Add a small bit of content which appears whenever visitors to your website mouse over a specific area of your website - such as having your company's slogan appear in a small text box when users hover their mouse over the log.

The Sparkle app for your iPhone or iPod Touch is a client which allows you to message your friends in Second Life without having to log fully into Second Life. Great if all you want to do is send someone a quick chat message without playing the game.
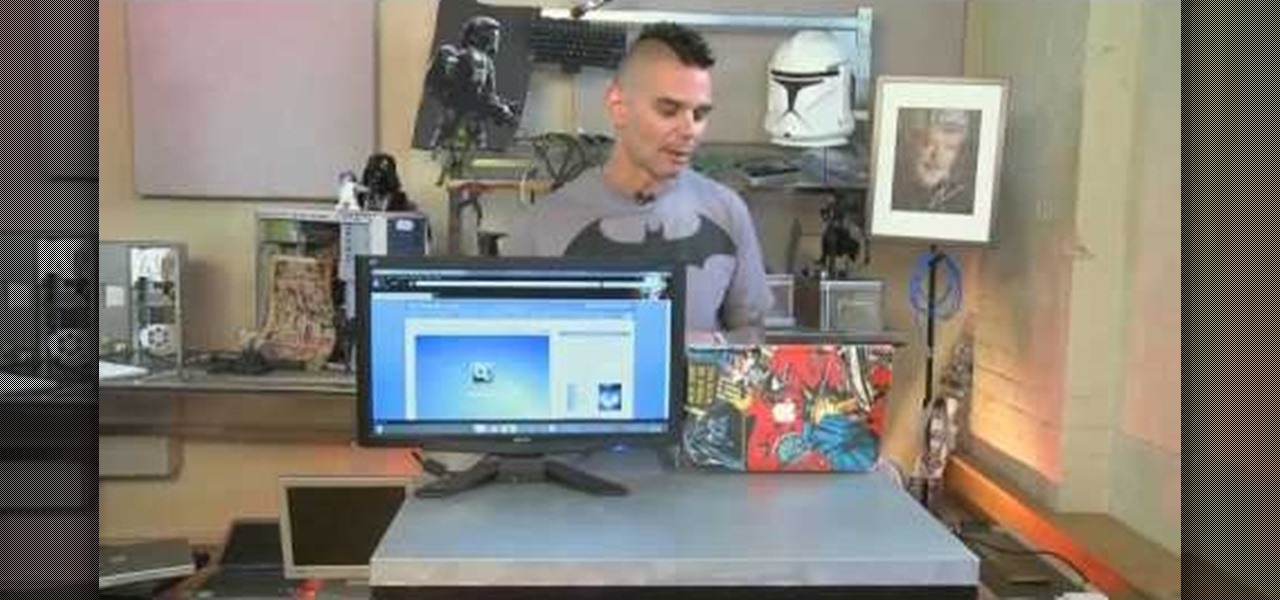
Looking for the easiest method of customizing the login screen on a Microsoft Windows PC? This brief video tutorial from the folks at Butterscotch will teach you everything you need to know. For more information, and to get started personalizing your own log-on screen, take a look.
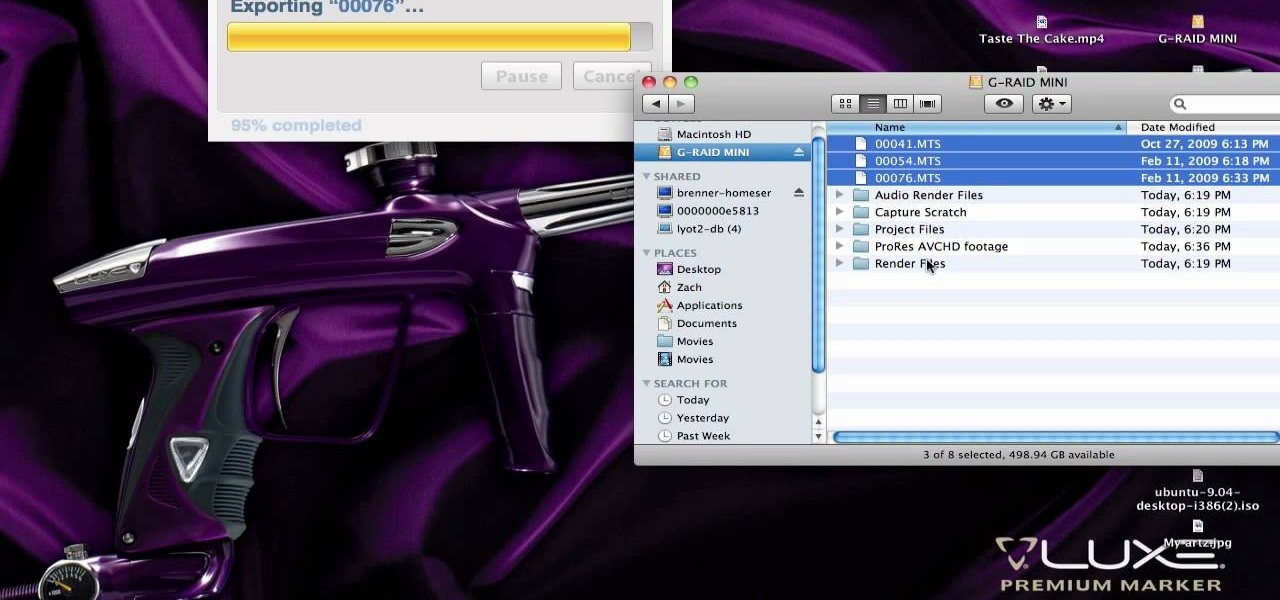
In this clip, you'll learn how to work with AVCHD files that can't be logged and transferred like MTS files. Whether you're new to Apple's Final Cut Pro non-linear video editor or just want to better acquaint yourself with the popular video editing program, you're sure to benefit from this video tutorial. For more information, including detailed, step-by-step instructions, watch this tutorial.
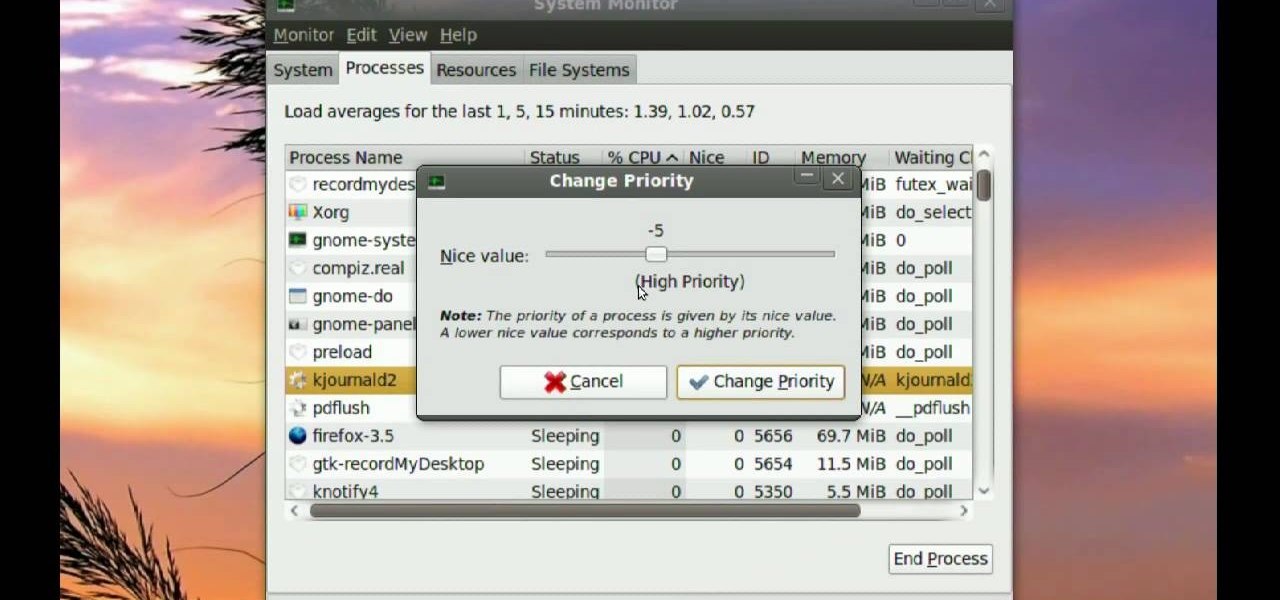
Ubuntu comes with pre-installed tools that can help solve problems you may encounter when using Ubuntu Linux. This video tutorial shows how to identify and address common problems in Ubuntu Linux. Such tools discussed include the system monitor, the log file viewer and the network tools.

If your not sure how to steam your media files to your Playstation3 this video will explain three different ways to achieve just this. Your options will include using a thumb drive, a personal web server or get the appropriate software.

In this video lesson of LEARN TO DRAW with Tom Gammill, where the creator of The Doozies discusses cartooning and the spirit of Christmas. Learn how to draw a cartoon santa claus using mostly circles and half circles. Towards the end of the video Tom teaches you how to make a holiday yule log too. Follow along and learn how to draw an easy cartoon Santa Claus.

Find lyrics to an unknown song by logging on to the Internet and typing in a few words from that song into a search engine. Locate lyrics to an unknown song with tips from a professional musician in this free video on music.

No need to spend money on fire starter logs and such items, with free lint from your dryer and some wax from a candle you can create a great item to start fires while camping, hiking and so on. Dryer lint and wax are both small and lightweight so they're easy to pack and carry around. Watch this video training tutorial and learn how to make flame fuel from dryer lint and wax.

Applications on the blink? In this tutorial, Gary Rosenzweig looks at various ways to force broken applications to quit. He also shows some handy keyboard shortcuts for logging out, restarting, shutting down and quitting instantly.

Epicurious Editor-in-Chief Tanya Wenman Steel demonstrates how to fill and roll up a genoise cake to make a jelly roll, a Yule log cake or bûche de Noël.

Learn how to log and capture movie footage in Apple iMovie so you can begin to transform your raw footage into a completed movie.

Don Schechter explains how to capture your footage from your camera to your computer and log it for easy access later on. You can use Adobe Premiere to capture your movie, but you can not forget to put your tape in your camera.

This covers using no-ip.com to set a dynamic domain name after you set up your own server. This makes the IP dynamic rather than static. It updates the domain name with your IP address so you don't have to. This is an informationleak.net video from Halla.

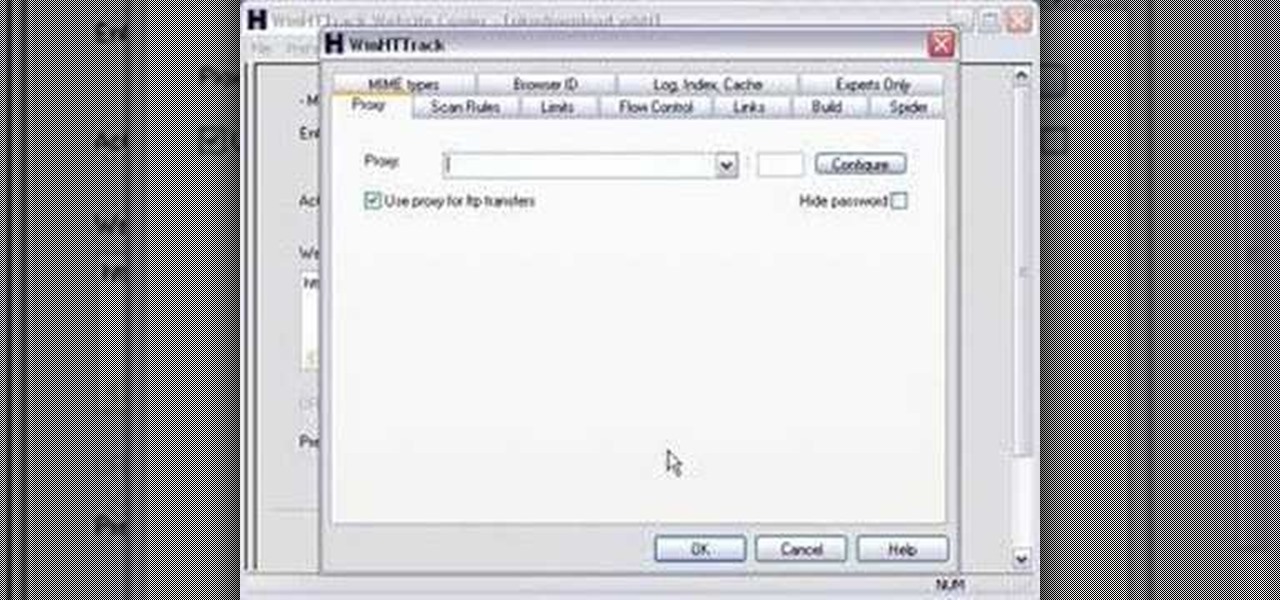
Here is a tutorial on using Httrack to download websites for off line viewing.Httrack is a website copier and 99% of the people on the web will use this software responsibly. This tutorial is for that 99%. Using Httrack is a great way to download a site you need to modify when the site server passwords have been lost.

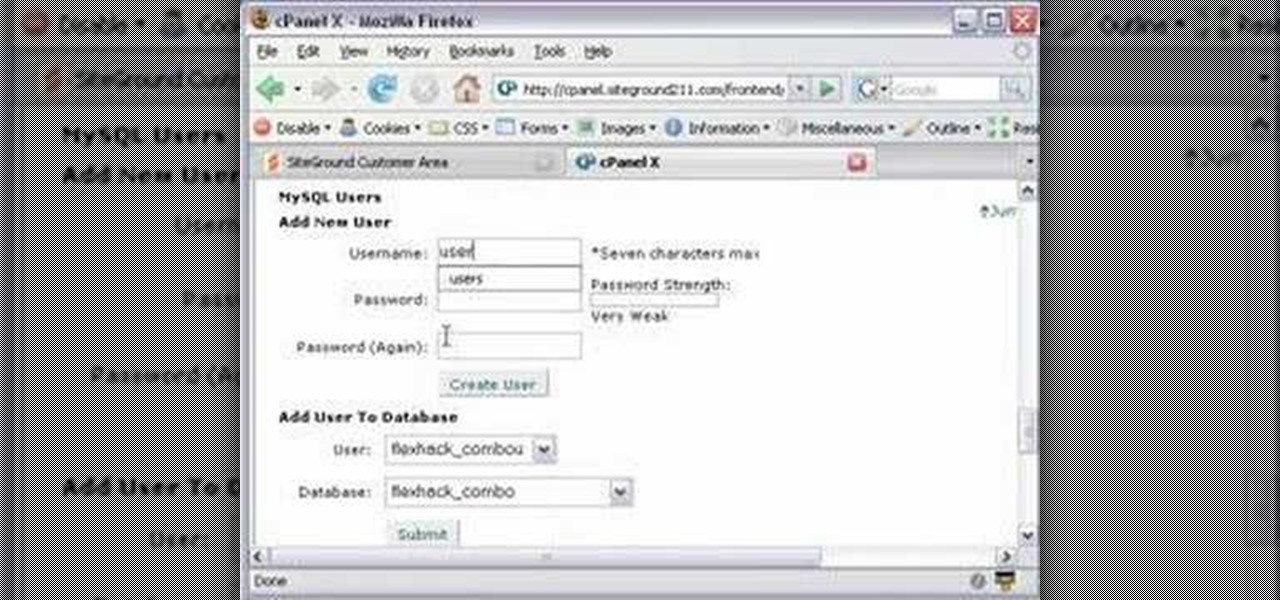
This CoffeeCup Web Form Builder software tutorial shows how to create a MySQL database to be used in CoffeeCup Form Builder to build web forms. Mike Lively shows you how to do this using cPanel and the Site Ground server for hosting since it allows an unlimited number of MySQL databases. Start by creating your database in cPanel and then upload the results to CoffeeCup Form Builder.

n this ASP.Net video lesson, you will explore the various ASP.NET 2.0 server controls available in Visual Web Developer 2005 Express Edition. In addition, you will begin to get familiar with the windows in VWD.

Can't wait until you get home to get onto MySpace? This video gives step by step instructions on how to try and unblock MySpace while you are at school or on a server that does not allow access to the site. This video does not have narration, but has written instructions on how to get around blocked sites with out using a proxy server. However, you have to have access to the system 32 files for this tutorial to work, and accessing these files does go against a lot of network policies.

If left unattended, a hacker with a USB Rubber Ducky and physical access to the computer can infiltrate even the most secure computer. Such attacks often go undetected without the use of a tool like USBRip, which can provide you with assurance that your device hasn't been compromised.

Information gathering is one of the most important steps in pentesting or hacking, and it can often be more rewarding to run things on the target itself as opposed to just running scripts against it remotely. With an SQL injection, a hacker can compromise a server and, ultimately, upload and run the "unix-privesc-check" script locally in order to further identify possible attack vectors.

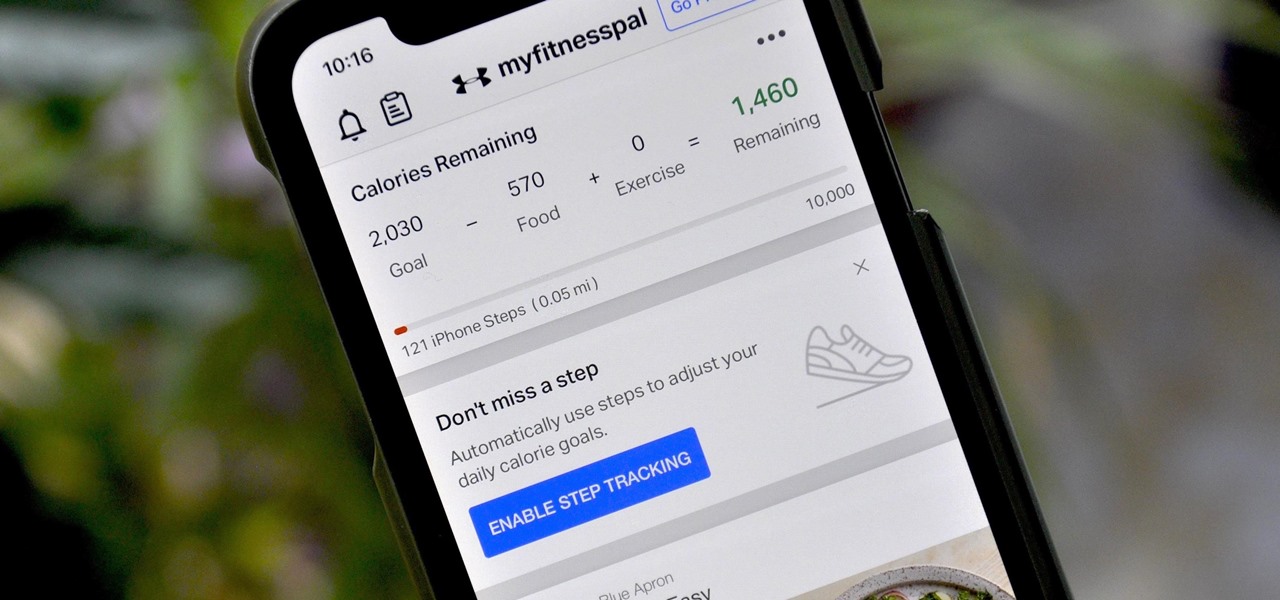
If you're new to MyFitnessPal, it might seem daunting. The app is way more than just a calorie counter, but that's because getting fit is just as much about changing your lifestyle as it is about watching what you eat. So don't let it overwhelm you — there are just a handful of tips you should know to hit the ground running.

Two-factor authentication (2FA) is a great way to add another layer of security to sensitive third-party apps and websites like Venmo. However, before iOS 12, to log into a particular 2FA-secured app or site on your iPhone, you'd have to memorize or copy the SMS code from Messages, then jump back in a timely manner to log in. Apple's latest iOS version streamlines this process.

Telegram routinely boasts about its secure messaging for truly private conversations between two parties. However, default cloud chats in Telegram are only encrypted between client and server, not client and client, which means you have to be a little proactive in making sure your private conversations on Telegram are really private.

The peaceful, pastel and doily-filled world of Pinterest is my oasis. My account conveys who I want to be and what I want to accomplish, so the idea of someone hacking it and ruining my favorite escape for me is heartbreaking. Fortunately, Pinterest has updated its security, implementing three new features to hack-proof your account.

WordPress did not become what is arguably the most popular blogging and CMS platform on the planet because it was difficult to use. Rather, its user-friendly and rich feature set led to it finding a home on somewhere north of 70 million websites—and that's just counting blogs hosted on WordPress.com.

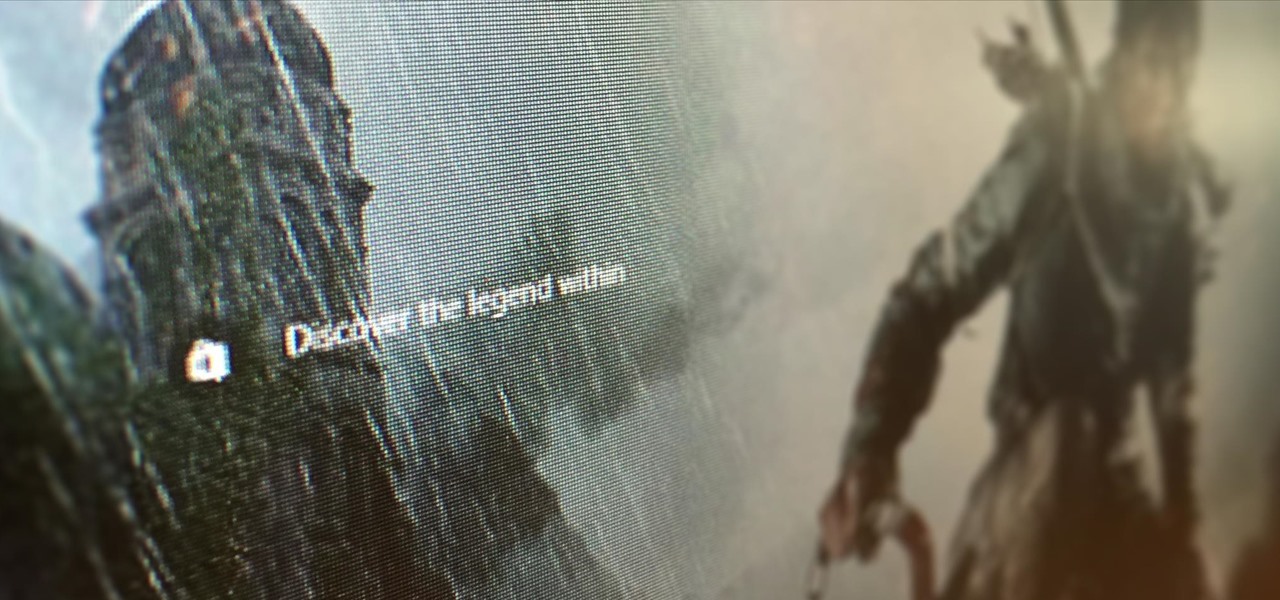
For the past three or four months, Microsoft has been pushing advertisements onto the lock screens of some Windows 10 users as part of its "Windows Spotlight" feature. This feature normally shows you scenic photographs and gives you the option to learn more about them by launching an Edge window once you log in. However, the aforementioned users have reported seeing the image below for the new Rise of the Tomb Raider game. Rather than taking you online in Edge to learn about it, you're given ...

Welcome back, my greenhorn hackers! As all you know by now, I'm loving this new show, Mr. Robot. Among the many things going for this innovative and captivating program is the realism of the hacking. I am using this series titled "The Hacks of Mr. Robot" to demonstrate the hacks that are used on this program.

This is a short explanation and tutorial on how to grab saved passwords from Google Chrome, ideally from a meterpreter session. The idea behind this is to understand how saved passwords work and how to keep them safe. Let's have some fun :D Understanding Google Chrome Saved Passwords

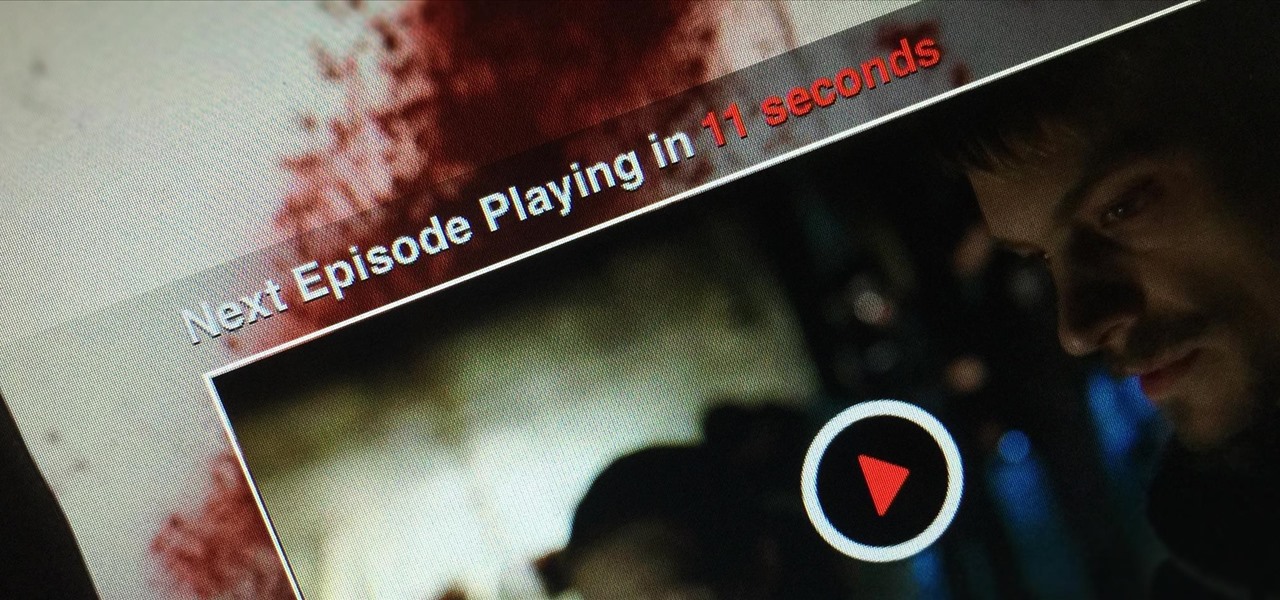
Netflix is an enabler. It creates a joy around binge-watching and couch potato-ness, and the major contributor to this epidemic is its built-in "Post-Play" feature.

While you may suck at Instagram, it's likely that you manage multiple Instagram accounts, whether strictly for personal use or for managing blog and business pages.

If I'm in a hurry, sometimes I'll just turn my computer off and rush out of the house. Sometimes, I'm in the middle of a long YouTube video when I dash off, only to come back and find that my video position has been tragically lost. Hopefully I don't lose my place in that motorcycle accident compilation video when I get ba... damn it.

There are a number of reasons why you might want to trick a web server into thinking you're on a different operating system (OS) or web browser. One might be that you want to test the mobile version of your website from your computer. Or perhaps for some reason a website is restricted to a certain OS or browser and you wish to circumnavigate that barrier. Today's guide shows you how to do just that!

Apps are now very much integrated with social media, especially with your Facebook profile. Pretty much every app these days lets you log in using Facebook, while some actually force you to, giving you no other option. But, the most annoying part is that these apps leave notifications all over your Facebook timeline, cluttering the hell out of it. So, how can you completely banish all of these apps from being able to access your Facebook?

For people that live outside of the United States, how many times has this happened when surfing through U.S. streaming services? If you're outside of the U.S. market and want to stream stateside services like Hulu, MTV, CBS, Pandora, and others—you're in luck. Tunlr is an application that re-addresses certain data envelopes, tricking the receiver into thinking the data originated from within the U.S. by using its own DNS server's IP address. You can even watch some non-US shows stateside, li...

Okay, it's not actually cake-powered, but it does use cake! Owing to the fact that cake and trapdoors are less than half a block tall, we can use fenceposts (which are a block and a half tall) attached to pistons to push people along, because the tops of the fenceposts will invisibly pop up through cake and trapdoors.

Dropbox announced Tuesday that a recent security breach compromised a list that included the email addresses of certain Dropbox users. To avoid future complications, the service announced that it would be implementing two-factor authentication, and even more useful, a security page that lets you monitor all activity on your account. In light of this and other recent web security threats, you might also want to know that services like Gmail, Facebook, and Yahoo! Mail have similar pages where y...

If you want to learn how to serve in tennis this is for you. The serve is the most important aspect in the game because the server has complete control. You have two attempts to serve the ball; if both attempts hit outside of the service box the server double faults and their opponent receives a point. When you are serving the ball your front foot should be at a 45 degree angle and your rear foot should be parallel to the baseline. Your weight should be evenly distributed over both feet. The ...

If you have been looking for a way to get the popular Joomla Content Management system running on Windows with IIS, you may have run into many problems. In fact, many people spend days trying to get Joomla running on IIS and run into roadblock after roadblock. The problem is getting PHP, MySQL, Joomla and IIS to all play nicely together. As you search for solutions, it is easy to find part of the answer, but rarely do you find it all in one place... until now. In this video tutorial we start ...

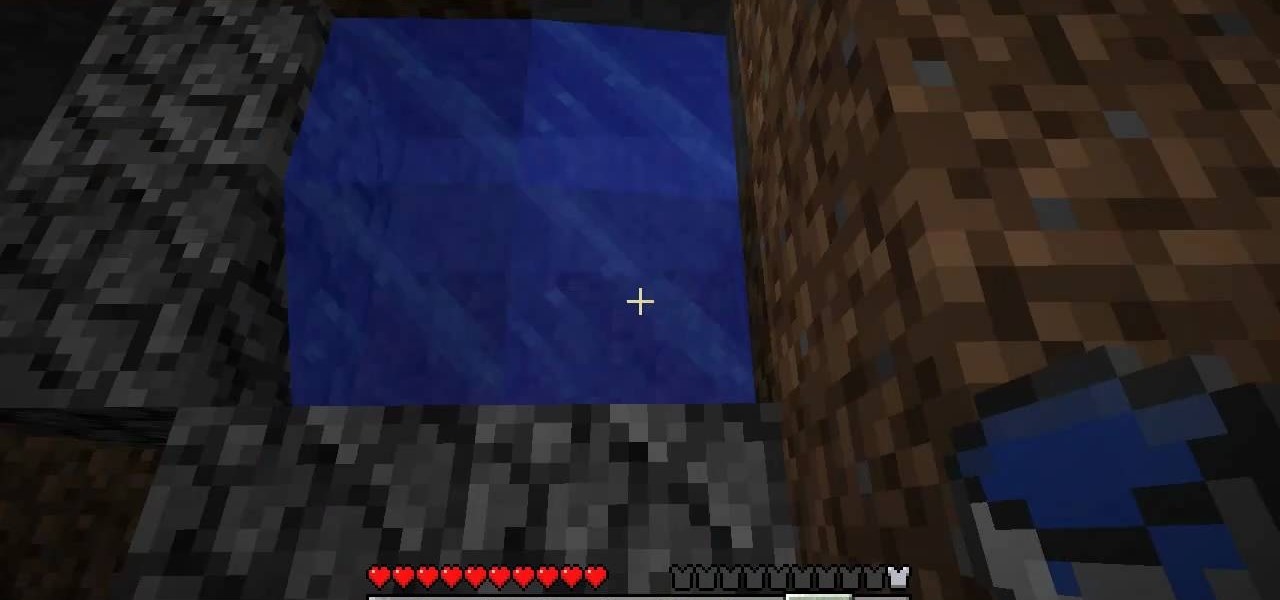
Without water, there is no life. That's the rule, and it applies everywhere- even on Minecraft servers. Check out this video to learn how to build a bucket and create an infinite water source in Minecraft. This will really come in handy.

So you know how to use a proxy server, but do you know how to set up a proxy chain? Proxy chains can be used to hide your tracks on the web. This video shows you how to use CGI and Tor to set up your own proxy chain.