It's no surprise that the Microsoft Kinect can provide far better motion tracking than the HoloLens currently can on its own, but at least one developer didn't want to wait for the company's own eventual implementation. Kyle G, founder and CEO of Wavelength Studios, projected his movements using a Kinect into a holographic zombie.
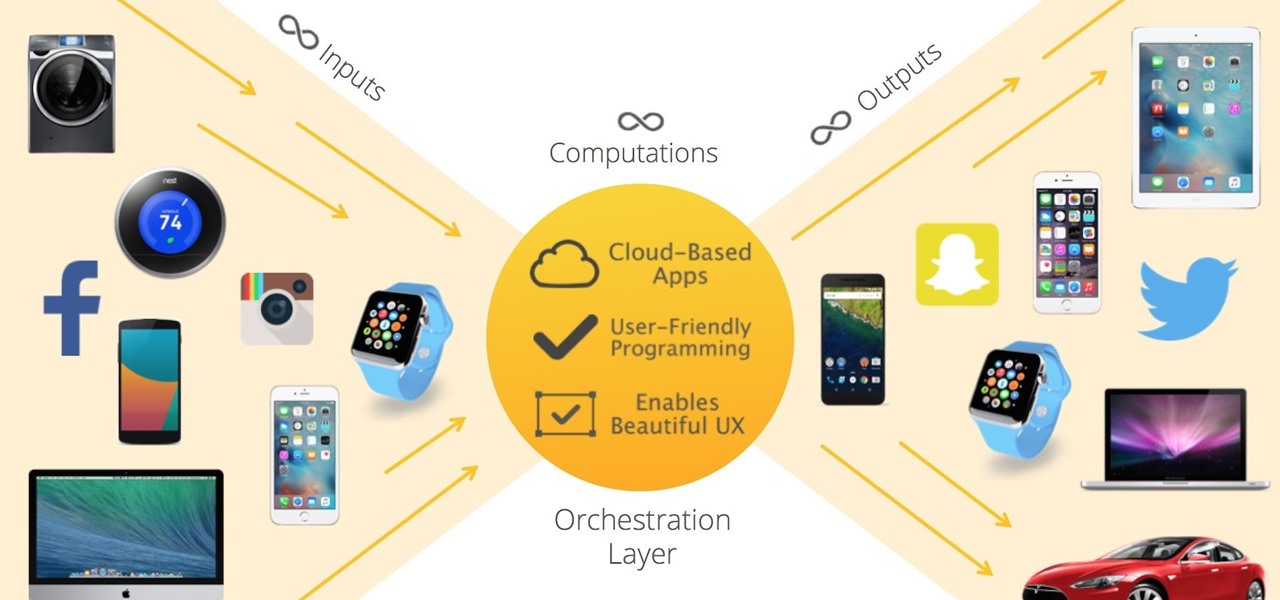
Mixed reality can give you the feeling that you've uncovered a hidden world layered into the physical one you already know. This can happen in so many ways, from a trading card that births a hologram or a first-person shooter with robots blasting through your walls. Xperiel—a California-based augmented and mixed reality company—wants to create a platform to make that a whole lot easier for developers.

Last week, the U.S. Justice Department issued criminal indictments against seven Iranian hackers. These hackers, working for private companies in Iran, are accused of orchestrating DDoS attacks against U.S. financial institutions from 2011-2013 as well as intruding into the control panel of a small dam in Rye, New York. It is thought that these attacks were a response to the U.S. tightening financial restrictions on Iran during those years and the NSA-based Stuxnet attack on their uranium enr...

Netflix has become the subject of heavy buzz this week, and not due to the latest season of Daredevil (which gets two thumbs up, btw). The online video entertainment provider is drawing fire over its admission that it has been throttling video streams for its AT&T and Verizon customers for years.

If you have personal information stored on a Kindle Fire tablet, be warned that Amazon has removed encryption support for Fire OS 5. So if you have stuff on these devices...maybe a risque book, or private notes, or pictures you'd rather not let out to the world, now would be the time to remove them. And unless Amazon changes its mind and re-enables encryption, don't use your device for anything personal, as anyone who gets a hold of it will be able to gain access to everything on it.

There was one company at the 2015 LA Auto Show that had everyone intrigued. They didn't have a big booth, and they only had one car on display, but they definitely had everyone's attention.

CEO's of IT companies doesn't know this because they are not a hacker. Only a true hacker can become a successful Security head officer.

Hackers are claiming money for a security flaw in Apple's new update. Quick Summary:

Surely you're aware of the Sony hacking scandal by now (here's a quick primer if you're not), as well as the multi-billion dollar company initially bowing to threats by canceling the Christmas release of the The Interview, the film at the center of the whole debacle.

In previous posts here, I have pointed out that hackers are in high demand around the world and in nearly every industry. Every military and espionage unit of every country is trying to hire high-quality, experienced hackers as fast as they can to hack their adversaries' computer systems in order to gain a strategic advantage and to spy.

Welcome back, my greenhorn hackers! Continuing with my Wi-Fi hacking series, this article will focus on creating an invisible rogue access point, which is an access point that's not authorized by the information technology staff and may be a significant security vulnerability for any particular firm.

A car is stolen every 33 seconds in the United States, and from that, the percentage of vehicles recovered in the first day is a whopping 52 percent. Over the next week, that number rises to around 79 percent, but after those initial seven days are up, it's unlikely the vehicle will be found.

Prepaid phones are becoming more and more popular, and tons of people can see the benefits of switching now that some companies are offering prepaid services that are on par with the big players. For a lot of folks, the only thing keeping them from switching is the huge early termination fees that service providers charge to break a contract early.

There are tons of situations that require you to give out your phone number, and I think just about everyone has regretted doing so at some point. It can be incredibly convenient to have a secondary or temporary number on hand, so if you don't want to provide your real digits, you can still get the call without revealing your true numbers. And that's where Burner comes in. Burner is a mobile app for iPhone and Android that lets you create alias phone numbers that you can take out of service a...

Lots of designer purse companies, especially Coach and Kate Spade, LOVE attaching beaded charms to their purses and clutches. Sparkly little bits and pieces add extra pizazz to anything they're attached to.

Let's face it ladies: All of us come with some baggage. While some of us have emotional baggage, we all have the physical kind: undereye baggage. This sagging and drooping of your undereye area is further aggravated by fine lines, wrinkles, and purple or blue circles. Ah, the loveliness of getting older.

Tom Pecheaux, Estee Lauder's new creative director, came to the company with a vision in mind: Bold, more unexpected drops of color for their eyeshadow palettes, lipsticks, and glosses. And bold is the only way to describe his Blue Dahlia palette, which is filled with intense electric blues, blacks, and silvers.

We all love primping products, but what girl doesn't want to save a few bucks when she can? While lots of beauty companies will advertise that they have the best curling iron for you to achieve those Kate Hudson beachy waves, the truth is that you really don't need a curling iron at all. In fact, to get your hair bouncy and curly, all you really need is a flat iron.

Have you ever been in a situation when you needed to remember something real important, but you didn't have you didn't have your trusty cell phone or other electronic savior with you?

Maya and Photoshop CS4 may be made by different companies, but that doesn't mean they can't work together. This video will teach you how to take a 3D model from Maya, import it into Photoshop, and then use Photoshop CS4's new 3D editing tools to overpaint the rough texture seams in the model. The end result will be much prettier than the model that you could have created with Maya alone.

Although not has highly popular as Call of Duty: Modern Warfare 2, Battlefield: Bad Company 2 is one of the few shooter games that is able to seperate itself from the arcade style of COD:MW 2. In B:BC2 you rely on strategy and teamwork in order to win multiplayer matches and the game. But if you're looking for something that will make you smile, check out this tutorial. In the video, you'll find out where the Sandcastle Easter egg is on one of the maps. It's just a small little thing, but is ...

Is there any character in the history of cartoons more iconic than Mickey Mouse? You'd be hard pressed to think of one, and in this tutorial, you can become part of the legend by learning to draw him!

This helpful video explains how to use letters when dialing on a Blackberry. Many companies have words in their phone numbers so Darci Larocque shows us how to dial those letters. All you have to do is go to the call log, and hold the key in, and type in whatever word you are trying to dial. She also shows us another tip: if you are calling an office and you need to enter in someone's last name, you can do that the same way. Blackberry users should definitely view this video.

Ana Maria, an origami artist, shows you how to make an origami angelfish. Her video explains in step-by-step detail how to make one of these cute paper folded creatures. By viewing her high-resolution video you can create an angelfish in less than 5 minutes. The video is by Hawk vs. Pigeon company, which specializes in video production. Their videos are always crisp, so demonstration videos are easy to follow. Make your origami angelfish today.

Club Penguin is a flash-based website with an a virtual world of online games for kids to play. Learn how to hack Club Penguin with tricks and cheats. Watch this video tutorial to learn how to find hidden items in the Club Penguin catalog (09/29/09).

Having trouble with people snatching your stuff? Did someone take your lunch from the company fridge? Here is an inexpensive, sneaky gizmo you can make to keep those sticky fingers away. This is a junk drawer hack from Make Magazine's Kipkay. It's activated when an item is moved from it, triggering a clothes pin to close and activate the voice command. See how to make a talking booby track in this video tutorial with KipKay!

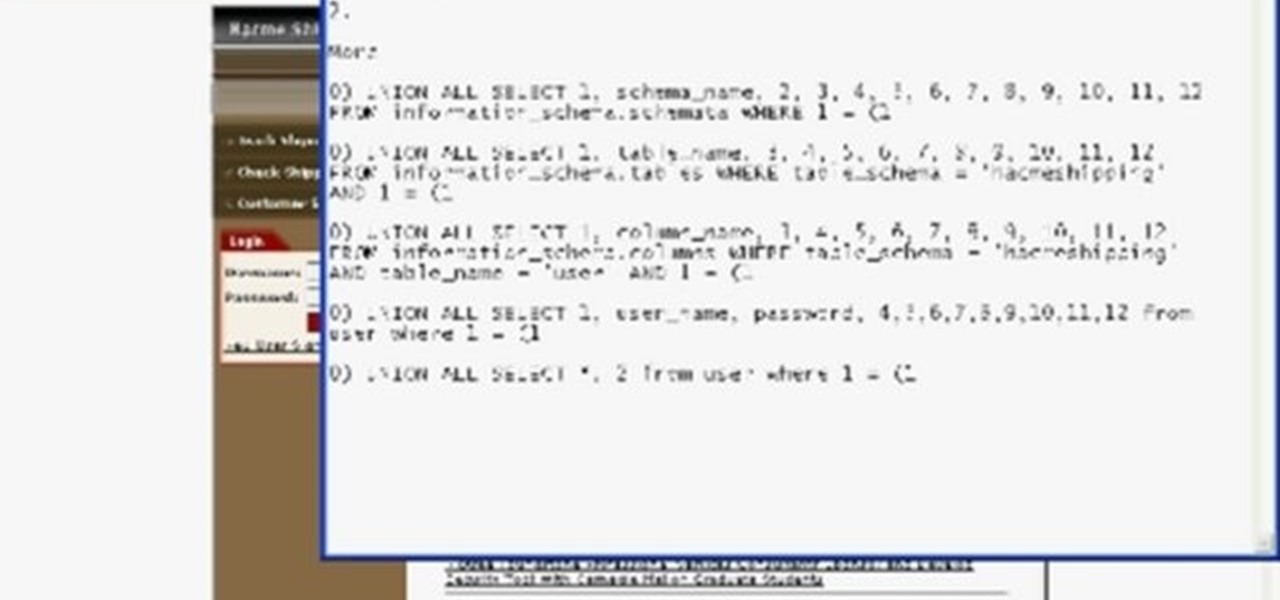
Foundstone Hacme Shipping is a web-based shipping application developed by Foundstone to demonstrate common web application hacking techniques such as SQL Injection, Cross Site Scripting and Escalation of Privileges as well as Authentication and Authorization flaws and how they are manifested in the code. Written in ColdFusion MX 7 using the Model-Glue framework and a MySQL database, the application emulates the on-line services provided by major shipping companies. This video will get you st...

This software tutorial takes a look at how to design an icon set in both Photoshop and Illustrator. An icon set is a set of icons that you can integrate into a number of different projects, like a website or a company letterhead, logo and identity set up. Having an icon set readily available for all your project needs will make your workflow faster and simpler. So watch and see how to make an icon set first in Photoshop and then in Illustrator.

You know how often times you'll find almost perfect jeans at the store, with the perfect faded wash, boot cut, and dark navy color, but they're just a wee bit too tight and a wee bit too long? Have you ever wished that the jeans company tailored those pants to you?

In the "Black Swan," Natalie Portman plays a veteran ballet dancer driven mad by the new young starlet in her company who threatens to usurp her place. Pretty soon, her dark and dreary mental state begins to affect her physical appearance as well.

Wouldn't it be nice to know how many people actually visited your site each day, and how long they stayed there? Google Analytics is a great, free utility from Google that will tell you just that and so much more. In this clip, the Web Guru will show you how to use this program, generate and install an HTML code onto your site so that you can keep track of your visitors and demographics. This is a fantastic tool for advertising purposes and so you can see which content is working best for you...

Got a seriously large number of business cards stashed in your basement due to ordering several boxes full only to have the company mess up on your phone number? Make use of these otherwise extraneous and superfluous cards by watching this video.

In this video tutorial, viewers learn how to create a FTP from a local computer to a website. In this video, viewers are shown (once you've chosen a web host) how to perform FTP file transfers from your local computer to your website. FTP (File Transfer Protocol) is a process that you can use to transfer files from your local computer to a remote computer (your website). Once you've set up a hosting account, your hosting company will provide you with FTP login credentials. Using an FTP softwa...

Companies spend millions on advertising every year, wouldn't it be great to get some of that money? Well you can. Adding ads to your personal blogs can really bring in revenue for an at home business, or just for yourself. This video will demonstrate and explain how to make money from your personal blog with ads.

What is better than a warm, fresh out of the oven blueberry muffin in the morning? Nothing! Check out this video and learn how to make your very own muffins for breakfast, snacks, or anytime! This tutorial, from FoodWishes.com will take you step by step through the process of making these gooey, warm muffins. So, the next time you have company or are in the mood for something delicious, check out this video and start cooking! Everyone will be impressed with these perfect little guys.

Sue McMahon, a food editor for Woman's Weekly, shows how to make a cottage loaf in this two-part video. To make this bread loaf you will need flour, salt, butter, fast action dried yeast, warm water, and one egg. Make this delicious bread loaf the next time you have company for a conversation starter!

After seeing many posts online about dry ice removing car dents, we put it to the test. It worked pretty well. The heat versus cold forces the panel of the car to constrict and suck out the dent. This is great for avoiding ridiculous costs of auto paint and auto body repair companies. DIY dent repair is as cheap as buying some dry ice. You can also look into using canned air (Dust Off) as it has a similar effect.

Belays enable climbers to stop fellow climbers during a fall. Therefore, belays are an essential safety device in climbing. Learn how to use belays in this climbing video tutorial. Take action: use a high friction rope device, have a large carabineer, communicate with partner, and consult your local outdoor store. Josh, the instructor in this how-to video from Live Strong, is an avid climber that resides off the coast in central California. He has managed for a mountaineering sports company f...

Preparing for a hike is easy with these tips. Get advice on backpacking, hiking, and the great outdoors in this video tutorial. Take action: use appropriate footwear, bring a first-aid kit, water, and food, and use walking sticks in uneven terrain. John Flaherty, the instructor in this how-to video from Live Strong, has a great love for the outdoors. In 2003, John and his wife started Central Coast Outdoors in northern California. His company provides hiking, kayaking, and biking services for...

Backpacking is easy with these tips. Get expert advice on backpacking, hiking, and the great outdoors in this video tutorial. Take action: keep weight off of shoulders, bring plenty of snacks and water, maintain healthy exercise, and consult a guidebook to determine an appropriate trail. John Flaherty, the instructor of this how-to video from Live Strong, has a great love for the outdoors. In 2003, John and his wife started Central Coast Outdoors in northern California. His company provides h...