointing the big drinker in any setting is easy to determine: you just need to make eye contact.

Whether you use a third-party keyboard or the stock offering, your Samsung device keeps a history of the last 20 words you copied on its clipboard. Samsung added this feature to Android to help make multitasking a bit easier, but if you use a password manager like LastPass, this feature quickly becomes a gaping hole in security. While you're copying and pasting your various passwords, the last 20 of them become freely available to anyone that gets their hands on your device.

Let's be honest for a second; we all have sensitive material on our phones that we wouldn't want anyone else to ever see. Maybe it's to protect ourselves or someone else, or maybe it's none of your business why I don't want you to see pictures of my bachelor party. Regardless, sometimes we need to keep things hidden and safe.

In my first tutorial on Linux basics, I discussed the importance of hackers using Linux and the structure of the directory system. We also looked briefly at the cd command. In this second Linux guide, I'll spend a bit more time with changing directories, listing directories, creating files and directories, and finally, getting help. Let's open up BackTrack and getting started learning more Linux for the aspiring hacker.

Do you want to be able to play games for free on your XBox 360? If you have some time and patience, hacking the console is probably the next step for you, and the first step in that is flashing your disc drive. This will delete it's native firmware, which does not recognize burned discs, allowing you to load your own custom firmware that does. This video series will teach you everything you need to know to flash each of the major types of disc drives used in the XBox 360, and have you well on...

Right out of the box, iPhone is incredibly easy to use. If you want to get the most out of every feature, you’ve come to the right place. This video tutorial straight from Apple will teach you how to use the keyboard on the Apple iPhone 3G. The iPhone redefines what a mobile phone can do.

"Magic The Gathering" has many card types like land, spells, sorcery, enchantments and more, each with its own strategy. Learn "Magic The Gathering" cards and card types from a certified judge in this free magic cards video series.

Welcome back, my rookie hackers! I recently began a series on using Metasploit, and my goal with it is to teach you the very basics the incredibly powerful hacking tool has to offer while progressively moving on to the more advanced features.

Violin Lesson #32-33 -- 4 Types of Shifts. Todd Ehle discusses the four types of shifts on the violin in this 2-part lesson.