There is a vast amount of knowledge out there on computers! In fact, it is so vast that no single person could ever possibly ever learn everything there is to learn about hacking or computers in general. People usually specialize in a certain field: cryptography, computer security, networking, software development, testing, and so on...It's probably a bit premature to decide what you want your speciality to be, but keeping the question in the back of your mind will help give you direction in ...

Cryptography is a quintessential part of computer security in the modern world. Whenever you buy something on eBay or log into Facebook, that data is encrypted before it's sent to the server in order to prevent third parties from eavesdropping and stealing your sensitive information.

Skype is a great service. It allows a free solution for VoIP to VoIP calls, and cheap VoIP to landline calling. However, a very disturbing, little known fact that might push you away from Skype does exist. If you closely read the terms of service agreement, it clearly says that Skype is allowed to decrypt your messages whenever they please. Here at Null Byte, we tend to enjoy our anonymity, don't we?

Video game controllers are our windows into the soul of the machine, our sole means of interacting with them. More often than not, consumers seem displeased by their controllers; it's comforting to blame sticky, poorly laid out buttons for messing up your game than your own lacking skills. The original "fatty" Xbox controller was so large it caused mass consternation and prompted Microsoft to replace it with a smaller version in a matter of months.

With the mass arrests of 25 anons in Europe and South America, and the rumors of an FBI sweep on the east coast of America floating around, times look dicey for hackers. Over the past few days, a lot of questions have been posed to me about removing sensitive data from hard drives. Ideas seem to range from magnets to microwaves and a lot of things in-between. So, I'd like to explain a little bit about data forensics, how it works, and the steps you can take to be safe.

This is the third part of my electromagnetic pulse series (see Part One and Part Two). By now, I've covered the hardware and general concept of electromagnetic pulse generators, but how exactly do they disable electronics? How can an invisible field of energy have such a catastrophic effect on computers, cell phones, and most any other electronics? I'll be answering all these questions in part three of Making Electromagnetic Weapons.

We're officially seeking Null Byters on a weekly basis who are willing to take the time to educate the community. Contributors will write tutorials, which will be featured on the Null Byte blog, as well as the front page of WonderHowTo (IF up to par, of course). There is no need to be intimidated if you fear you lack the writing skills. I will edit your drafts if necessary and get them looking top-notch! You can write tutorials on any skill level, and about anything you feel like sharing that...

We're officially seeking Null Byters on a weekly basis who are willing to take the time to educate the community. Contributors will write tutorials, which will be featured on the Null Byte blog, as well as the front page of WonderHowTo (IF up to par, of course). There is no need to be intimidated if you fear you lack the writing skills. I will edit your drafts if necessary and get them looking top-notch! You can write tutorials of any skill level, about anything you feel like sharing that is ...

Snapseed is a highly regarded and award-winning photo-editing app for iOS devices. Originating out of image manipulation specialist Nik Software in San Diego, Snapseed is Apple’s iPad App of the Year and, after using it for the purposes of this review, I believe it points to the future of image editing.

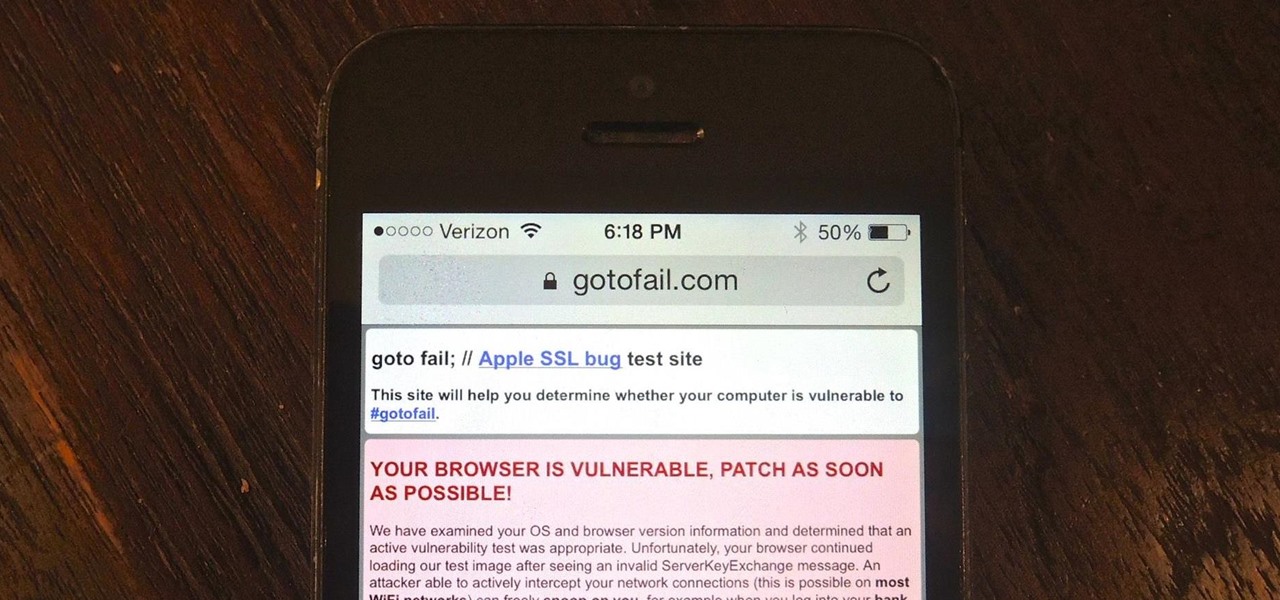
SSL stands for Secure Socket Layer. It's an encryption standard used on most sites' login pages to avoid their users' passwords being packet sniffed in simple plain-text format. This keeps the users safe by having all of that traffic encrypted over an "https" connection. So, whenever you see "https://" in front of the URL in your browser, you know you're safe... or are you?

Dropbox continues to make headlines with their recent programming blunder which left the accounts of its 25 million customers wide open during a four-hour time span. During the duration, anyone in the world could access any Dropbox profile by typing in any password. And seeing as this wasn't the first security failure, everyone, including the most loyal users are considering dropping the Dropbox.

Moving up from a point and shoot to a digital single lens reflex camera is a big step. And actually, a DSLR can be a better buy than a new point and shoot, many of which rival the prices of entry level or used DSLRs. Keep in mind when you buy a new body, the lenses are the most important elements. Once you start investing in them, it makes it much harder to switch brands. So if it isn’t too late, do some research.

I have said it before, and I’ll say it again: if the United States can put a monkey in space, it can certainly come up with a way for me to eat 5-10lbs of chocolate per day without gaining any weight! Sadly, however, no one seems to be tackling the calorie-less food problem, so I’m here to share my favorite foods that don’t land on your thighs.

The days of trundling hoops, hopscotch and painted wooden rocking horses are long since past. The latest trend in toys? Biofeedback. Electroencephalography. A decade into the 21st century, the toy market is awash in products that incorporate functional neural sensors.

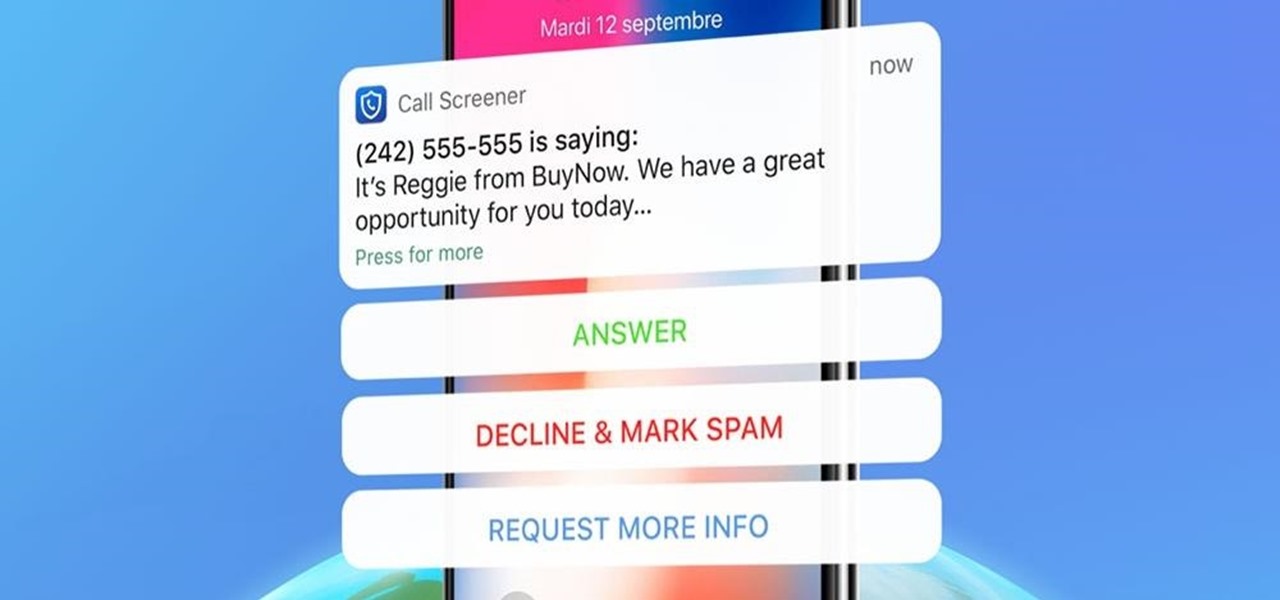
We all know the stress that a ringing phone causes these days. Should you pick up that unrecognizable number? More often than not, it's a bad decision. You hear the automated message and hang up. Or worse, a real human asks you about your day before trying to sell you something.

Copying and pasting is even more important on a phone since there's no mouse and keyboard. And like on a computer, copying is usually limited to one item at a time — but with the Samsung Keyboard app, you have the ability to copy multiple sets of text.

Applications are finally beginning to make use of Android 6.0's fingerprint authentication, letting users access sensitive information without having to enter (or unsafely store) complicated passwords on their phones.

Apple released iOS 7.0.6 last week, an update to fix a serious security flaw that allowed hackers to not only capture sensitive user information such as bank statements and passwords, but also modify that same data on secure HTTPS sessions.

Vibrate is not as inconspicuous as one might think, which means silent mode is usually the option that many stick to when in class, at work, or anywhere that forbids loud noise.

Security is always a top priority for our smartphones. Leaving your phone at the bar or even at a friend's house can leave you open to hacks and lead to the loss of sensitive information.

PDF files are awesome because they're easy to share and they prevent the format on your document from being messed up, no matter what system or program it's opened in. Their biggest downside, though, is how difficult they are to edit or change once they're made.

According to Wikipedia, "Sympathetic Resonance is a harmonic phenomenon wherein a formerly passive string or vibratory body responds to external vibrations to which it has a harmonic likeness."

Trippy! Get the kids around the table for this one.

You walk over to your laptop, wiggle your mouse to wake up the screen, then fire up your browser to come visit Null Byte. Catching the article about Anonymous and how they presumably will not take down the Internet, you find yourself wondering... how would someone take down the Internet? Could they even do it?

Industrial espionage, social engineering and no-tech hacking are all very real and there are simple precautions that you can take to protect yourself, which this article will discuss. Whether you are a high-profile businessman or a housewife (or husband), keeping information you want to keep private, private, should be important to you.

If you're interested in bypassing Windows and Linux passwords, there is a great tool from the good people at Kryptoslogic. Have you ever forgotten your administrator password? Have you ever bought a used computer with a password on it? Well, Kryptoslogic have created a boot-disc call 'Kon-Boot', which allows you to bypass any Windows 32 or 64 bit OS, as well as Linux passwords. There is both a paid and freeware version available.

You can blame your naggy mom, a crappy soap bar, and school or work stress for your acne. But ultimately, you should blame yourself. While it's true that your skin type (oily vs. dry vs. sensitive) and how your skin reacts to stress play a big part in blemishes, there is a nurture component to this argument.

Over the past couple of weeks, there have been a series of high-profile hacks and leaks. From the rooting of CombinedSystems, to a secret FBI conference call leak, all the way to the distributed denial-of-service (DDoS) attacks on U.S. government sites—with a lot in-between. As governments move to close their long fingers around the free speech that exposes their secrets, this shadowy collective of loose-knit, but like-minded individuals are hell bent on preventing them. Or are they?

Color Correction: Put Your Best Foot Forward via Hurlbut Visuals

I've been dealing with emotional difficulty for many years. It started when I had surgery for the epilepsy I was dealing, and quite literally, dying with. Since the surgery on March 28, 1990 I have had no seizures, but I have had plenty of emotional difficulty. Along with that, surviving some traumatic events has added some emotional baggage...in other words struggling...along the way.

Tim Hawkinson is an artist who truly inspires. The Los Angeles based artist creates complex, whimsical sculptures with simple mechanics and basic materials. One of his most notable pieces is the art-world-renowned "Uberorgan", a giant football field sized, fully-automated bagpipe, cleverly constructed with plastic sheeting and pieces of electrical hardware.

Good skin care begins with knowing what kind of skin your have, what special issues you have, and what products work best for your skin. In this video we show you how to identify your skin type and choose skin care products that best suit you. Skin Care Routine

Want a buff bod? No need to workout! Just follow these steps to exfoliate and get beautiful, glowing skin. Loofah

Tired of seeing large pores on your face? Need to take care of this problem before it gets out of hand? Below, you will see steps that you can take to rid yourself of this problem.

A few simple tips on learning to use brushes in Photoshop if you have a pressure sensitive tablet (like Wacom) and stylus pen. Use Photoshop brushes with a stylus.

This video shows you how to use the new context-sensitive control panel in InDesign to access frequently-used editing features without opening additional panels. You learn how control panel options adapt to the type of object you select, such as an image, text, or table. Check out this video created by Adam Pratt now! Use the control panel with InDesign CS3.

Locked out of your house? Well make your life easier with a code sensitive garage door opener. This is a simple step to install a garage door opener. He shows where it should go and how to just use a screwdriver to install it. Add and install a garage door opener.

Your kitchen holds the secret to great skin. Use these ingredients to make facial scrubs in your own kitchen. Coffee grounds

Note: The article assumes that the reader has a fundamental understanding of at least one other programming language, and that this is intended serve as a quick reference for Perl's basic syntax & behavior in regards to Variables, Control Structures, & Functions.

This stunt involves the entire Jackass Crew wearing nothing but speedos and connected by ropes that are attached to them by the waist one-by-one like a linked chain. The length of the rope should be roughly 2-3ft long separating each person. A ledge or platform about 1ft in width can be either wood planks or some type of industrial metal, if all of their weight won’t be able to support the wood. This platform is sitting over a pool by a couple of feet. Inside of the pool is some kind of disgu...