Nmap is more powerful than you know. With a few scripts, we can extend its functionality beyond a simple port scanner and start to identify details about target servers sysadmins don't want us to know.

With the addition of the OpenSSH client and server in the Windows 10 Fall Creators Update, you no longer have to rely on third-party programs to open an SSH server and connect to a Windows machine. While still a beta feature, this represents a long-overdue update fulfilling a promise made back in 2015.
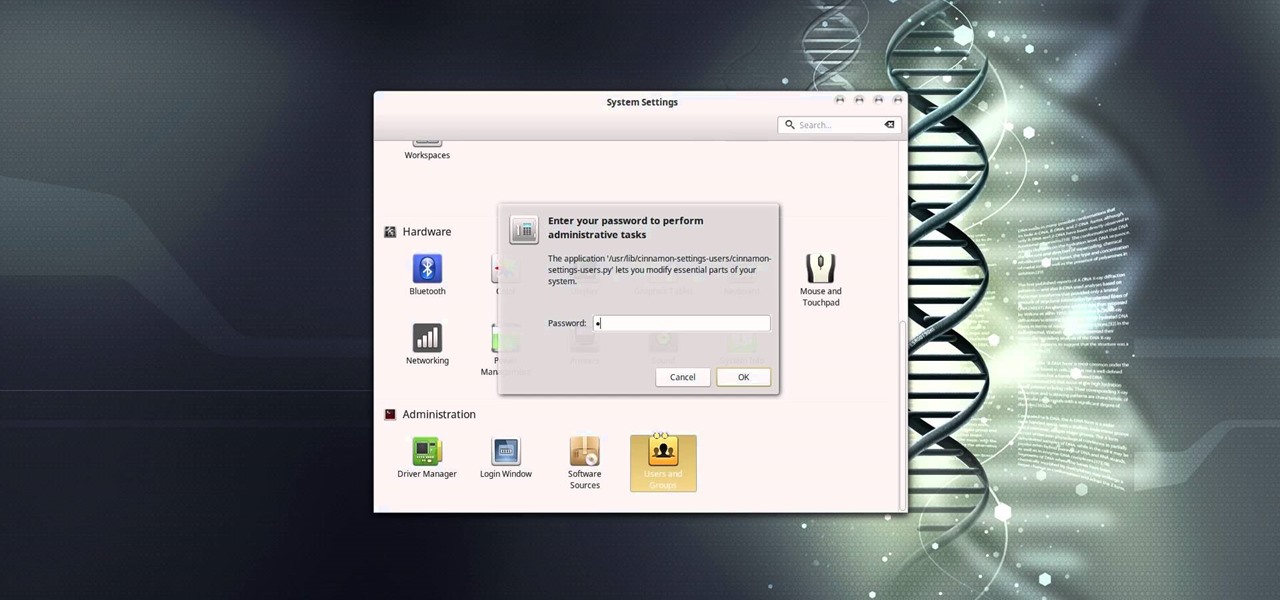
In this video tutorial, I'll show you how to remove the password from the log in screen on Linux Mint 17.2

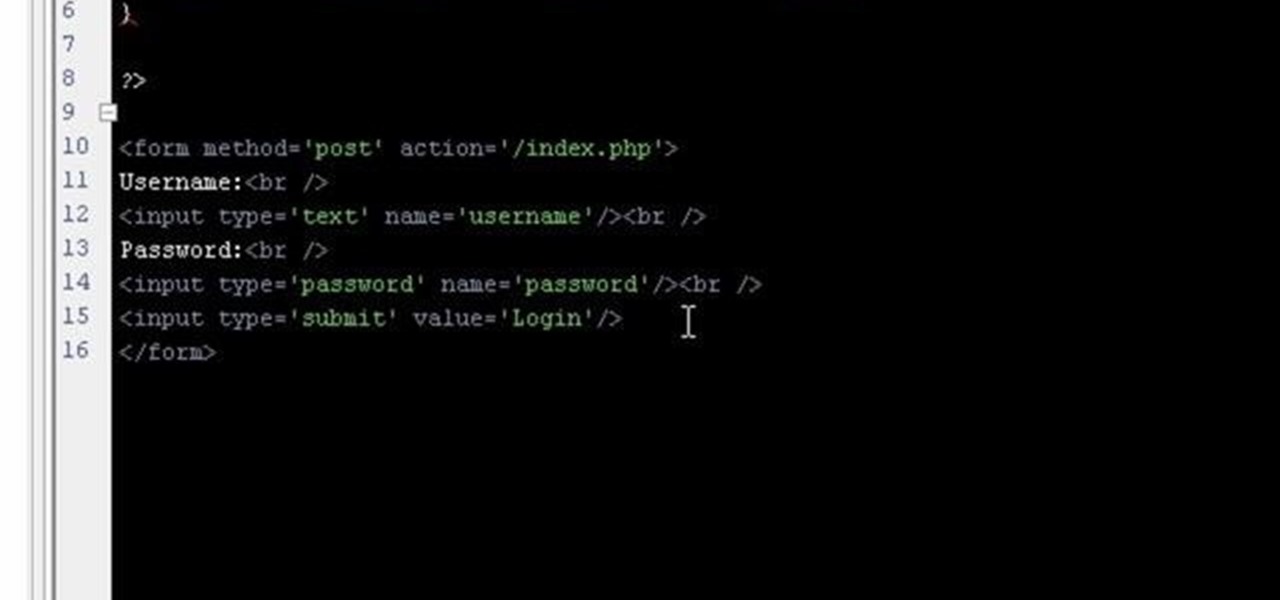
Welcome back, my hacker novitiates! There are many ways to hack databases, and most of these techniques require SQL injection (SQLi), which is a way of sending SQL commands back to the database from a web form or other input. In this tutorial, we will use SQL injection to get access to the underlying server. So instead of getting access to the database and its data, we will use the database as an intermediary to gain access to the underlying server.

As we're all aware, recon is vital to a successful hack. We need to know everything we can about the target in order to perform the best possible attack. Port scanning is a basic recon concept that is introduced very early in learning proper reconnoissance. The issue with port scanning is that is makes a lot of noise. Every connection to every port will be logged. This is where stealth scanning comes in. Also known as SYN or half-open scanning, stealth port scanning is a bit quieter, and is l...

Welcome back, my greenhorn hackers! In previous Wi-Fi hacking tutorials, I have shown you ways to create an Evil Twin, to DoS a wireless AP, and to crack WEP and WPA2 passwords, but in this tutorial, I will show you something a little bit different.

Apps that save your passwords have been around for quite a long while. But apps that complete the entire login process automatically? Now that's a different story.

Welcome back, my budding hackers! Recently, I showed you how you could exploit the widely disseminated OpenSSL vulnerability that has to become known as "Heartbleed". Although the world has known about this vulnerability for over a month now, it will likely take many more months—or even years—for everyone to close this vulnerability.

It's known that during the Thirty Years' War that took place in Europe between 1618 and 1648, soldiers used Swedish fire torches (also called Canadian candles) for heating, lighting, and cooking meals.

In this video tutorial, viewers learn how to import, manage and export 16:9 footage in Adobe Final Cut Pro. Begin by opening the Log and Capture.Then configure the Logging, Clip Settings and Control Settings. For the Control Settings, set the Device Control as Fire Wire NTSC and the Capture/Input as DV NTSC 48 kHz Anamorphic. Then scroll through the sequence setting of the footage and check Anamorphic. To export, click on File and select Export. Click in Options set the the size to Compressor...

Compound butter is just flavoured butter. LegourmetTV shows you how to make garlic butter, which is a good companion to fresh bread. One clove of roasted garlic is added to half a cup of unsalted butter to make simple garlic compound butter. You can also add cinnamon and sugar to butter for toast. Alternatively, you can even add any of your favourite herbs to melt down a steak. You can also shape the butter into a log, wrap it up in baking paper and keep it in the refrigerator for storage. Th...

On this video from Bushcraft Machete, he explains the purpose of a scandi edge and how to use it. He uses the machete as a planer, stripping the bark from a log by holding the machete almost flat against the log and tapping the back of the blade with a stick. He explains that a scandi edge is sharpened all the way down to a point and has a very low angle. This type of edge makes the machete useful for carving off thin strips of wood. He has sharpened his machete with a scandi edge near the ha...

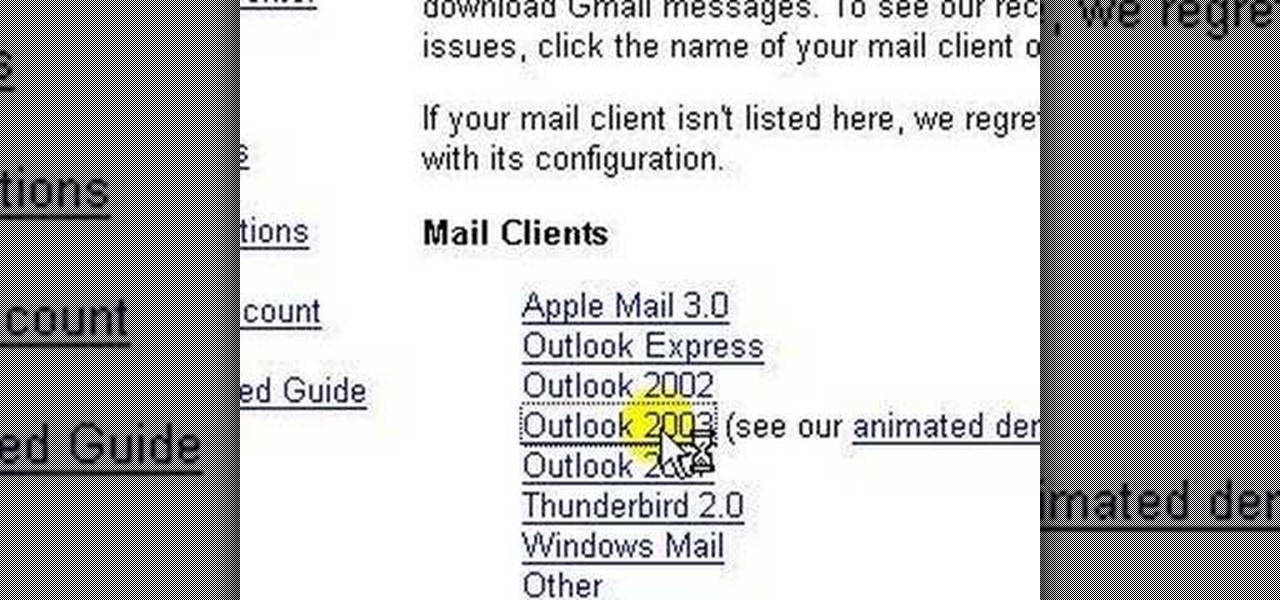
lakercoolman shows us how to set up our gmail account with this quick tutorial. Basically outlook express is a program that helps us to organize our email with added features such as contacts, to do lists and calender entries. Its an offline email client that allows us to work offline and also lets us set up exchange servers aswell. Ohter email servers such as hotmail and yahoo charge for thios service but the advantage of gmail is that IMAP or POP access is free. in ofer to set up, navigate ...

Whatever your reasons for doing it, if you are trying to hack passwords, it helps to have the right software for getting the job done. With the Cain and Abel program, you will be well on your way to hacking even the toughest personal passwords.

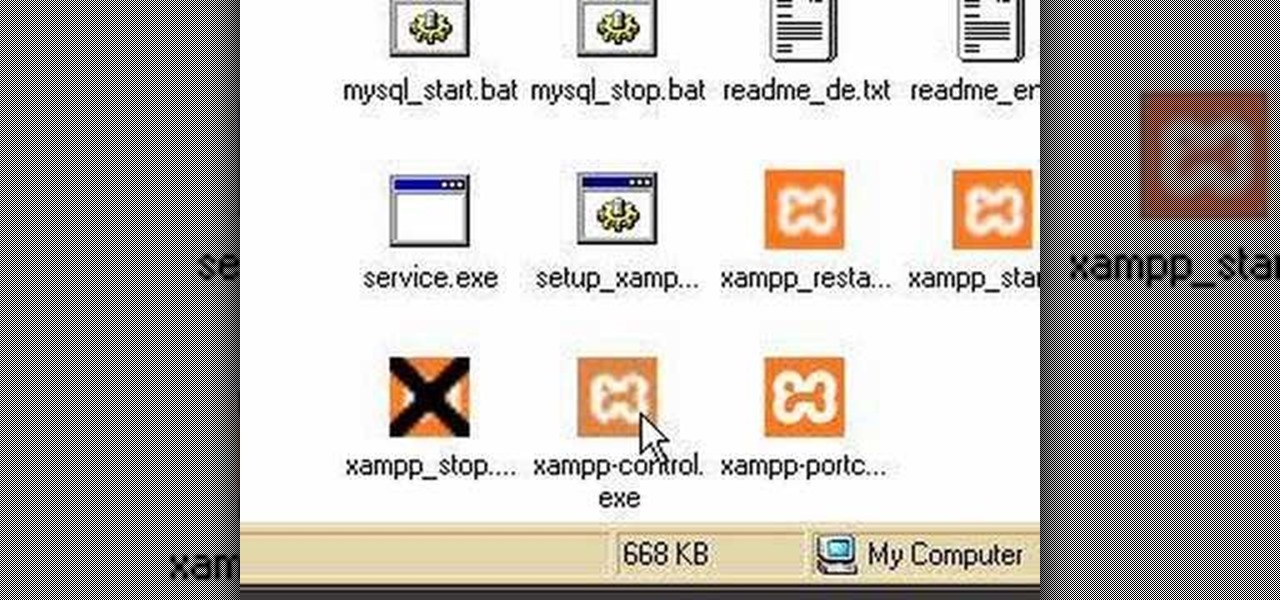
Using a simple peice of software XAMMP to streamline the setup process of apache+php+mysql

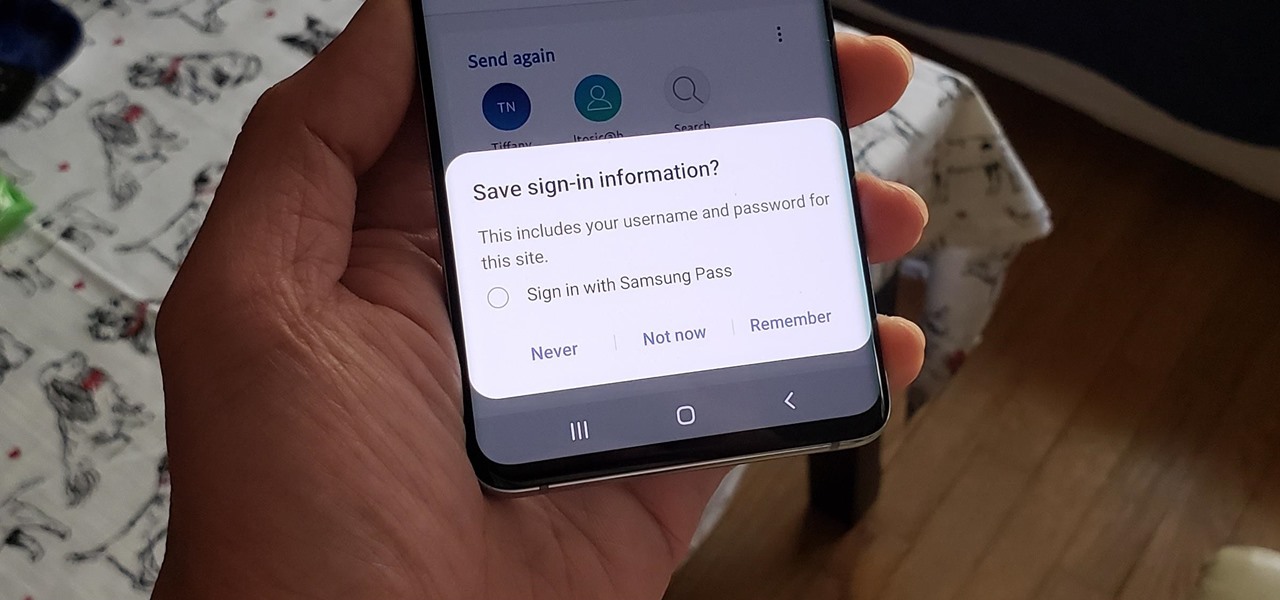
If you use Google Chrome on your computer, you've undoubtedly saved a ton of passwords since the browser always prompts you to. But Samsung uses their own password service on their phones by default, so you'll have to change a setting if you want to use your Chrome passwords to log into apps and sites on your Galaxy.

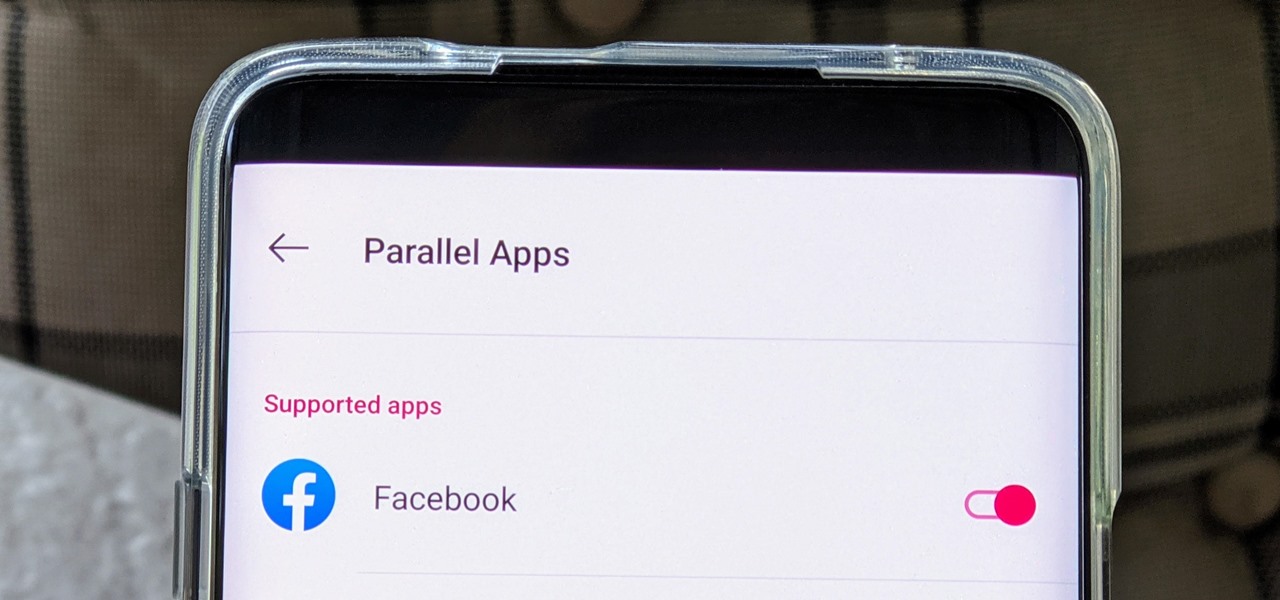
The Facebook app only supports one account being logged in at a time — but what if you need one for work and one for your personal life? That would normally involve logging out and logging in every time you need to switch accounts, but your OnePlus device offers a much better solution.

Auditing websites and discovering vulnerabilities can be a challenge. With RapidScan and UserLAnd combined, anyone with an unrooted Android phone can start hacking websites with a few simple commands.

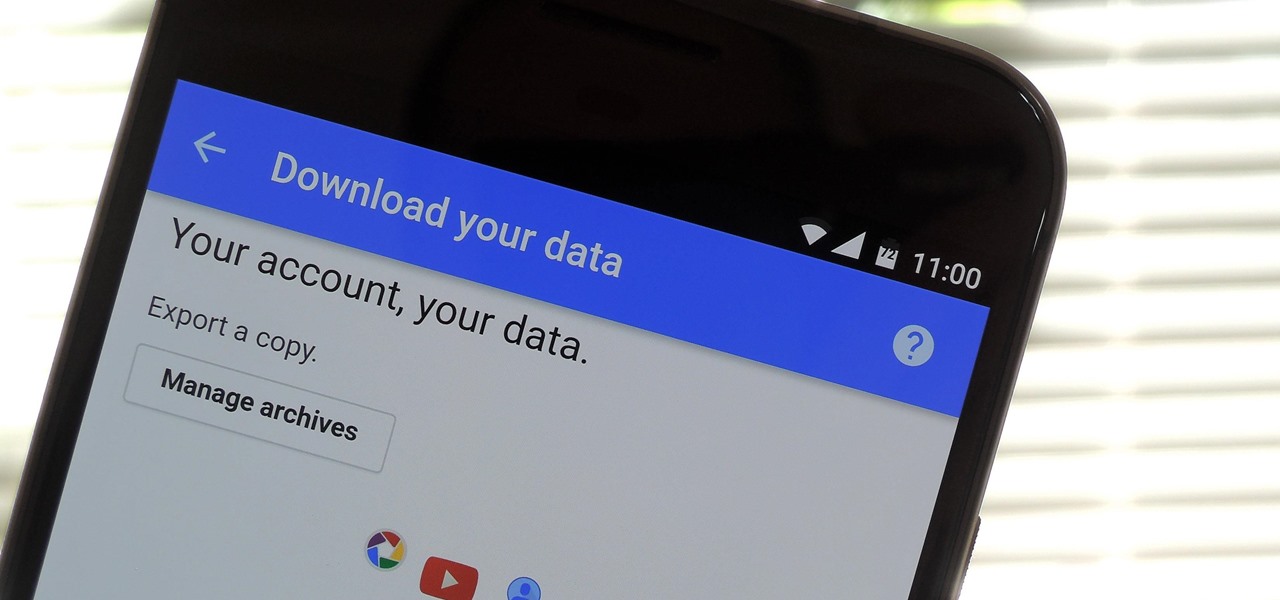
Threats to your privacy and security are everywhere, so protecting your data should be the highest priority for anyone with a smartphone. However, one threat many people overlook is the company who supplies the operating system your Android phone runs — Google.

If you're an Android user, Google probably has almost your entire digital life stored on its servers. Family pictures are backed up on Google Photos, your e-book library resides with Google Play Books, videos are on YouTube, chat logs in Gmail and Hangouts, starred places and location history in Google Maps, and so much more.

Kryptowire, a company specializing in mobile security solutions, released a report on Tuesday, November 15 that exposed firmware in a number of Android devices that was collecting personally identifying information (PII) and uploading it to third-party servers without users' knowledge.

Hello partners, first of all I would like to thank all those who have sent me positive feedback about my posts, to say that I'm always willing to learn and teach. I'm also open to answer the appropriate questions.

Welcome back, my neophyte hackers! In previous tutorials, we learned how to steal system tokens that we could use to access resources, how to use hashdump to pull password hashes from a local system, and how to grab password hashes from a local system and crack them.

With all of the different websites we use in our day-to-day lives, keeping track of our numerous login credentials can start to become a hassle. This has created a market for password managers that aim to centralize these account credentials and generally streamline the process of logging into our favorite sites.

Welcome back, my greenhorn hackers!

First off, I would like to say two things. One, this is not for beginners; if you don't feel that you understand this how-to at all, do not try it. Second, never ever install random software or change settings if you do not trust the source.

If you're working on a website and want users to use it repeatedly and form a community on it, you should probably give them a way to create an account and log in to your site. This video will show you how to create an AJAX login script using AJAX with jQuery, which will allow your users to do exactly what I described above, making your website much more professional and a much better place for people to stay and click on ads or whatever else you want them to do.

In this video, we learn how to create a free flash website using Wix. First, log online and go to "www.wix.com" and either create a screen name or log into your account. Now, click on "create" and choose a premade template or make one from scratch. Now, change the background to a color you prefer, then add in a frame and different media to your page. You can also add a title to the website by clicking on the "text" section. You can play around with the different effects and additions, making ...

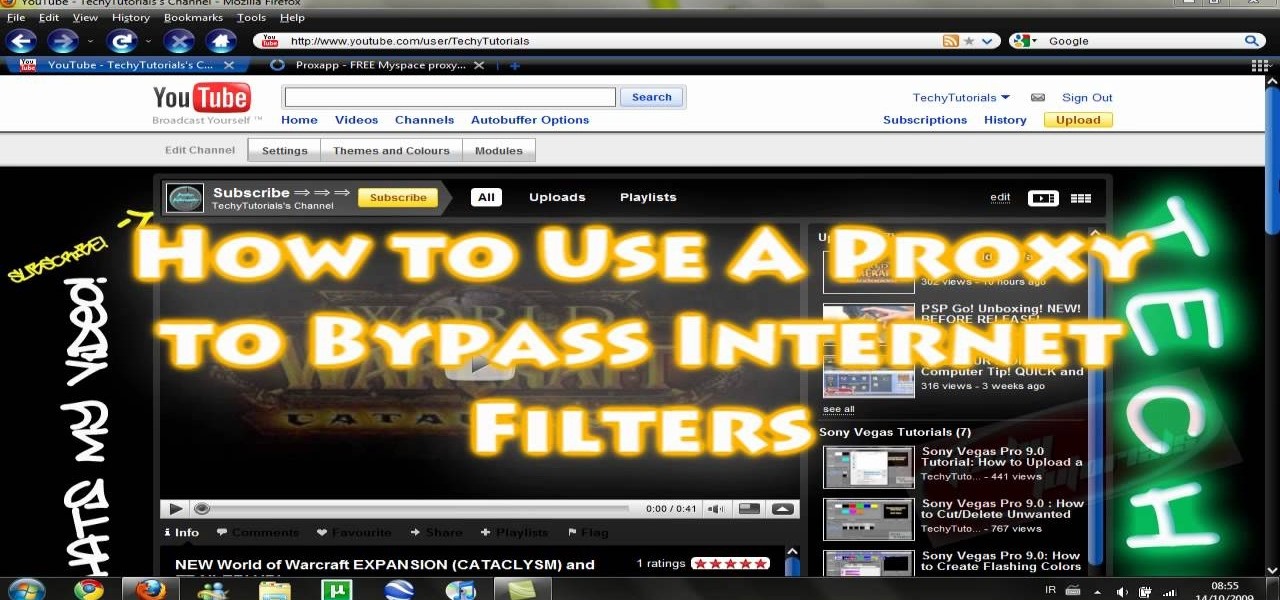
The video shows us how to use a proxy to bypass the Internet Filters. Most of the times in our schools and colleges most of the websites including the social networking ones will be blocked for security reasons and makes us unable to log into those websites. In such cases even the ones from the YouTube, several videos will be blocked. So in this video, we will be shown how to bypass those filters and log into those sites. Firstly go to the website Proxapp and over there you will be asked the ...

Ken Appleby demonstrates how to forward a domain with GoDaddy. First, open your web browser and log onto your GoDaddy account. Click the domain manager option on the left hand side of the home page and log in if necessary. Choose the domain that you would like to forward. Find the forwarding option which is located on the top central portion of the domain manager window. Tick the enable forwarding box. Then, type the address that you would like to forward your domain to in the forward to box....

The video describes a method of doing the twiddle scratch on a DJ turntable. The sound one gets is like a double-click flair, as it’s similar to the double-click flair. In order to do the twiddle scratch, keep your stronger hand (the hand u frequently uses) on the dies while your other hand is on the log. Keep your thumb against the log lightly, and tap back and forth with your two fingers while scratching the disc with your other hand. The whole procedure is given step by step.

Dissolve yeast and 1 1/2 teaspoonful of white sugar in lukewarm water. Mix until bubbly then set aside.

If you've forgotten the password to one or more of the Windows XP accounts on your computer, take heart: This video tutorial will show you how to bypass, and then change, a Windows XP start-up password. For a detailed run through of this simple Windows log-in hack, watch this video how-to.

If you want to play the Minecraft 1.8 pre-release you can try it out on a test server. This guide shows you how to download and install the Minecraft 1.8 pre-release and try out the beta on a server before the official release comes out. It also details how to uninstall Minecraft 1.8 so that you can play Minecraft 1.7.3 instead if you have problems starting or playing the newer version.

Needing to load website content with AS2 into Flash? You've come to the right place. In the following video, learn how to load text from a text file sitting on a web server and display it in Flash using dynamic text and Actionscript 2.0. Also taught? How to load a jpg, gif, png, and/or swf file using Actionscript 2.0. All files loaded into the flash movie within this video will be loaded from an external web server.

A Membership Provider allows a web application to store and retrieve membership data for a user, and the standard ASP.NET Membership Provider uses pre-defined SQL Server tables. In this video tutorial, Chris Pels shows how to create a custom membership provider that uses custom SQL Server tables separate from the pre-defined tables used by the standard provider. The principles covered in the video will apply to creating custom membership providers using other databases such as Access or Oracl...

Hello everyone, In this video I will be going over what in my opinion are the top 10 bukkit plugins to make a great minecraft server. First thing I would like to state is that Essentials or commandbook was not featured in the video because I didn't want to feature something that big (or essential). I would also like to say it really does matter what kind of server you are going to be running becuase different types of server need different types of plugins.

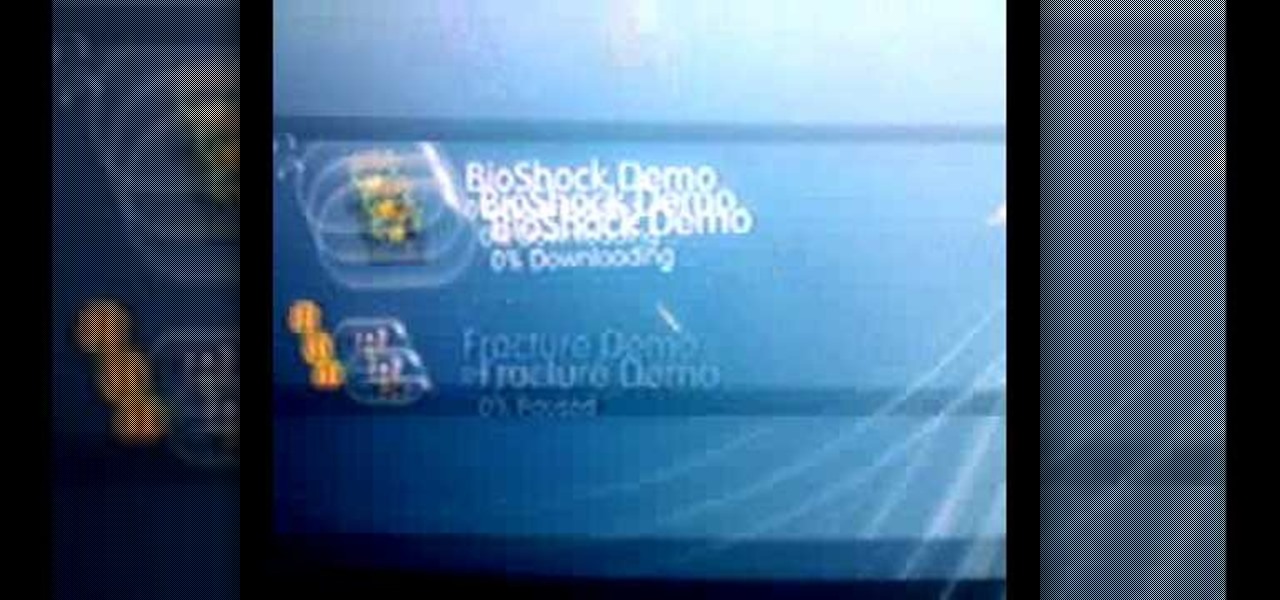
In this video we learn how to use a proxy server to hack PS3 store. First, go to settings and then internet settings. From here, go to the custom method and then click continue until you see the option for a proxy serve. Then, enable this with it and make sure all your connections are automatic. Then, your internet connection will be tested. When it's finished, test out the connection to see if it's working. Then, go to the PS3 store and you should be able to hack it using your proxy server. ...

In this clip, you'll learn how to get started using Symantec Backup Exec to protect SharePoint & Exchange servers. It's easy! So easy, in fact, that this helpful how-to can present a complete overview of the app in just under five minutes. For more information, including detailed, step-by-step instructions, take a look.