This video teaches you to sync Google Calender with the Apple iPad Calender app. The first step involves going to 'Settings' and then to 'Mail Contacts Calenders'. Add an account to the application. For doing this, go to Microsoft Exchange. Type in your email ID in the space provided for it and skip domain. Type in your username and password. Click on 'Next' and 'Accept' in the resulting box. Then a box named 'Server' appears. For the server type 'm.google.com' and click 'Next'. Turn off the ...
In this Computers & Programming video tutorial you will learn how to update a website with an FTP client (v† la FileZilla). Download FileZilla client from www.filezilla-project.org. Find your server IP address from your web host, which will be found in the hosting control center. In the video, it is GoDaddy.com. Open your filezilla client and put in the IP address of your web host and your username and password for your hosting account. Then click ‚Äòquickconnect‚Äô. This will connect you to ...
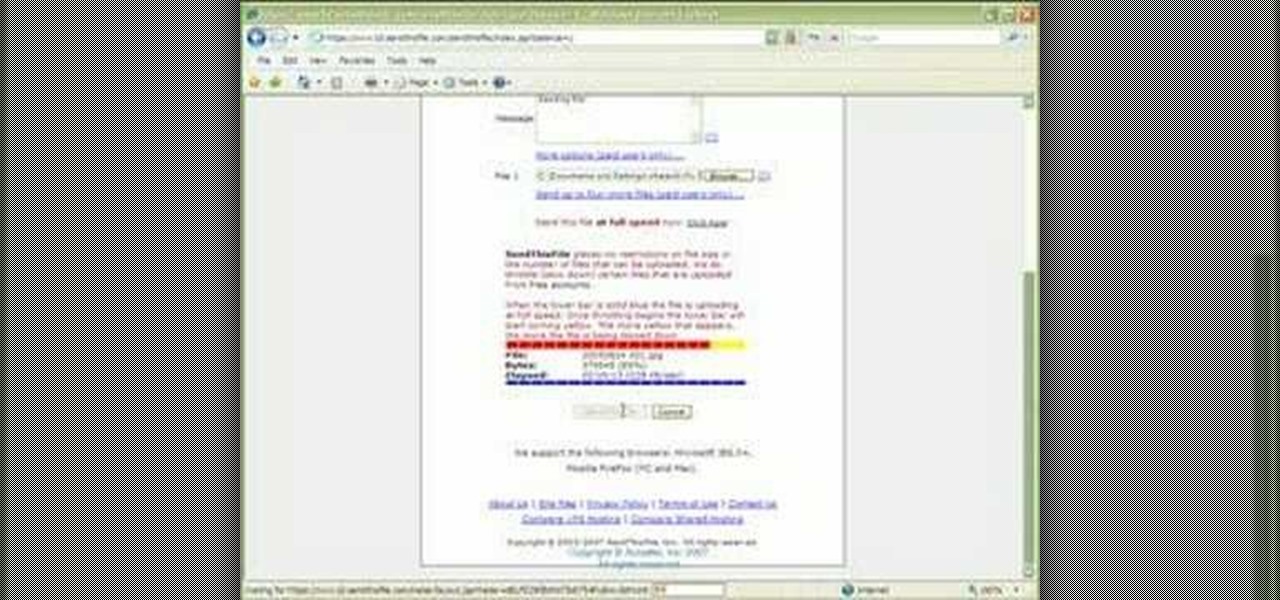
1. Type in WWW.sendthisfile.com in the web toolbar and press enter 2. Click on Register found on the top right side

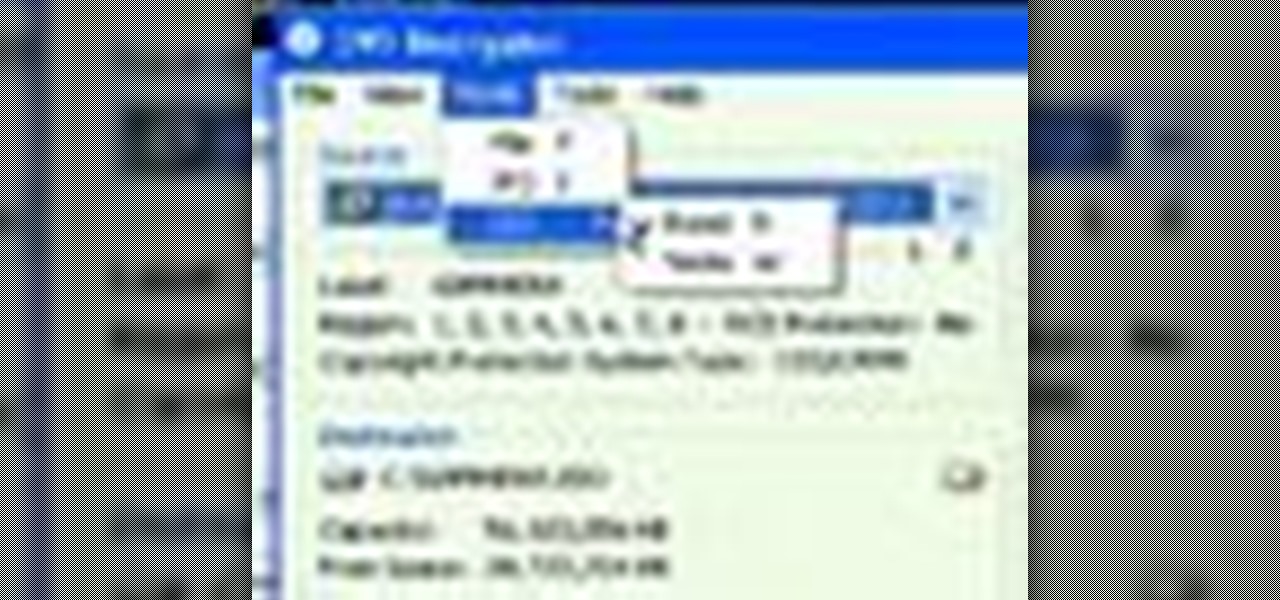
Some times malicious programs can infect your registry and fill it with lots of unwanted information. You may need to clean it to prevent the virus from causing any further damage to your computer or to even disable the virus. It is a very lengthy and complex process to do this manually. So you will need to use one of the powerful free tools available online. Hijack This is one of the most powerful program that can be used for this purpose. So go the website and download this free tool. Insta...
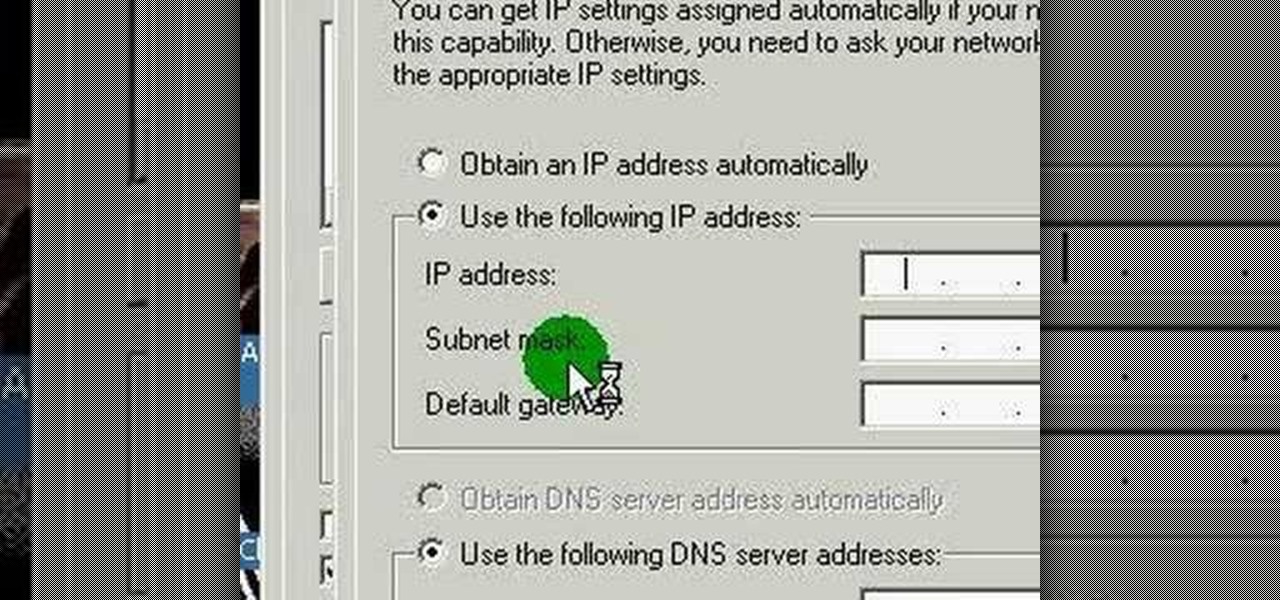
This video discusses how to change your IP address in Windows XP. Start by clicking on the Start Button and then Run. Type in "cmd" and press enter. This will open a Command Prompt box. From here type in "ipconfig" which will show your current IP configuration, including your IP Address, Gateway, DNS Servers, etc. Next type "ipconfig /release". This will release all IP information from your current network adaptor. Next open up network connections, right click on Local Area Connection and sel...
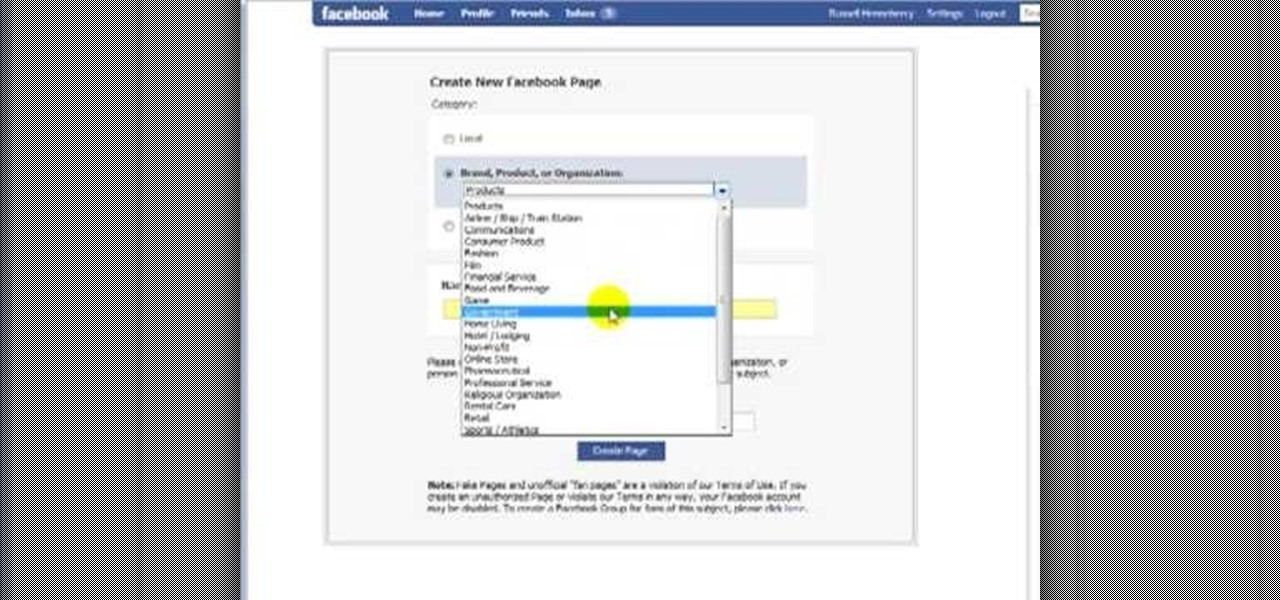
First, you must log on to your personal face book page or create one if you do not already have, but don't log in yet. Then at the bottom of the face book home page click the click here sign within the words to create a page for a celebrity, band, or business click here. Now that you are on this page log in. You will be able to select what you are. Enter name of your website, now select that you are authorize to create this page. You must then enter your electronic signature, which is the exa...

This video demonstrates the technique to setup a Yahoo email on an iPod Touch. You start going into settings and then clicking account. On the next screen you will click "Other" and then click on "Pop". At this point you enter your name and email address that you use for your Yahoo email account. Incoming server or host name is "pop.mail.yahoo.com", next is the username (which is your yahoo email address without the @yahoo). You will then enter your password and the out going smtp server whic...

Hak5 isn't your ordinary tech show. It's hacking in the old-school sense, covering everything from network security, open source and forensics, to DIY modding and the homebrew scene. Damn the warranties, it's time to Trust your Technolust. In this episode, see how to turn any Windows application into a service.

In this four-part video tutorial, Joe Stagner will demonstrate, using ASP.NET, uploading a single file from the client machine to your server.

Most of us stay with a certain computer operating system - or a specific version of that system - because it gives us a great amount of ease. But what if you're using an older edition and it's starting to look a bit, well, outdated? Make your Windows Server 2003 look newer by installing the Windows XP Luna theme. You'll have to enable Themes to make this work. Check out this video for the tutorial.

Installing Joomla on a Windows server can be tricky, on Windows running IIS even more so. Installing Joomla 1.5 in this scenario has caused many frustrations.In this video, we take the process step by step and jump over the hurdles that cause some people to wind up pulling their hair out. If you follow along closely, you will be up and running in no time, and if you haven't already tried to do this, you will wonder why people find it so difficult. There are some prerequisites to the steps in ...

When you try running Apache, Joomla, PHP and MySQL at the same time, you should expect a few hiccups. But there are ways to get them running smoothly and effortlessly together, and this video will outline the process of getting your Joomla Content Management system up and running correctly on Windows.

This video takes us through a process of speeding up our internet connection using OpenDNS.com. Open the webpage and go to solutions and click on the icon open the DNS page and it lists computer or router, she selects computer and list of operating system is listed, she selects vista. She goes to start and selects control panel, click on view network status and connection, in that select view status and then click on properties and on the networking page, go to internet protocol version 4 and...

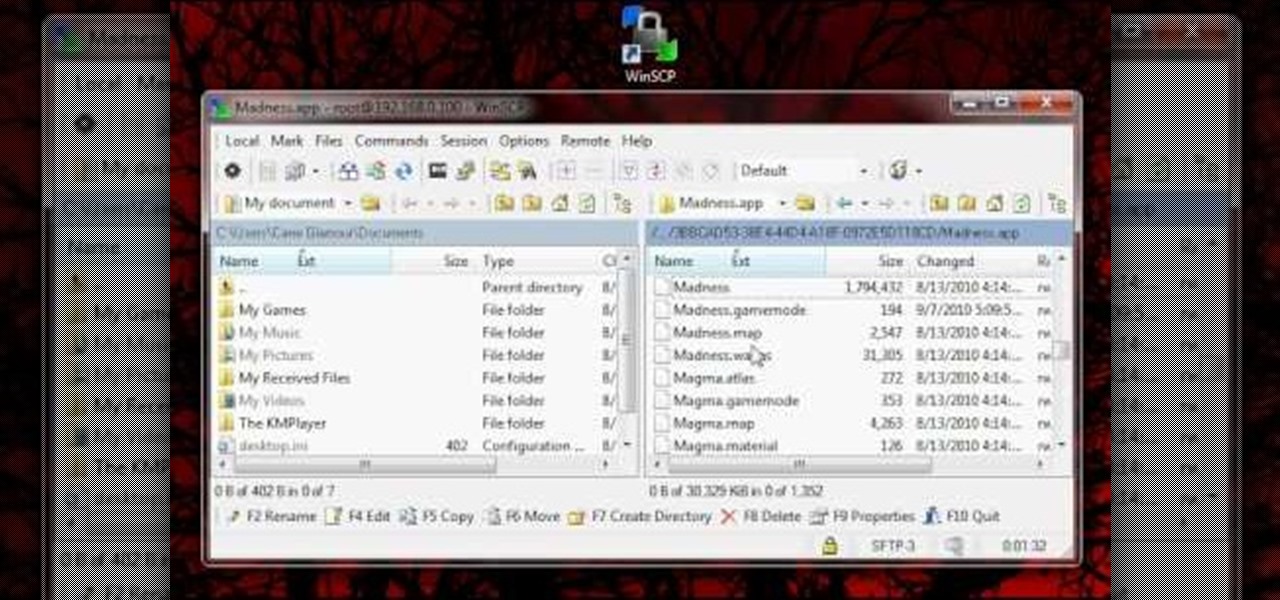
In order for this tutorial to work, you will need a jailbroken iPhone or iPod Touch. Once you have this, download the OpenSSH protocol from Cydia and then download WinSCP onto your PC. Once you've hooked everything up and logged in, navigate through your Applications directory until you find the TowerMadness app. Once you have opened the TowerMadness app, all you need to do now is find the right file and change it around to increase the amount of money you have!

Remember summer camp? Remember the smell of the log cabins? The feel of the treated wood? Well, you can create something for your home that's perfect for a nostalgic summer camp aesthetic. Meg Allen Cole (recently of Threadbanger) was inspired to make this mid-century modern wall hanging piece made from a small wooden log (or branch) when she was at a relaxing, wooded vacation spot in Maine. And she shows you how to make one, too!

Whether you're new to Adobe InDesign or a seasoned graphic artist after a general overview of CS5's most vital new features, you're sure to be well served by this official video tutorial from the folks at Adobe TV. In it, you'll learn how to get all the benefits of real-time, on-set logging even when working with tapeless cameras with OnLocation CS5.

Want to play your video collection on any media extender, console or AppleTV? Step one is to get your movies off of the DVDs and onto your hard drive! If you're like most people you probably have a huge library of DVDs that you've bought and collected over the years. Unfortunately, it's an inconvenient format if you want to playback all that content anywhere around the house. So, learn how to rip and encode that stack of DVDs into a format that you can play on your Windows Media Extender, set...

When you have a personal Instagram account but also manage other profiles — like ones for work, your entrepreneurial startup, an alter ego, or your famous pet, to name just a few examples — how do you manage them all from the same device?

It's easier than you might think to hack into Wi-Fi routers using just one unrooted Android phone. This method doesn't require brute-forcing the password, a Windows OS for converting PowerShell scripts into EXE format, a reliable VPS for intercepting hacked Wi-Fi passwords, or Metasploit for post-exploitation tricks.

While hackers have taken advantage of numerous vulnerabilities in Adobe's products to deliver payloads to Windows users via PDF files, a malicious PDF file can also wreak havoc on a Mac that's using the default Preview app. So think twice before double-clicking a PDF open on your MacBook — it might just be a Trojan with a rootkit inside.

Imagine for a moment that a VPN is like putting on a disguise for your computer. This disguise works to change your IP address, secure your traffic with encryption, and mask your location to bypass regional restrictions. This makes it a helpful tool for both whistleblowers and journalists. VPNs are also built into the well-known Tor Browser.

New updates to the journaling app Day One include more security for journal writers' data. For example, users can now enable end-to-end encryption. The encryption does not happen automatically; however, users must go to Settings — within Journals — then select each journal they want encrypted.

At this point in our series on creating a customized hacking container, you should be able to use Docker to save and retrieve customized instances of Ubuntu from your own machine. Make sure to revisit part one and part two if you need a refresher.

Hey everyone, this will be a quick post. Facebook does not use HTTP Strict Transport Security (A header that tells the browser to only use HTTPS when communicating with the server) on subdomains of facebook.com. That means, if someone uses facebook in a different language, the browser will attempt to connect using HTTP first. An attacker can intercept that request and serve a different page, including a fake login one.

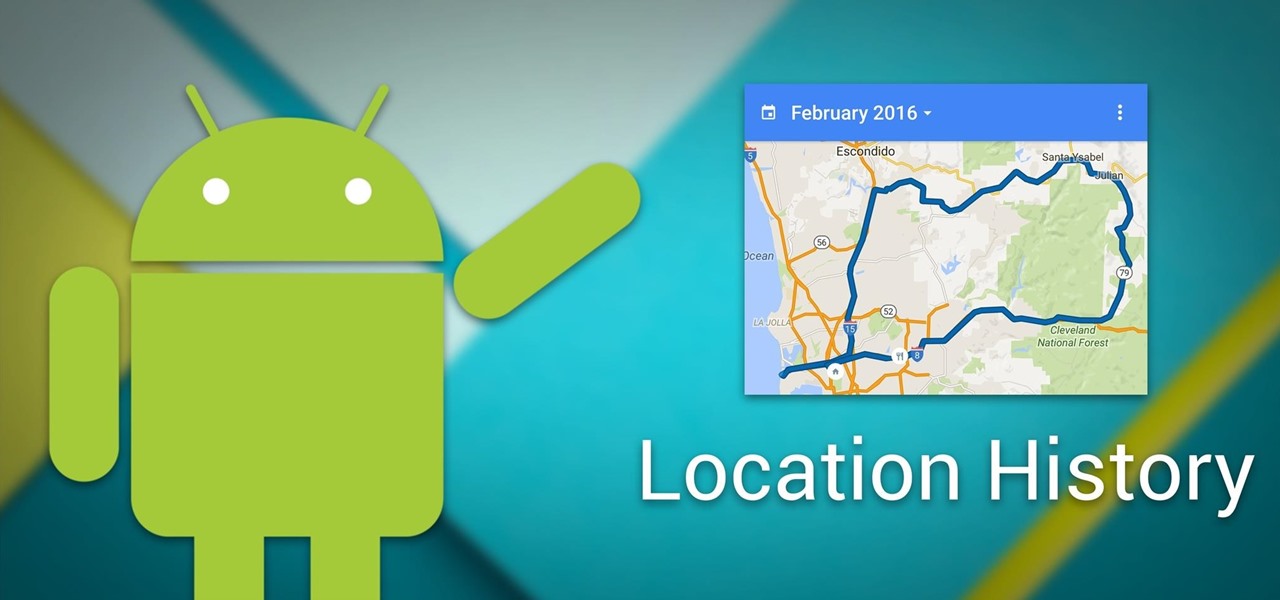
Your smartphone has a GPS chip inside of it that can pinpoint your location down to the nearest 4 meters, and this little device stays in your pocket or purse all day. Combine those two facts and you start to realize that your phone knows exactly where you've been during every moment that has passed since you've owned it.

Good day people, today we will examine some basic, for some people well-known attacks, also we will take a look at some advanced attacks.
Have you ever used an open wifi, which after you connect displays a website to enter your credentials to get internet? That website is called captive portal and widely used in airports, hotels, universities etc. Have you ever wondered what would happen if someone would set up an open wifi with the same name displaying a very similar web page asking for credentials? Usually if there are multiple wifi networks with the same name and encryption, devices only display the one with the highest sign...

This is a quick and easy method for receiving the backend IP (1) of a server who is hidden behind a proxy (2) or a firewall (3).

If you remember last time, we successfully uploaded picture with a small hidden PHP command executer embedded in it onto a server. Now, our goal is to take this a step further and get an interactive shell. To do this, we need to upload another file that either binds a port for us, or connects back. For this tutorial, we will use a Python reverse Meterpreter shell.

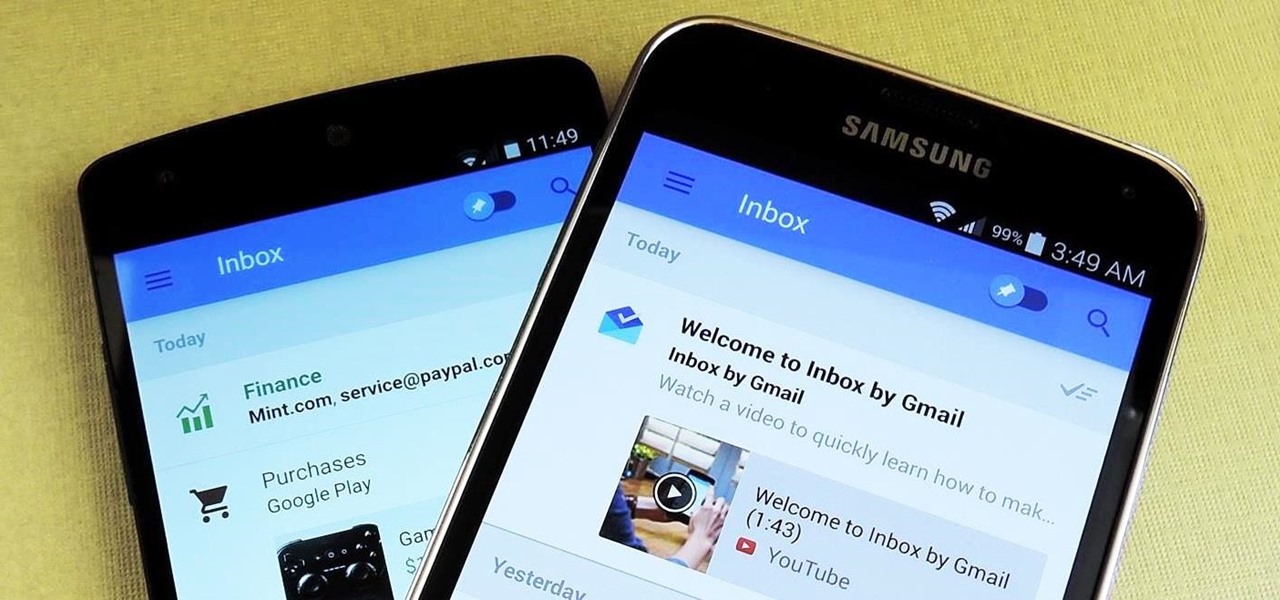
Google's new Inbox by Gmail service offers a new take on email with a particular emphasis on productivity. But, as an invite-only service at this stage, not many people can access Inbox just yet.

Only scumbags hide their call and message history, right? Wrong. While it may seem like a tactic for the unfaithful, it's still a good thing to do for certain contacts on your phone that you don't want to block outright.

Welcome back, my budding hackers! We've spent a lot of time learning to compromise Windows systems, and we've successfully compromised them with Metasploit, cracked their passwords, and hacked their Wi-Fi. However, very little time was spent developing ways to extract the information from the system once inside.

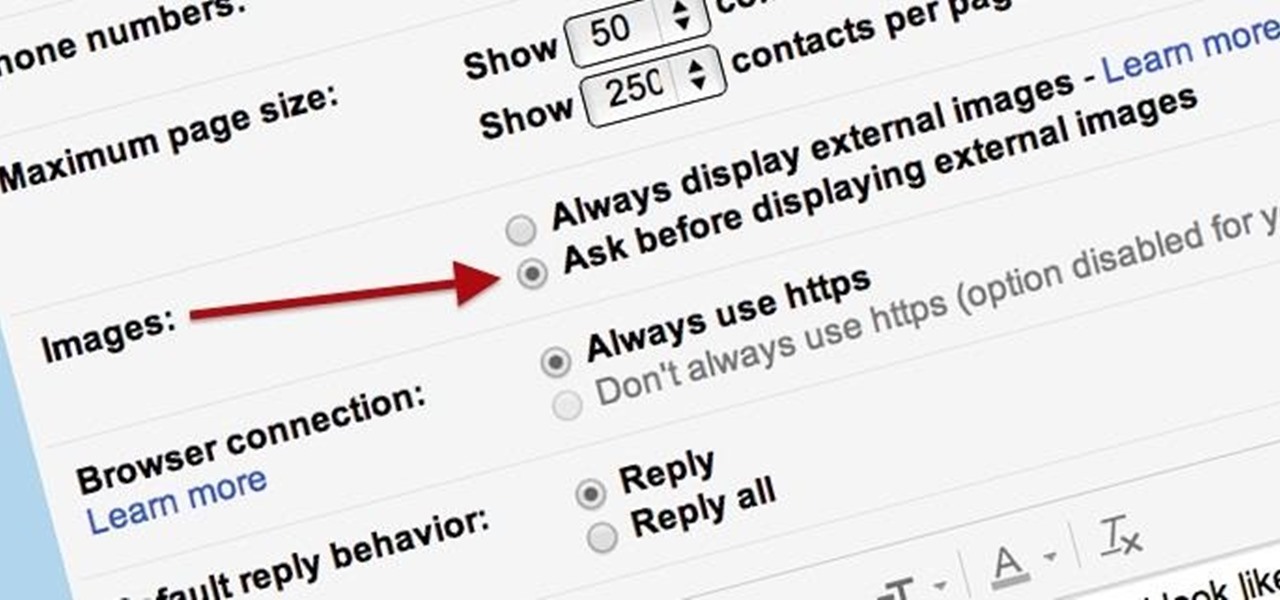
Securing your email address is one of the most important things you can do on the internet. Hackers, spammers, and overly aggressive marketers can turn your Gmail inbox into a heap trash if you're not careful.

Spam emails are emails that are sent to you without your permission. They can quickly fill up your email account if you don't do anything about it. Each email server deals with spam in a different way. Gmail is good at separating the spam for you so that you can get rid of it more quickly. It is easy to delete the spam and if you want to take it a little farther, you can get some of the spam to stop coming all together.

Welcome back, my fledgling hackers! If you're like most aspiring hackers, at one time or another you've probably spent too much time playing Call of Duty and not enough time preparing for your final exams.

A few days ago, Russian hacker Alexy Borodin found a way to get free in-app purchases on an iPhone or iPad. In-app purchases include things like items and power-ups for iOS games, as well as subscriptions and "premium" memberships for certain apps.

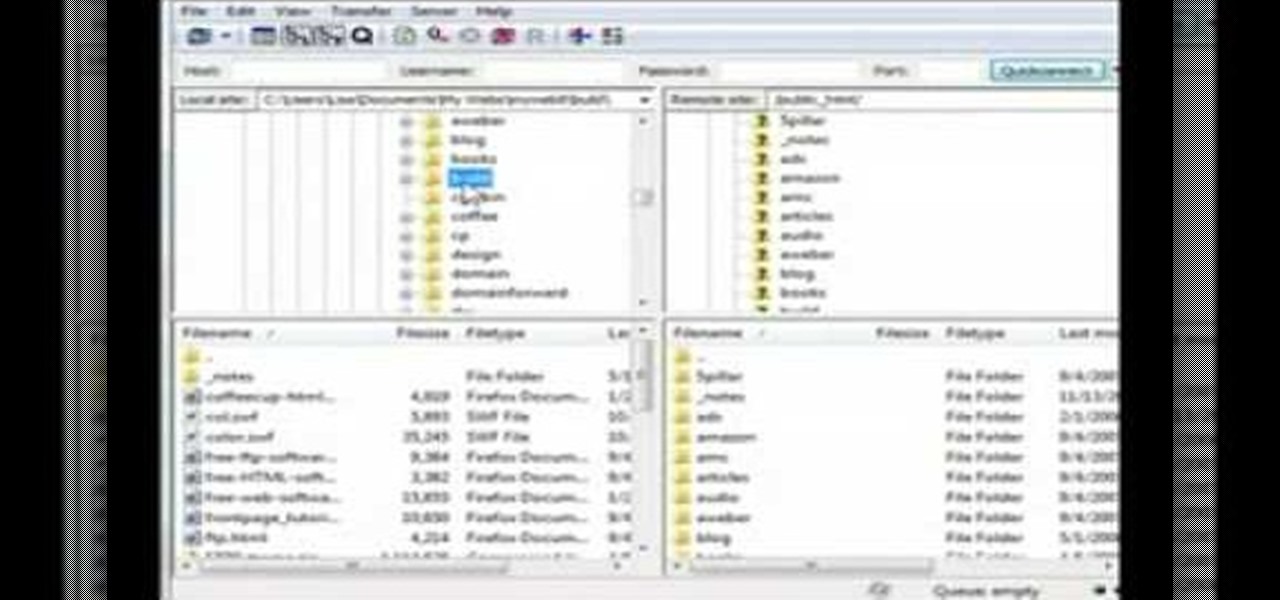
This video describes that how to use the file transfer protocol prgram. First we have to download filezilla to our computer. Go to google and download it first into the computer. There is a username and password to use the FTP. Open the filezilla and come to Host. There we have to type ourdomain.com or ftp.yourdomain.com. Next you have to enter the username and password. Next you have click quickconnect there. Then you will connect to your webserver. In filezilla there are four quadrants ther...

Isn't it annoying when you want to check your Facebook or MySpace but you are at school and hit a big giant Websense blocker? Well, if you are stuck in a library or somewhere else where there are filters on your surf-ability, check out this tutorial for a useful hack.

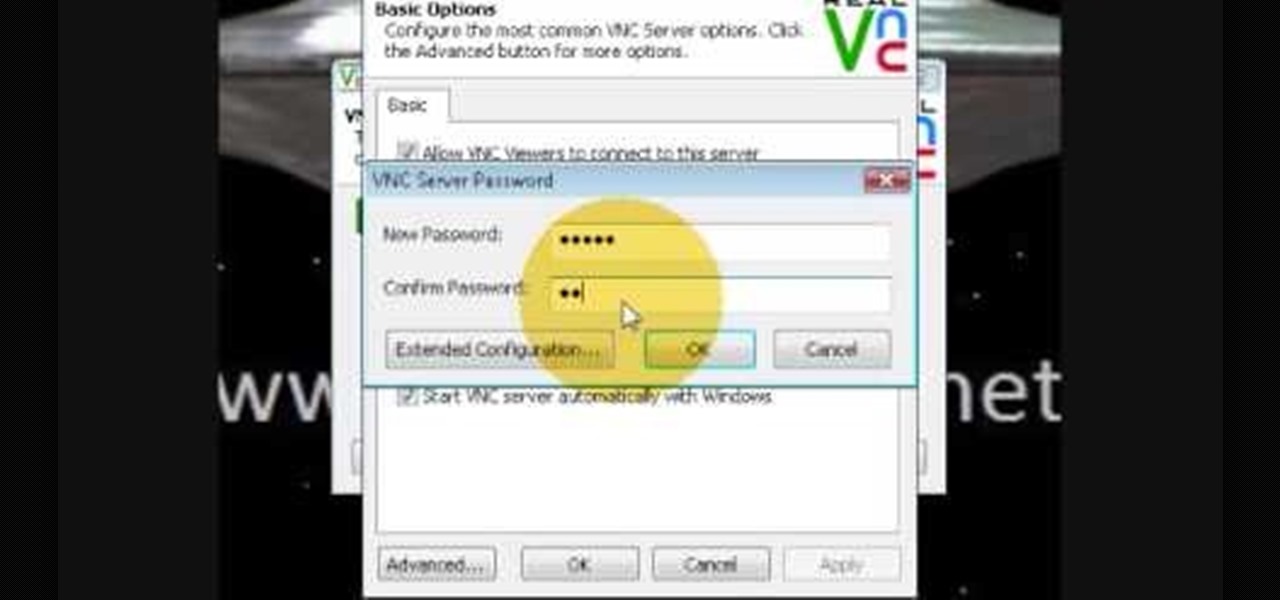
If you want to know how to monitor another computer screen with Real VNC, you must watch this video. Install Real VNC in your computer and computer that you're going to monitor. Remember the folder where you installed it and check the "Create a VNC Viewer desktop icon" checkbox. Write on a paper the IP address of the computer that you're going to monitor. On the VNC Server Status window, click Configure button. On the Authentication field, select VNC password and on the Encryption field, sele...

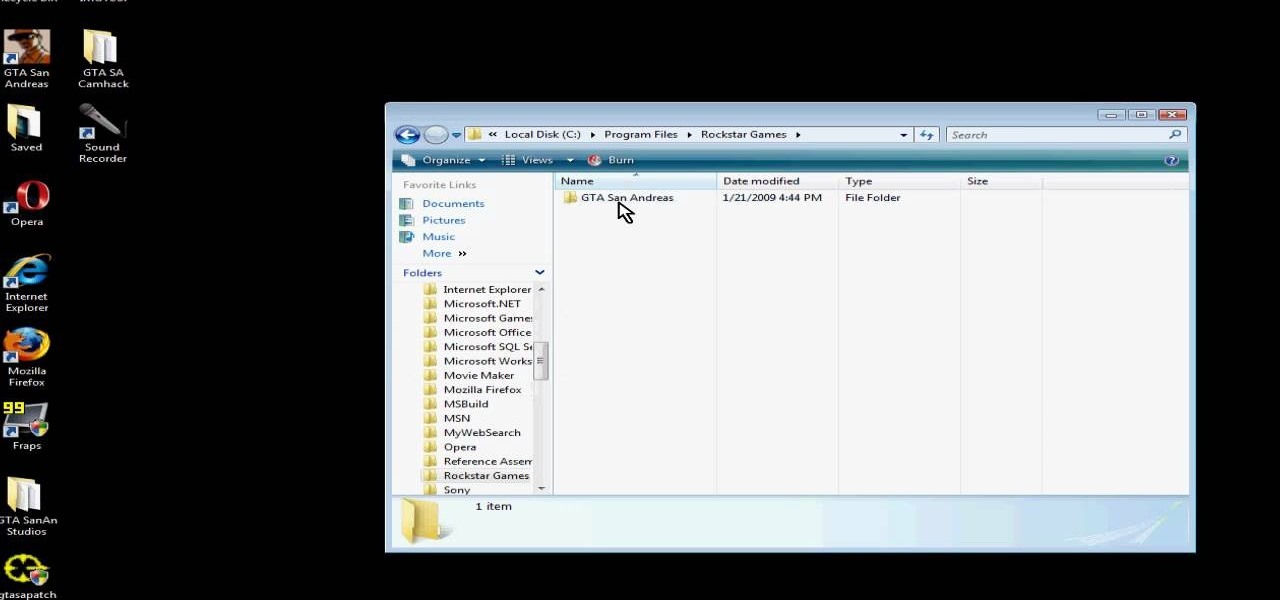
Although Grand Theft Auto 4 was released, many people are still going to want to play GTA San Andreas. Here's how to download and install GTA San Andreas Multiplayer. First, go to Google and search GTA San Andreas Multiplayer. Then, click on the first result that comes up. Go to that website and click on one of the download links that shows up. (Either one of them is fine.) Open the file and follow the Setup Wizard. The installation process takes a very short time and is very easy. Then navig...