This two part Achievement Hunter guide will show you where to find all of the different skulls and collectibles necessary to unlock the 'Librarian of Macragge' achievement in Warhammer 40k: Space Marine. Keep an eye out for those skulls and audio logs so you can grab the achievement for yourself!

When you're surviving in the wild there's no running to 7-11 to grab some snacks. It's all up to you. This excellent instructional video teaches you how to build and set an Asian trail spring trap. Primarily, this trap would be used for medium sides animals as they make their way along a forest trail. The trap requires a heavy object near the trail (ideally a rock, or fallen log), a length of fine, strong cordage, a 4ft piece of sapling and several small branches for this device's triggering ...
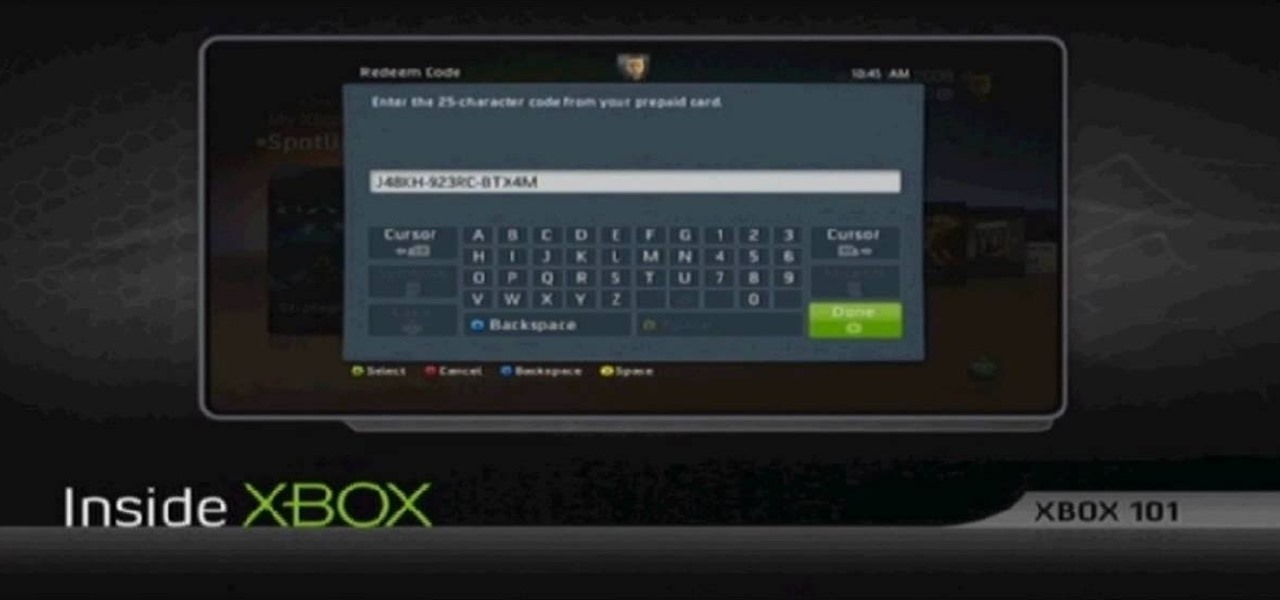
In this tutorial, we learn how to redeem a code for Microsoft Points (Xbox 101). First, you will need to log onto your Xbox Live account on your console. From here, pick a game that you want to purchase. Make sure you research the information about the game and you really want it, because you cannot return it. After this, choose the option to redeem a code and then type in the code for your Microsoft Points. After you do this, you will be bale to purchase the game that you want and you will h...

In this tutorial, we learn how to make homemade valentine's hot chocolate stones. First, take 8 oz of a good dark chocolate and chop it up. Place this in a bowl, then add in 1/8 tsp of chipotle peppers. Also add in a pinch of salt, then add in 1/2 c of heavy cream to a skillet and bring to a boil. After it boils, pour it over the chocolate and let it sit for around 3 minutes. Then, give it a stir until it's completely smooth and beautiful. Pour this onto plastic wrap, then roll into a log sha...
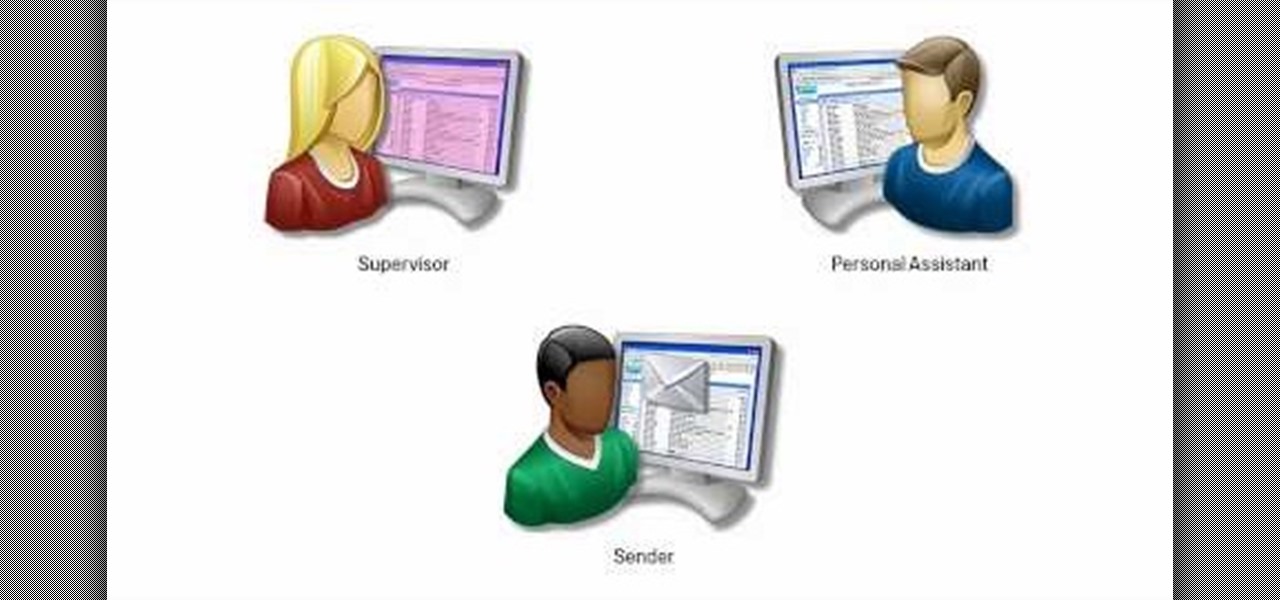
When you're personal assistant needs to handle your e-mails for you, it can be quite daunting having to give out your personal account information just so they can have access to your e-mail. And more importantly, having to battle for log in time might also be quite the hassle. With Gmail you can actually delegate your personal assistant so they have access to your inbox and can reply and send messages on your behalf, but they cannot change settings, passwords, or chat on your behalf. In this...

In this video tutorial, viewers learn how to read Google email offline. Begin by logging onto your Google account. Then click on Settings and select the Labs tab. In the Offline headline, click on Enable. To not grab all your emails, go to the Offline tab and select which messages will be synchronized with your computer, based on labels and time frame. This video will benefit those viewers who use Google mail, and would like to learn how to read their emails offline in case their internet con...

Adobe After Effects is powerful but difficult-to-use video editing tool. Youtube is a massive index of videos, most of which are low-quality and poorly edited. This video tutorial teaches you how to combine the two effectively by using After Effects CS4 to prepare HD videos for uploading to Youtube. It also includes other tricks like how to make a moving log as part of your video. Uploading HD quality videos will make your channel stand out and get more views.

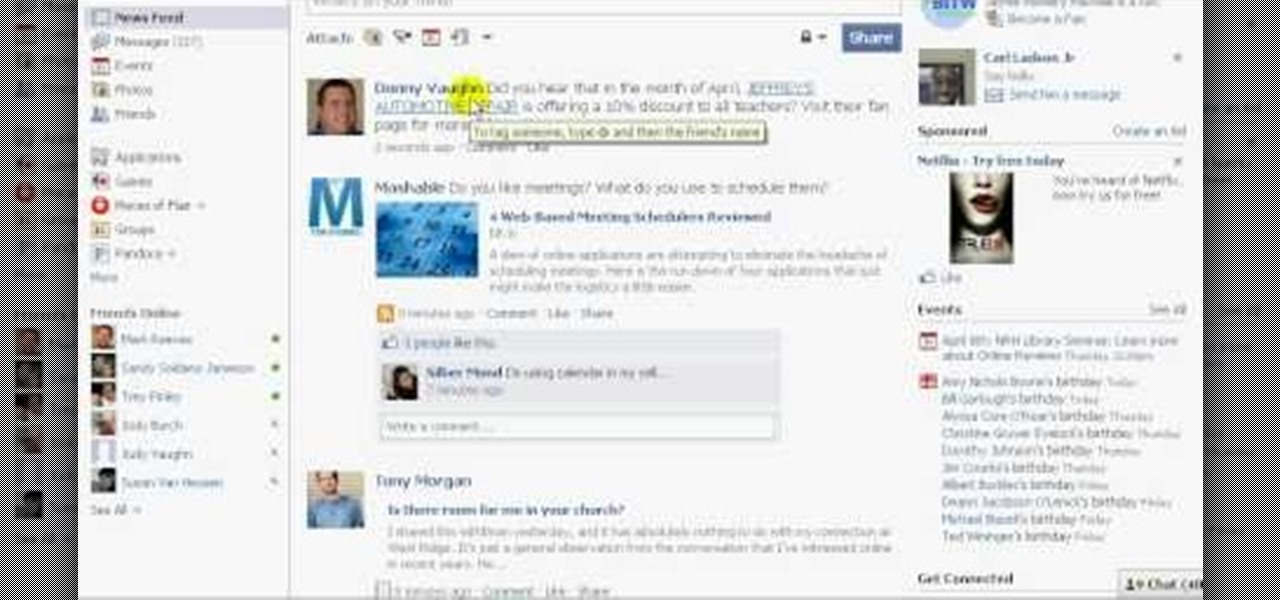
In this video, we learn how to tag people in pages in status updates. To do this, you need to open up your browser and log into www.facebook.com. Once you get to your profile, you will see a box that says "what's on your mind?". Type whatever you want to into this box, and to tag someone all you do is write "@" followed by their name, and their profile should pop up. Click on their picture and the text will now show a blue hyper-text when you post it. Now when people see your status, they can...

This video shows you how to make a fishing spear for catching fish or small wildlife in survival situation.To start, you need a sapling about 5 feet long and a knife. Make a raw sharpening of the stick. Then split the log at the tip for a length of 6-8 inches. To split, put the knife on the middle of the sapling, near the tip, and press hard against it. Once it is split, find a twig with the width of a pencil and push it inside the split, making the two halves of the stick form a gap between ...

As a kid, you always liked to be constructive, building with Legos and Lincoln Logs, and at one point you even got into playing the strategic, building block, video game Tetris. Why not go back to the gold old days and find a new game of today similar to those of your young years, like Rumis?

Chef Billy Parisi from Fix My Recipe responds to a request sent by one of his viewers, to "fix" a barbecue chicken skewers meal.

It was bound to happen with all those numbers floating around in your brain – you've forgotten your Windows password. Here's how to recover it.

Faced with a missing log-on screen startup problem? This clip offers some advice for resolving it. It's easy! So easy, in fact, that this home-computing how-to from the folks at Britec can present a complete overview of the process in just over five minutes. For more information, including detailed, step-by-step instructions, take a look.

The fine folks at The Pathfinder School present what they call a spring tune-up for for you knife techniques, which have presumable deteriorated during the winter. The host is trying out a new knife he has been asked to test, and uses it to make a trap knotch and drill into a log, among other things.

K'NEX is one of the most popular construction toys on the market, right next to Lincoln Logs and LEGOs, but what makes K'NEX stand out is the fact that children can build mechanically derived toys. Instead of blocks or little logs, kids use interconnecting plastic rods and connectors, which give them tons of contraptions to build and play with. Today, K NEX has even more possibilities with wheels, pulleys, panels and flexi-rods to make amusement park roller coasters, airplanes, animals, bikes...

K'NEX is one of the most popular construction toys on the market, right next to Lincoln Logs and LEGOs, but what makes K'NEX stand out is the fact that children can build mechanically derived toys. Instead of blocks or little logs, kids use interconnecting plastic rods and connectors, which give them tons of contraptions to build and play with. Today, K NEX has even more possibilities with wheels, pulleys, panels and flexi-rods to make amusement park roller coasters, airplanes, animals, bikes...

K'NEX is one of the most popular construction toys on the market, right next to Lincoln Logs and LEGOs, but what makes K'NEX stand out is the fact that children can build mechanically derived toys. Instead of blocks or little logs, kids use interconnecting plastic rods and connectors, which give them tons of contraptions to build and play with. Today, K NEX has even more possibilities with wheels, pulleys, panels and flexi-rods to make amusement park roller coasters, airplanes, animals, bikes...

K'NEX is one of the most popular construction toys on the market, right next to Lincoln Logs and LEGOs, but what makes K'NEX stand out is the fact that children can build mechanically derived toys. Instead of blocks or little logs, kids use interconnecting plastic rods and connectors, which give them tons of contraptions to build and play with. Today, K NEX has even more possibilities with wheels, pulleys, panels and flexi-rods to make amusement park roller coasters, airplanes, animals, bikes...

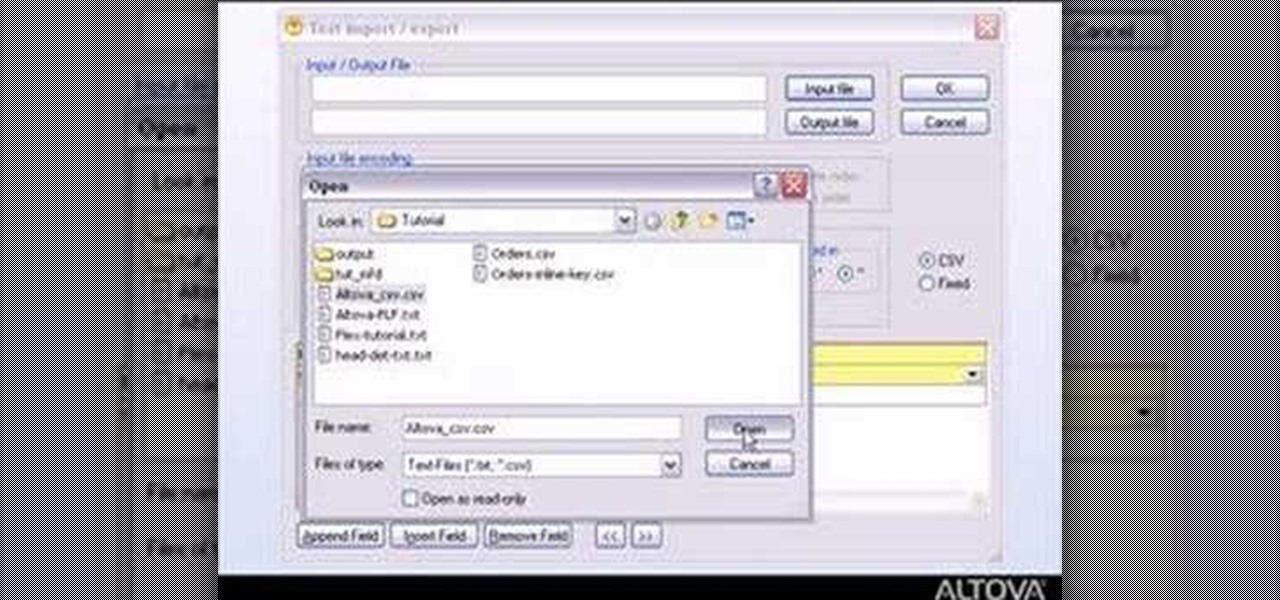
MapForce supports flat files as the source and/or target of any mapping involving XML, database, EDI, web services or other flat file data. In this how-to, you'll find instructions for mapping data from arbitrary text files (such as log files, CSV, fixed-width, and other legacy data sources) to databases and XML files.

Google has released a sync tool which provides an automated 2 way sync between your Google and your Outlook 2003 or 2007 calendar. It was easy to install and set up, plus it works! Just log into your Google calendar and you'll see it at the top.

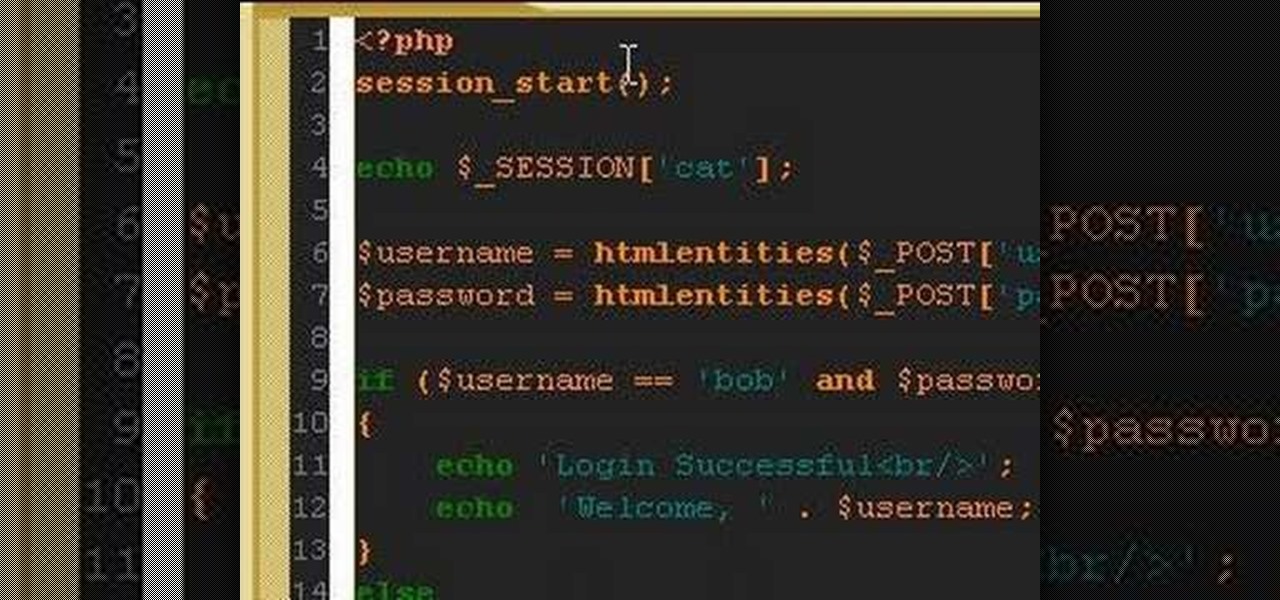
A PHP programming tutorial on creating login sessions to keep users logged in.

The Pi-hole project is a popular DNS-level ad blocker, but it can be much more than that. Its DNS-level filtering can also be used as a firewall of sorts to prevent malicious websites from resolving, as well as to keep privacy-killing trackers such as Google Analytics from ever loading in the browser. Let's take a look at setting a Pi-hole up and customizing a blacklist to suit your needs.

With a tiny computer, hackers can see every website you visit, exploit services on the network, and break into your Wi-Fi router's gateway to manipulate sensitive settings. These attacks can be performed from anywhere once the attacker's computer has been connected to the router via a network implant.

At long last, the magical world of Harry Potter has received a mobile game worthy of its name. Harry Potter: Wizards Unite is the game in question, and is set to touch down worldwide on June 21, 2019. For the longest time, however, the game has been available as a soft launched game for testing, and with a little tinkering, you can actually try it out right now before its official release stateside.

With the number of web applications out there today, it comes as no surprise that there are just as many vulnerabilities waiting for hackers to discover. Finding those vulnerabilities can be a difficult task, but there are plenty of tools available to make the process easier. While it won't help find any zero-days, web scanners such as Uniscan will detect common vulnerabilities.

When Pokémon GO developer Niantic launches its Real World Platform for augmented reality gaming, it will run over 5G speeds courtesy of T-Mobile parent company Deutsche Telekom and the edge servers of its MobiledgeX subsidiary, the companies announced today.

In the world of technology, there's often a trade-off between convenience and security. The Java Remote Method Invocation is a system where that trade-off is all too real. The ability for a program written in Java to communicate with another program remotely can greatly extend the usability of an app, but it can also open up critical vulnerabilities that allow it to be compromised by an attacker.

Command injection is a technique used by hackers to execute system commands on a server, usually via a web application or some kind of GUI. This can happen when an application provides some sort of functionality to the user involving the use of system commands. When the input is not properly sanitized, commands not originally intended to be run are allowed to be executed.

With all the web applications out on the internet today, and especially the ones built and configured by novices, it's easy to find vulnerabilities. Some are more perilous than others, but the consequences of even the slightest breach can be tremendous in the hands of a skilled hacker. Directory traversal is a relatively simple attack but can be used to expose sensitive information on a server.

The microphone in a Windows computer is accessible to most applications running on the device at all times and completely without security limitations. Information gathered from recorded audio conversations taking place in the surrounding area of a compromised computer can be used for social engineering, blackmail, or any number of other reasons.

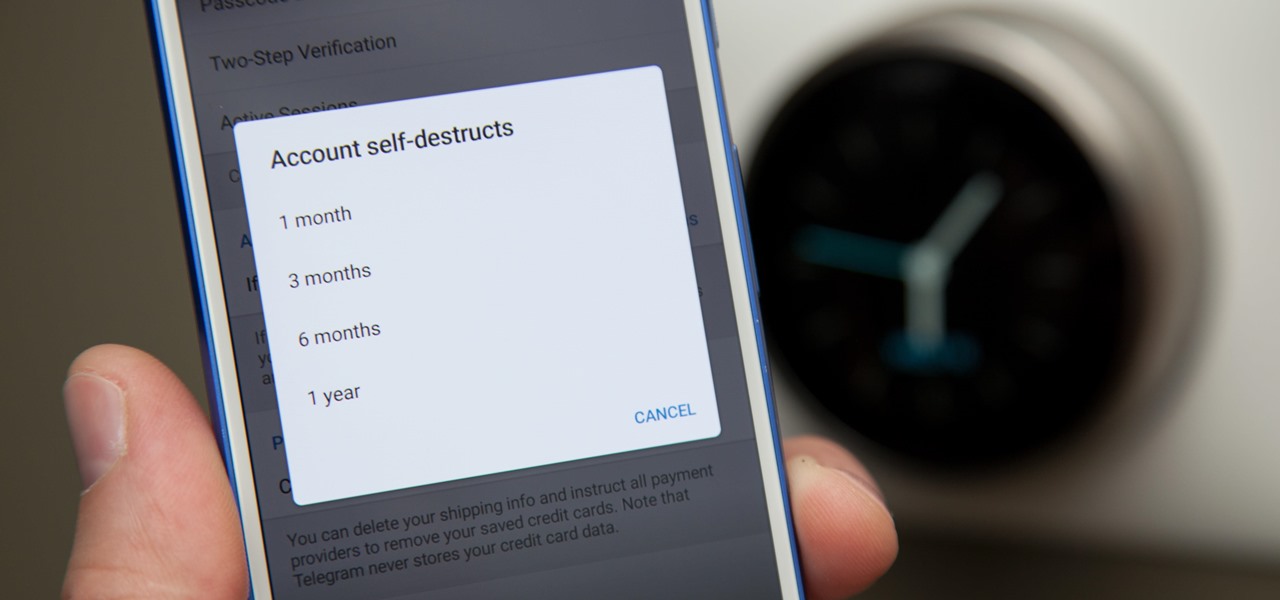
You can send self-destructing messages in Secret Chats, but that's not the only thing that can destroy itself in Telegram after a specified amount of time. Your whole account can disappear after a certain amount of inactivity, so it's important to adjust these settings to give you more time or to kill your account even quicker.

It seems like there's a cyber security scare every day. Consumers are growing increasingly concerned about the safety of their accounts, and they have reason to be. Hackers will maliciously attack you anywhere — and we mean anywhere — they can to get your private information.

The HoloLens is the world's first untethered holographic head-mounted computer, which Microsoft has been rather proud of—and they have every reason to be. Of course, as soon as we developers get adjusted to the idea of keeping the scope of our projects inside the bounds of the HoloLens' processing power, Microsoft hits us with the Holographic Remoting Player.

Without explicit cooperation between Apple and the US government, authorities could still be monitoring Apple users. According to The Information, Apple is worried the servers it has been using might be bugged. We already know the NSA intercepts equipment to install backdoors, so this is a legitimate concern.

Welcome back, my tenderfoot hackers! As you should know from before, Snort is the most widely deployed intrusion detection system (IDS) in the world, and every hacker and IT security professional should be familiar with it. Hackers need to understand it for evasion, and IT security professionals to prevent intrusions. So a basic understanding of this ubiquitous IDS is crucial.

If you want to keep your online world secure, your best bet is to have a different password for every site and service that you use, and to make sure each of the passwords are comprised of random characters instead of familiar words or numbers. But this obviously creates a problem—how exactly are we supposed to remember all of these complicated passwords?

WPA Enterprise is widely used in large corporations as it offers individual and centralized control through a server that authenticate the users (RADIUS server). In this tutorial I will show you how to break the barrier and obtain the user credentials.

Recently, I've been experimenting with BeEF (Browser Exploitation Framework), and to say the least, I'm hooked. When using BeEF, you must "hook" the victims browser. This means that you must run the script provided by BeEF, which is titled "hook.js", in the victims browser. Once you've done that, you can run commands against the victims browser and cause all kinds of mayhem. Among these commands, there is an option to use the victims webcam. This is what we'll be doing here today, so, let's g...

Welcome back, my novice hackers! In this third installment of my Hacking Web Apps series, we will look at the authentication of web applications. Remember, there are many ways to hack web applications (as I pointed out in my first article), and cracking authentication is just one method.

Welcome back, my hacker novitiates! As you know by now, the Metasploit Framework is one of my favorite hacking tools. It is capable of embedding code into a remote system and controlling it, scanning systems for recon, and fuzzing systems to find buffer overflows. Plus, all of this can be integrated into Rapid7's excellent vulnerability scanner Nexpose.