You may not have thought of dorks as powerful, but with the right dorks, you can hack devices just by Googling the password to log in. Because Google is fantastic at indexing everything connected to the internet, it's possible to find files that are exposed accidentally and contain critical information for anyone to see.

The next libSSH or OpenSSH exploit may be just around the corner. Keep your SSH service out of Shodan's database before hackers find new ways to bypass the password protecting the server.

In the world of technology, there's often a trade-off between convenience and security. The Java Remote Method Invocation is a system where that trade-off is all too real. The ability for a program written in Java to communicate with another program remotely can greatly extend the usability of an app, but it can also open up critical vulnerabilities that allow it to be compromised by an attacker.

Welcome back, my aspiring hackers! In previous tutorials, I have shown you how to scan the globe for vulnerable servers and write simple scripts in BASH and Perl to perform other reconnaissance tasks. In a very recent guide, I taught how to scan vulnerable servers for Heartbleed.

The Motorola Droid is getting a little long in the tooth, but it is still a remarkably capable phone with full keyboard, which makes it almost unique among it's Android-based competition. If you've rooted your phone (good for you!) and for some reason want to go back to the stock configuration that your phone was in when you took it out of the box, this video will show you how to do it. One good reason is if you want to update your phone's firmware, which will not work if you phone is rooted ...

Other World Computing provides a guide for advanced users demonstrating the upgrade or replacement of a hard drive in a Mac Mini Server computer. This comprehensive video takes you through all steps from tool selection to re-assembling the Mac Mini Server and it is recommended that the video is watched right through before attempting the procedure. In particular, it demonstrates the difficulty of opening up a Mac Mini using a small putty knife. Once the case is off, the three wireless antenna...

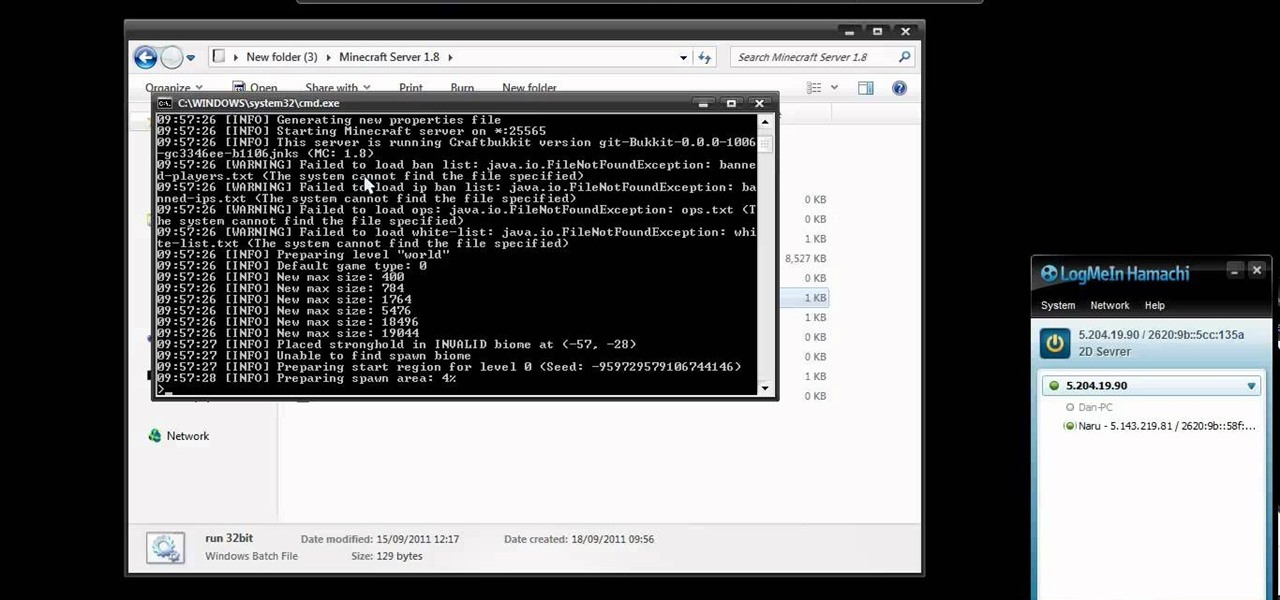
If you're looking to run a Minecraft 1.8 server using Logmein's Hamachi product, take a look at this guide on how to set one up. Hamachi is a great way to run a Minecraft 1.8 server for cheap.

This five-part series on C# programming covers many things. First, you learn how to save to the Microsoft SQL Server. Then, you'll learn how to retrieve that data. You'll also learn how to navigate the DataSet, edit SQL data, and delete data. If you have Microsoft Visual Studio and SQL Server, give this lesson a try.

Whether it's a small business or a work group inside a large corporation, all members need access to the same materials in order to work effectively. Mac OS X server makes it easy for groups to collaborate and communicate through their own Wiki-powered Internet website. To learn how to use Wiki Server with Mac OS X Server, watch this video tutorial.

Learn about assigning static IP addresses to a Windows 2003 server - a good idea if your server is constantly changing its IP address because of your DCHP server.

How to Use COD4 Cracked Servers.

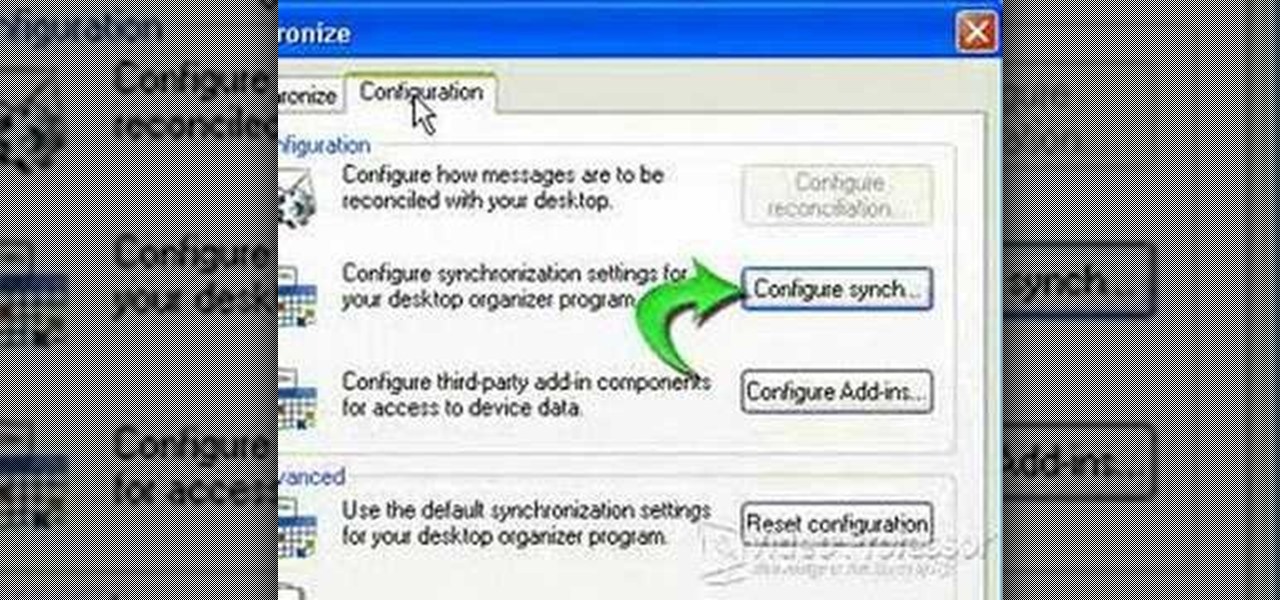
This video shows how to synchronize our blackberry smartphone with MS outlook. First open up the Blackberry Desktop Manager. Let us start by synchronizing the blackberry. Double click the synchronize button to load the synchronization settings. Here we can specify what we want to synch and where we want to synch firm. Click the configuration tab and select configure synch. Our device configuration menu let us pick which application on the black berry to synch and where to synch. Today we are ...

This video will show you how to set up a Garry's Mod server and allow others to access it. In order to get your Garry's Mod server public, you need to ensure that your router is properly configured to allow Garry's Mod ports.

How to Use Your Mac as a Server: Turn your Mac Mini into a server! Yes, that's right, with a little know-how and a little spunk, you can turn an inexpensive Mac Mini computer into a server to provide services over you network. You won't even need the Mac OS X Server, just the Mac OS X Client, so there is no extra software to buy, just the Mac Mini and it's operating system.

Whether it's a small business or a work group inside a large corporation, all members need access to the same materials in order to work effectively. Mac OS X server makes it easy for groups to collaborate and communicate through their own Wiki-powered Internet website. In this video tutorial, you'll learn how to adminster the Wiki server in Leopard Server in Mac OS X.

Mac OS X server includes a calendar server for users and groups to coordinate events, schedule meetings, reserve resources and use time more effectively. To get started using iCal Server on your own Mac OS X Server, watch this video tutorial.

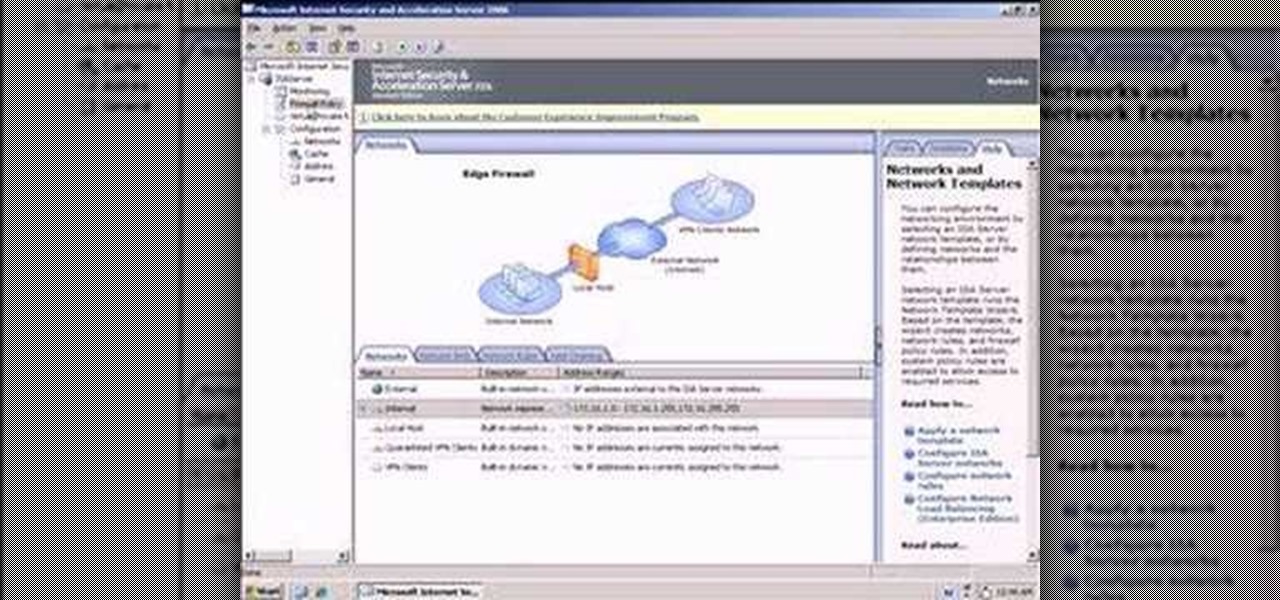
During the installation of ISA Server 2006 you were given relatively few options for configuring ISA Server therefore it is important to understand how to use the ISA Server Management tool. This video helps you understand the 'big picture' of ISA Server management.

So what exactly is ISA Server? ISA Server, which stands for Internet Security and Acceleration Server, is Microsoft's software-based firewall, proxy, and web caching service/product. Now what does all of that mean? This video helps explain it!

A hacker with privileged access to a Windows 10 computer can configure it to act as a web proxy, which allows the attacker to target devices and services on the network through the compromised computer. The probes and attacks appear to originate from the Windows 10 computer, making it difficult to detect the attacker's actual location.

Tor is an excellent obfuscation network for web traffic, and while instant messaging over the network is very useful, it can be relatively difficult to configure. In this guide, we'll look at two synchronous communications platforms (instant messengers) which can be routed over the Tor network, Ricochet and XMPP.

Hacking from a host machine without any form of proxying is reckless for a hacker, and in a penetration test, could lead to an important IP address becoming quickly blacklisted by the target. By routing all traffic over Tor and reducing the threat of malicious entrance and exit nodes with a VPN, we can configure Kali to become thoroughly private and anonymous.

SSH local forwarding is a must for covering your tracks and getting out there to do your work. Also called SSH tunneling, this process will put one or more steps between your machine and the machine you're working on, for security and other purposes. It can be a bit daunting for newbies to get down, and that's where Punchabunch comes in.

Welcome back, my hacker novitiates! If you have been following this new Snort series, you know that Snort is the world's most widely used intrusion detection/protection system. Now a part of the world's largest network equipment company, Cisco, it is likely to be found everywhere in one form or another. This makes a compelling argument for learning how to use it, as it will likely be a necessity in any security-related position.

Want to play multiplayer Terraria? You need to set up a server. This video will show you how to set up a multiplayer server without using Hamachi. This is the easiest, most foolproof way to set up a Terraria server.

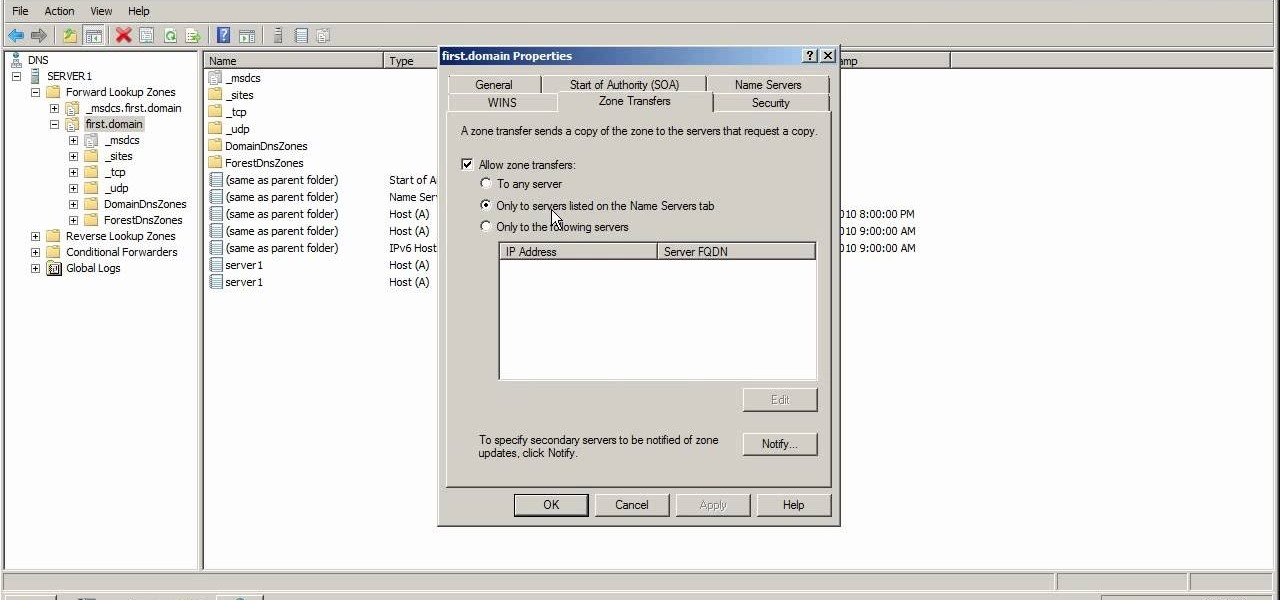
If you ever use NS lookup in Microsoft Windows Server 2008, you have to permit the machine running it to accept zone transfers. To do so, follow the instructions in this video. This video will show you how to use the name servers tab in DNS to allow machines to receive DNS lookups.

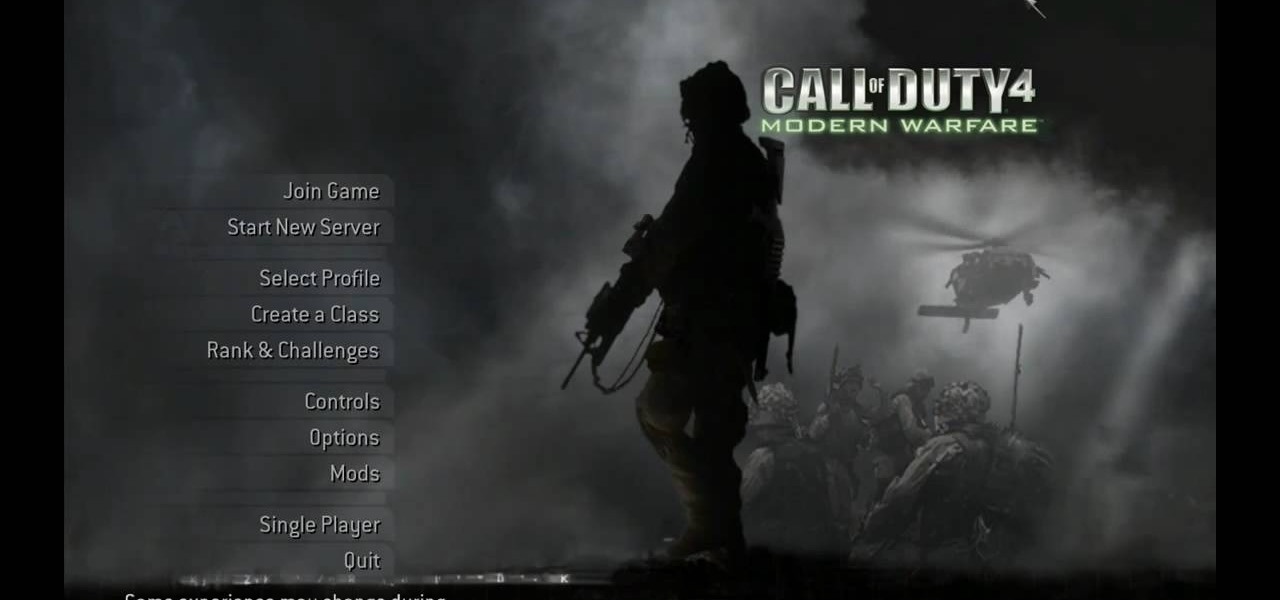
In this tutorial, we learn how to make a Call of Duty 4 working server. First, go into your game and go to "start new server". Next, name it whatever you want and put internet into the dedicated section. After this, save the information and a console will pop up. Don't close this, minimize it. Next, open up your game and go to "join game" and search for your server. When you find it, click on the information and write down the IP address it has inside of it. Now, go to XFire and type in the I...

This how to video shows you how to configure Microsoft Outlook 2003 to access an exchange server. This is useful if you want to use the program with an exchange server and do not know how. First, open up Microsoft Outlook 2003 on your computer. On startup, click next and yes. Select Microsoft Exchange server and click next. Uncheck use cached exchange mode and enter the server name. Enter your user name in the correct form and click check name. It will not be filled in. Click next and then se...

Remote Server is a very handy tool for users wishing to utilize OnTime Windows and OnTime VS.Net without having direct access to SQL Server. This installment from Axosoft's own series of video tutorials on the OnTime Project Management Suite covers Remote Server in detail and how to set it up. Take a look.

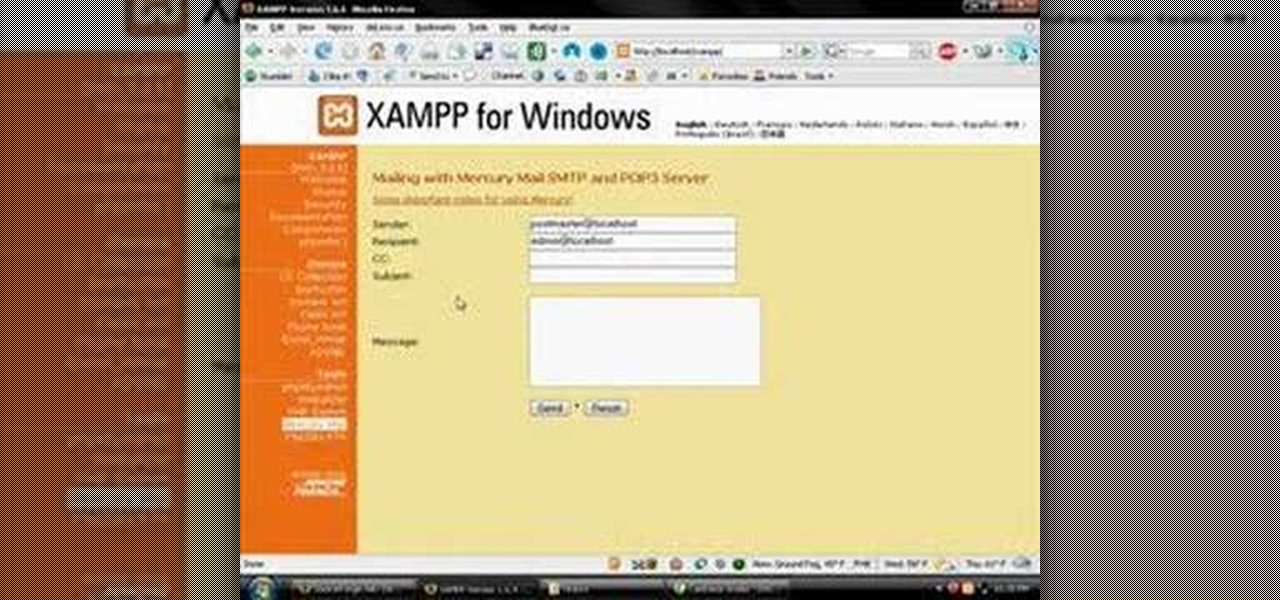
XAMPP servers are a free open source server that makes it cheap and easy for you to test and review your website building as you go. This tutorial covers how to configure your XAMPP server for windows.

If you have a website or do any type of web development you have probably needed a server at some point. Not everybody has a full blown commercial web server at their disposal for development, experimenting, and testing their site, so try this solution: an XAMPP open source bundled server.

A custom application directory partition is a method of dividing your DNS servers for replication, and allows replication to occur between domain controllers. This video shows you the process of setting up your own using Windows Server 2008, though it will also work for the 2003 version as well.

How to Use Your Mac as a Server: Turn your Mac Mini into a server! Yes, that's right, with a little know-how and a little spunk, you can turn an inexpensive Mac Mini computer into a server to provide services over you network. You won't even need the Mac OS X Server, just the Mac OS X Client, so there is no extra software to buy, just the Mac Mini and it's operating system.

As with any media asset management system, your catalog of assets will keep growing. As your storage fills up, Final Cut Server makes the task of archiving and restoring simple. Final Cut Server sets up your storage system into online and archive systems.

Do you have an old PC sitting around somewhere in your garage? Want a dedicated audio server that will play back MP3s, Internet radio, and other digital music files over your home stereo system? This CNET video teaches you how to convert your old PC into an amazing server!

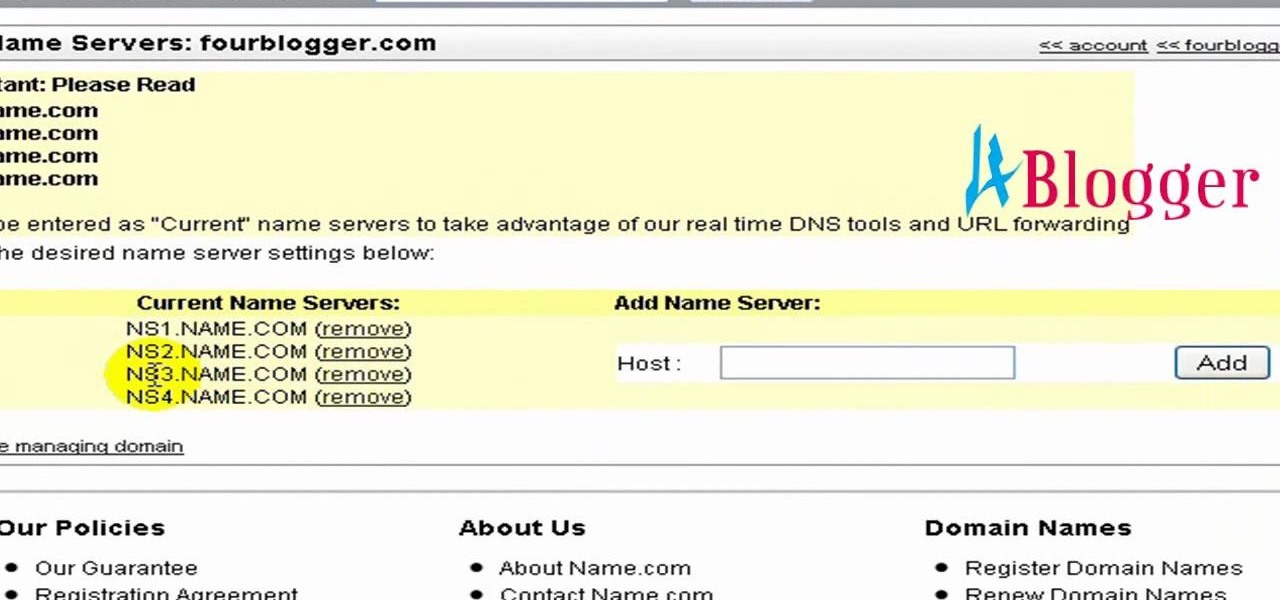
Edit name servers in the domain management area. If you're buying domain and web hosting from a single provider, like Hostgator, then the domain name automatically has a corresponding host.

Turn your American Apparel Le Sac dress into a cute Gathered Mini. It's a fun look and really easy to accomplish. The Le Sac dress has at least TWELVE different configurations for you to enjoy, which means more closet space, and less laundry! It can be a totally new dress each day of the week. Follow along and get this easy, sexy style that's perfect for summertime.

A wire mandala is basically a wire halo of sorts, meant as a geometric configuration which contains the image of a deity. For some, a wire mandala can be used for meditation and stress relief, while for others it is a beautiful religious pendant that can be attached to earring clasps and chains to make necklaces.

Watch this cinematography tutorial on how to use the microShouldermount, which can be attached onto a tripod or used in its typical configuration as a shoulder mount. You can attach a monitor along the grip rod. Learn the essentials of the Redrock mounting systems for professional digital video cameras. Interesting tutorial for professional cameramen & digital filmmakers.

Kevin Rose is joined by John Todd, a well known, leading Asterisk expert, to introduce you to the amazing VoIP (Voice over IP) world of Asterisk, the open source voip telephony toolkit. In this episode, Kevin and John take you through the installation and configuration of this powerful tool, and show how it can be used to give anyone complete control over their phone experiences, such as voice over wifi, eliminating phone costs, choosing from hundreds of VoIP providers, creating your own voic...

Imagine for a moment that a VPN is like putting on a disguise for your computer. This disguise works to change your IP address, secure your traffic with encryption, and mask your location to bypass regional restrictions. This makes it a helpful tool for both whistleblowers and journalists. VPNs are also built into the well-known Tor Browser.