Incorporating features such as CarPlay, UI enhancements such as the new call screen, and several bug fixes, iOS 7.1 was the first major update to Apple's operating system since iOS 7 was released in June of last year.

Update: April 24, 2014 Looks the the one day availability was a precursor to a wider launch, as now anyone can buy a pair of the Glass Explorer Edition without needing an invite. Check out Google's Glass Shop for some easy ordering, still with the $1500 price tag.
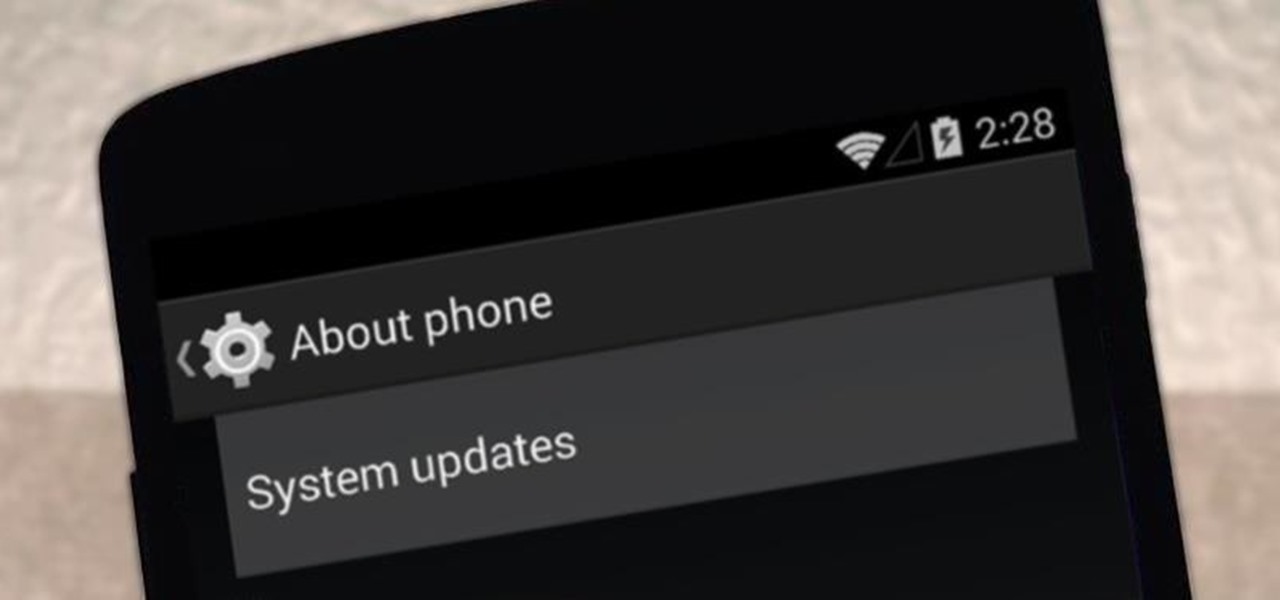
It appears that the next iteration of KitKat, Android 4.4.3, is fast approaching. If the past is any indication, today's update to the Nexus 5 software changelog on Sprint's website tells us a new version of Android will begin rolling out within 24 hours. Sprint has broken the news of a forthcoming Android release twice in the past. With 4.4.1 and 4.4.2, a mini-changelog was posted on the Sprint website about a day before Google began pushing updates to its Nexus devices.

If you've ever noticed, even just for a fleeting moment, that the auto brightness on your Nexus 5 seemed to "glitch out"—you are not alone.
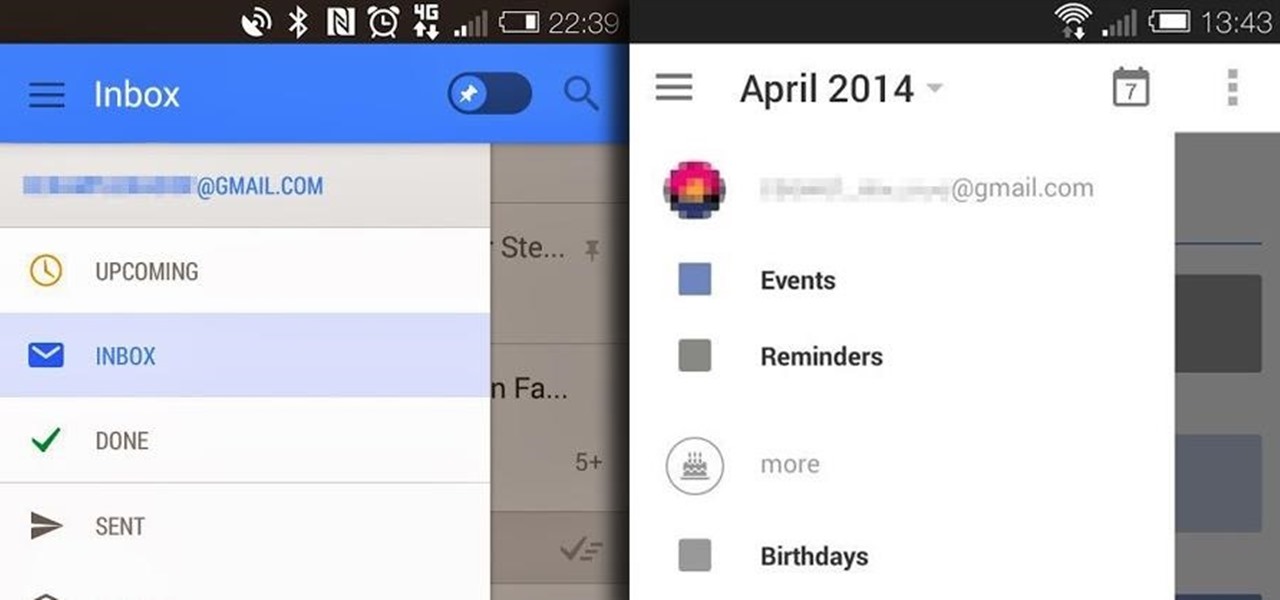
Google I/O may still be a couple of months away, and although we don't expect anything groundbreaking—no new Android versions, just fixes to KitKat—we could be treated to some new apps. No, not Pokémon inspired Maps, rather new versions of Google's Calendar and Gmail apps.

Google released its long-awaited Google Now launcher a couple months ago, allowing users to access Google Now with the simple command of the voice. As great as the feature is, it requires that our screens be on, unlike the Moto X's "active listening" service that operates with Google Now, activating through a screen-off state.

The old "my battery is dead" excuse for not calling your mother may soon be a thing of the past. A team from the Korea Advanced Institute of Science and Technology (KAIST), led by Professor Jo Byeong-jin, has developed a "wearable thermo-element" that can be built into clothing to power your electronic devices. The science behind the innovation converts body heat (thermal energy) into usable electric energy. Made with lightweight glass fiber, this small thermo-element strip can produce about ...

I've already shown you an easy last-minute prank involving toothpaste-filled Oreos, now here's a great joke involving an integral part of the cookie-eating experience—milk.

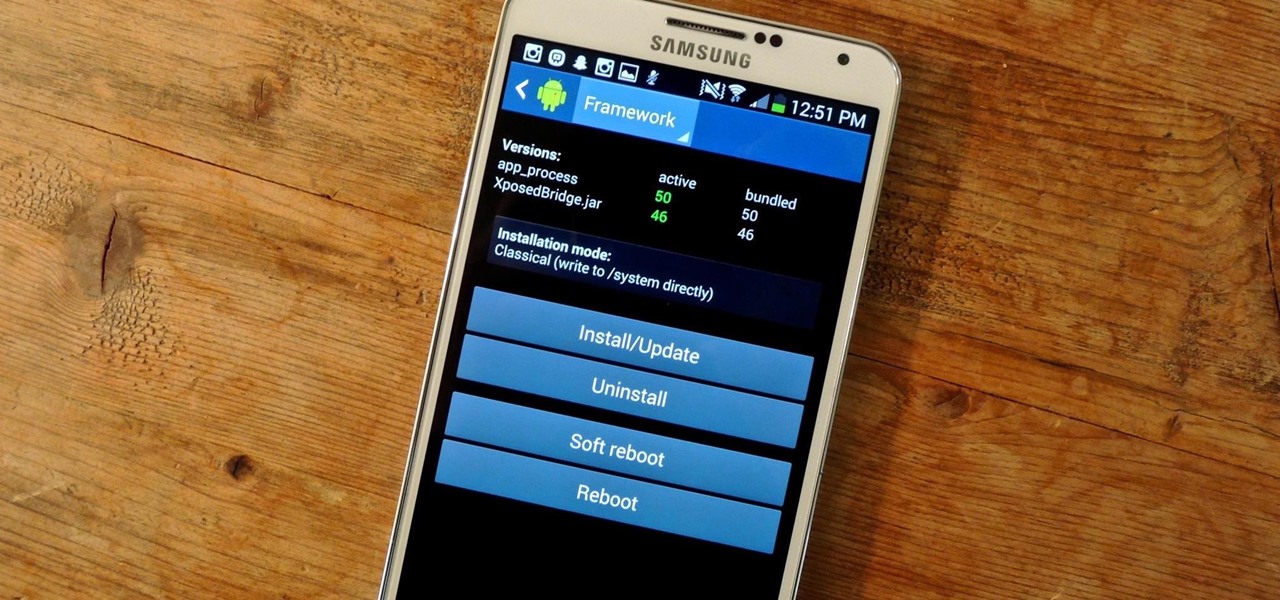
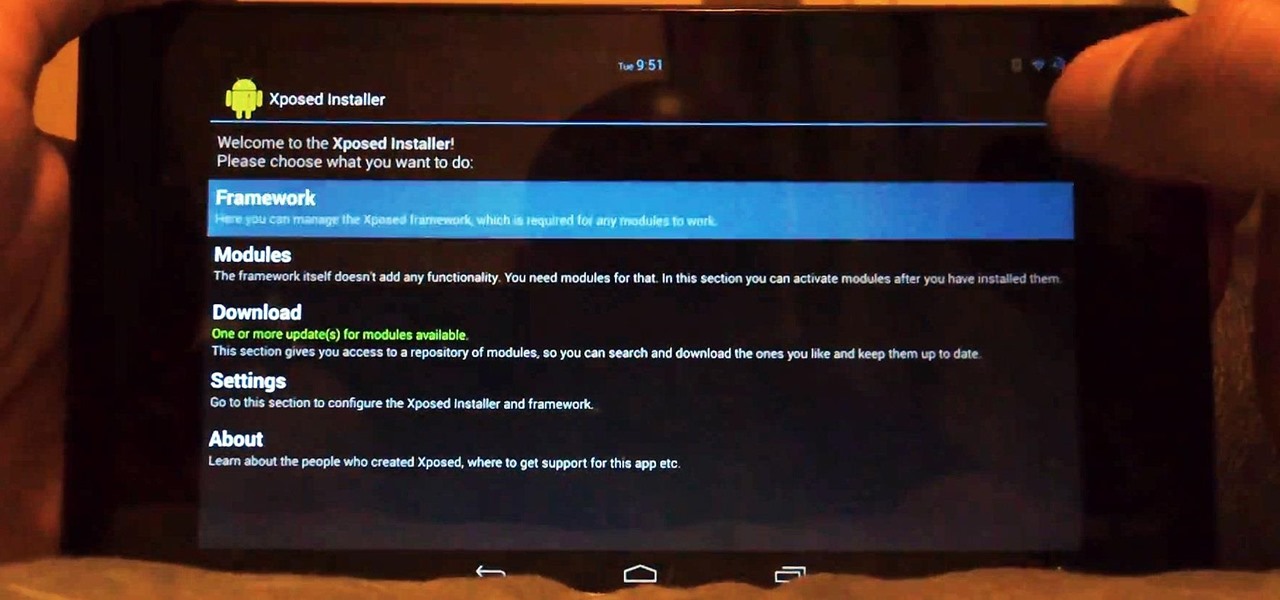
Allowing us to easily get features that would otherwise be available only through flashing mods and custom ROMs, Xposed Installer has been a godsend since its development, simplifying the sometimes tasking and potentially harmful process of changing the core components of Android's operating system.

The ability to see the world around you and instantly share that "vision" is something that makes Google Glass great for everyday use. No reason to pull out your phone to show off the amazing sushi plate you were just served—look at it, give a couple of quick taps and voice commands, and boom, your social network is salivating in jealousy.

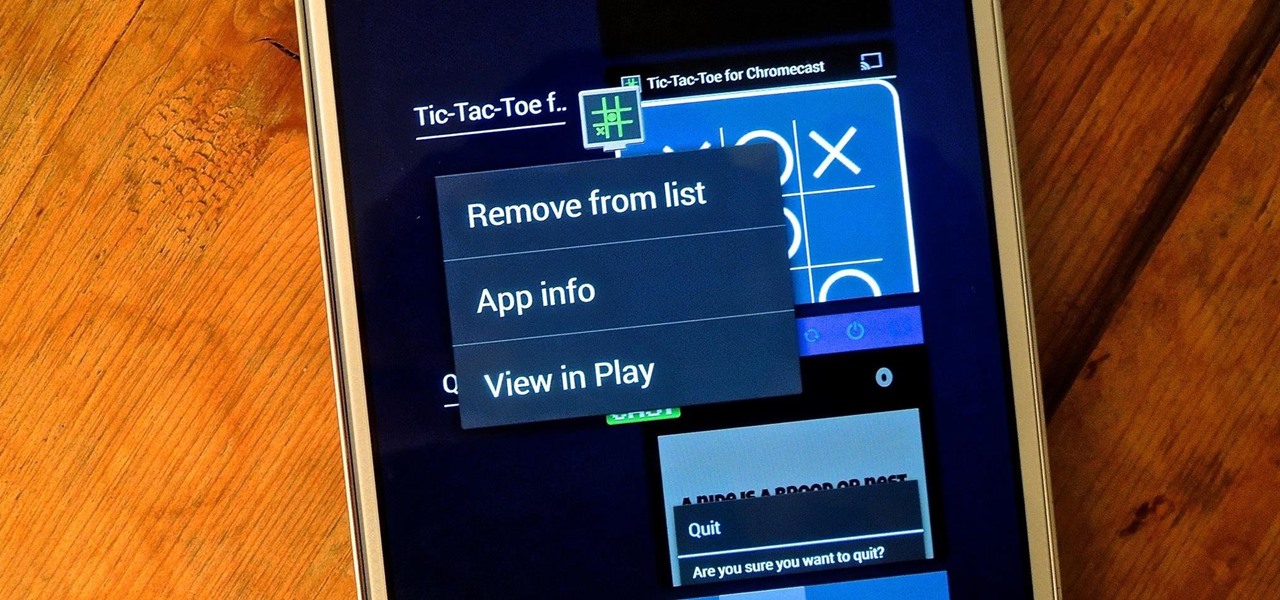
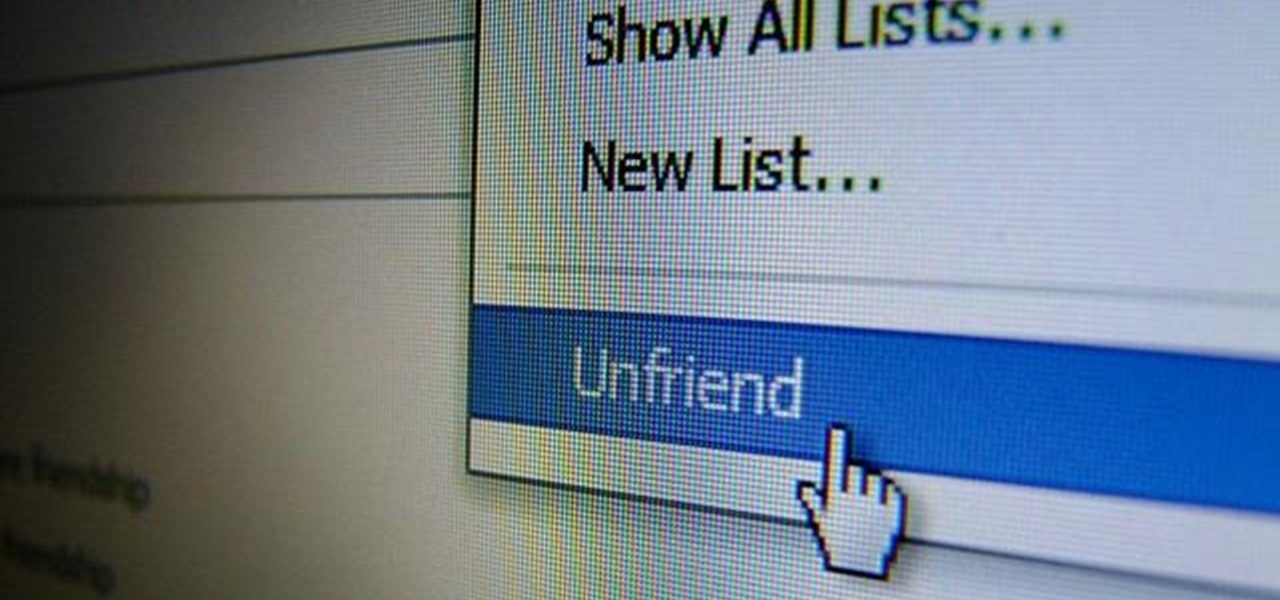
On more than one occasion, I've wanted to check out the Google Play page for an app I was currently using, whether it was to get contact information or read recent reviews to see if others were experiencing issues that I was.

Applying for jobs can be a truly miserable experience. Sending out endless résumés, filling out those janky online applications, and creating cover letters can really wear a person down. So, any suggestions that make that process easier are always welcome.

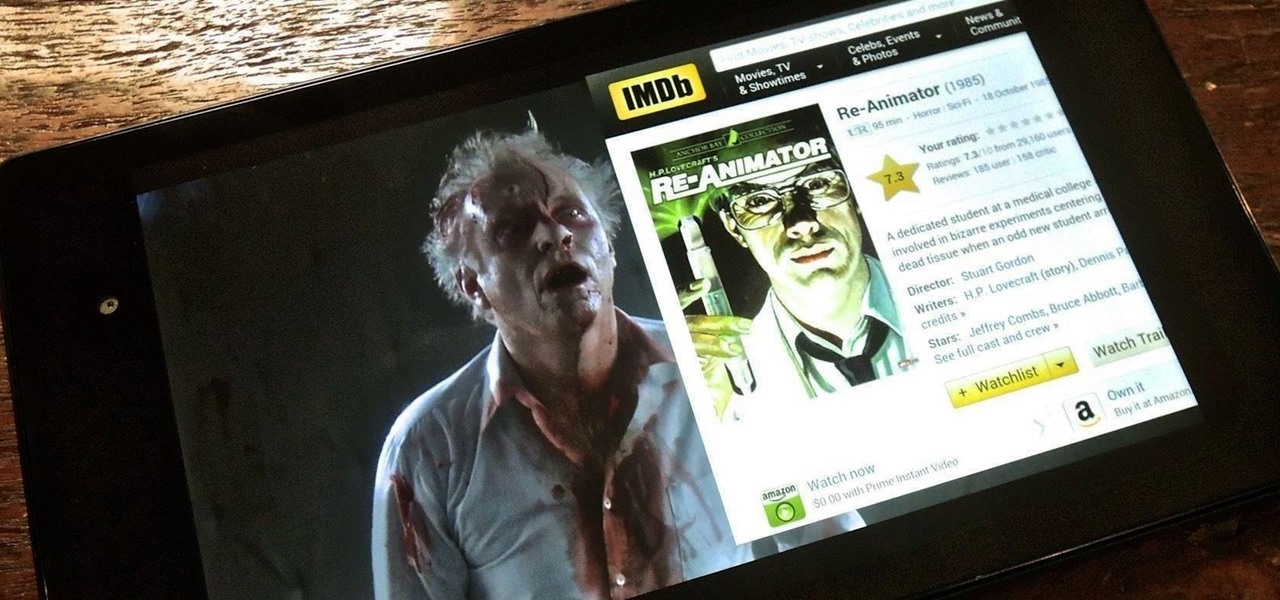
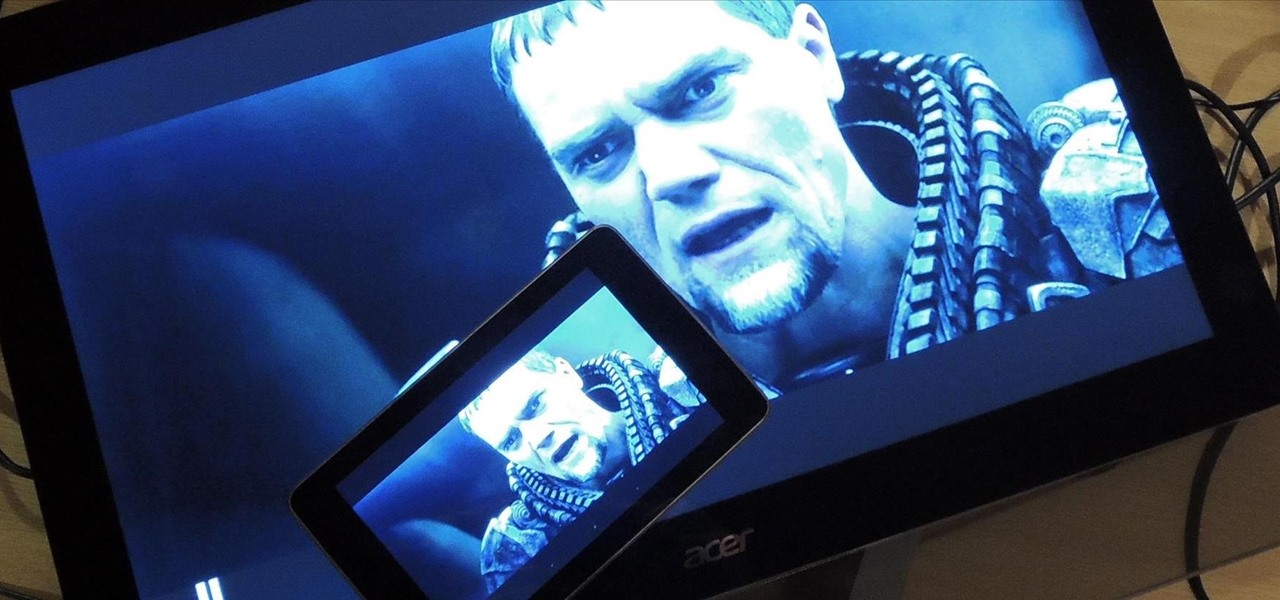
Efficiency is one integral attribute that I need from my Android device. I want to be able to multitask like a maniac and do things on the fly. While multitasking itself is nothing new, actually being able to watch Netflix while scrolling through IMDB at the same damn time was reserved mainly for newer Samsung-ier devices.

Leaving your Wi-Fi radio "on" allows your smartphone to auto-connect to trusted wireless networks in lieu of using cellular data, but it also consumes battery power while it's constantly network hunting.

Apple hates game emulators. Go ahead, look around in the iOS App Store, you won't find any. But who needs 'em anyway?

Facebook makes it easy to show how much you appreciate a funny status, great picture, or cool news article using their iconic "thumbs up" button, but what about those terrible jokes and annoying baby pictures? Where's the "thumbs down" for that crap?

There's one reason why most of us have a Samsung Galaxy S3—because we don't want an iPhone. Yes, there are some pretty cool things about the iPhone aesthetically, but looks aren't everything. Anyway, with the nearly unlimited customizations options we have available for Android, cloning the iPhone-look is no problem—even the lock screen.

It's always the snack you're most looking forward to that ends up being moldy when you open the fridge to grab it. Always. That slice of leftover pizza or chunk of cheese you've been thinking about all day? We've all been there. What separates us is how we choose to deal with it. Personally, I toss anything that has even the slightest hint of mold, but not everyone errs on the side of caution. Some people don't mind the risk and just cut off the green or fuzzy parts and eat the rest.

It's been a great week for Chromecast owners. First, Google released the development kit, allowing devs to install the casting code into their apps. Then, CyanogenMod dev Koush updated his AllCast app to support the Chromecast. That means you can shoot personal movies, music, and photos directly from your Android device over to a Chromecast-connected display.

Presentational video for our DIY Camera Crane project. Video: .

Texting something as simple as "What up, bruh?" can be transformed into something way more baller by adding emojis, emoticons, GIFs, and textspeak. Some people would even argue that texting is a form of art, similar to Shakespearean sonnets, but it still has a ways to go if you ask me.

While browsing the internet on your Samsung Galaxy S4, you've probably scrolled to the bottom of a very long webpage, Twitter feed, or down into the abyss of some other app. Depending just how far down you've scrolled, it can be a test of your patience (and fingertips) scrolling back up to the top.

Are you tired of your snoopy coworkers and friends lingering over your shoulder as you type in your security passcode? Unless you have the newer iPhone 5S with Touch ID that scans your fingerprint, you've only got a couple of security options—either a 4-digit numeric passcode or a cumbersome password.

When we take pictures with our smartphones, it’s safe to assume we’re taking more than one. We're either trying to capture the right light, look, or expression… or maybe a slight nod to the right to show off your good side.

You don't have to be Drake to realize that some friends are better than others. There are friends you know are only there for the party, and friends who actually listen when you whine about your life. There are friends you go out with for a beer, and friends you call when you're drunk and need a lift at 4am.

Introducing a unique way to share photos and videos among friends and family, Snapchat was the big hit of 2013 (despite its many flaws). Thanks to its ephemeral nature and lack of third-party sign-in integration, it quickly grew into a multibillion-dollar company in the span of just 12 months.

We will show you with easy step by step instruction how to create a beautiful edible apple swan. This swan is easy to create and can be done in under 5m. Makes for a great centre piece during a special dinner.

The next generation gaming systems are so close to release I can almost taste the plastic. The new PlayStation 4 is set to be released in just a couple days on Friday, November 15th, but if you're like me, there's only one thing preventing you from upgrading in a second.

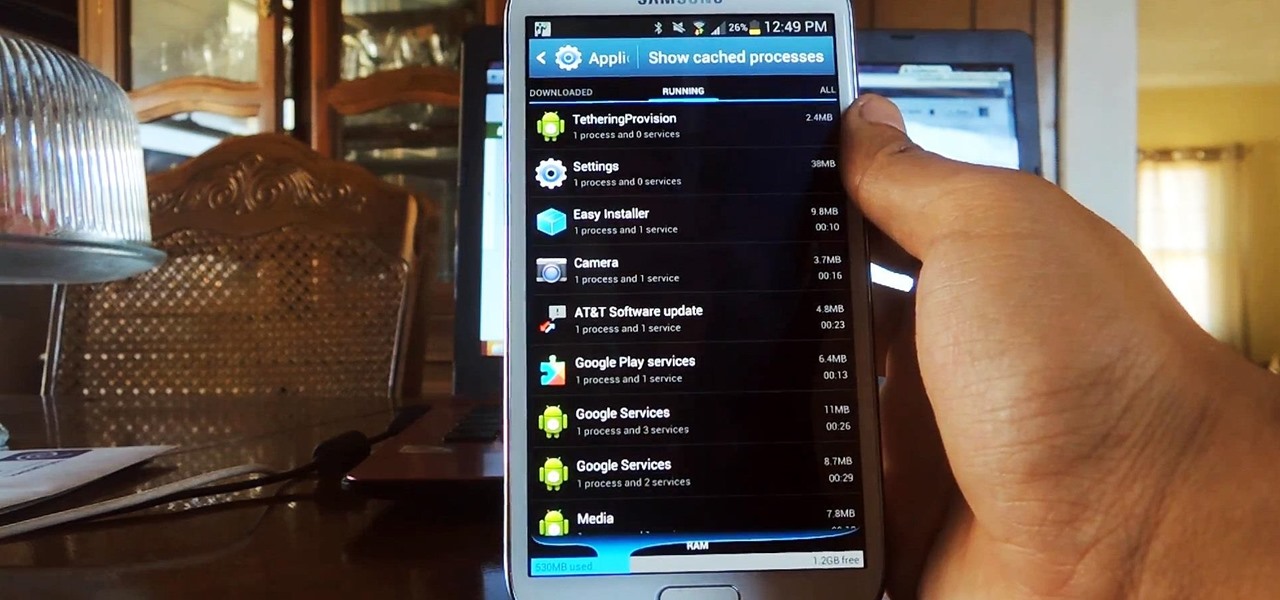
A certain selection of applications on your Android device (both system and downloaded) start running as soon as your Samsung Galaxy Note 2 turns on, laboriously hammering away at whatever tasks they have to do.

For now, the redesigned and fresh-faced Android 4.4 KitKat is exclusive to the new Nexus 5, though it will be rolling out to other Google (Nexus 4, Nexus 7, Nexus 10) and Google Play Editions (Samsung Galaxy S4, HTC One) devices in the next week or two.

Customization of our Android devices, outside of what Google and mobile carriers allow us to do, used to mandate that our devices were rooted and running a custom ROM.

I read, walk, and do lunges all at once. Time is money, and I'm all for multitasking whenever I can. Thankfully, my Samsung Galaxy S3 is extremely good at it, but extremely good could still be extremely better.

You don't need to be a robot to be overly concerned with battery life, especially if we're talking about Terminators, which have nuclear or hydrogen fuel cells that keep them running for years straight. It will be a long time before smartphones get that upgrade, so in the meantime, we have to figure out how to make them last more than a couple hours in a single charge.

A lot of people hate chopping onions, and understandably so. Their shape and layers make them difficult to handle if you don't have much practice, and even if you know exactly what you're doing, it's a task that usually ends in tears.

Back when I was a kid, I didn't get many awards or trophies, aside from perfect attendance three years in a row. If only there was an award for procrastination. While there are apps out there for my iPhone like Clear and even the stock Reminders app, they still don't push me hard enough to get things done on time—or at all.

While there's still no set date, Jelly Bean 4.3 is rumored to be released on the Samsung Galaxy S4 and other TouchWiz devices within the next couple of weeks (or months), presumably sometime after the upcoming Samsung Unpacked event.

Welcome back, my fledgling hackers! One of the first issues any hacker has to address is reconnaissance. Before we even begin to hack, we need to know quite a bit about the target systems. We should know their IP address, what ports are open, what services are running, and what operating system the target is using. Only after gathering this information can we begin to plan our attack. Most hackers spend far more time doing reconnaissance than exploiting.

The new Moto X is still a couple of weeks from being released here in the United States, but that doesn't mean we can't play around with a few of its cool features.

We use ADB and Fastboot for so many things in our softModder tutorials, and to get them, you normally have to download the entire Android SDK and install them. But not anymore.

Due to its enormously awesome size, the Samsung Galaxy Note 2 usually takes two hands to maneuver through photos and texts, write emails, and get directions on the map.