How To: Some Terms a Hacker Must Know...
Welcome back Hackers\Newbies!

Welcome back Hackers\Newbies!

With all of the personal data that's stored on our smartphones, it's of vital importance that we have some sort of lock screen security enabled. One of the Galaxy S5's killer features is obviously the fingerprint scanner. It makes the process of dealing with a secure lock screen a bit easier than typing in a password or PIN.

The Samsung Galaxy S5 was just officially announced at Mobile World Congress. The new flagship device will be available worldwide beginning April 11, 2014, including all major U.S. and international carriers. With over 200 million Galaxy devices sold to date, the S5 doesn't stray too far from the trend, at least not aesthetically. We've still got a high-grade plastic shell with perforated back covers, and four color choices at launch. Our highlights of the release event are as follows.

Welcome back, my budding hackers! As you know, I firmly believe that to be a true professional hacker, you need to be proficient in Linux. This is for a number of good reasons.

I went to get my boat ready for the summer and discover that my engine block was cracked. I looked online to find the cost of a new block to be way out of my range so I decided to see if I could repair the cracked block. Cast iron is very sensitive to heat and I do not have the skills to weld cast iron. So I decided to see if JB Weld would repair the block or not. To discover if it worked or not, watch the video below.

Back in the '80s, I was just a kid with a LEGO hobby. I remember building castles and floating boats, spaceships and monster trucks, even a working LEGO train powered by battery, lights and all.

Riding a bike is a great way to get exercise and as means to getting around but incorrect bike assemble will make for a bad time. Double check all your work and make sure everything is lubed up and fastened before taking your bike out for a spin.

The makeup artist Julia presents this tutorial in partnership with VSP vision care in order to demonstrate makeup tips for people wearing glasses or contact lens.

Apple's Always-On display feature for the iPhone 14 Pro and 14 Pro Max can show important information on the screen even when the device is sleeping. While the dimmed Lock Screen may seem like a WYSIWYG component, there are actually a few ways you can customize it to fit your needs better.
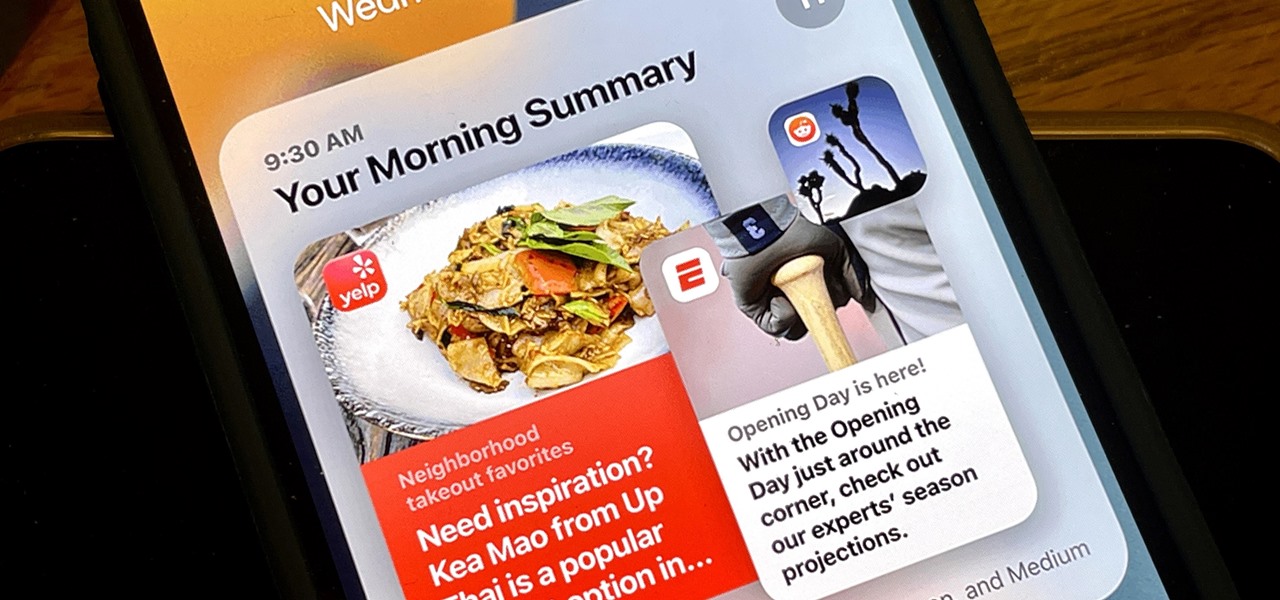
Apple unrolled an array of nifty iPhone features in iOS 15. One of the more valuable updates lets you group all your untimely notifications and view them throughout the day at only the times you choose.

Google is an incredibly useful database of indexed websites, but querying Google doesn't search for what you type literally. The algorithms behind Google's searches can lead to a lot of irrelevant results. Still, with the right operators, we can be more exact while searching for information that's time-sensitive or difficult to find.

It's important to know who you're dealing with after hacking your target's MacBook. Getting remote access is simple, but covertly gathering information about the user and their system can be a challenge.
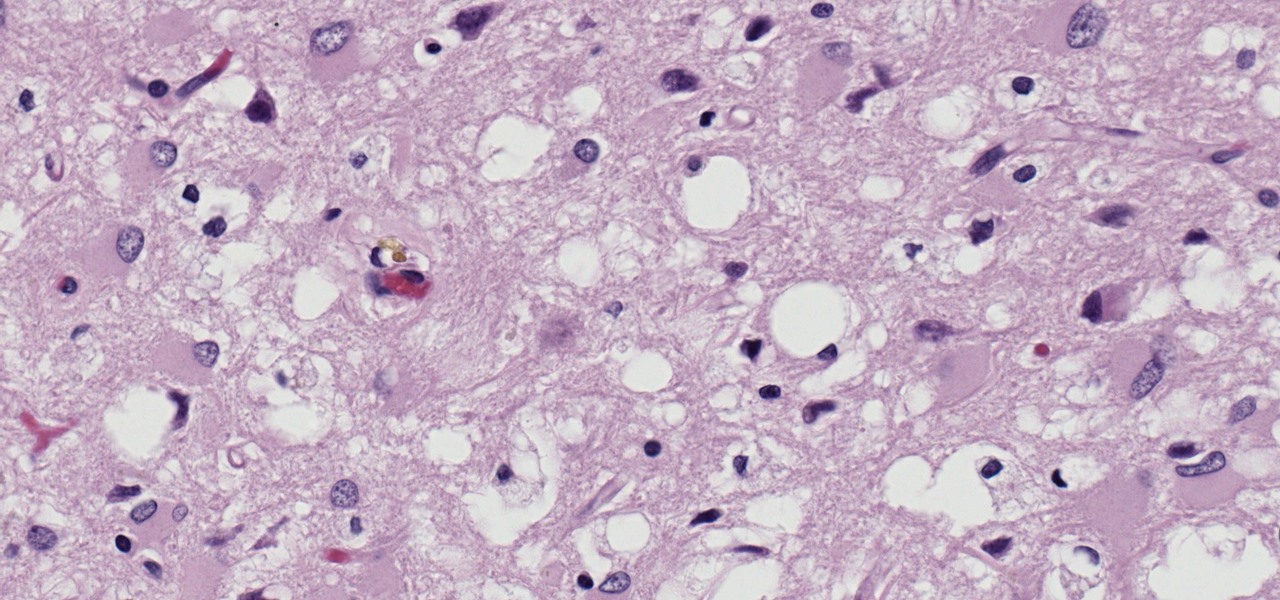
Prion diseases are a group of infectious brain diseases that causes extensive tissue damage, resulting in sponge-like spaces in brain tissue. Prions include Creutzfeldt-Jakob disease in humans, bovine spongiform encephalopathy (often called mad cow disease), and chronic wasting disease in hoofed ruminant mammals.

After poor sales of last year's HTC 10 and the terrible reviews their first 2017 flagship received, HTC really needs the HTC U11 to succeed. But they're not taking things lying down, as they've come up with some interesting tech for their latest handset.

Before we dive any further into getting your Mac ready for hacking, I wanted to continue on with the concept of encryption. In the last part, we talked about full disk encryption on your Mac, but now I want to quickly cover the encryption of disk images before we dive into managing passwords, terminal emulators, etc.

Good day to everyone, today I will present some basic and advanced concepts that targets sophisticated attacks on the social basis, also I will write about some steps that can prevent this attacks from occuring, basically we will examine Social Engineering from the angle of attacker and victim, some people who are interested in security and work for middle-sized companys can learn and use something interesting from this post.

What's your top pet peeve? Open-mouthed chewing? Nail biting and knuckle cracking? The sound of silverware scraping? Or perhaps it's a bigger behavior, like leaving the toilet seat up?

In this article, I'll be explaining the basics of how microcontrollers work, physically and virtually. First off, microcontrollers are no simple thing, so don't be discouraged if you find it mind-boggling! The world of microcontrollers is fascinating, engaging, and an awesome hobby; it never gets boring. I'll be focusing more on I/O and analog based microcontrollers, such as those running Arduino, and using Atmel chips as examples (these are most commonly available, and easy to program).

We've all seen the breathtaking, colorful photos of the Eagle, Egg and Cat's Eye Nebulae. You may not recognize them by name, but you've seen them, whether in astronomy textbooks, magazines, websites, album covers, or tee shirts. They are some of the most striking photographs ever taken from the Hubble Space Telescope (HST).

While new features in Safari, Camera, Photos, Notes, Weather, Messages, and other Apple apps may steal the show on iOS 17, there are some impressive new features you need to know about when it comes to FaceTime audio and video calls.

Withstanding an attack from a motivated hacker is one of the most important responsibilities a system administrator must undertake. This is especially true for websites that may contain sensitive customer information and a high volume of users. So it's important for a sysadmin to take proactive measures to find and fix vulnerabilities in their websites.

You can lock practically any app on your iPhone or iPad behind biometric or passcode protection. And we're not talking about using any funky workarounds, either. There's now an official Apple way to protect sensitive apps and their data. It even safeguards your personal information, keeping it out of sight across the system. You can even hide apps, making it harder for others to know they're there.

Apple just released its iOS 16.6 update for iPhone on July 24. When you install the new software, it may look like there's not much to it since Apple doesn't include any features in the release notes beyond "important bug fixes and security updates," but a few new features are hiding within.

A little-known setting on your iPhone gives you the power to change the color of certain contact names and email addresses when drafting an email. Customizing the color works well for visually separating contacts at a glance, and it can even help you from sending an email to the wrong person.

With protests springing up across America, there's a chance you may have your first interaction with law enforcement. Many demonstrators will have their phones in-hand to film the action, which, sadly, could prompt an officer to demand the device and any self-incriminating data it may contain. Before this happens, you should know there are tools at your disposal to protect your data in such situations.

In iOS 13, Apple added an important new feature to its HomeKit smart home ecosystem called HomeKit Secure Video. With it, you have a secure, private way to store and access recordings from your smart home IoT cameras.

Smartphones have so much sensitive information attached to them. If you share your home with others, then you know the pains of trying to keep anything private. Photos are surely among the things you'd prefer to keep to yourself, so OnePlus has you covered.
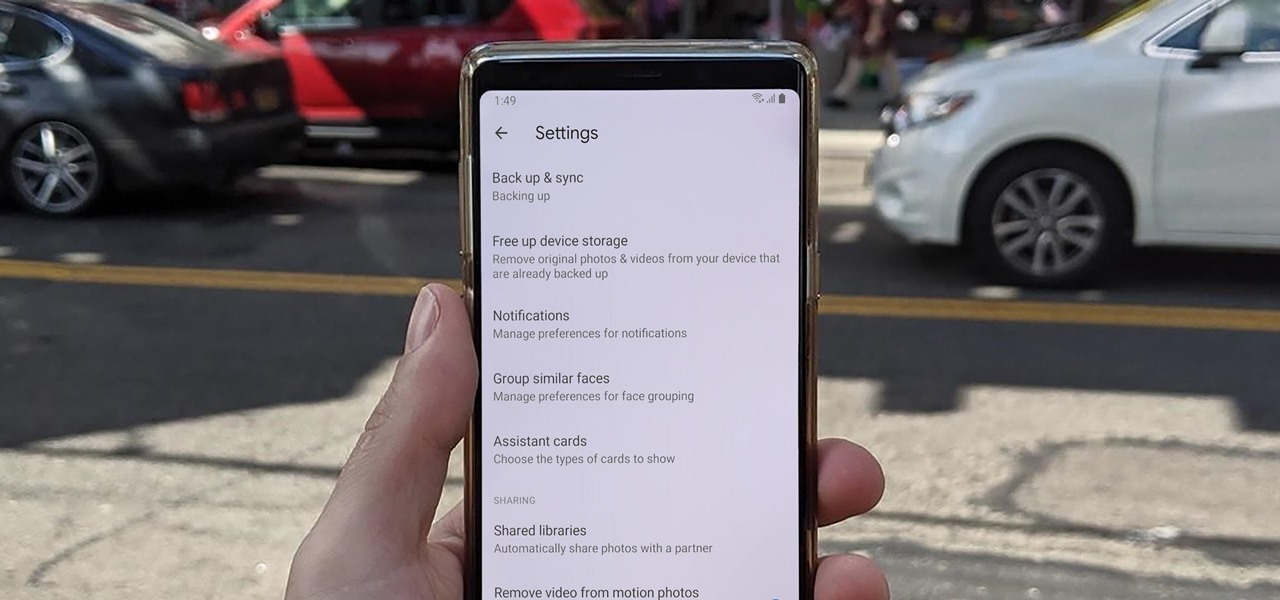
Sharing pictures from Google Photos by sending a link saves time because you don't have to download the image from Google, then reupload it somewhere else. But anyone who has your link can access your pictures, and baked into every file is metadata that you may not want prying eyes to know about.

|Choose Your View: Quick Bullet Points | Detailed Descriptions Android's newest major update is a special one — it's the tenth full version of the world's most commonly used operating system. The latest release, dubbed simply Android 10 (codename Android Q), was first showcased as a beta back in March 2019, so we've been digging around in it for several months. There's one dramatic visual change, plus there are a lot of goodies in general.

In the realm of internet security, it's becoming clear that augmented reality is not immune to the increasing wave data breaches plaguing users.

Once you've installed Ubuntu with security in mind and reduced the possibility of network attacks on your system, you can start thinking about security on an application level. If a malicious file is opened on your system, will an attacker be able to access every file on the computer? The chances are much slimmer if you put the proper defenses in place.

The HTC U isn't set to be revealed until mid-to-late-April, but that isn't stopping the leaks from creating hype. Weibo user Ann Bunny just leaked a spec sheet for the new HTC phone, which can be seen below. Keep in mind, though, all details are still just rumors at this point, but they're certainly juicy.

Facebook Messenger is getting ready to roll out a Snapchat-esque feature that will let users send messages that self-destruct after a certain amount of time, so you'll have an extra level of security when you need to send sensitive financial information or, more likely, risqué texts or images.

The highly anticipated VR headset hasn't been on the market long, but there's an issue that has some consumers, and even government officials, concerned about the Oculus Rift. You probably guessed the issue surrounds privacy and the extensive, not-so-secret way that it's collecting your personal data. The privacy concerns came about as various customers and media outlets took notice of the rather lengthy Terms and Services that pop up once you strap yourself into the Rift headset.

Hello Everyone! I wanted to share a free and open source note taking tool that I've been using for quite some time now.

You would think that with each major iOS update, there'd be fewer ways to bypass the lock screen. Unfortunately, Apple's developers have consistently failed every year since 2013 in this department, leaving open lock screen exploits for iOS 7, iOS 8, and now the latest iOS version, iOS 9, with each exploit being discovered within days of the OS release.

A four-digit passcode is what protects your iPhone, and the sensitive material within it, from strangers or nosey friends. Four digits are the only thing preventing someone from snooping through your pictures and posting them online for the public to see, and that's if you even have passcode security enabled.

Lending someone your phone to make a call is always an awkward situation, as you closely monitor them to make sure they stick to a phone call rather than wandering off into private applications like your photo or messaging apps. You don't necessarily want to eavesdrop on their conversation, but trusting people with your phone is difficult, especially if you have some risqué or embarrassing pictures stored on it.

It's universally known that broccoli, kale, Brussels sprouts, cauliflower, and all cruciferous vegetables (also known as brassicas) are good for you—but you probably don't know exactly how good they really are.

Adding to the recent recent slew of bugs and issues within iOS 7, it now seems that emails sent with attachments are not encrypted, despite Apple's claims that they are.