The surging activity in augmented reality in both the business and consumer sectors is being matched with a wealth of updates and partnerships from Snap Inc.

After weeks of reports about their first augmented reality device, Apple actually shipped a real AR product this week in the form of a TV tie-in AR app.

The Super Bowl isn't just the most important NFL game of the year, it's also the biggest night for brands to bring their most creative advertisements to a vast television audience.

The year 2020 was a pivotal span of time during which the word "virtual" took on a brand new meaning. Instead of referring to VR or augmented reality, the term was hijacked to describe meeting across long distances through a variety of software tools, most often through video.

Quietly, while the rest of the world was engaged in pandemic and political concerns, a few weeks ago Facebook casually upgraded its Spark AR platform with what it calls Unified Effect Publishing.

When it comes to posting to social media from your smartphone, the process is typically the same. Find the app. Open the app. Tap the app's version of the compose button.

Penetration testing, or pentesting, is the process of probing a network or system by simulating an attack, which is used to find vulnerabilities that could be exploited by a malicious actor. The main goal of a pentest is to identify security holes and weaknesses so that the organization being tested can fix any potential issues. In a professional penetration test, there are six phases you should know.

Whether you miss the good old days of Telnet or you want to know what hacking was like when security was nothing but an afterthought, Telehack is the game for you. The text-based hacking game is a simulation of a stylized combination of ARPANET and Usenet, circa 1985 to 1990, with a full multi-user universe and player interactions, including 26,600 hosts.

When it comes to sniffing Wi-Fi, Wireshark is cross-platform and capable of capturing vast amounts of data. Making sense of that data is another task entirely. That's where Jupyter Notebook comes in. It can help analyze Wi-Fi packets and determine which networks a particular phone has connected to before, giving us insight into the identity of the owner.

It's safe to say that we can call the annual ranking of AR investments a holiday tradition at Next Reality.

The landscape of the augmented reality space is broad, diverse, and constantly shifting, perhaps more so than any other vertical in technology. At the same time, major players are attempting to standardize various hardware designs and delivery methods, while still others are rushing to claim their piece of virtual property through AR clouds and application stores.

Motorola is a shell of its former self. In 2010, it had just released the Motorola Droid, a phone so popular it led to all Android phones being called "Droids" by non-techies. But there have been some rough years between then and now, and Motorola's latest "flagship" doesn't look like it will help get them off this path.

Canary tokens are customizable tracking links useful for learning about who is clicking on a link and where it's being shared. Thanks to the way many apps fetch a URL preview for links shared in private chats, canary tokens can even phone home when someone checks a private chat without clicking the link. Canary tokens come in several useful types and can be used even through URL shorteners.

If you want to get started sniffing Wi-Fi networks, you usually need to start with a wireless network adapter. But thanks to a Wi-Fi sniffing library written in Arduino and the ultra-cheap ESP8266 chip, you might not need one. For less than $10 in electronics, you can build a tiny Arduino Wi-Fi sniffer that saves Wireshark-compatible PCAP files and fits anywhere.

The latest film addition in the American-produced Millennium series, The Girl in the Spider's Web, was just released on Blu-ray a few days ago. As you could expect, the movie has many hacking scenes throughout, just like the previous English and Swedish language movies centered around hacker Lisbeth Salander. Of course, with the quick pace of some scenes, the hacks can be hard to follow.

The gym can be pretty distracting. With the slamming of weights and pieces of equipment, loud music blasting through the speakers, and plain old grunting, it can be challenging to focus on your workout. However, with your just your phone, you can not only eliminate these distractions but make the most of your time there.

Mystery is a tricky thing. Used correctly, it can give onlookers the impression that wondrous and perhaps valuable things are afoot. However, once the veil of suspension of disbelief is removed in any significant way, that same mystery can quickly turn into not just skepticism, but outright anger at what may have seemed like an attempt to dupe trusting onlookers.

The newest version of macOS has arrived. While everyone's mind is being blown by Mojave's groundbreaking new Dark Mode, we'll be taking advantage of its insecure file permissions to establish a persistent backdoor with a self-destructing payload that leaves little evidence for forensics.

Russian cyber disinformation campaigns have many missions, but one of particular interest is using technology to monitor, influence, and disrupt online communications surrounding culturally sensitive topics or protests. The ability to watch these events, and even filter positive or negative tweets to amplify, gives rise to the ability to execute a number of disinformation campaigns.

The latest Star Wars movie, Solo: A Star Wars Story, has grossed almost $350 million worldwide during its first month in theaters. This is a good opportunity to discuss how hackers can use media hype (in this case, Hollywood movie hype) to disarm an unsuspecting Windows user into inserting an evil USB stick into their computer.

There has been significant debate over law enforcement's right to access our digital devices in recent years. New tools from Grayshift and Cellebrite are popping up faster than ever to help government agencies, as well as traditional hackers, break into iPhones. If you're concerned, you can take steps right now to beef up your passcode and prevent outsiders from gaining access to your device.

Smartphones are like high tech buckets that collect our personal information through constant use. This has some obvious benefits, like getting a more personalized experience with our devices. On the other hand, this data is a tempting target for bad actors looking to make a buck at the expense of your privacy.

While iOS 11.3 doesn't have as many new features as iOS 11.2, there's still a lot to love about Apple's latest update for iPad, iPhone, and iPod touch, even if some of the best features we were expecting didn't make the cut.

For almost a decade, projector phones have tried to entice consumers with their convenience as media machines. While these devices are alluring, they've never really taken off with mainstream success. The latest effort, Moviphone, sounds tempting if you watch a lot of films and TV on your smartphone, but is it good enough to be your daily driver?

Wonder Woman has always been a Halloween and cosplay staple. It's a costume that's both dependable and stylish — just like the Amazon who wears it. This year's reprise with Gal Gadot offers a fresh take on the old standby, with more muted colors, a tougher demeanor, and a decided lack of stars or stripes. Tahnee Harrison from CineFix's DIY Costume Squad has come up with a compromise between the old and new costumes. It's got the cut, styling, and details of Gal Gadot's 2017 costume, but the b...

When hacking into a network during a penetration test, it can sometimes be useful to create your own wireless AP simply by plugging a Pi into an available Ethernet port. With this setup, you have your own backdoor wireless connection to the network in a matter of seconds. Creating an AP is also helpful while traveling, or needing to share a connection with a group of people.

Kali Linux is the obvious first choice of an operating system for most new hackers, coming bundled with a curated collection of tools organized into easy-to-navigate menus and a live boot option that is very newbie-friendly. But Kali isn't the only distribution targeted at pentesters, and many exciting alternatives may better fit your use-case. We've already covered BlackArch Linux, now it's time to talk about Parrot Security OS.

On April 7, 2017, residents in Dallas, Texas, woke to the sound of emergency sirens blaring all over the city. No one could shut them off, and after repeated efforts to contain the situation, the city had to shut down the entire system. While the media reported a sophisticated computer hack was responsible, the truth was much less high-tech.

A new technological movement without the technology itself is just an idea sitting and waiting. Once the technology is present in the equation, movement forward can begin. This is how many of us see the head-mounted displays (HMDs) and smartglasses that have recently entered the augmented and mixed reality market — or are coming out in the next few months. This is a movement that will sweep over the world, changing everything in its path, and these are some of the people behind it.

Most of us skip through documents like privacy policies and EULAs (end-user license agreements) because they're long and boring. But, as Congress just passed the SJR34 bill in early April, you're probably a little concerned about your personal data, so we summarized the privacy policies for major ISPs and mobile carriers in the US.

Right now is that magical time of year when the general public decides to embrace their inner fattie and get baking in the kitchen. Hello, pies and cakes and cookies and everything carbs. Goodbye, diets—see you in the next year, when you cripple us with unbridled guilt and longing.

Black Mirror, Netflix's technology-horror anthology, never fails to provide thought-provoking entertainment centered around emerging and futuristic technologies, and the third season's second episode, "Playtest," delves deep into the worlds of mixed, augmented, and virtual reality. While designed to leave you haunted by the end, offering a more "evil" narrative than we'll likely see in our actual future, the episode explores possibilities that aren't as far off as one might think.

If maintaining privacy is an ongoing battle, the front line is your smartphone. Apple included several new security features in iOS 10, but at the same time, some of the best new functionality comes with potential privacy trade-offs that everyone needs to understand.

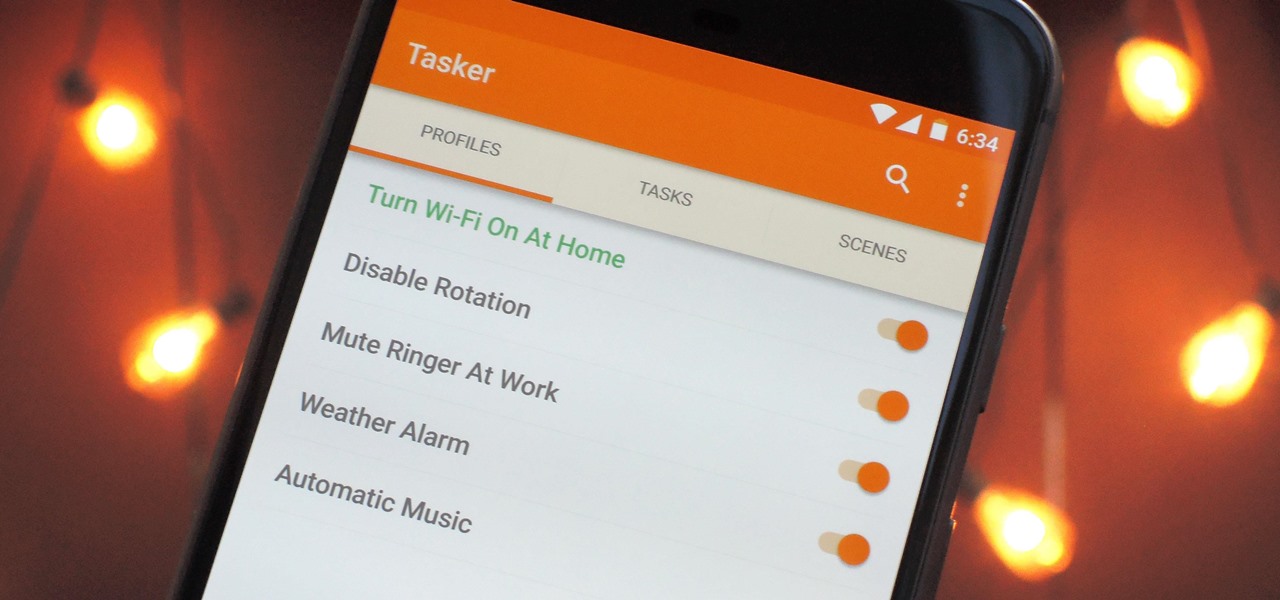
When it comes to automation apps on Android, Tasker is still the king of the hill. For a price of $2.99 on the Google Play Store, it's a great buy for any would-be tinkerer that would like to get into automating actions on their Android device. Then, when you consider that there's a free 7-day trial version available, there's almost no reason that you shouldn't at least test the waters with Tasker.

Apple's latest mobile operating system, iOS 9, may not be the huge overhaul that iOS 8 was, but that doesn't mean there aren't plenty of new features. In fact, there are a ton of subtle changes that you may not notice right away. Here's a rundown of all the coolest new features you need to know about on the new iOS 9 for iPad, iPhone, and iPod touch.
Hello and welcome to my article. I have made this article for anyone who wants to become a hacker, and wants to know how to get started.

Apple just announced the iPhone 6, and no matter whether you've been with Android for a few months or few years, there's a good chance you're enticed by the idea of switching over to the other side.

It's super easy to add filters, adjust levels, and crop images using the default photo editor on your smartphone, but there's rarely any built-in tool for removing the background in a photo. A third-party app can help isolate people and objects in your pictures, and we've found a free one that's easy to use, works with high-resolution images, and is available for Android, iOS, iPadOS, and the web.

The year leading into fall is turning out to be packed with a flurry of augmented reality activity. Most notably, TikTok is adding another major weapon to its AR arsenal. Also on deck are the powers of Hollywood horror in the form of an innovative approach to AR marketing that uses sounds.

Facebook's earnings calls are generally focused on numbers—revenue and user growth. But this week the company's founder and CEO, Mark Zuckerberg, carved out a significant portion of the call to elaborate on Facebook's plans for immersive computing.