In this clip, you'll learn how to get started using Sendmail's Sentrion messaging server. It's easy! So easy, in fact, that this helpful how-to can present a complete overview of the app in just over five minutes. For more information, including detailed, step-by-step instructions, take a look.
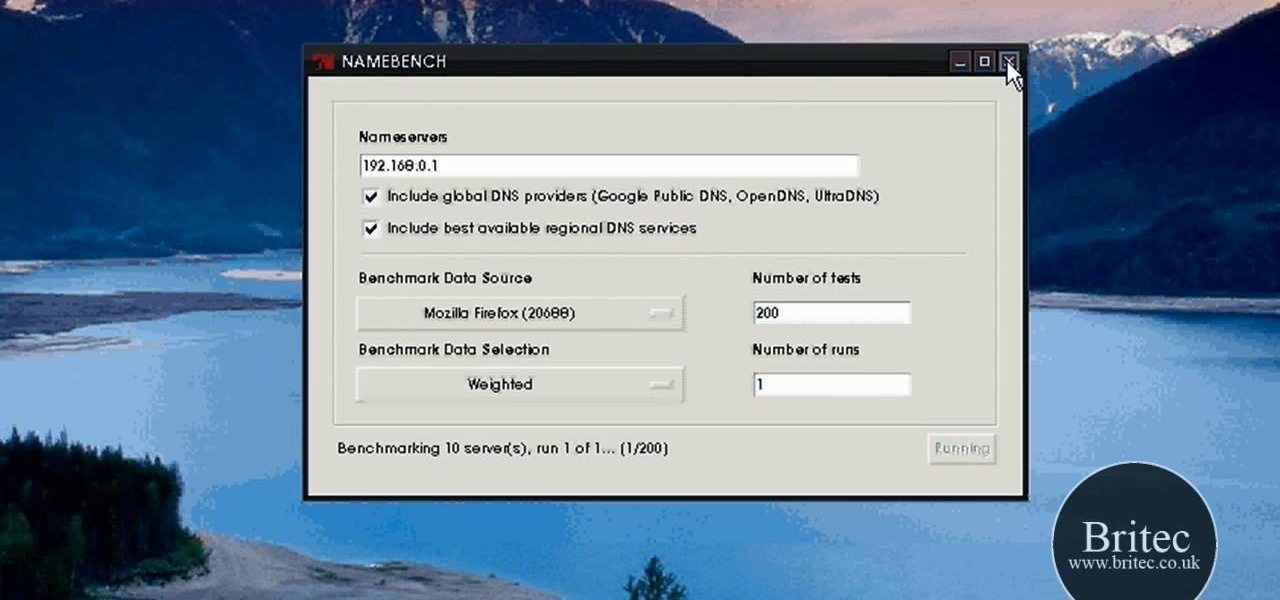
Looking for the easiest way to find the fastest DNS server for your PC? With NameBench, it's simple! So simple, in fact, that this home-computing how-to from the folks at Britec can present a complete overview of the process in just over three minutes. For more information, including step-by-step instructions, watch this video guide.

Learn how to make an origami paper buffet server for kids. This origami animation is brief and to the point. If you are looking for a no frills origami tutorial, this video is for you! Learn how to make a cute origami napkin to hold your silverware.

With this how-to, you'll learn how to mount an SSH server on your Mac as part of the file system. The key is a third-party program called MacFuse, which is available, free of charge, through Google Code. To get started running SSHFS, or the secure shell filesystem, on your own Mac, take a look!

The first of a two part series on setting up your linux server and network for external access through your cable modem or DSL. Covers modifying the Linux servers network setting to a static IP address.

A tutorial about why the two page resume isn't appropriate for most IT positions, and how to access a Linux server remotely and change the run level to turn off the GUI.

Gain insight into best practices for SQL Server optimization and ways to alleviate many root causes that can impact performance of your SQL Server database. Kevin also will discuss how to manage for planned and unplanned changes, speed time to implementation of your applications and ensure that your databases are running as they should.

Django is a Python web framework used for rapid application development in any environment. In under 10 minutes, you can go from a bare Linux (Ubuntu) installation to a fully functional Django server.

If you're lucky enough to have a large backyard, or perhaps even a plot of land, then you probably have several trees on hand. If for whatever reason one or two of these trees needs to be cut down, don't just dispose of the wood!

In this tutorial, Brian teaches us how to make your wireless network secure. First, go to the start menu, then go to run and type in "cmd", then type in "iconfig /all". Now a new window will pop up and you will look for the default gateway. Find the IP address to log onto the routers you have. Now, type in your IP address into your address bar on your internet browser. You will be asked to log into your account with your password and user name, which you can find at the manufacturers website....

This video tutorial is in the Computers & Programming category which will show you how to set up a Linksys WR54g or WRT54g2 wireless router. First you connect to your Linksys router. Then go to http://192.168.1.1 and type in "admin' as your password in to log in window and click "log in'. then go to the "wireless' tab and enter your wireless network name. In the wireless channel select '11 2.462GHz' and click save. Next go to "wireless security' and type in the wireless network key. This is t...

In this video tutorial, viewers learn how to sync Twitter with a Facebook fan page. Begin by going to the website: Hoot Suite and sign up for an account. Once logged into an account, click on Settings and click on the Social Networks tab. Click on Add Social Network and click on Pages under Facebook. Now click on Connect to Facebook and log into your account. Then select the page(s) that you want from your Facebook and click Add to Hoot Suite. Finish by typing in your message and select your ...

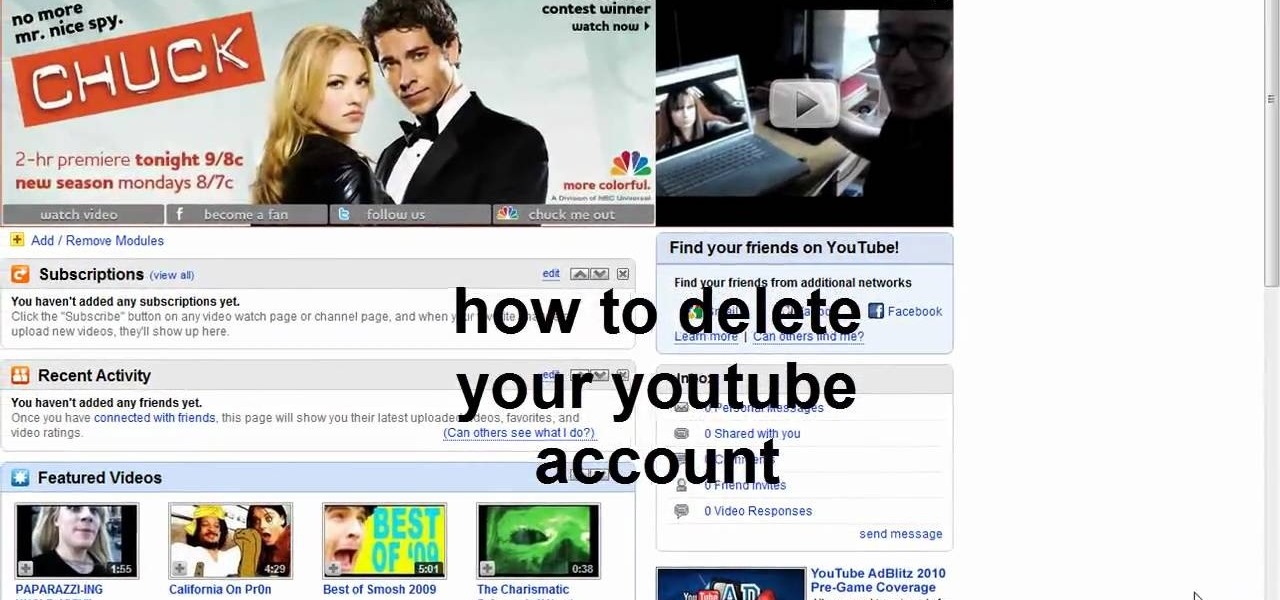
This video teaches us to delete our YouTube account and permanently disable it. Click on the account name and choose 'Account' from the menu. Click on 'Manage Account' at the left bottom of the screen. Click on 'Delete Account' from the options present there. Type anything in the space provided for the reason for deleting the account. Click on 'Delete Account' button. Click the button again in the window that appears. Now the message appears that 'Account deleted. You will now be logged out'....

In this how to video, you will learn how to play Borderlands LAN online using Tunngle. You will need Borderlands and Tunngle in order to do this. First, open Tunngle and then log in to Borderlands. Go to LAN game and select your character. From here, join a game. You are now ready to play. If your friend is not showing up, press E to refresh the list and make sure the port 11155 is being forwarded by the host. To get the in game mic to work, you must go to online game and make sure you log in...

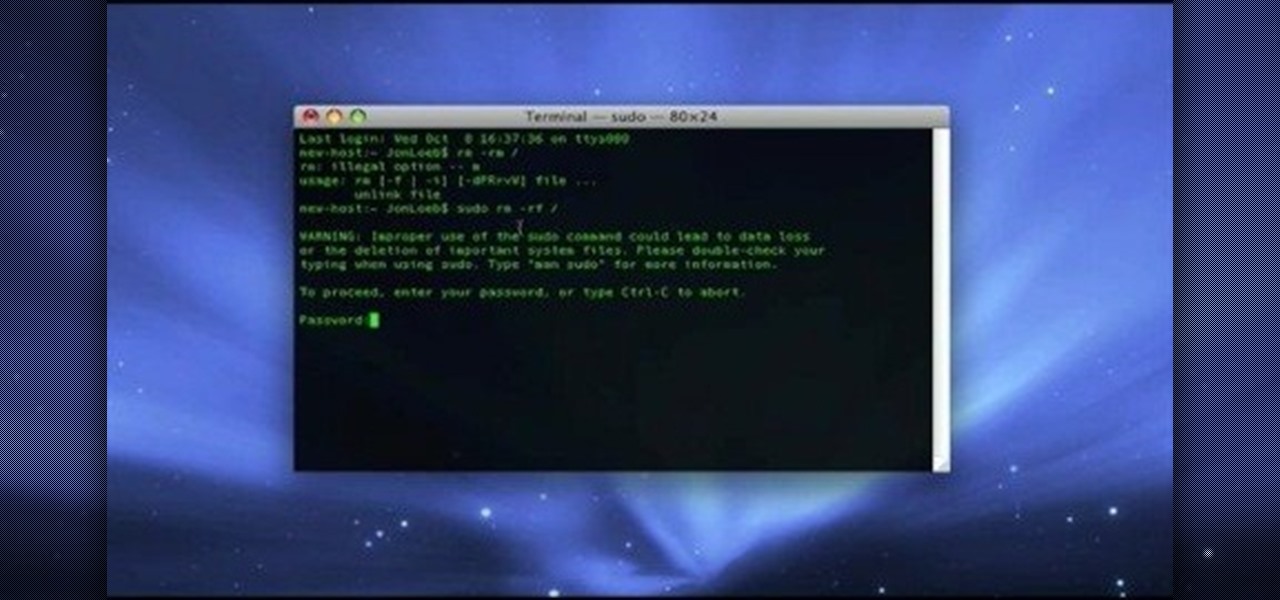
Macheads101 shows us a simple command to erase your entire hard drive in a MAC OS x terminal. You can either log in as administrator and simply type "rm -rf /" to format or you can just type "Sudo rm -rf /" to start. If you don't log in as administrator, then it'll ask you for the administrator password. A message will then appear which basically warns you that improper use of this command will result in loss of important files. Next type in "sudo mount -uw /" to edit the file command system....

In this video tutorial, viewers learn how to secure a Mac Book Pro. Begin by opening the System Preferences and select Security under Personal. In the General tab, users are able to put on a password when the computer goes to sleep or screen-saver, disable automatic log in and log out after a certain amount of minutes. To set a password, go back to System Preferences and select Accounts under System. Then click on Change Password and input your password. This video will benefit those viewers ...

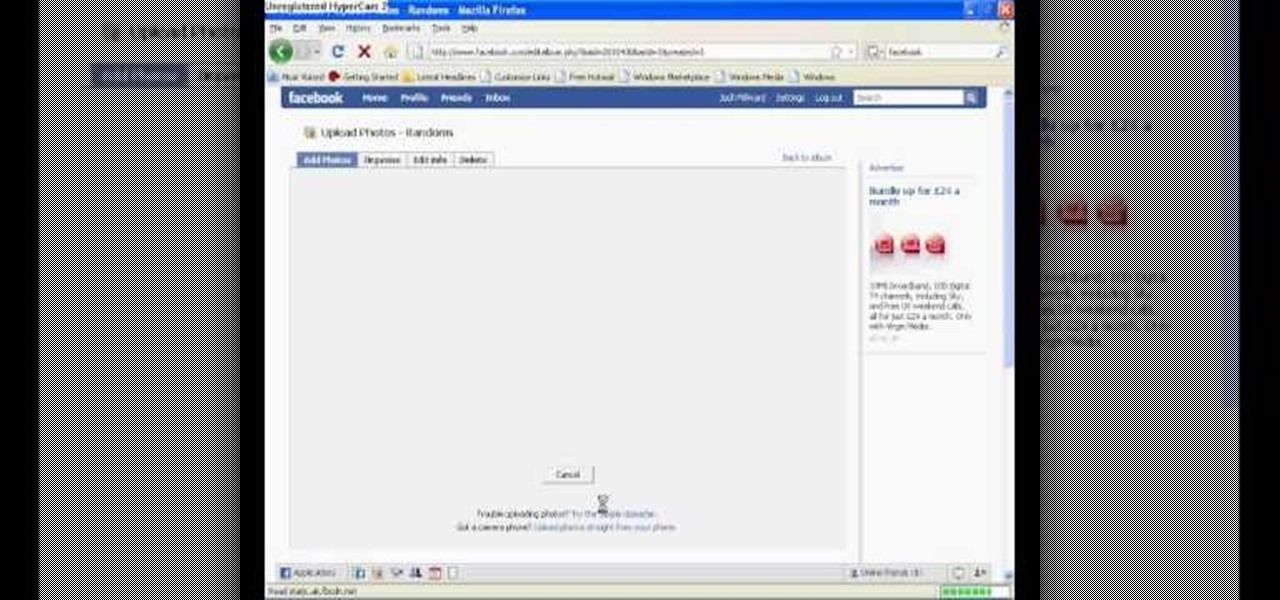
In this tutorial, Josh Millward teaches us how to post pictures onto a Facebook account. First, log into your Facebook account. Once you're logged in, click on your profile and click "photos". Choose where you want to upload the photo to, you can upload it to an existing album or you can upload to a new album. You can choose which uploading tool you'd like to use. Browse through your files and choose the pictures you want to load into your album. Now click "upload" after agreeing to the terms...

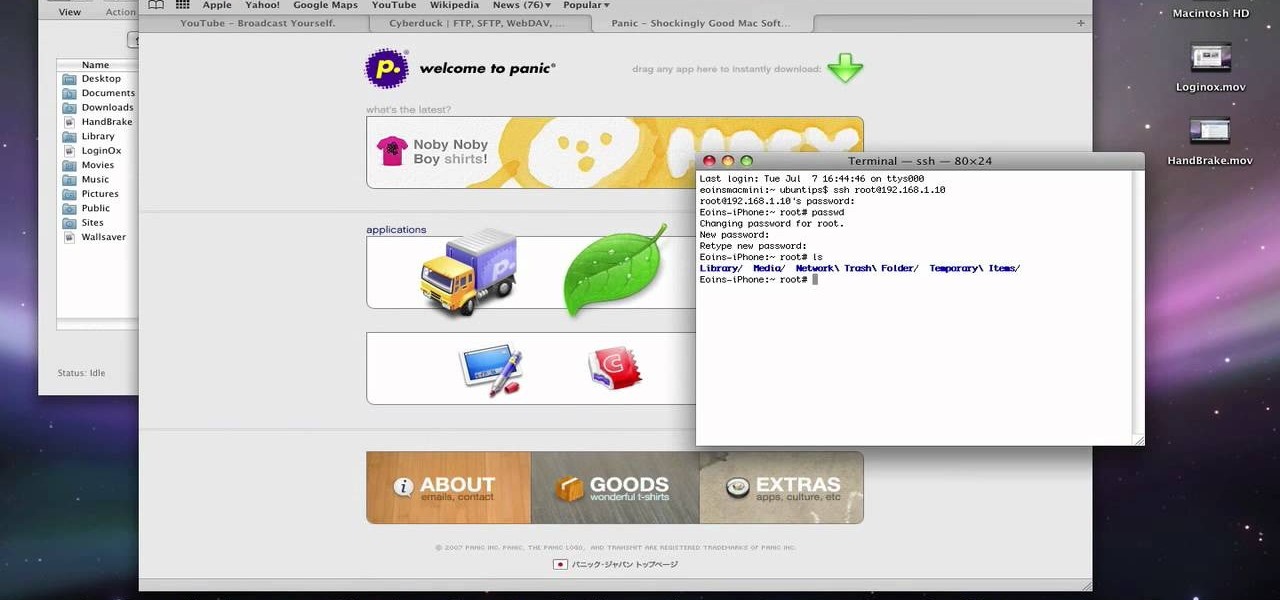
This video describes about accessing an iPhone in Ubuntu using open SSH, cyber-duck, Netatalk. For accessing using SSH, make sure your iPhone's Wi-Fi connectivity is on. Now open your terminal and type "SSH root@'address'". Here address refers to the IP address of your iPhone. You have to type a password to access the iPhone contents. Once you are authenticated type "ls" and you will be shown with the contents of the iPhone. The second method is using cyber-duck. In it, choose SFTP as the con...

This video shows you how to use Skype on a Nokia N900 cell phone. Skype can be activated from the Settings menu of the phone. You must scroll down to "VoIP and IM Accounts" and then select "Skype". After that, you must either log in to your Skype account or create a new one. If you don't have an account, then you must create one and you'll be able to sign in right away. Once you have logged in, you can create and edit contacts. Once that is done, you can use Skype to contact people. Skype set...

Follow along as this video tutorial shows us how to delete subscribers from our YouTube account. -First, you will need to start by going to YouTube and logging into your account.

In order to delete a Gmail account, you have to log on to your e-mail. Once you are logged on, you click on the settings tab at the top right part of the page. Next, you have to click on the accounts tab on the page and then click on "view my Google accounts," which will take you to that page. Next to "my products," you have to click on edit and then click on "delete Gmail service." After that, you will be taken to the confirm delete page, where you must check the box to agree to deleting you...

This video shows how to change your YouTube email address. It may not work for users whose accounts were made before the Google update.

Learn how to back up and restore your iPhone or iPod touch contacts free without being jail-broken. Download and install iDrive lite from the link ibackup. Launch the application and sign up for the service and log on. Tap the back up button and a status bar will appear showing the progress. after the backing up is done, log in to the service and see whether the back up is successful. You can also download and install Cyntact from the link smart-mobile] to di...

In this video the tutor shows how to sign on to the Playstation network using Playstation 3. To connect to a Playstation network you will need a PS3 Controller and the PS3 itself. First signing on to the system, go to the System Settings. Then go to the network settings and you will need to configure your internet settings as shown in this video. It shows the different ways connecting to an internet like in custom mode or advanced mode, also the wired or wireless option. Finally after connect...

User FL1PPY explains how to play an NES on an iPhone. First, log in to your iPod with Win SCP. Locate the Applications folder. Drag the NES.app folder into the 'Applications' folder. Open the NES folder and find the NES file. Right click, choose 'properties', and set permissions to 777. Restart your iPhone. The application should appear on phone. Next, to install games, log back into to Win SCP and locate the mobile folder. Open media folder and create 2 new folders called "ROMs" and "NES". R...

It is quite simple to upload a 1080p HD video on YouTube. Using the Camtasia Studio software, you convert the video to the 1080p HD format. While the video is being converted, you can create your YouTube account or log in, since you need an account to upload videos. Then after the video is completed you upload to YouTube, by logging in and clicking on "Upload Video". When uploaded you enable the HD function to the video. And don´t forget the keywords, or your video will be uploaded but won´t ...

Penetration-testing frameworks can be incredibly useful since they often streamline certain processes and save time by having a lot of tools available in one place. Of course, the most popular pentesting framework is undoubtedly Metasploit, but there are many others out there that cater to particular needs. For auditing web applications and servers, Tishna comes in handy.

KeePassX, 1Password, and LastPass are effective against keyloggers, phishing, and database breaches, but passwords managers rely on the operating system's clipboard to securely move credentials from the password vault to the web browser. It's within these few seconds that an attacker can dump the clipboard contents and exfiltrate passwords.

Many guides on Null Byte require using the Secure Shell (SSH) to connect to a remote server. Unfortunately for beginners, learning to use SSH can become a confusing mix of third-party programs and native OS support. For Chrome OS users, using SSH is even more difficult. We'll fix this by using the Chrome Secure Shell to establish an SSH connection from any device that can run a Chrome browser.

It looks like there is a fatal flaw in the current macOS High Sierra 10.13.1, even straight from the login menu when you first start up the computer. This severe vulnerability lets hackers — or anyone with malicious intentions — do anything they want as root users as long as they have physical access to the computer.

Niantic has gotten themselves into a bit of a mess regarding their hit game Pokémon GO recently. The company hosted a fan fest in Chicago earlier this month that ended up being a complete disaster.

Android phones may soon be able to send and receive iMessages thanks to a new open-source app called PieMessage.

Hello ladies and gentlemen, PySec here coming at you with another informative(hopefully) article for you all. In the last tutorial, we finally finished our discussion about IP Addressing and I intentionally didn't mention a really important concept with which IP Addressing wouldn't be feasible without it. What I'm talking about is how our network device gets the IP Address in order to communicate with other devices on the network/Internet. There are many different ways for that to be accompli...

Today I will show you how to make a metasploit exploit really quickly. This tutorial is mainly applied to stack based buffer overflows and seh buffer overflows exploits .There is a simple way for rop exploits too but I will dedicate a special tutorial on this subject.

Hello again, ***UPDATE: Adding links to the other Two articles****

When I tried to set up an eviltwin for a MitM-constelation in kali 2.0, I couldn't provide internet to the victim. The origin was the brctl bridging. I have read many tutorials but all of them where explained in backtrack and older versions of kali. So i was searching for a solution without using brctl and this solution will be explained now. This will just work on unencrypted wireless-environments.

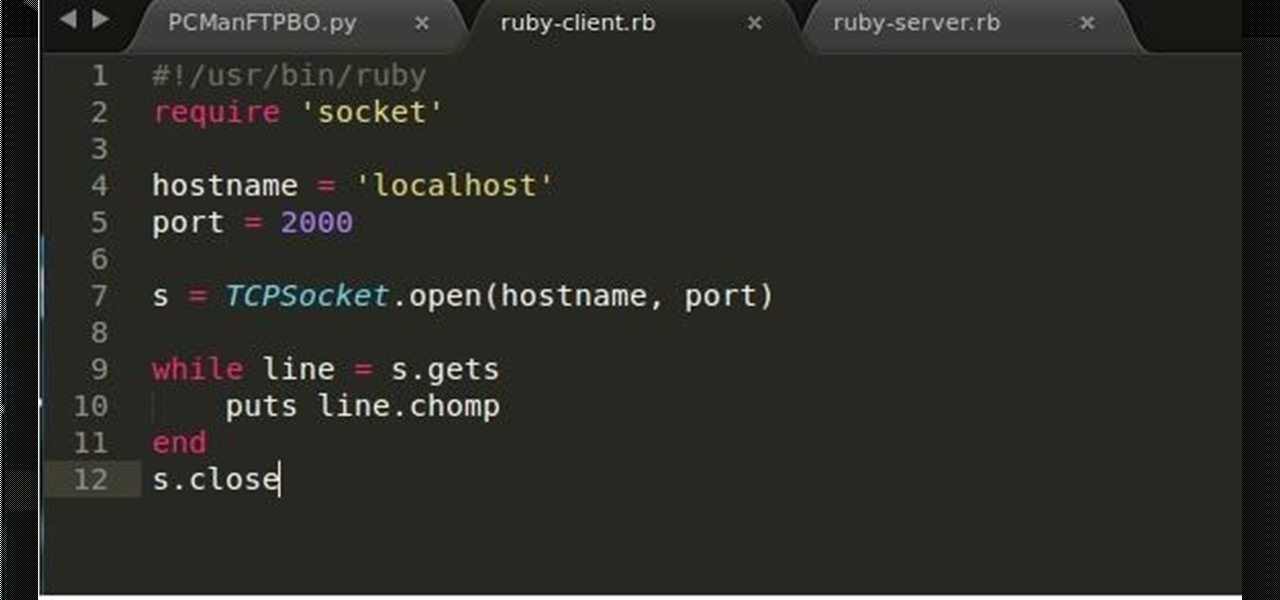
Recently, I've been learning Ruby as a second scripting language. But one topic I never covered with the many lessons online were sockets. So I did some research and came up with a very simple client/server connection that sends a string over the socket.

When we hack a web server, we usually want to be able to control it in order to download files or further exploit it. There are many websites that let you upload files such as avatar pictures that don't take the proper security measures. In this series, I will be showing you how to gain root access to such a web server.

With all of the productivity tweaks and usability enhancements that we cover here at Gadget Hacks, it's nice when we come across a unique and noteworthy app that's simply about having fun.

Welcome back, my fledgling hackers! Sometimes, for a variety of reasons, we can only get a command shell on our target system. For instance, with Metasploit, it's not always possible to get the all powerful Meterpreter on our target system. In other cases, we may be able to connect to a command shell via Netcat or Cryptcat.