
News: Minecraft BronzeSMP Server Ep 1!
Hey guys, today I bring you the fabulous BronzeSMP Server series! I hope you guys will enjoy this video as much as I enjoyed making it!


Hey guys, today I bring you the fabulous BronzeSMP Server series! I hope you guys will enjoy this video as much as I enjoyed making it!

Welcome back, my rookie hackers! Most often, the professional hacker is seeking protected information from the target system or network. This might be credit card numbers, personally identifiable information, or intellectual property (formulas, plans, blueprints, designs, etc.). Most of my Null Byte guides have been focused on getting into the system, but this only begs the question—"what do I do when I get there?"
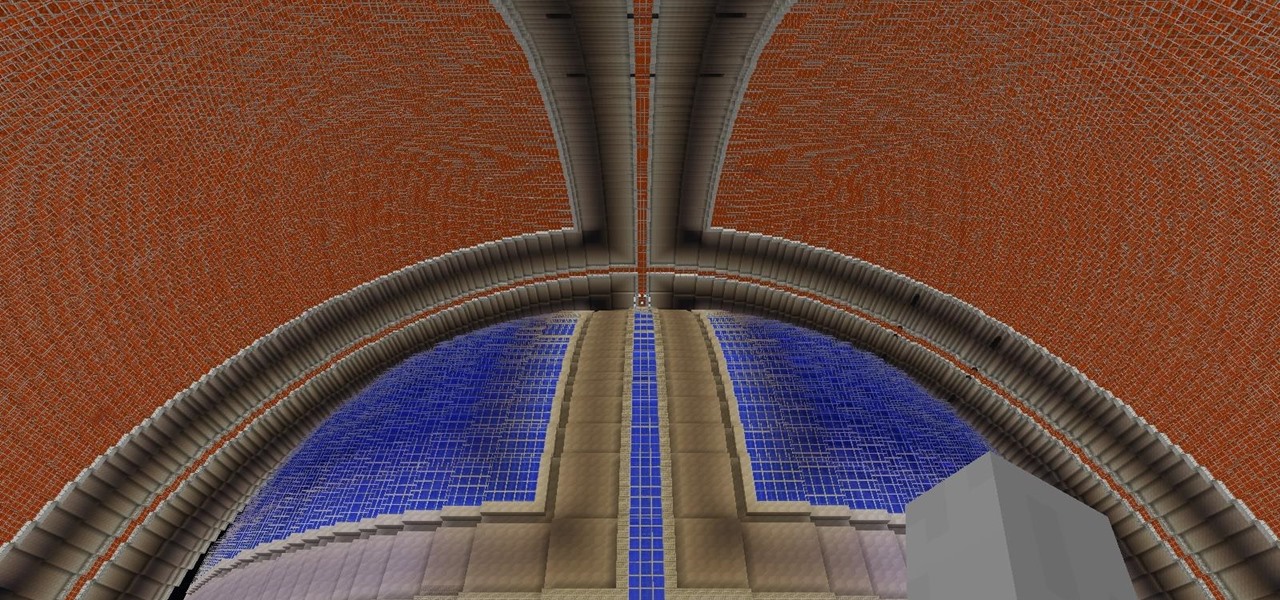
Still working on mega project builds. This one is going into my own PVP server which (will) contain 4 theme'd biomes inside of a 155m sphere - inside of a 255 meter containment sphere inside a 1000m+ void. The outer sphere acts as both artificial sunlight and a drop-death height of 50m. 4 more outer panels to go (water and lava) and it's ready for interior work and redstone - including command-block powered proximity traps that don't have any triggers marking them as well as hidden walls that...

It took many months of cries from all around the internet—and a particularly large groan from an ex-Lifehacker editor-in-chief—but Apple has not only acknowledged the existence of its iMessage problem, it's promising a fix.

Welcome back, my greenhorn hackers!

For over 20 years, a tiny but mighty tool has been used by hackers for a wide range of activities. Although well known in hacking circles, Netcat is virtually unknown outside. It's so simple, powerful, and useful that many people within the IT community refer to it as the "Swiss Army knife of hacking tools." We'll look at the capabilities of Netcat and how the aspiring hacker can use it.

One of the best things I love most about any new gaming console are the apps—I can switch from playing Assassin's Creed III to re-watching the fifth season of Breaking Bad on Netflix without ever getting off the couch. Beat that Atari.

Steam is an online platform that lets you download and play over 2,000 video games, from first-person shooters to RPGs, as well as a pretty long list of indie games. You can play on your PC, Mac, mobile device, or even your television, and it has a community of over 40 million gamers. Prices are different depending on the type of game and how new/popular it is, but they're generally about the same as what you'd pay for an Xbox or PlayStation version. They also have a decent list of free games...

If you've ever logged on to the popular music application Pandora, your password is saved onto that computer in the local storage...for good.

Use PubSubHubbub
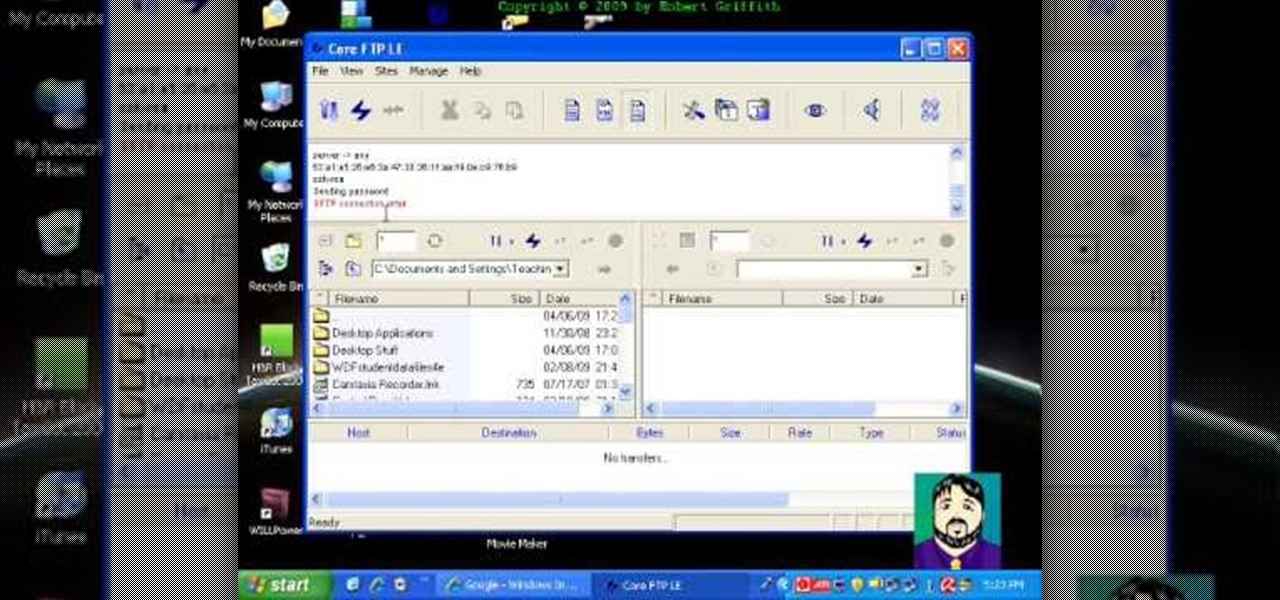
Select an FTP client that allows you to connect to the webserver. Download a free Core FTP Le software. Install the program. Use the site manager to name the internet site. Create a host/url, a user name, password and a connection. Connect to the web server. Create an index file to make files viewable. Open the Core FTP LE software. Drag files from the desktop (left side of the dialog box) to the internet server (right side of the dialog box.)

Prepare a chocolate cream roll. And into your whip topping, put in one teaspoon of vanilla extract, about a cap full. Stir the whip, the vanilla removes the packaging taste. Spread the whip all over the cake, nice and thick. Clean out the edges and round it out. With a fork, drag the prongs across the top of the log. And all around the surfaces. With a knife, spiral out the ends of the log. Start in the center and slowly spiral out. Dust the top of the cake with cocoa powder, then do the ends...

Minecraft 1.8 has introduced Enderman to tons of blocky servers all over the world. If you're looking for ways to fight against Enderman or just avoid Enderman all together, take a look at this walkthrough on how to do both. Be sure to grab an Ender Pearl so that you can half their attack range!

Find which airlines Google is providing free Wi-Fi on this holiday season, fix shutter lag on digital cameras, wipe your hard drive for free, improve your Wi-Fi router performance, adjust your television and monitor for accuracy, choose the best 1080p projector, use a single server that can handle OS X, Windows & Linux simultaneously, and use the best audio encoding system for Windows Media Center and Zune.

This tutorial covers the ABC's of getting started in Web Development. Mike Lively shows you how to get a server, a free HTML editor, and free FTP Software.

XAMPP is a free install program you can use to turn your computer into a web server. This video also has a installation guide for XAMPP

Samba can be configured to allow any user with write access the ability to create a link to the root filesystem. Once an attacker has this level of access, it's only a matter of time before the system gets owned. Although this configuration isn't that common in the wild, it does happen, and Metasploit has a module to easily exploit this security flaw.

Reconnaissance is one of the most important and often the most time consuming, part of planning an attack against a target.

Passwords on Windows are stored as hashes, and sometimes they can be tough to crack. In certain situations, though, we can get around that by using the hash as is, with no need to know the plaintext password. It's especially interesting if we can manage to get the hash of an administrative user since we can then authenticate with higher privileges by performing an attack known as pass the hash.
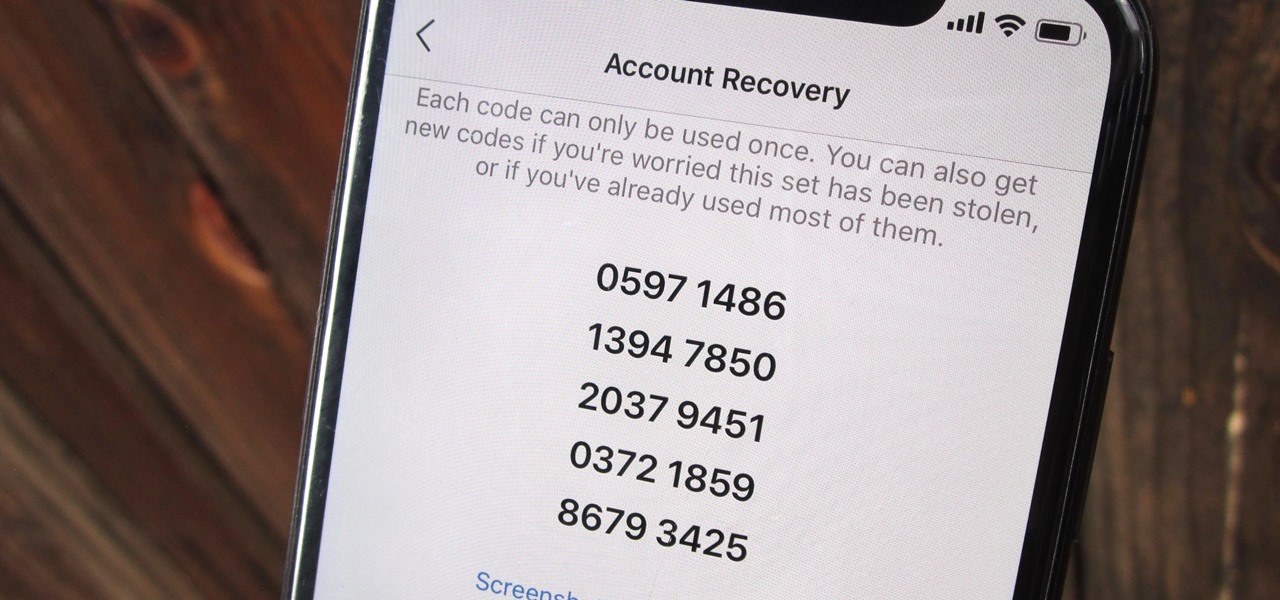
Two-factor authentication (also known as 2FA) adds a necessary additional layer of security to your username and password in many important apps. On Instagram, 2FA requires you to confirm it's you attempting to log in, with a special code sent to you via text message. Enter the code and you're in ... but what happens when you need to log in and don't have access to your phone?

The iOS 12.0 beta earned admiration for its superior performance to last year's controversially buggy iOS 11. That doesn't mean it was free from problems before the stable release went live. During the initial iOS 12.0 beta testing phase, there were plenty of bugs and glitches, many of which affected the apps we use every day. However, none of these issues persist anymore since iOS 12 stable went live.
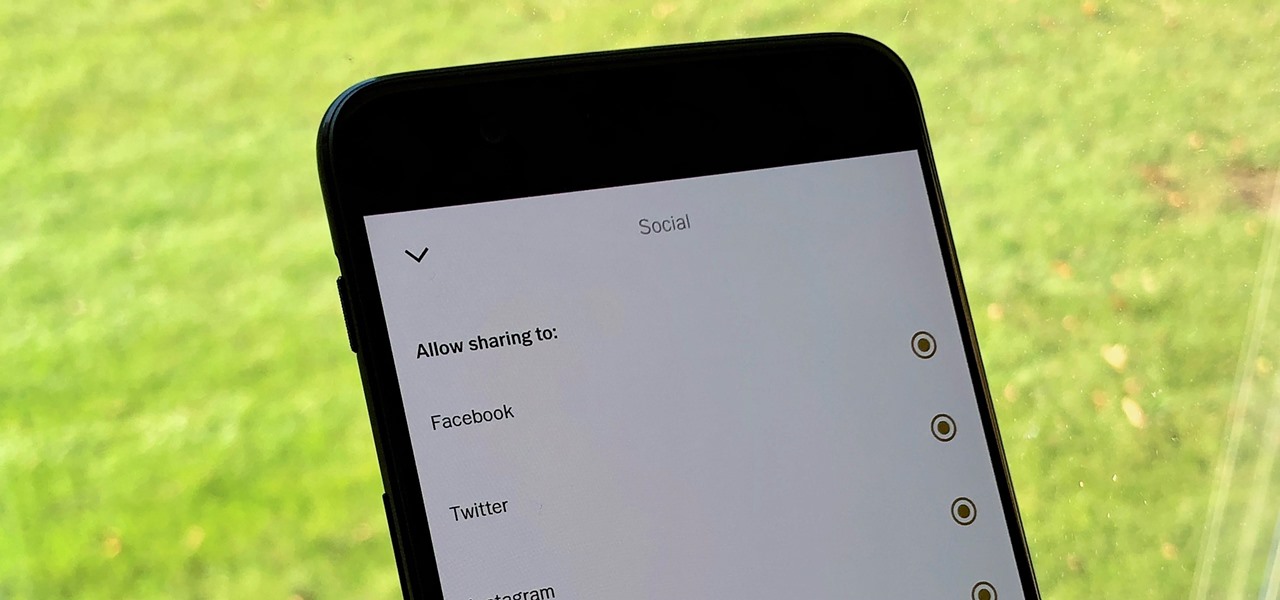
In this day and age, publishing content to one social media account just doesn't cut it. VSCO, Facebook, Twitter, Instagram ... you need to be active on all. And if you prefer editing and posting all of your photos on VSCO, you need a way to share those images with your other accounts.

Sharing your Wi-Fi password is like giving an unlimited pass to snoop around your network, allowing direct access even to LAN-connected devices like printers, routers, and security cameras. Most networks allow users to scan and attempt to log in to these connected devices. And if you haven't changed the default password on these devices, an attacker can simply try plugging them in.

Welcome back, my hacker novitiates! If you have been following this new Snort series, you know that Snort is the world's most widely used intrusion detection/protection system. Now a part of the world's largest network equipment company, Cisco, it is likely to be found everywhere in one form or another. This makes a compelling argument for learning how to use it, as it will likely be a necessity in any security-related position.

Welcome back, my greenhorn hackers! A few years back, Microsoft implicitly recognized the superiority of the Linux terminal over the GUI-based operating system by developing PowerShell. Since Windows 7, every Windows operating system has had PowerShell installed by default, and they even made PowerShell capable of running Linux commands on Windows!

Hey everyone, this guide will show the process of stealing your victims Facebook credentials. This is a followup to my previous post.
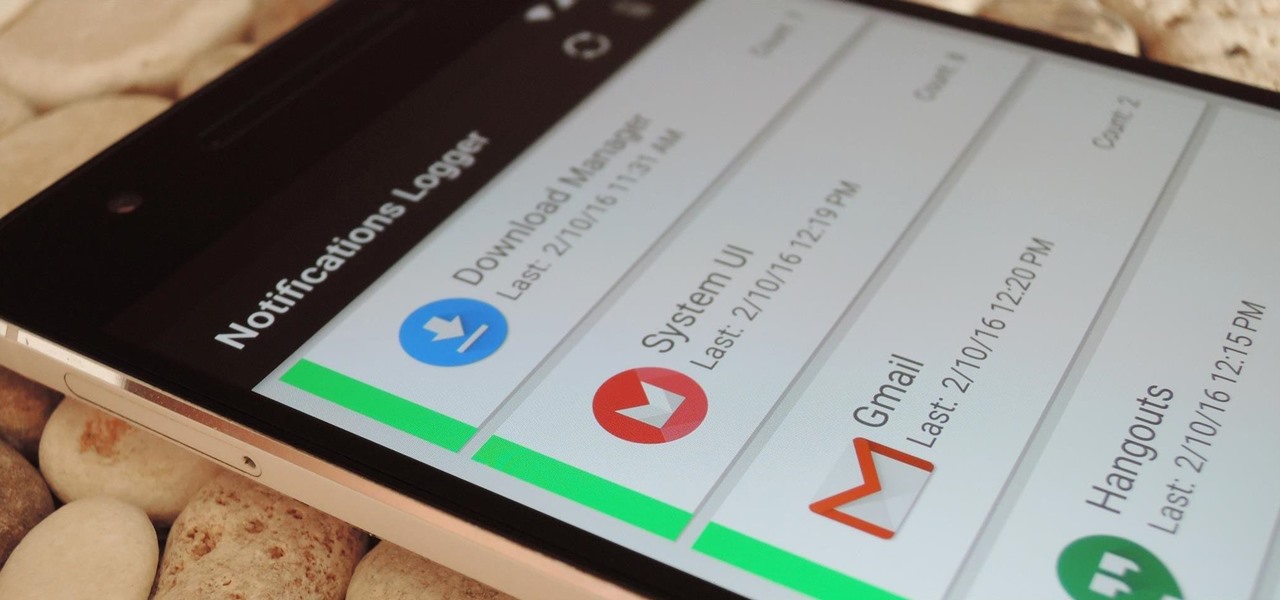
If you've ever prematurely dismissed all of your push notifications before you got a chance to read each one, you know how annoying it can be to dig through all of your apps to try and find the one with the missed notification.

Whether you're ready to admit it or not, we've all got our alter egos—especially when it comes to the internet. Perhaps you have one Facebook account that you use publicly, while maintaining a second account for more private interactions.

I saw many people asking for a Tutorial about writing their own Remote Administration Tool, so I now introduce you in a basic kind of RAT. This program is not for real use, but for learning how you could write this kind of tool. It will be basicly coded and not very refined. I used Python 3, so you have to install it if you want to use this program unchanged. Also this RAT is for Windows and almost all features won't work under Linux.

Windows 10 runs on laptops, desktops, tablets, and even phones—but even though the operating system should scale accordingly, fonts and icons aren't always perfectly sized for every screen. Luckily, though, there's a handy new menu for adjusting the size of your screen's contents, which you can use to make everything bigger or smaller to match your preferences.

Hi Folks. This is my first post. I will teach how to create a server and client python reverse shell using sockets and python language. The script i'll post here is going to be very simple, and from here you'll have the possibility to adapt to your own purpose. For example, my original script can download files, upload files, make changes to registry, create user accounts and more. I'm sure you could do it on your own too.
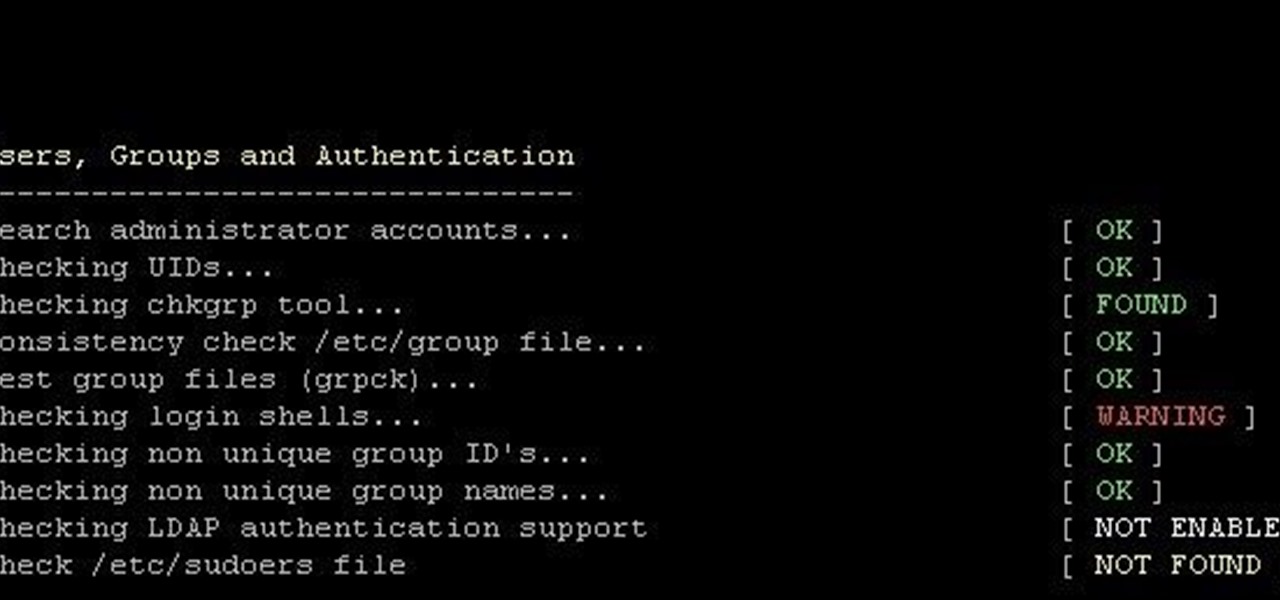
This is finding some of your vulnerability using Lynis. This tool Lynis is used on Unix and Linux type operating systems (sorry windows). So lets get started

Welcome back, my hackers novitiates! As you read my various hacking tutorials, you're probably asking yourself, "What are the chances that this hack will be detected and that I'll land behind bars, disappointing my dear mother who already thinks I'm a loser?"

Welcome back, my aspiring hackers!
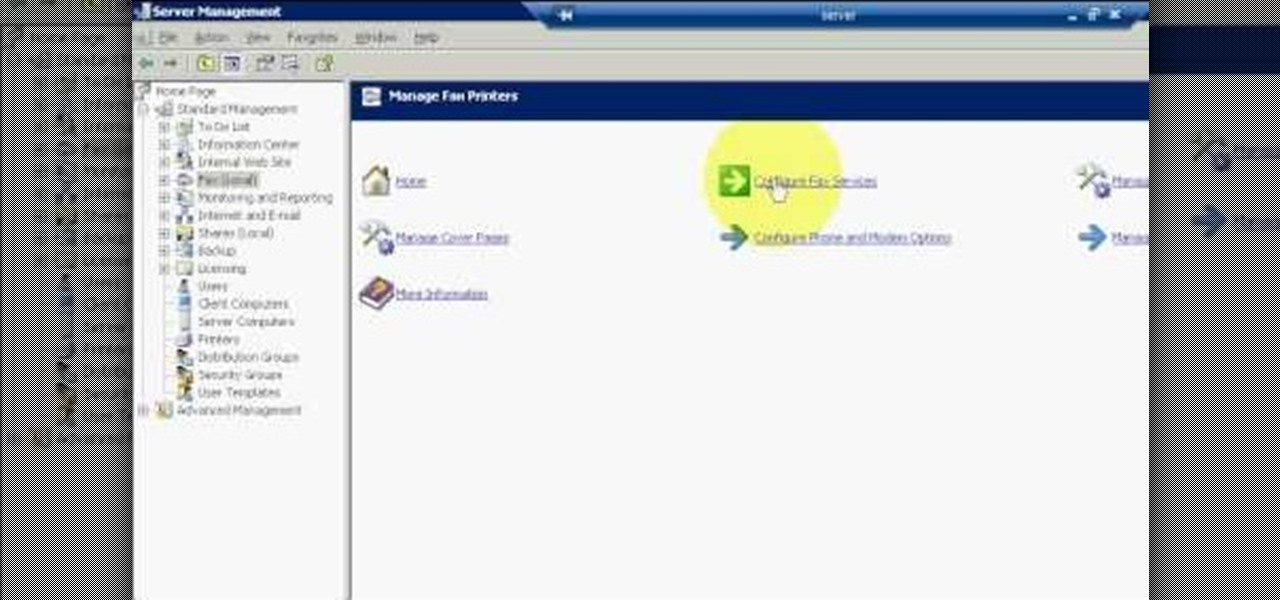
The first step to create a fax using Outlook 2003 and 2003 server. Using add/remove windows component make sure your fax equipment is properly installed. Under the start menu select the printers and fax option and select the share option. Then under administrator tools/users/new/users/fax to enter your password to turn our fax information transfer on. You must now select fax user and select advanced settings and double check to make sure the fax is able to see the object it needs to send the ...
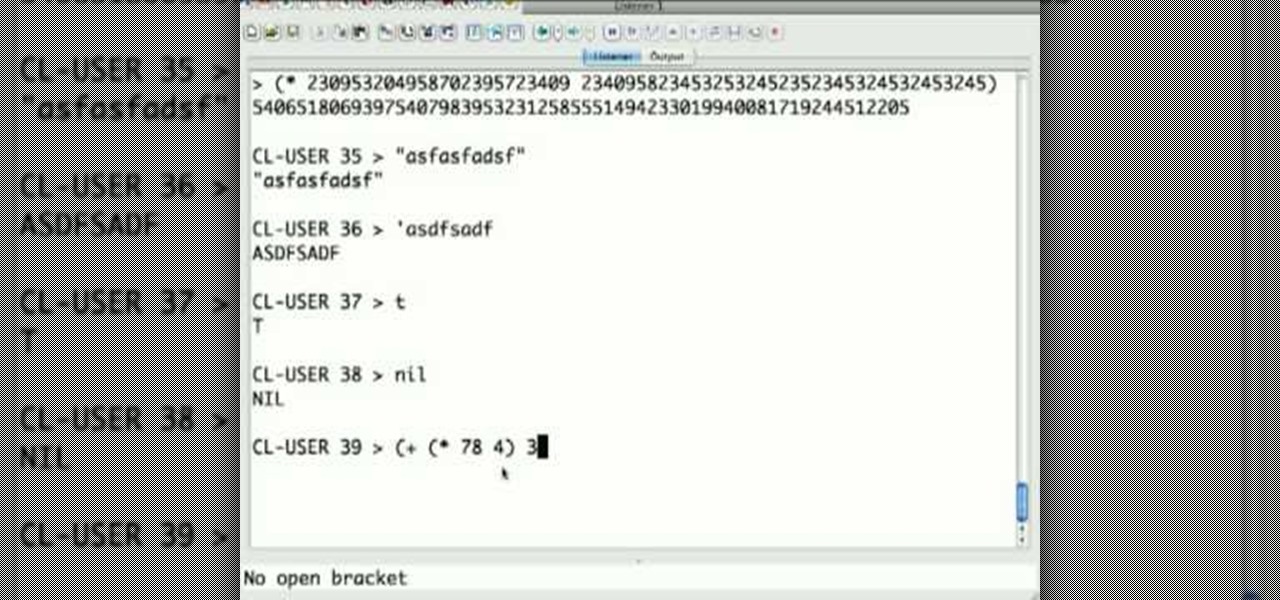
The programming language LISP is definitely not as well known as XML or C++, but it's been around for a very long time and is one of the easiest computer programming languages to learn if you want to create a web server. It is a contemporary of Cobal and was devloped by John McCarthy. To learn how to use LISP for beginners, check out this tutorial.

You can create a multiple user accounts and enable fast user switching. To do this go to system preferences and open accounts. Now authenticate yourself by clicking the lock icon to be able to make changes. Now click + button
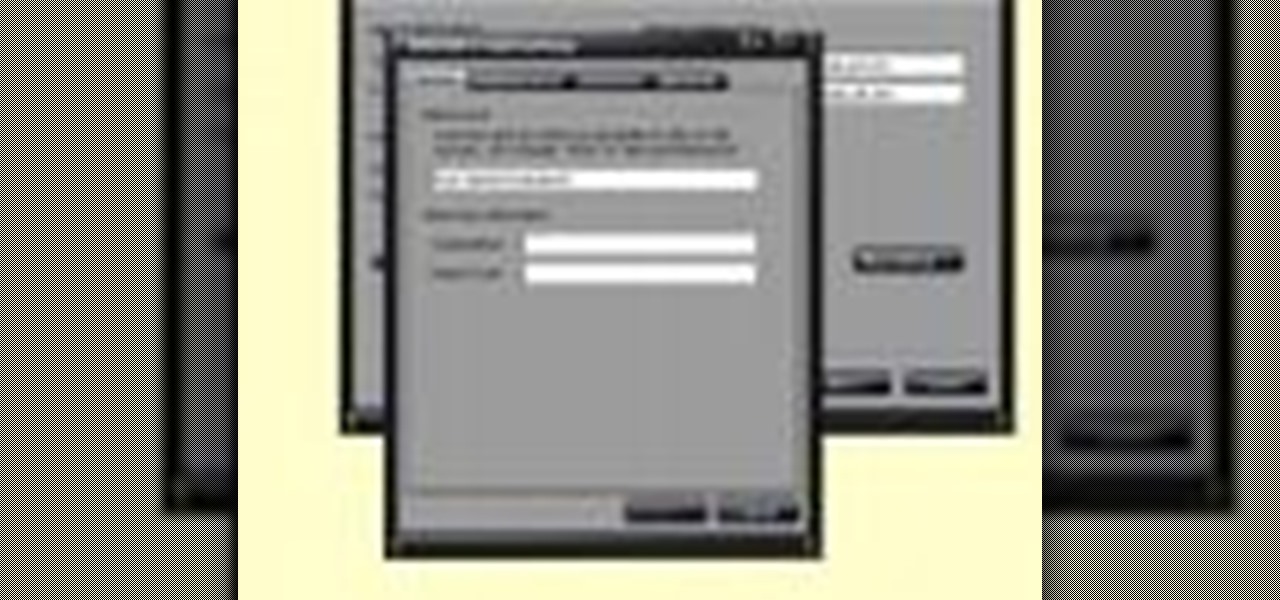
In this tutorial, we learn how to set up your AIM/AOL e-mail accounts in Outlook. First, go to Outlook and open up e-mail accounts through the tools menu. Now, add a IMAP serve, then add in your user information. After this, enter in your server information, and click the settings button. Change the name of your folder if you are using multiple accounts, so you don't confuse them. In the next tab, check the outgoing server mark, then on the advanced tab, change the last number to 587. Press o...
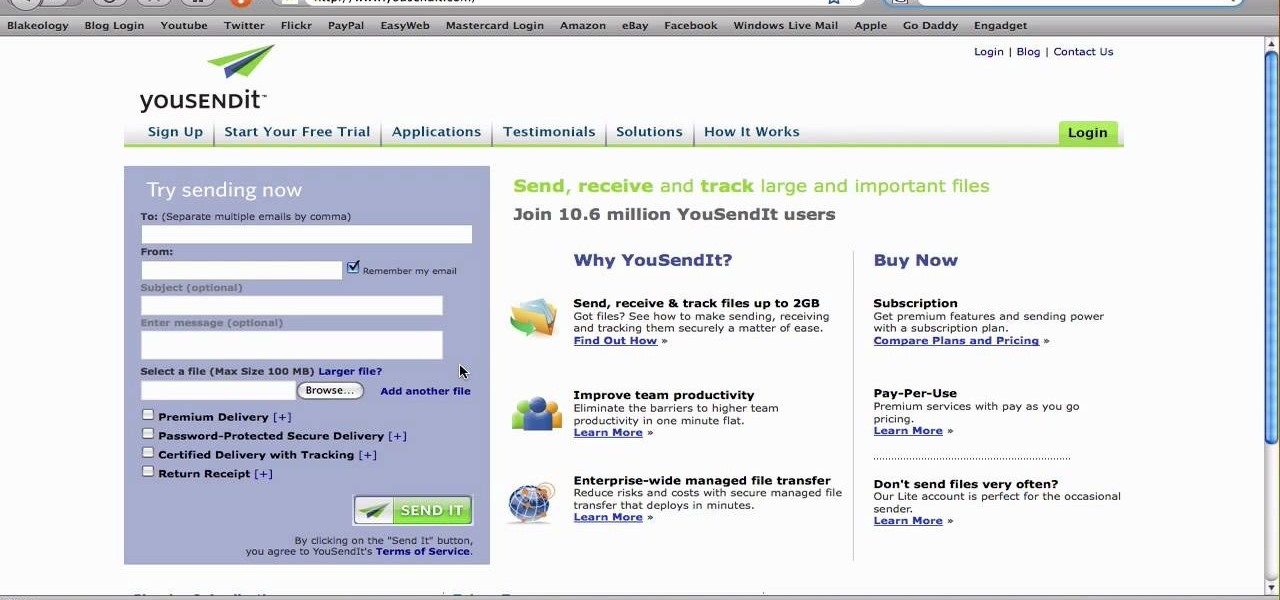
Most e-mail servers cut you off at about 10mb for attachments. If you need to send a larger file, watch this tutorial. In it, you will learn how to send files upwards of 100mb for free and avoid server limits. This clip will show you how to send quick and easy files to your friends without worrying about them not fitting in your messages. This video will show you step by step how to accomplish this in less than five minutes.
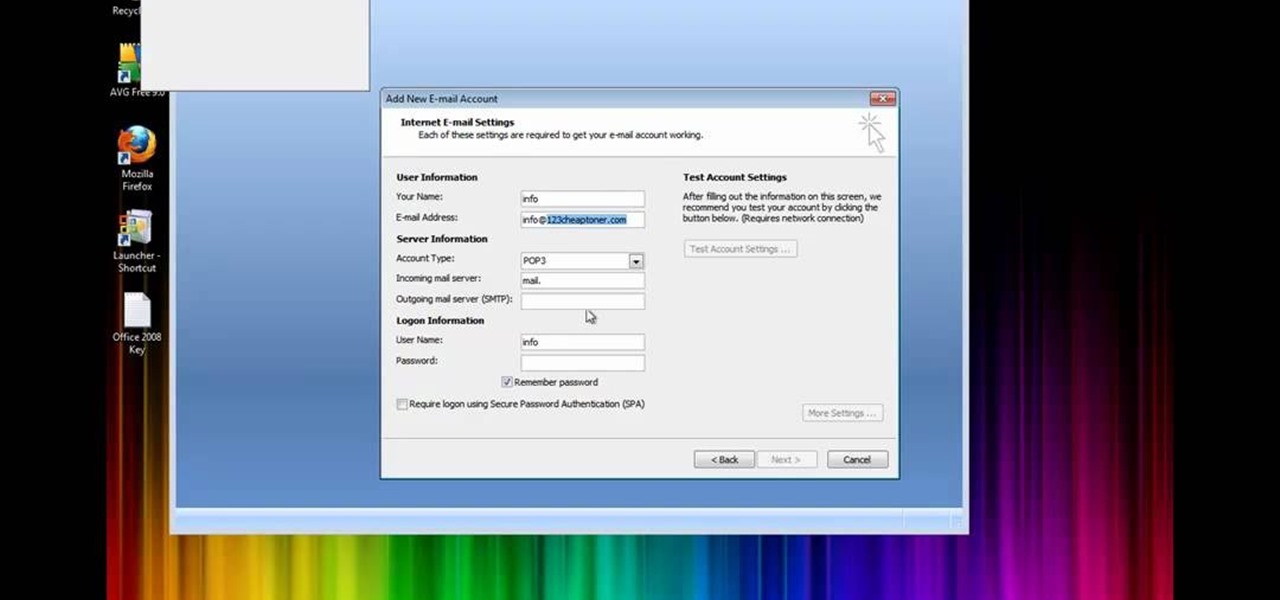
In this how to video, you will learn how to set up Outlook 2007 in Windows 7, XP, or Vista. First, open the program. Click next and and check manual configuration. Select the top option in the next window. Now you must fill in your name, email address, and server information. Lastly, fill in your user name and password. Click more settings and select the outgoing server tab. Here you will authenticate your email address. Once this is done, click okay and next. Click finish and the program can...