
How To: Send food back at a restaurant
Learn when it’s appropriate to send your meal back in a restaurant, and how to do it without offending the chef.


Learn when it’s appropriate to send your meal back in a restaurant, and how to do it without offending the chef.
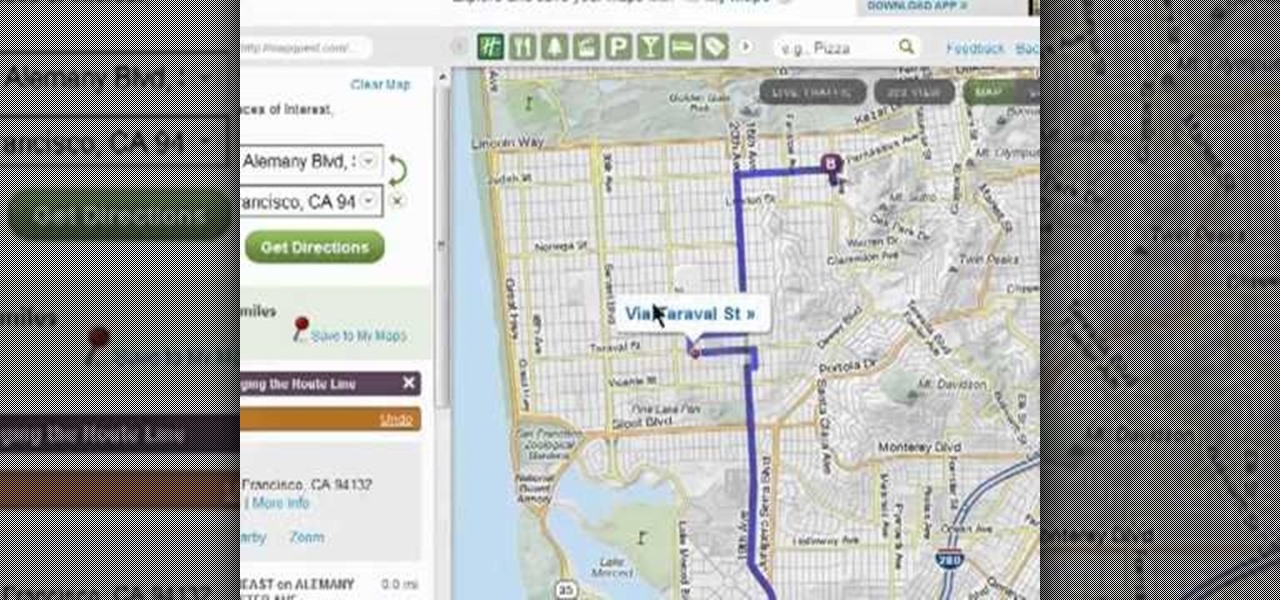
Need some help figuring out how to sign into the latest version of MapQuest? It's easy. And this brief video tutorial from the folks at Butterscotch will teach you everything you need to know. For more information, including detailed, step-by-step instructions, and to get started using the new, improved MapQuest yourself, take a look.

Admin accounts are given special privileges to change the system (like installing programs) that user accounts are not. This tutorial shows you a quick way to check using Windows 7's calendar, and also how to go through the Control Panel to find out if you're an Admin or general User on your computer.

Accidentally leave your Gmail open on a public computer terminal? Don't fret. You can have Gmail sign out any unwanted sessions with a click of the mouse. This free video tutorial from the folks at CNET TV will show exactly what to do. Protect your Gmail email account and log out any unwanted sessions with this how-to.

When performing this iPod hack, make sure to turn off your iTunes and keep it from popping up after you've plugged in your iPod via USB. Take a look at this tutorial and learn how to hack into you iPod on your Mac with the program Alterpod. With luck, no error log will pop up once you click restore.
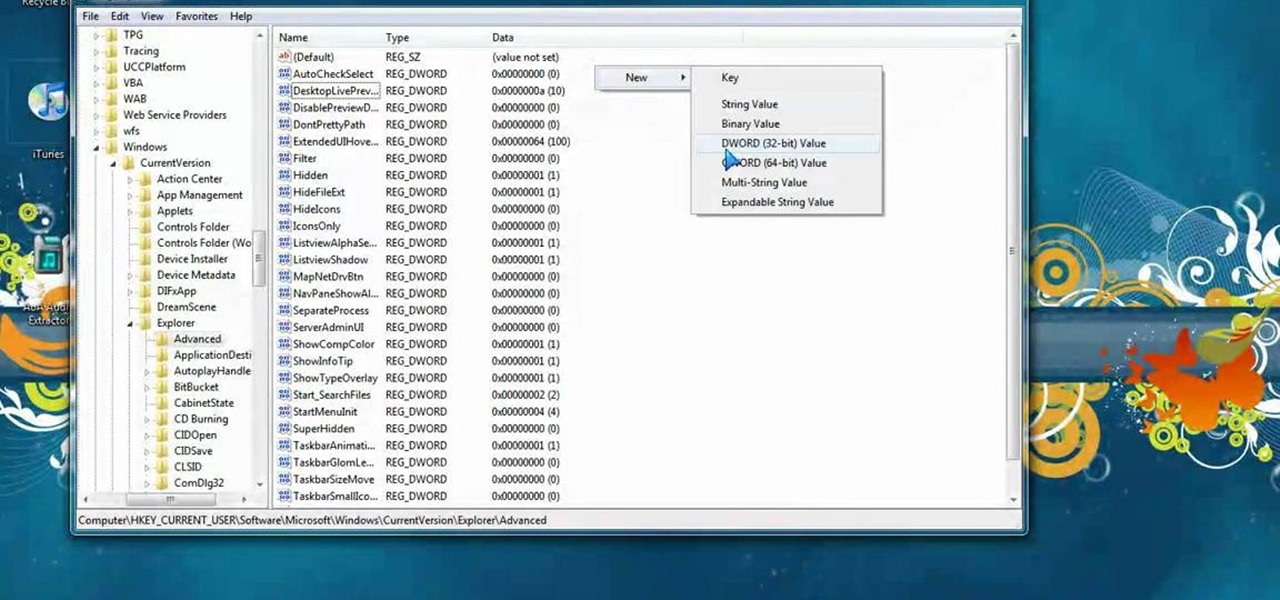
In this video, we learn how to tweak Aero Peek and Desktop Live Preview on Windows 7. First, go to registry editor, then current user, then software, then Microsoft, and go down to Windows. After this, click on current version, explorer, and advanced. Now, right click on the white space and click "new keyword value" and name it "desktoplivepreviewhovertime". After this, double lick and change it to decimal, then change the value data to 10. Next, create another keyword value and name it "Exte...
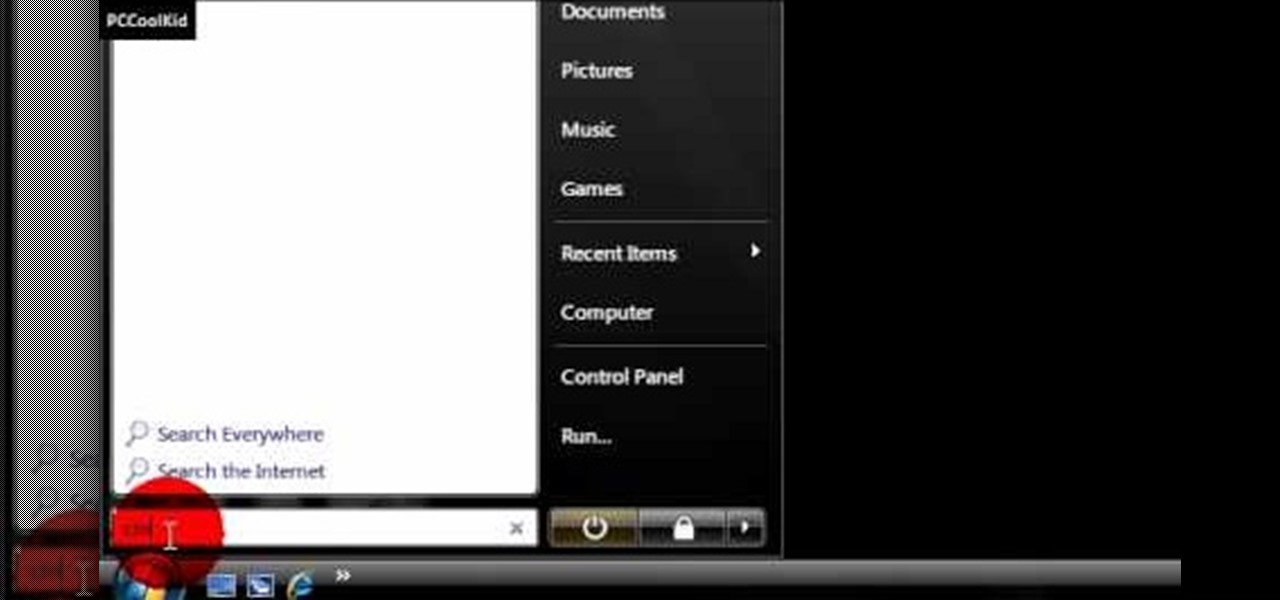
In this video, we learn how to enable the Windows default administrator account to appear at the log in screen. First, go to your "start" menu and type in "cmd". Right click "cmd" and click "run as administrator". Now click continue and type in "net user administrator /active:yes", (making sure you put the appropriate spaces), and press enter. Now it will say your command was done successfully on the space underneath where you just typed your text. When you restart your computer you will now ...
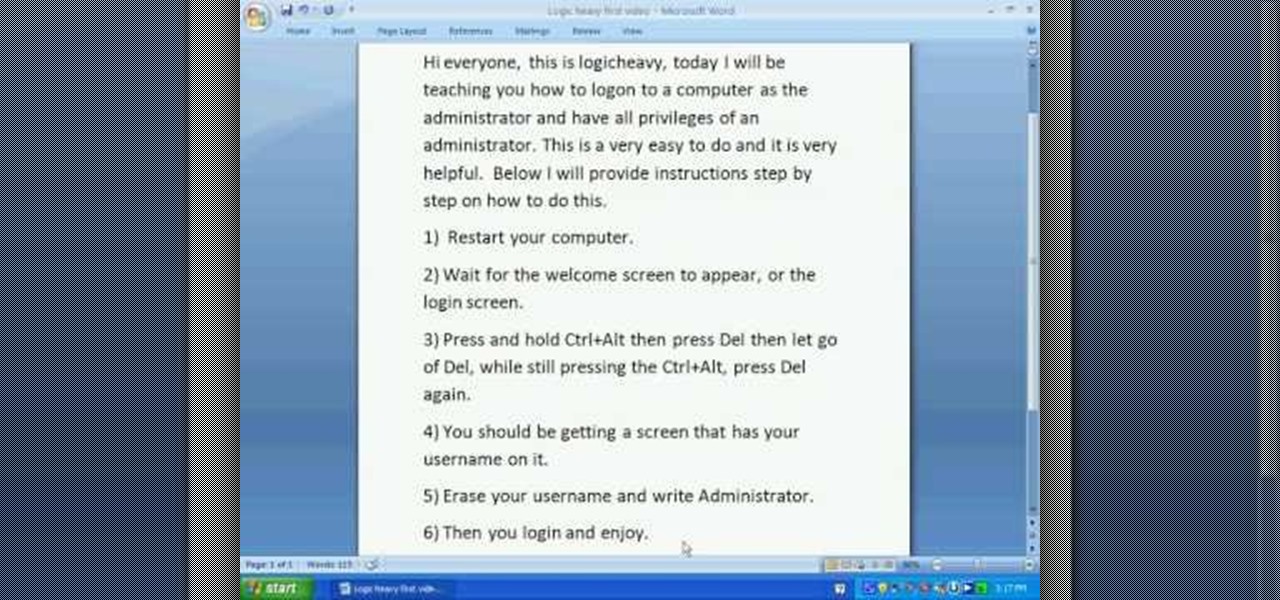
The video starts with a guy talking while we see a computer screen with instructions on how to log in as an administrator of your Windows XP Personal Computer.
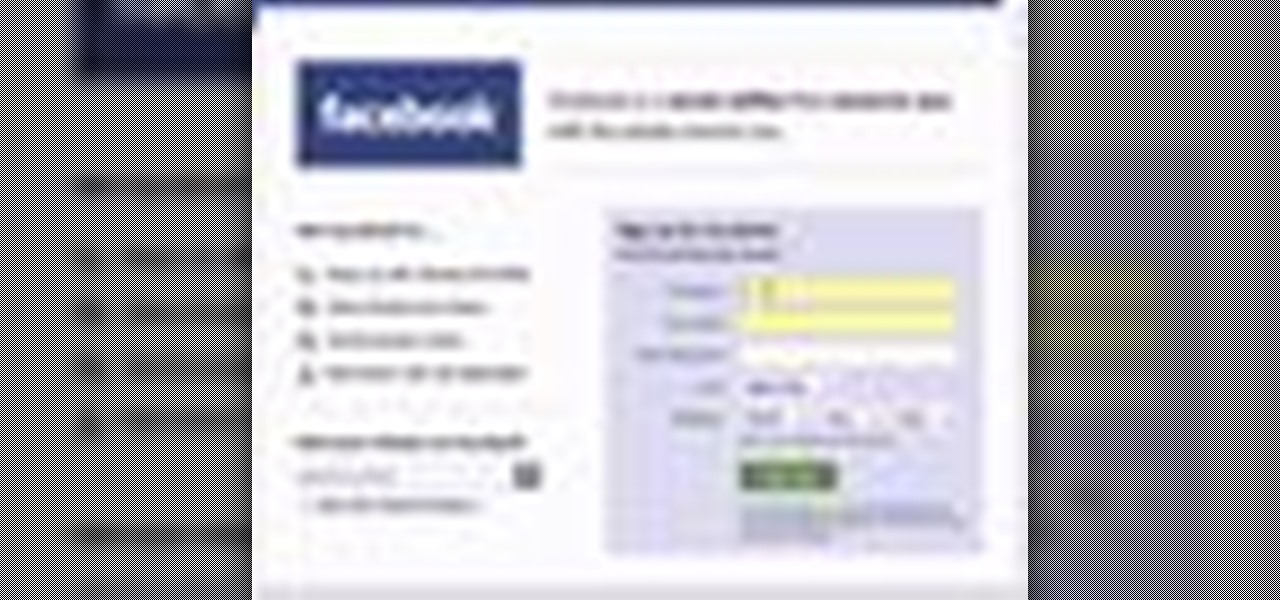
Start out by going to www.Facebook.com. From this page you will be able to create your own personal Facebook profile. Fill in your name, email, password, sex, and date of birth. Click 'Sign up' after you have filled in all of this information correctly.

Minecraft is such an incredible game that it allows players to create other games within their Minecraft servers. Here is one that is particularly fun. This is Blockey. Watch this video to learn how to build your own Blockey arena and get started playing.
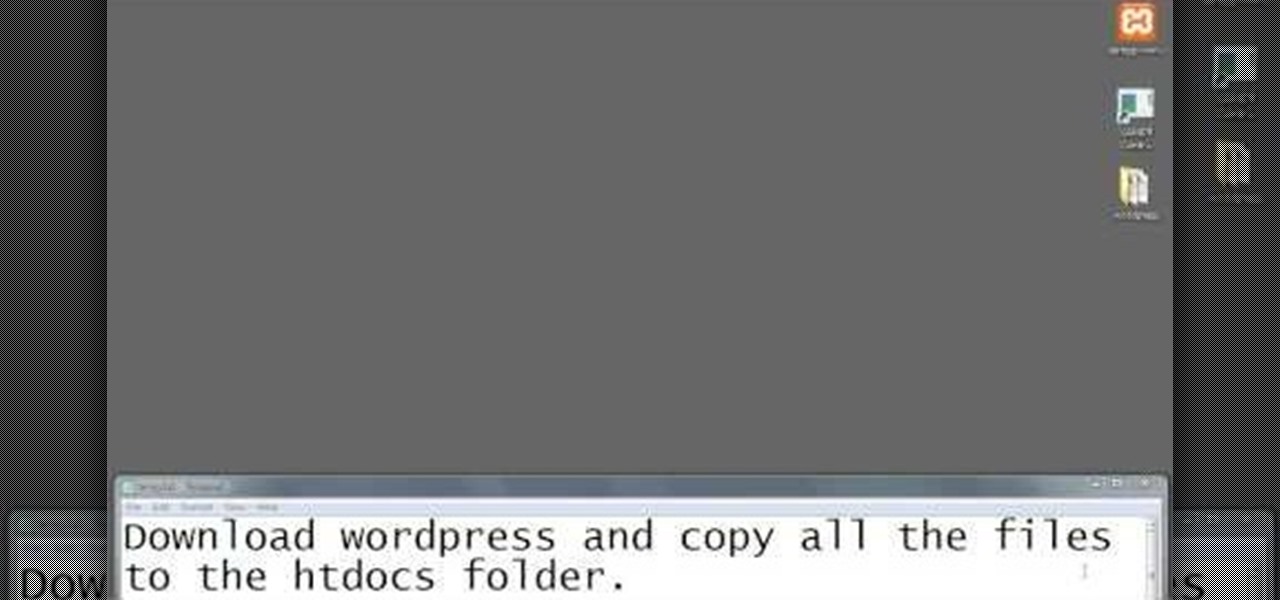
So you want to start your own website / blog / forum / web empire. Good, at least you aren't getting into financial services! This video will show you how to install three important programs that will help you get started: XAMPP, Wordpress, and MyBB. These programs will help you set up your web server, blog, and forum respectively, three important tool that you will need to use effectively to become a force on the web.

Got banned from a website you love to torment? Well, there's a way to keep it going. You can get back onto a site by changing your IP to get past the servers. This will only work if your IP is banned. If your username is blocked directly, you will have to find another way.
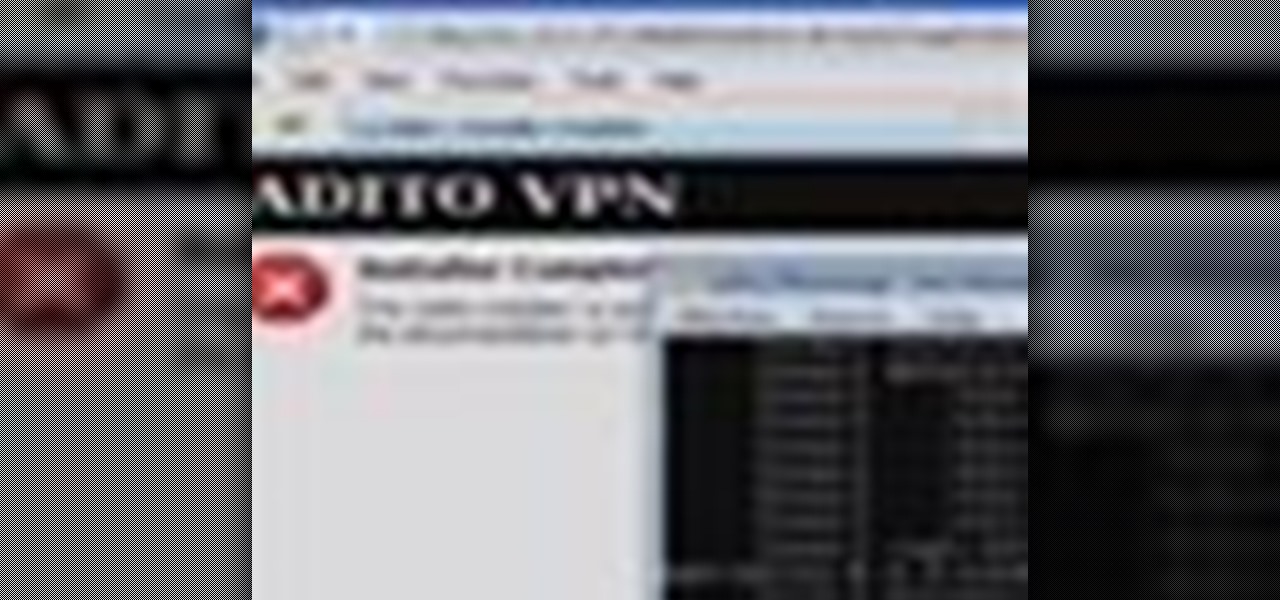
This time on the show, bypassing restrictive firewalls with a free and open source virtual private network server for Windows and Linux that will have you connecting back to the home or office with just a web browser! Best of all? It's free! Check out this video for detailed information on how to build an SSL VPN.

Welcome to a tennis lesson from FuzzyYellowBalls, the the best place to learn how to play tennis online. Our free video tennis lessons teach you how to play the game in a new way that combines technical analysis, visual learning, and step-by-step progressions.

A lag switch allows you to cheat in online games or on XBOX LIVE by disabling the flow of data to your console or PC. We will show you how to build one.

Some governments and organizations employ proxy servers to filter web content, permitting access to some web sites while blocking others. Here are several ways to get around these censorship policies. This is employed in China with YouTube and many other voices of anti-goverment ideas.
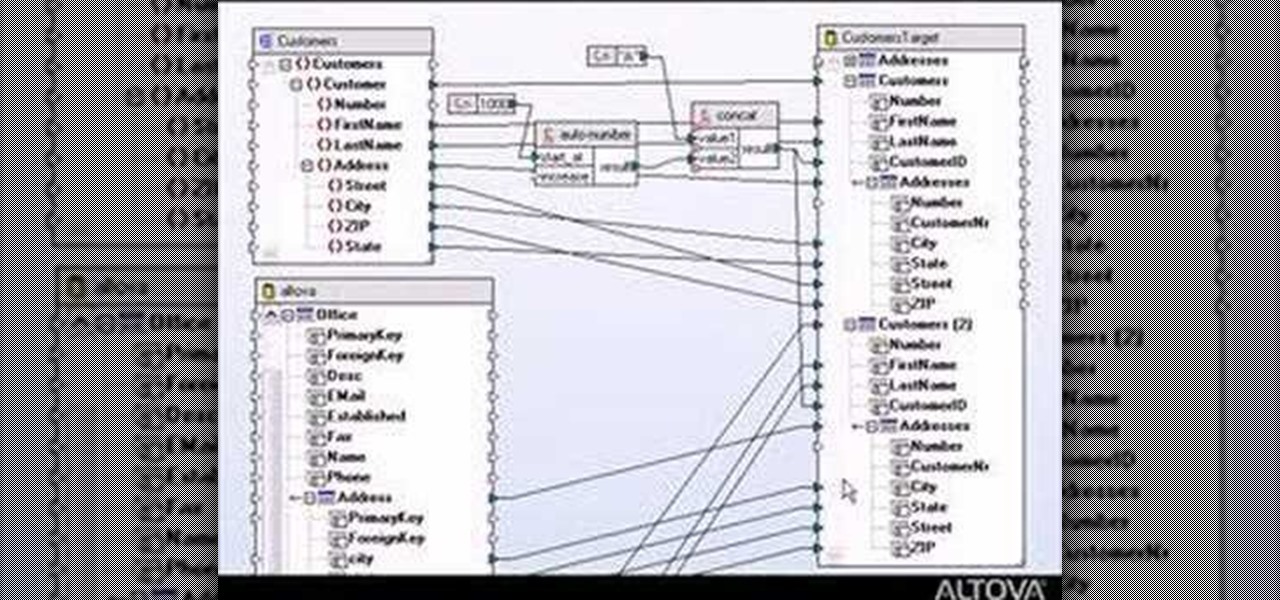
Designing a data mapping project in MapForce? The output functions in MapForce let you preview textual or XML output, save it to disk, or look at SQL statements for database output before committing them to the database server. Learn how in this tutorial.

Apple released the third public beta for iOS 13.5 today, Wednesday, May 6. This latest public beta update comes exactly one week after Apple released iOS 13.5 public beta 2, which, among other things, introduced Apple and Google's joint COVID-19 exposure notification API. Public beta 3 updates that settings page to show a more detailed "Exposure Logging" option instead.
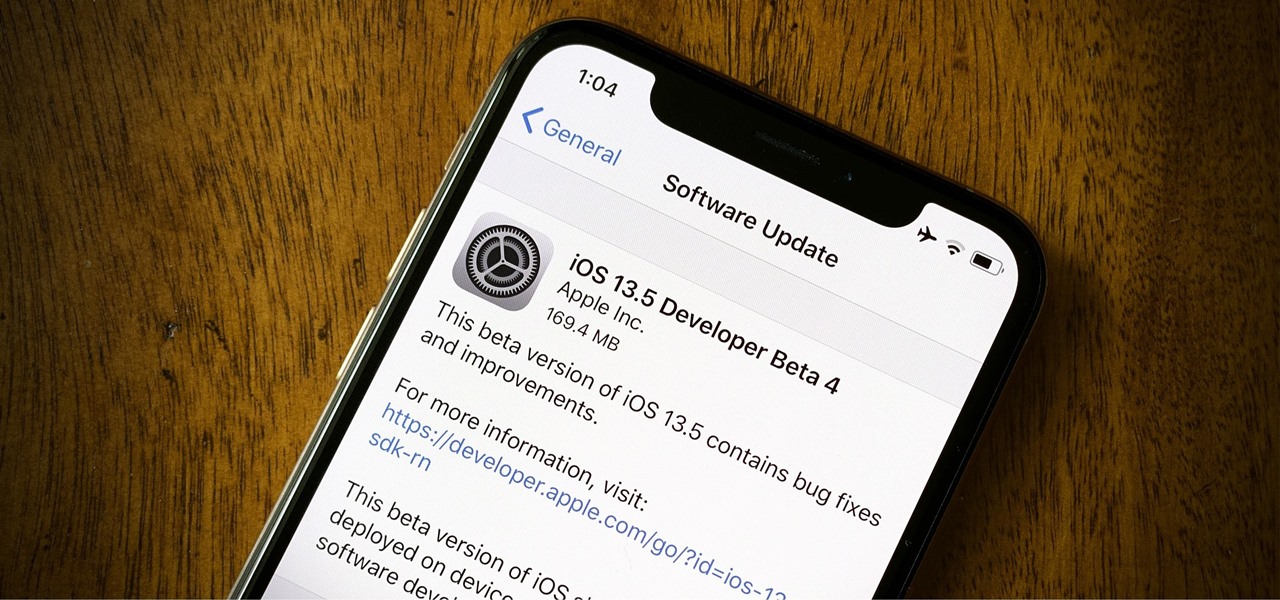
Apple released the fourth developer beta for iOS 13.5 today, Wednesday, May 6. This update comes one week after the release of iOS 13.5 dev beta 3, which introduced Apple and Google's joint COVID-19 exposure notification API to iOS for the first time. Apple updated that settings page to now include an "Exposure Logging" setting instead.

Samsung, like other OEMs, partners with third-party companies to include their apps on Galaxy devices. For example, Microsoft pays Samsung millions to pre-install certain Office apps. But one of these partners might not be on the up and up.

If you're worried about the security of your Mac, there are easy measures to prevent the most dangerous attacks. Named after the tactic of accessing an unattended computer in a hotel room, we can thwart "evil maid" attacks with Do Not Disturb and LuLu, free macOS tools by Objective-See that keep an eye on unattended computers and flag suspicious network connections that indicate a malware infection.

A hacker with privileged access to a Windows 10 computer can configure it to act as a web proxy, which allows the attacker to target devices and services on the network through the compromised computer. The probes and attacks appear to originate from the Windows 10 computer, making it difficult to detect the attacker's actual location.

One of the ultimate goals in hacking is the ability to obtain shells in order to run system commands and own a target or network. SQL injection is typically only associated with databases and their data, but it can actually be used as a vector to gain a command shell. As a lesson, we'll be exploiting a simple SQL injection flaw to execute commands and ultimately get a reverse shell on the server.

Screenshots taken from a compromised computer can provide hackers with access to private emails, photographs, and information found in sensitive documents. This data can be used by the attackers to build profiles of a target for social engineering attacks and blackmail or even just to release the information out in the wild.

For years, PuTTy has reigned supreme as the way to establish a Secure Shell (SSH) connection. However, those days are numbered with the addition of the OpenSSH server and client in the Windows 10 Fall Creators Update, which brings Windows up to par with macOS and Linux's ability to use SSH natively.

Backdoors are convenient to leave behind once you've already found a way into a server, and they can come in handy for a variety of reasons. They're good for developers who want a quick way into machines they're working on, or for systems administrators who want similar access. Of course, backdoors are also a hacker's best friend, and can be added in a variety of ways. One good tool for doing this is Weevely, which uses a snippet of PHP code.

When it comes to sharing files between a smartphone and a computer, there are several solutions available for a Windows and Android pairing. But for those of us with Apple devices, the selection of apps in this category isn't quite as great. You can use AirDrop to quickly share files, but searching for files is not so easy.

Welcome back everyone. I apologize for the lack of training articles, but I've been rater busy lately. I've recently picked up a second job and my college courses are now back in session, so I'm a bit strapped for time.

In this series you will learn how to use PHP to perform attacks, gather information, and setup backdoors. Along with performing attacks you will learn how to protect yourself from them. In this part you will learn about PHP as well as install Apache and PHP. What you'll need for this series

Hello aspiring hackers, It's been a while since I wrote a tutorial, so I figured I might just share one of the tools that I have created to help the community grow.
Greetings null-bytians. Say you have been able to penetrate your neighbour's AP, and of course you had spoofed your MAC address. Now you go on and test to see with excitement if the password really works and the MAC is still spoofed. You login successfully and you browse the web forgetting to check what your current MAC is. Well, if you may do an ifconfig command, you will see that your permanent MAC is being used. Oh!! and guess what, ... your real MAC has been logged. Even though there is t...

There are few things more satisfying than fulfilling a craving with instant gratification. Companies like Pillsbury and have made this possible with the introduction of their famous Ready to Bake Cookies line: just rip open the package, break off the cookies along the creased lines, place on a cookie sheet, and bake.

Some people are of extremely secretive nature. They do not like sharing their personal events in their lives with anyone. Thus people around that person wont be able to figure out details on their life's personal matters. It is not like they want to hide some mysterious secrets from the world, but it is just their nature that they do not want others to know much about them or are too shy to share their feelings with others. Being secretive is neither good nor bad, it is just how they are.

Welcome back, my greenhorn hackers! Earlier in this series, I showed a you a couple of different ways of fingerprinting webservers. Probably the easiest way, is to use netcat and connect to port 80 and pull the webserver banner.

Welcome back, my budding hackers! One of the keys to becoming a professional and successful hacker is to think creatively. There is always a way to get into any network or system, if you think creatively. In previous tutorials, I have demonstrated ways to crack passwords on both Linux and Windows systems, but in this case, I will show you a way to get the sysadmin password by intercepting it from a Remote Desktop session.

Welcome to this short and easy tutorial on hacking and DDosing (is that even a word I don't know) anyways lets get started

This tutorial shows you how to get through the laser traps you'll encounter in Chapter 7 of Dead Space 2. The game in this walkthrough has been set to Normal difficulty, and also shows you where to find the logs on this level.
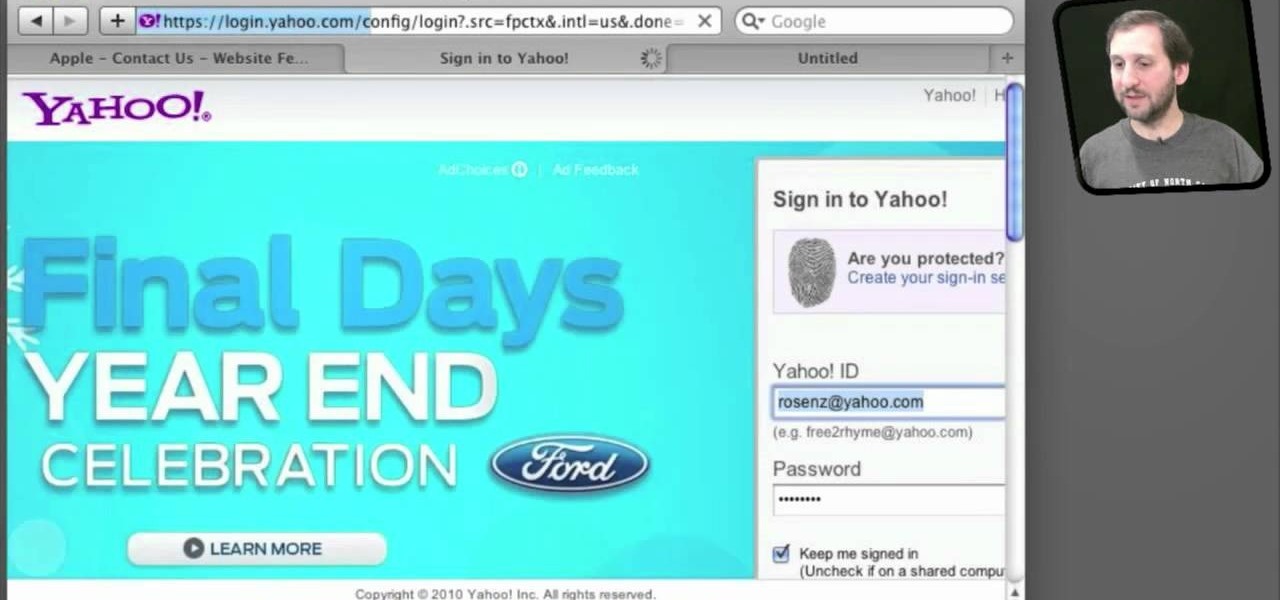
Use the AutoFill feature in Safari to quickly fill in web forms for sites that you visit again and again and save time when logging in. Form entry data is stored in your address book contacts, and from information you have filled out in web forms before. You can see the passwords used by AutoFill in the OS X keychain, and you can also specify and limit general access to those passwords.
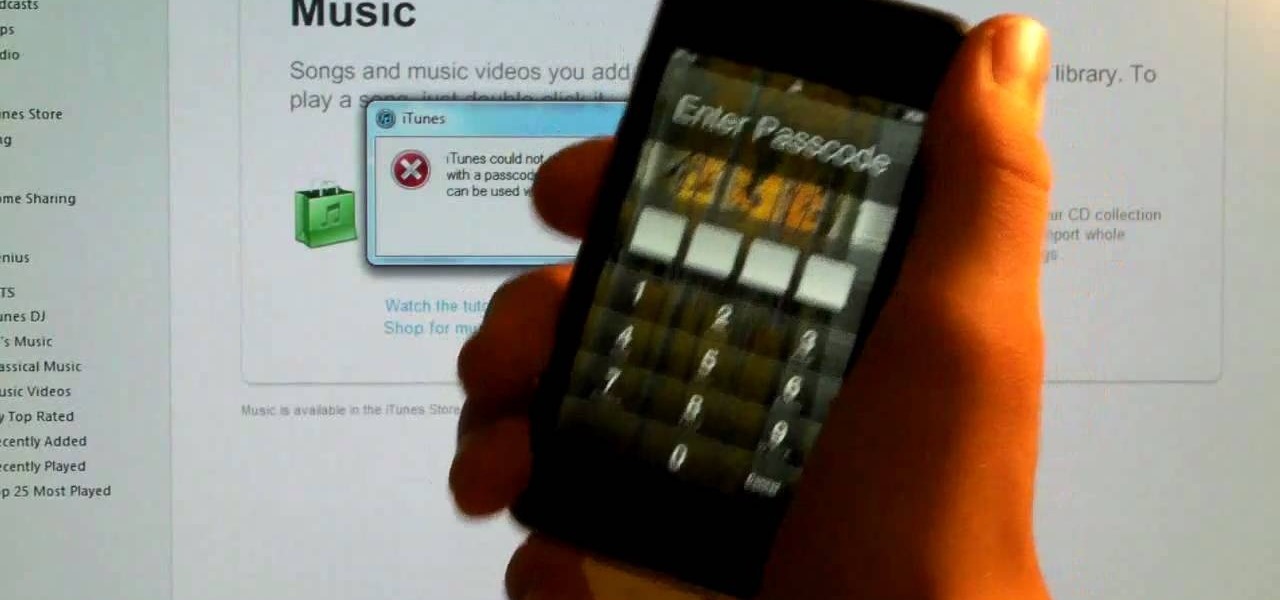
Remove the password on any iOS mobile device! This video will teach you everything you need to know to remove the log-in pass code from your iPhone, iPad or iPod Touch. For more information, including detailed, step-by-step instructions, and to try it out for yourself, watch this hacker's how-to.
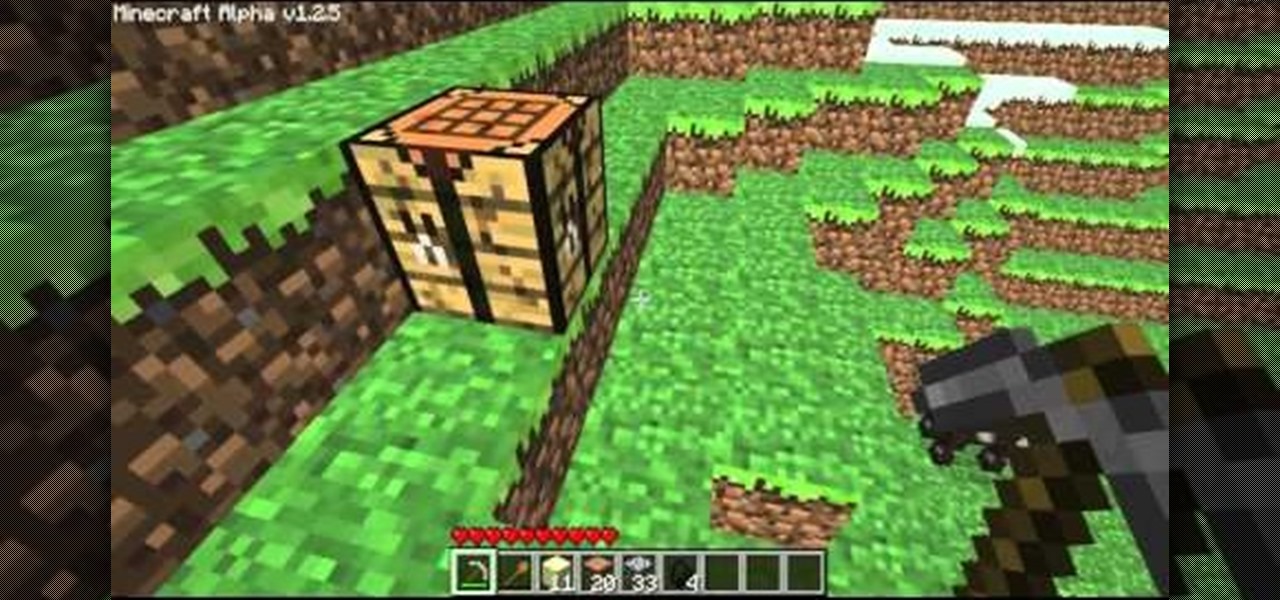
Your first night in Minecraft is the most perilous one, and you don't have to build just a simple shelter. There's enough time to build a complete house out of twenty-three logs, twenty-three blocks of sand, four blocks of coal and eighty-one blocks of stone.