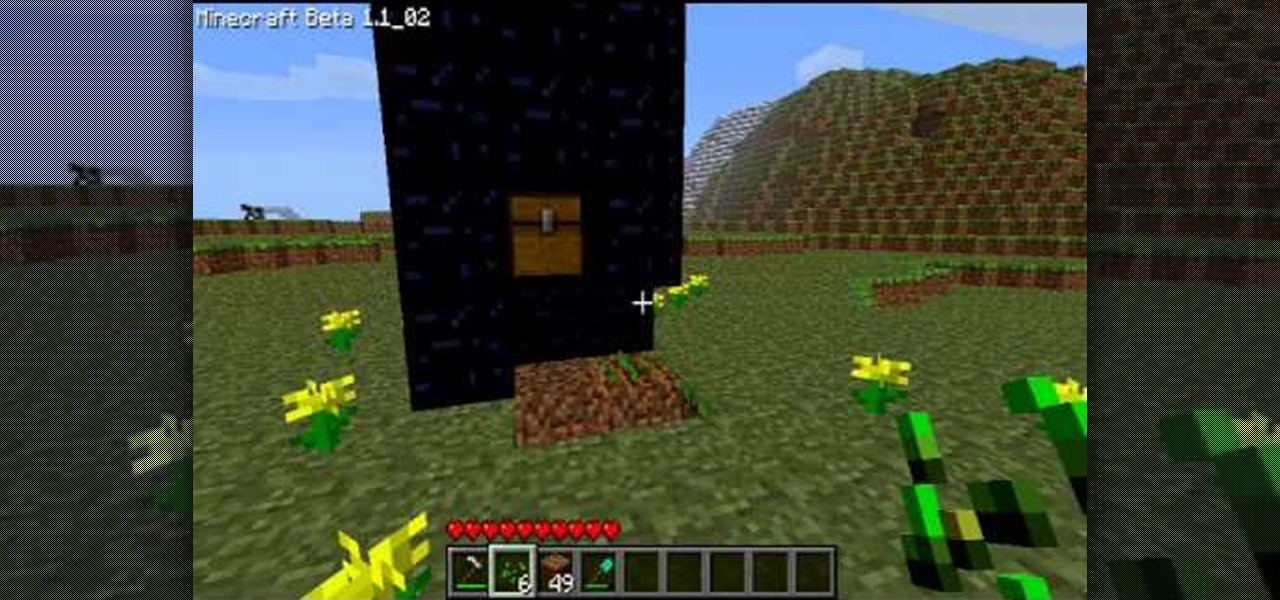
Even if there's a giant block of obsidian, you can figure out a way to exploit a glitch that will let you easily break into it. You're also shown a way to easily break into protected chests on shared servers in Minecraft.
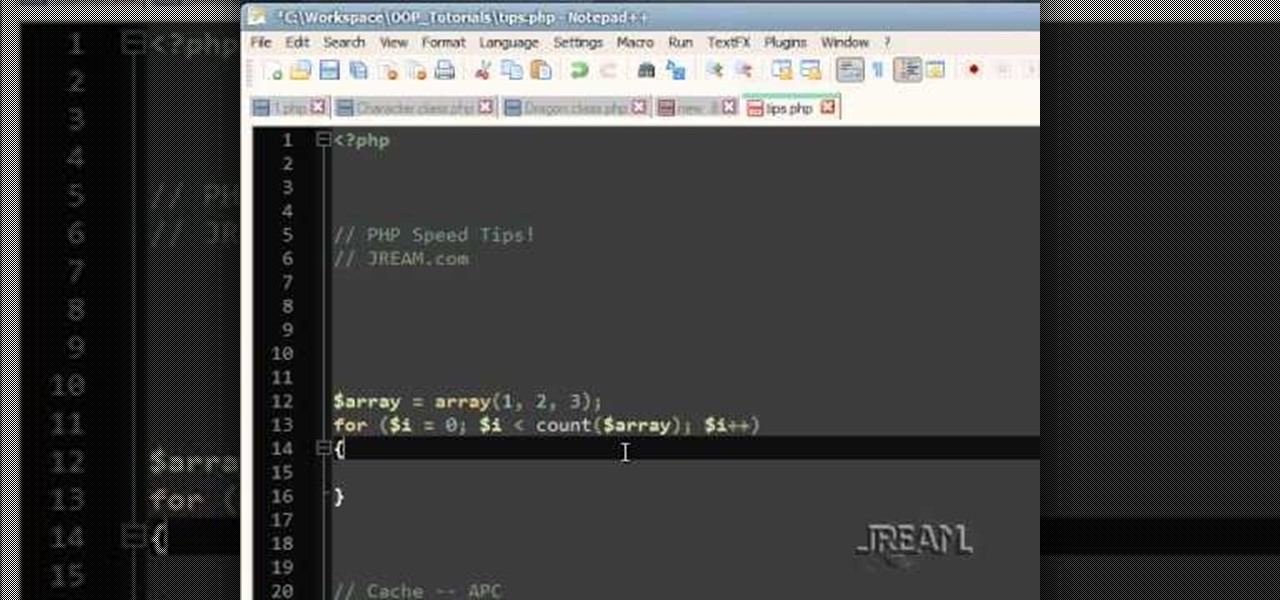
If you're looking to shave a few milliseconds off the Zend Engine's work load, check out this tutorial for some PHP programming speed tips. This efficency will pay off when you have tons of traffic to your site and save you valuable server resources.

Creepers and zombies aren't very smart, but if you're on a multiplayer server for Minecraft, you're going to want to be able to protect your stuff! Here is how you can construct a locking door using cobblestones, an iron door and redstone.
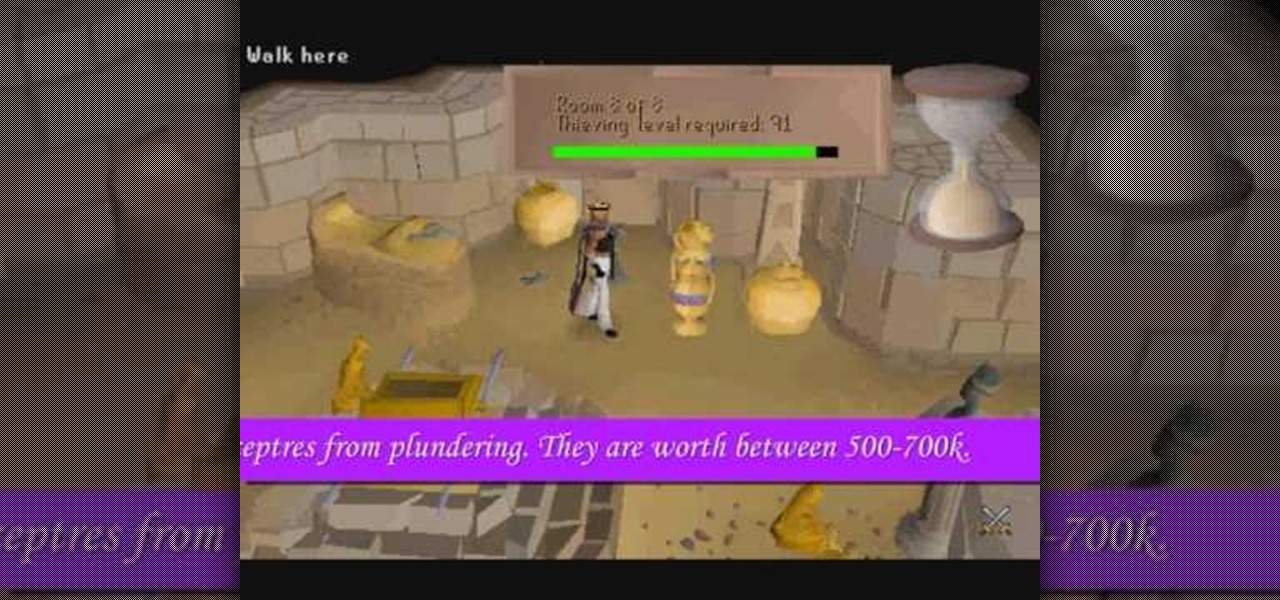
Become the best at thieving of anyone else on your RuneScape server! Starting as just a level one Pickpocket, this guide shows you how to take your character all the way up to level 99 in thieving! Everyone had better watch their belongings around you.
Become a juggernaut of destruction on your server when you play the free online game Sherwood Dungeon! This cheat shows you how to hack the game so you become invicible! You will need the latest version of Cheat Engine to be able to do this.

In this clip, you'll learn how to install the Joomla content mangement system on GoDaddy. It's an easy process and this home-computing how-to presents a complete demonstration. For more information, including detailed, step-by-step instructions, and to get started installing Joomla on your own GoDaddy webserver, take a look.

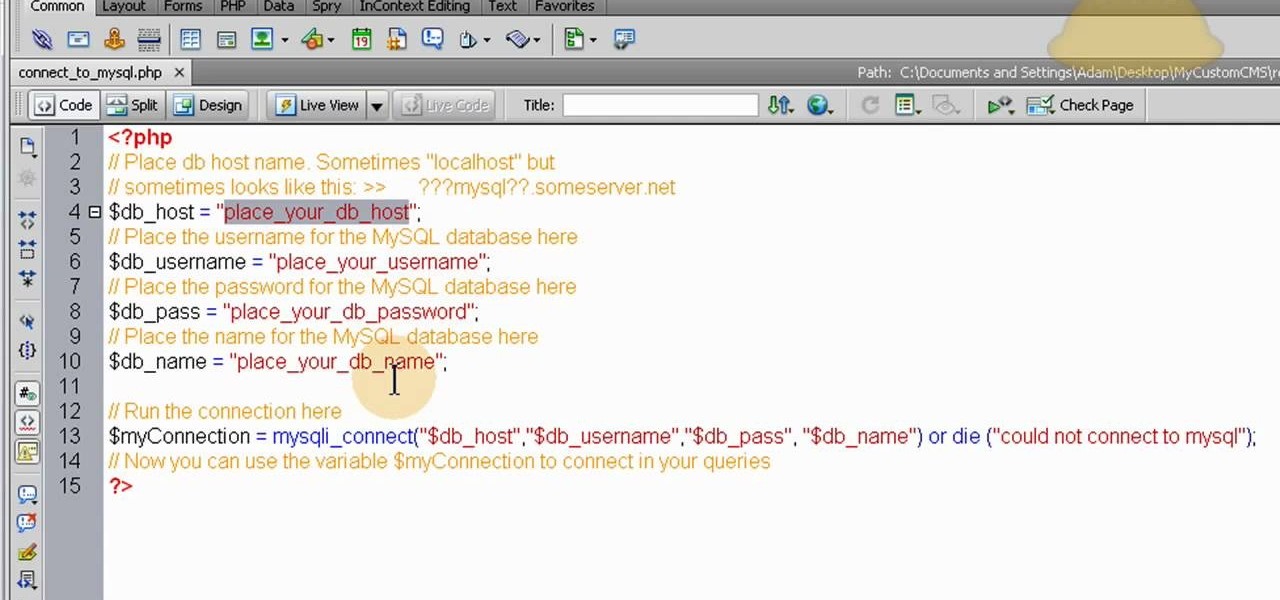
This is a video aimed at those who are just starting to set up their own website. You're going to want to begin with creating a MySQL database on your server, and then set up a default layout in Dreamweaver, which you can then customize to your liking.

While the PlayStation 3 is great at playing BluRay discs, if you want to play back downloaded videos, it can prove to be quite problematic. Use this software hack to unlock the Play Station 3 for video playback, whether it be from a hard drive or streamed off the internet.

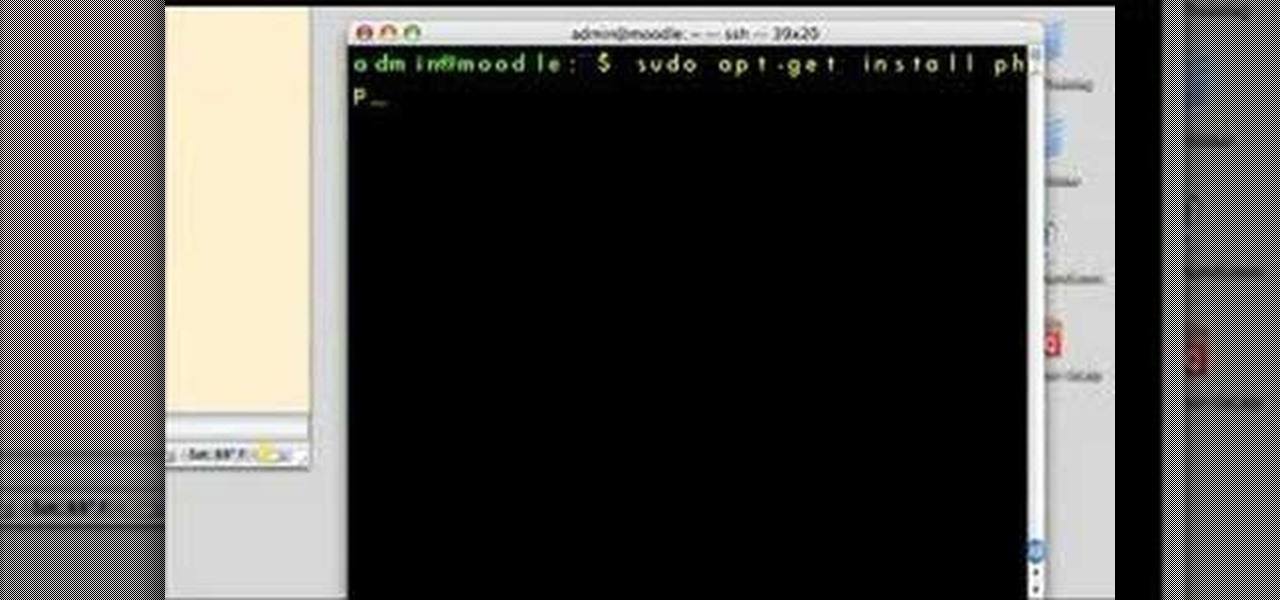
Interested in teaching an online course using your own server but can't quite figure out how to install everything you'll need? This video demonstrates how to sinstall the PHP GD Library for Moodle, the free, open source course management utility, via SSH. For exhaustive, step-by-step instructions, take a look.

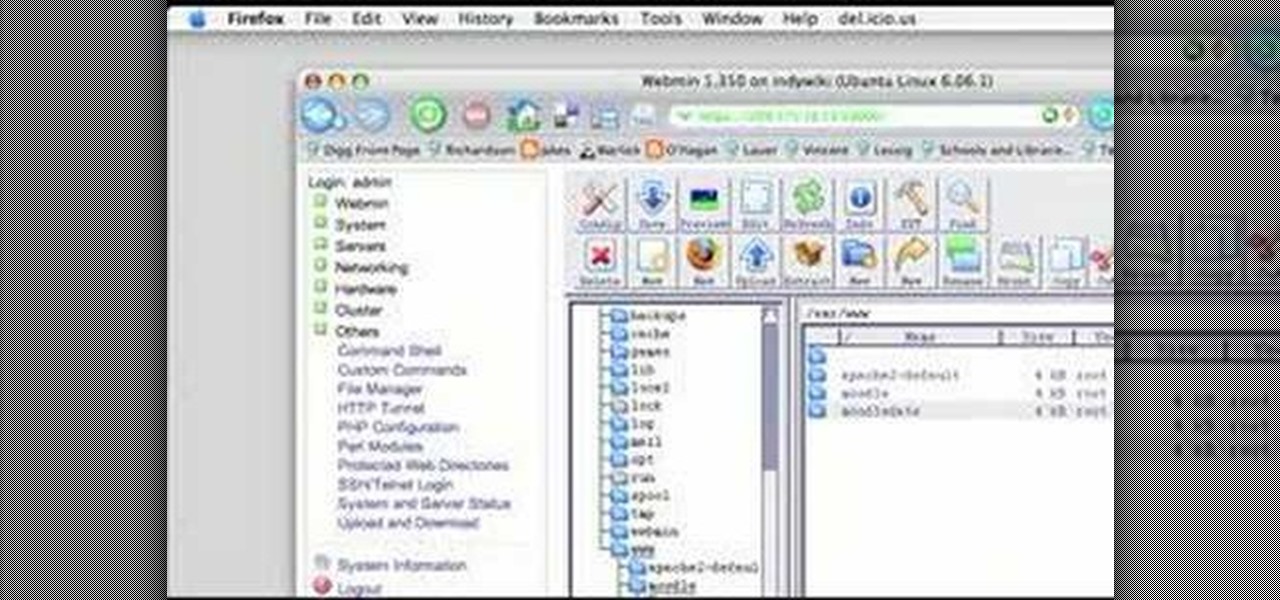
Interested in teaching an online course using your own server but can't quite figure out how to configure everything? This video demonstrates how to adjust folder settings within Moodle, the free, open source course management utility, via the Webmin interface. For step-by-step instructions, take a look.

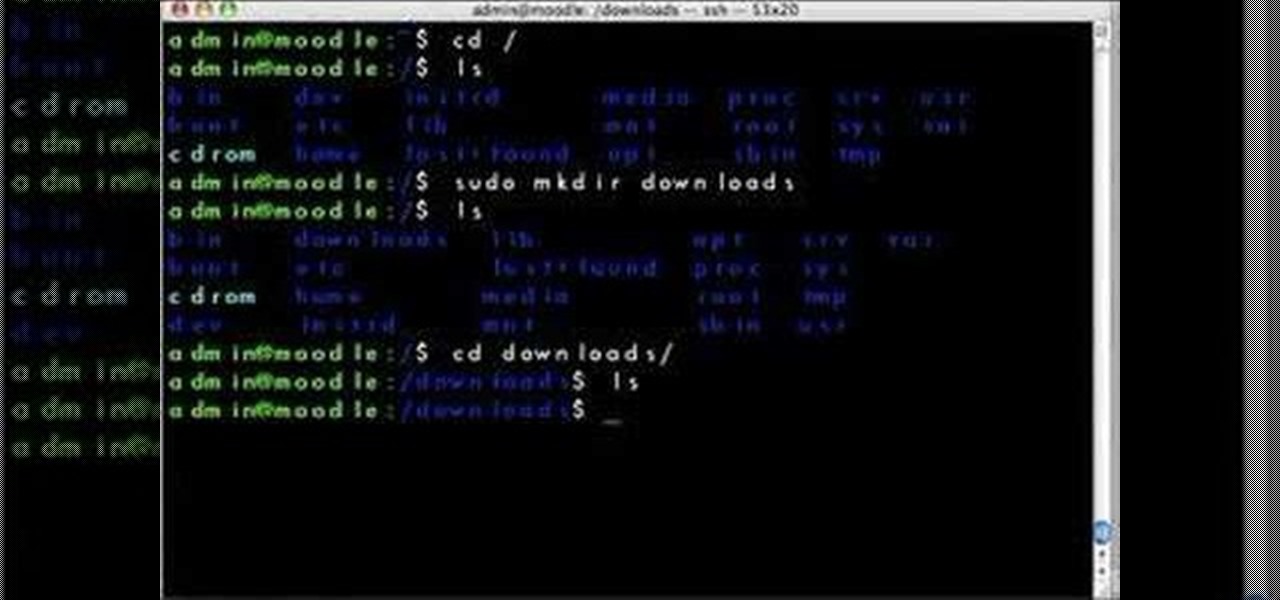
This video demonstrates how to install Webmin via SSH. Once you've downloaded the Webmin interface package, you'll want to install it onto your serve. In order to do that, you'll need to depackage it. If you're new to Linux or otherwise unclear about how to proceed, then watch this video for step-by-step instructions.

In this video you'll learn how to download Webmin, a web-based Unix administration interface, which will allow you to manage your serve with a web browser. If you're interested in running the Webmin interface, then watch and follow along.

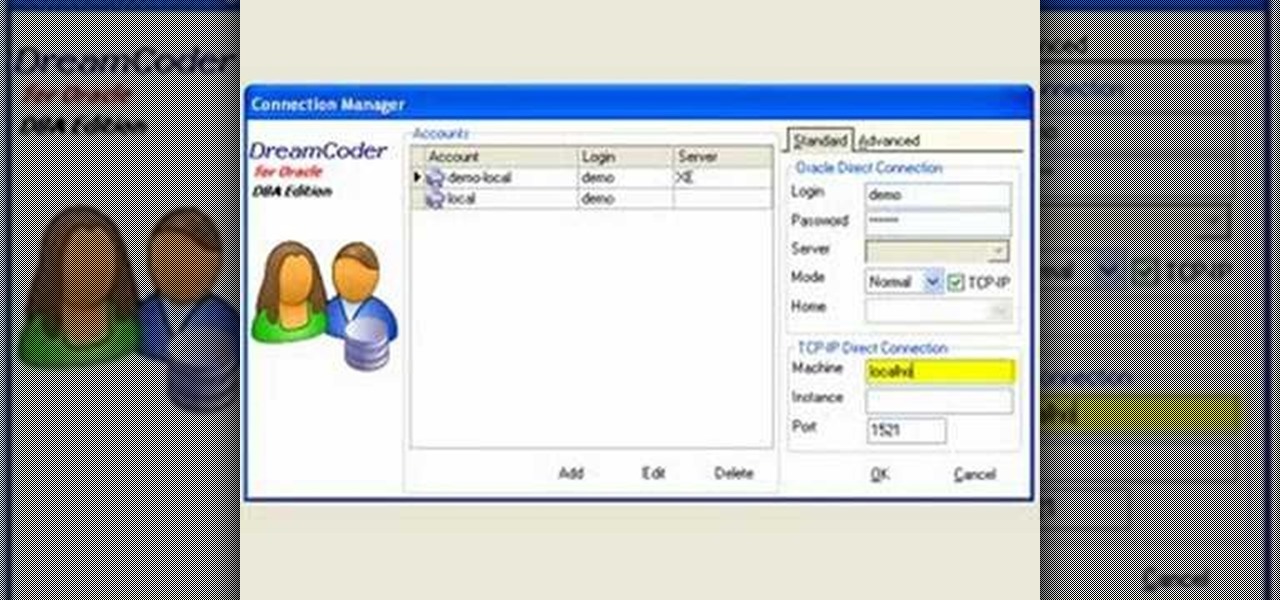
This tutorial will walk you, step by step, through, the process of establishing a connection between Oracle database server and DreamCoder for Oracle using the TCP-IP Direct connection option. To learn more about connecting to an Oracle database without an OCI client, press play!

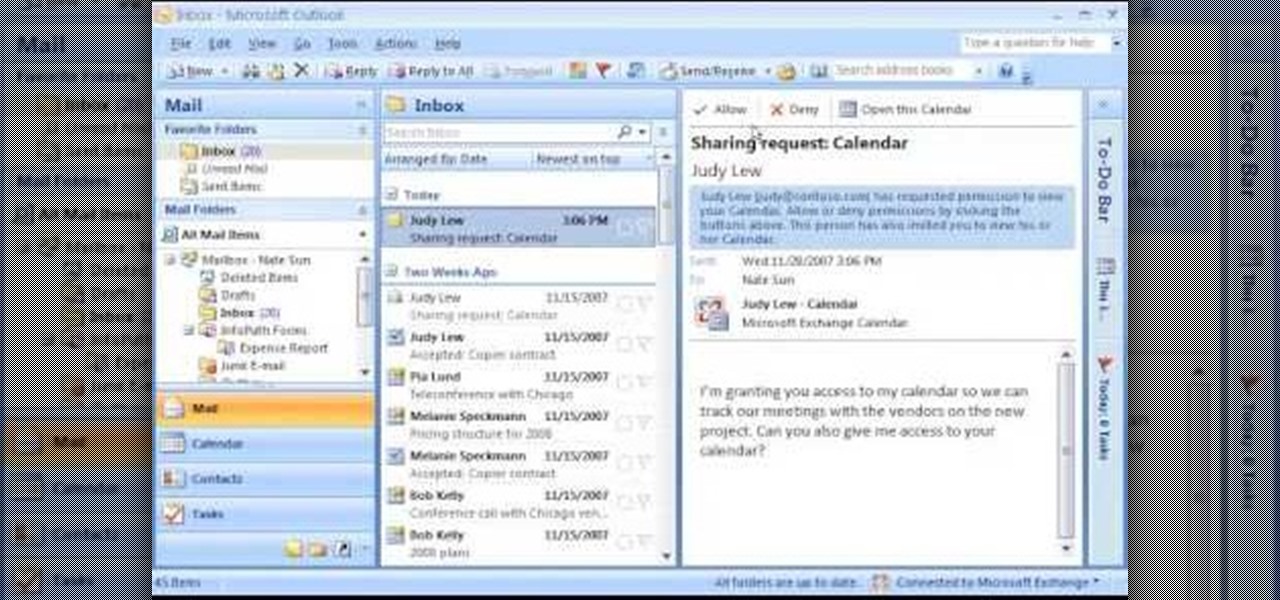
This tutorial shows you how to share your calendar three ways in Microsoft Office Outlook 2007. If your company uses Microsoft Exchange Server, you can share your calendar within the organization by using that feature. You can also send a snapshot of your calendar in e-mail to people outside your company. And you can publish your calendar on the Microsoft Office Online Web site and restrict how much detail is shown and who can access it.

Check out this tutorial and learn how to use Excel Calculation Services to handle processor-intensive calculations from your Microsoft Office SharePoint Server 2007 team site and to control access to external data.

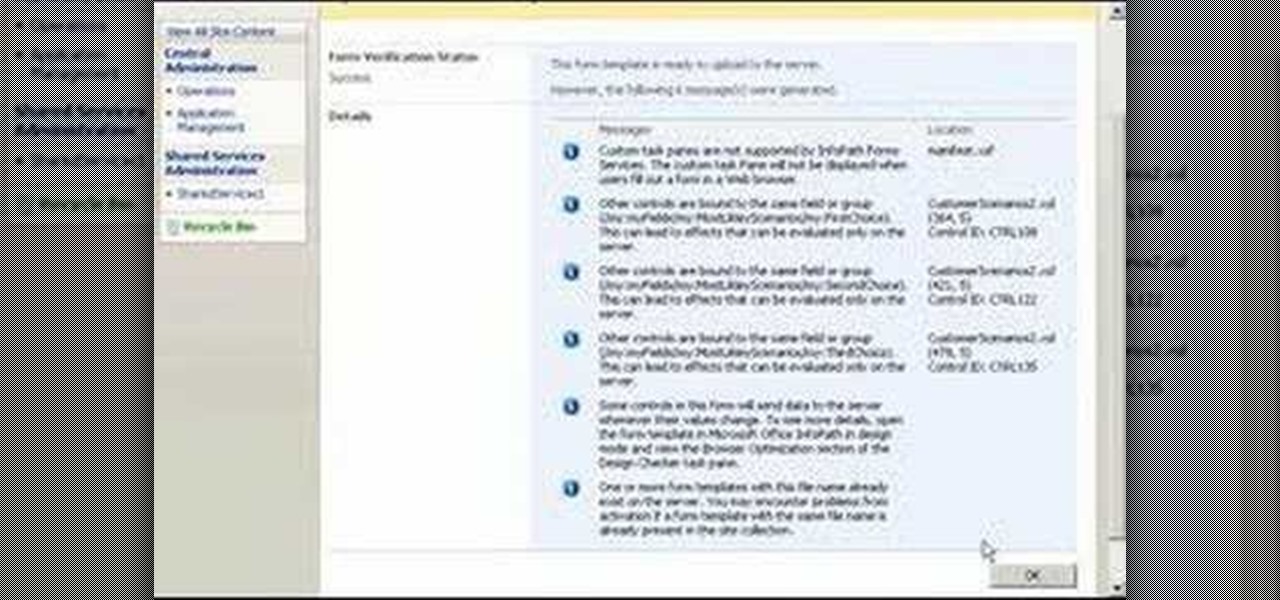
Now you can enable users to fill out Microsoft Office InfoPath 2007 forms by using a Web browser, which makes your forms more accessible to a wider audience. This instructional video shows you how to go through the process an IT Administrator can use to verify, upload, and activate an administrator-approved form template on a Microsoft Office SharePoint Server 2007 site.

This how-to shows how to make gold in World of Warcraft. With this technique you can easily make 500-1000g a day in your spare time. This completely depends on the economy of your server, but it is amazing how you can make so much money.

See how simple it is to create data-driven web sites using ASP.NET 2.0, Visual Web Developer 2005 Express Edition, and SQL Server 2005 Express Edition. Watch this video tutorial to learn how to create a database, add its data, and display that data on a web page.

In this video tutorial, Chris Pels will show how to persist and restore information in the ViewState of a custom user control. First, learn how to persist simple values containing .NET primitive types such as String, Int32, Boolean, etc. Then see how to persist complex types such as Class which contain properties storing information. The sequence of processing View State information during the lifecycle of an ASP.NET page is also discussed.

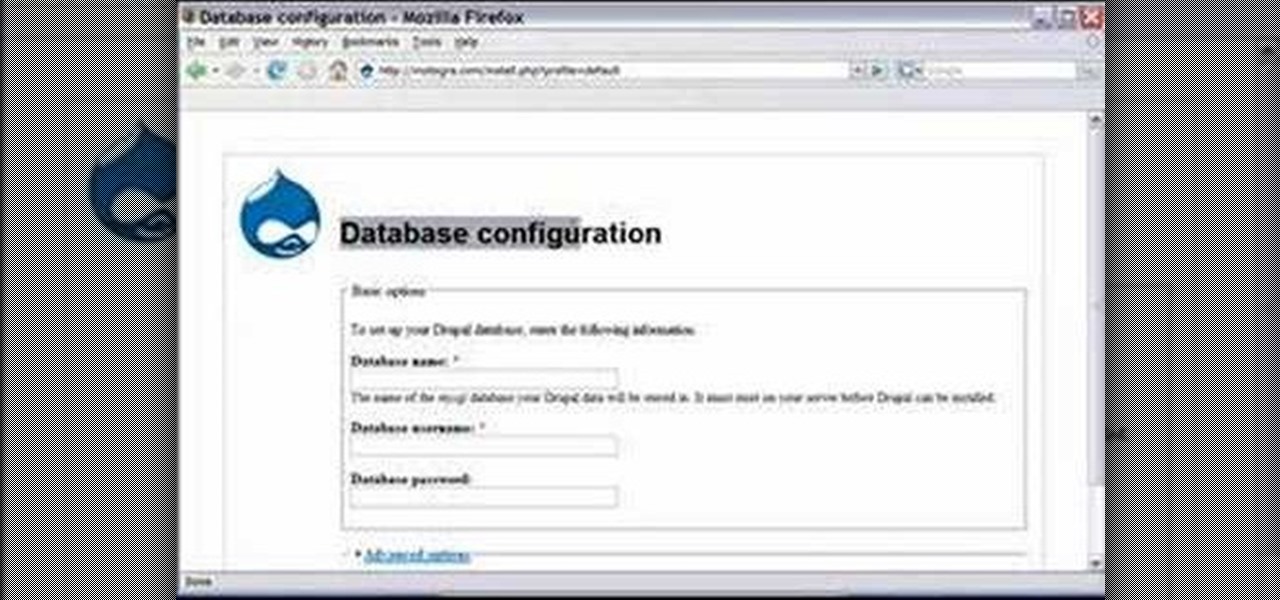
Basic installation of Drupal on a web server from start to finish with good explanations of Drupal's framework. Tutorial assumes viewer knows basic FTP and database configuration.

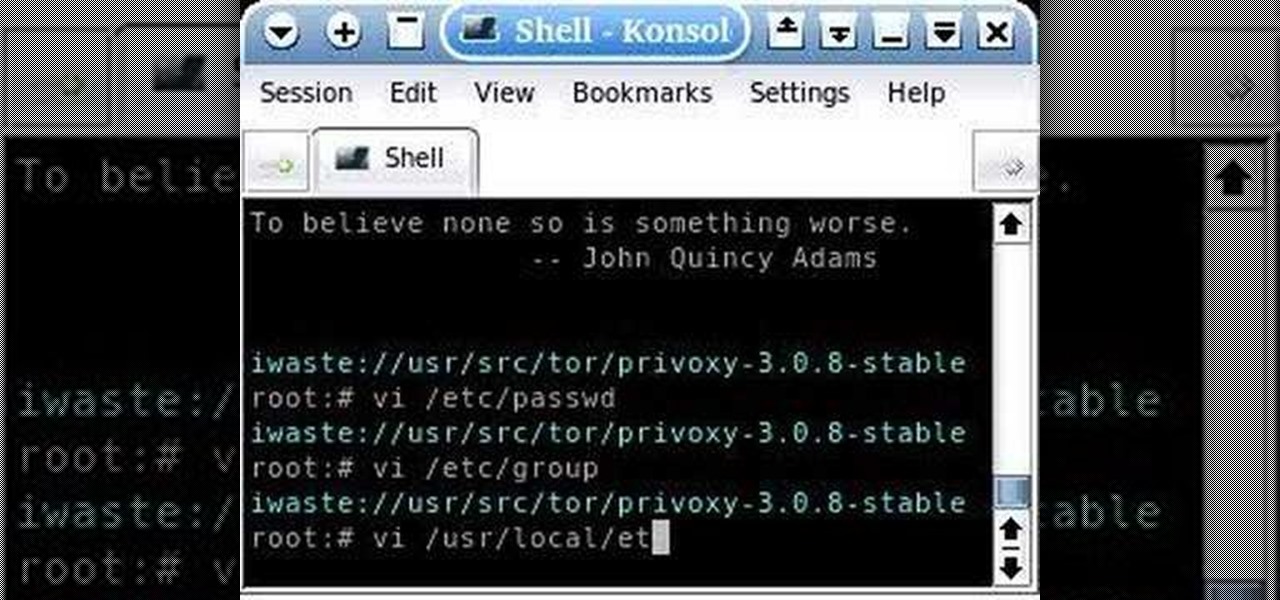
This is a tutorial about how to browse the web anonymously on a Linux server. Requires some knowledge of Linux. Be sure to note that information sent through this system is ever MORE open to hackers than the normal Internet. Don't send any personal information this way.

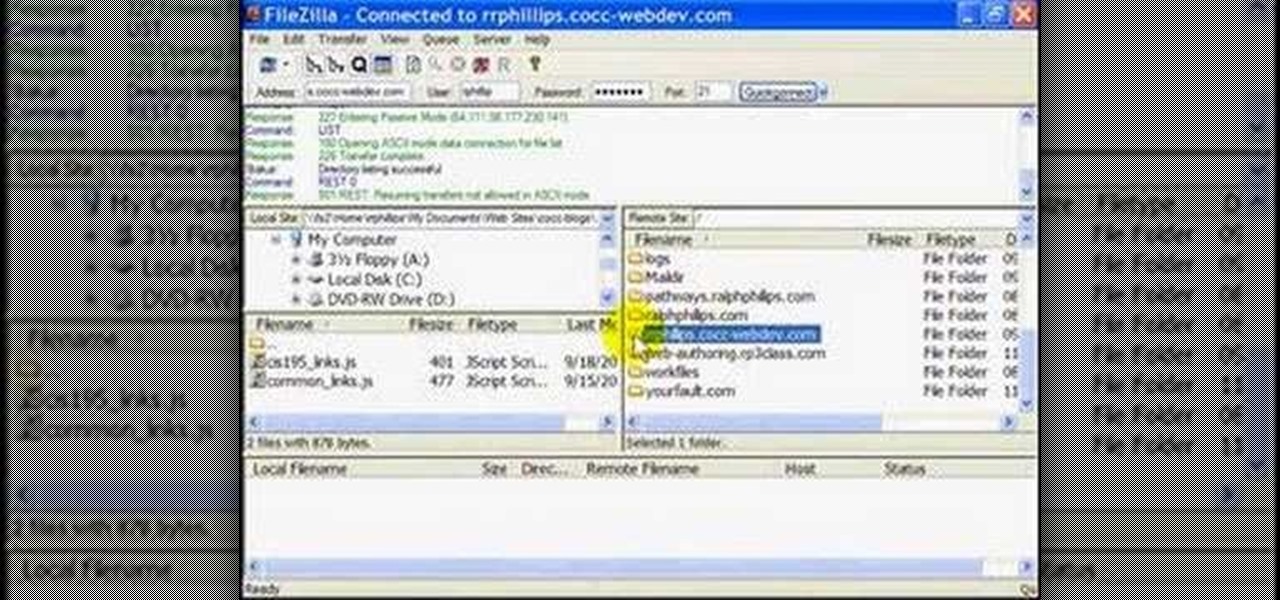
Use the Filezilla FTP client to publish files to your web server.

This video shows a cut and paste illustration of the tools Google offers in it's documents programs. Sharing a document can either occur by transmitting the doc from your home server to another person's home OR you can upload a doc to Google and browse from anywhere-- not just your home computer.

Apple just released iOS 13.5 for iPhone developers today, Monday, May 18. This GM (golden master) update comes 12 days after the release of iOS 13.5 dev beta 4, which introduced updated COVID-19 exposure notification logging settings and the ability to share your Medical ID with first responders when placing an emergency call.

We've all seen the login pages that allow you to log in to third-party accounts using your credentials from Facebook, Google, or Twitter. It saves you the trouble of creating another account and remembering more passwords — but it can also become a privacy and security issue, which is why Apple created the "Sign in with Apple" feature for iOS 13.

Spotify integration in Bumble has been around for a few years now, allowing prospective matches to view the artists you listen to the most on the popular music streaming service. It definitely helps people connect, but sadly, it doesn't work as well as it should because it rarely updates to show what you're listening to now.

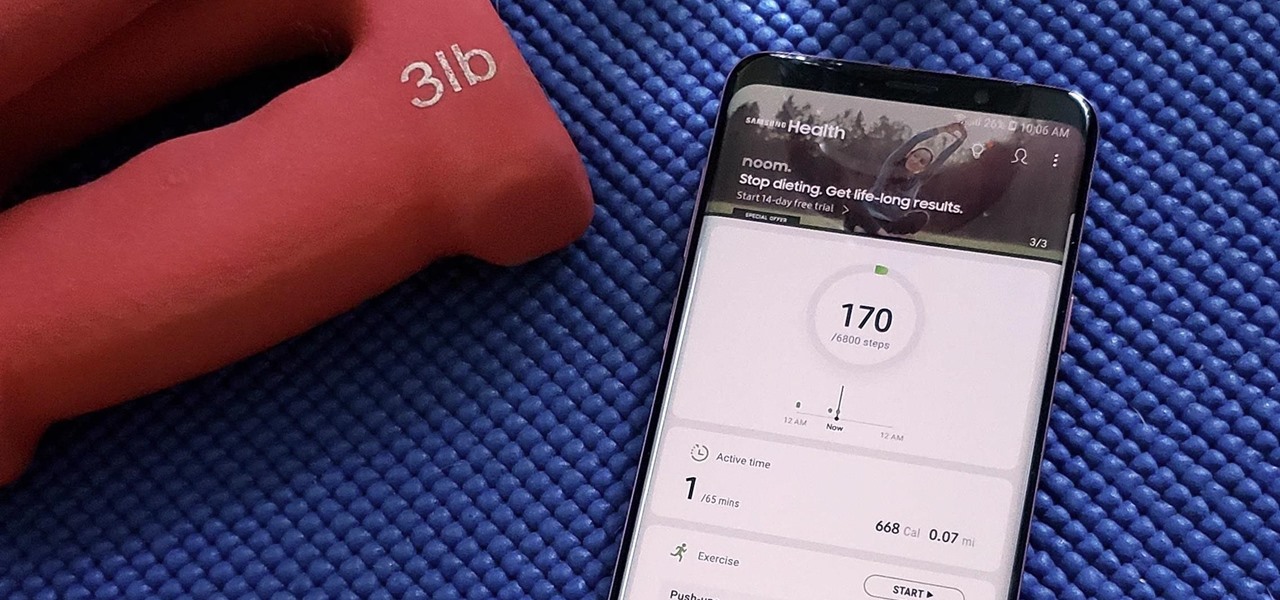
Samsung Health has become one of the most comprehensive wellness apps thanks to features that cover everything from step counting to nutrition logging and symptom diagnosis. But because the app has so much to offer, it can be easy to overlook some smaller, but useful features.

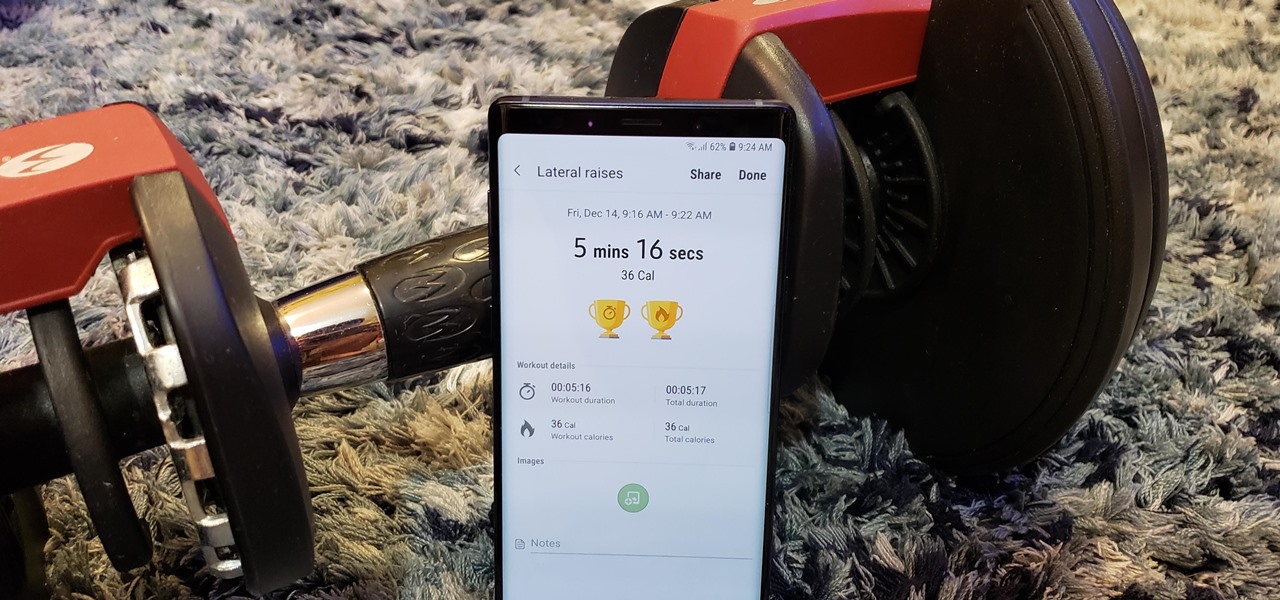
Keeping track of your physical activities can be difficult, especially if you have a hectic lifestyle with responsibilities to constantly stay on top of. Thankfully, Samsung Health is there to help you log your workout routines, leaving you with one less thing to keep track of as you go about your busy day.

It always helps to be prepared for the worst. This applies to our phones now more than ever, as we depend on them to be our record keepers for text messages from friends, family, and coworkers. If you ever lose or severely damage your phone, having a backup of your precious texts gives you the peace of mind of knowing that you can always get them back.

Using a keylogger to intercept keys pressed on an infected computer can circumvent encryption used by email and secure chat clients. The collected data can often reveal usernames, passwords, and potentially compromising and private information which hackers abuse for financial gain.

Getting new loot can be challenging in Fortnite Battle Royale. Whether you decide to pay for the Battle Pass or stick with the Free Pass, you still need to put in 50+ hours to unlock all the items. For those of us with Amazon Prime subscriptions, there's another way to unlock free items, and it won't cost you an extra dime.

Configuring onion services for the first time can be tricky. A surprising number of system administrators make seemingly trivial mistakes that ultimately lead to catastrophic cases of de-anonymizing supposedly anonymous sites on the dark web. OnionScan is a tool designed to identify common misconfigurations in onion services and aid us in understanding how to fix them.

During a penetration test, one of the most important aspects of engaging a target is information gathering. The more information you have coming into an attack, the more likely the attack is to succeed. In this article, I'll be looking at SpiderFoot, a modular cross-platform OSINT (open-source intelligence) gathering tool.

The Shadow Brokers, a hacker group known for its dump of NSA hacking tools in 2016, has just leaked their remaining set of data which implies that the NSA compromised SWIFT, the global provider of secure financial services, to spy on banks in the Middle East.

Welcome back, my rookie hackers! The Golden Fleece of hackers is to develop a zero-day exploit, an exploit that has not been seen by antivirus (AV) software or and intrusion detection system (IDS). A zero-day exploit is capable of skating right past these defenses as they do not contain a signature or another way of detecting them.

Welcome back, my budding hackers! Metasploit, one of my favorite hacking/pentesting tools, has so many capabilities that even after my many tutorials on it, I have only scratched the surface of it capabilities. For instance, it can be used with Nexpose for vulnerability scanning, with Nmap for port scanning, and with its numerous auxiliary modules, nearly unlimited other hacking related capabilities.

In the weeks before Apple officially released iOS 8, consumers were abuzz over rumors that a new feature would password-protect your photos and text messages from prying eyes. Unfortunately, this ended up being untrue, though we did cover some alternatives to protecting your important information using some built-in features and a third-party app. Now, there's a new iOS app that can do it all.

Welcome back, my greenhorn hackers! After the disaster that was Windows Vista and the limited and reluctant adoption of Windows 8 and 8.1, Windows 7 has become the de facto standard operating system on the desktop/client.

Welcome back, my rookie hackers! A short while back, I began a new series on database hacking, and now it's time to continue and extend your education in that field. As you know, the database contains all of the most valuable info for the hacker, including personally identifiable information, credit card numbers, intellectual property, etc. So, it's the ultimate goal of cybercrime and the APT hacker.

How to use Home Sharing in iTunes 9 to transfer music files to another computer. First make sure both computers have iTunes version 9 installed. To check this go to the iTunes 9 menu next to file in upper left and select the about item. On windows machines this will be in the help menu. In the computer with the music files we need to make sure the iTunes library is nicely organized. Again go to iTunes menu, this time open the preferences menu, and advanced icon. Check mark both sections "Keep...