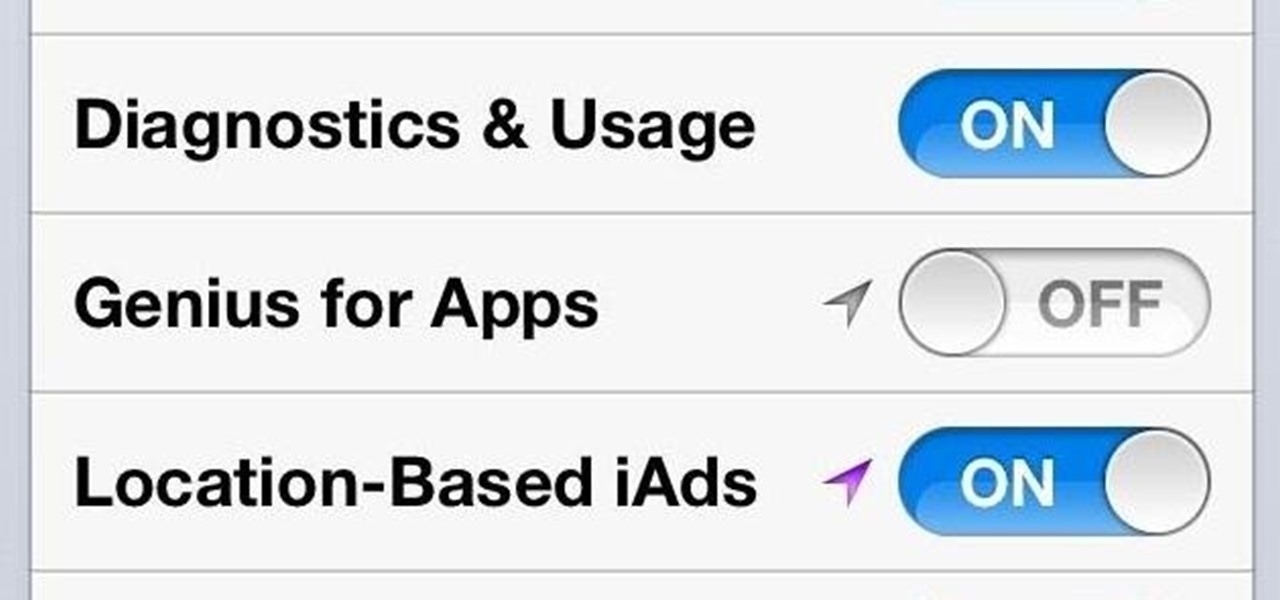
As is the case with most software updates, Android 5.0 brought changes that were viewed by users as somewhat positive and somewhat negative. This generally happens because we're accustomed to the old way of doing things, and changes, no matter how useful, can slow us down.
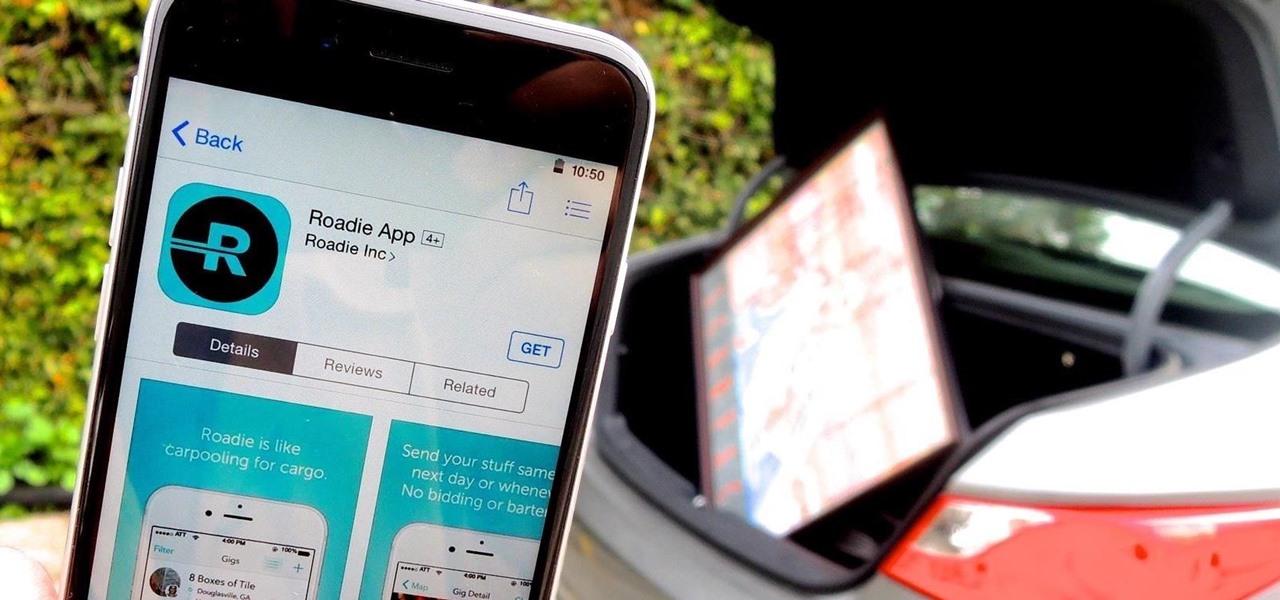
The next time you plan on going on an adventurous road trip, get paid for it! With the the new mobile app called Roadie, from developer Marc Gorlin, you can get paid to go where you're already going.

In the wake of the NSA scandal and celebrity-photo hacks, lots of people scrambled to find more-secure ways to send text messages, share emails, and surf the internet. Known for their incredibly secure data networks, Germany's email services saw a remarkable increase in new users from across the world. Last year, we covered Sicher, a German app that lets you send and receive encrypted self-destructing messages on your smartphone.
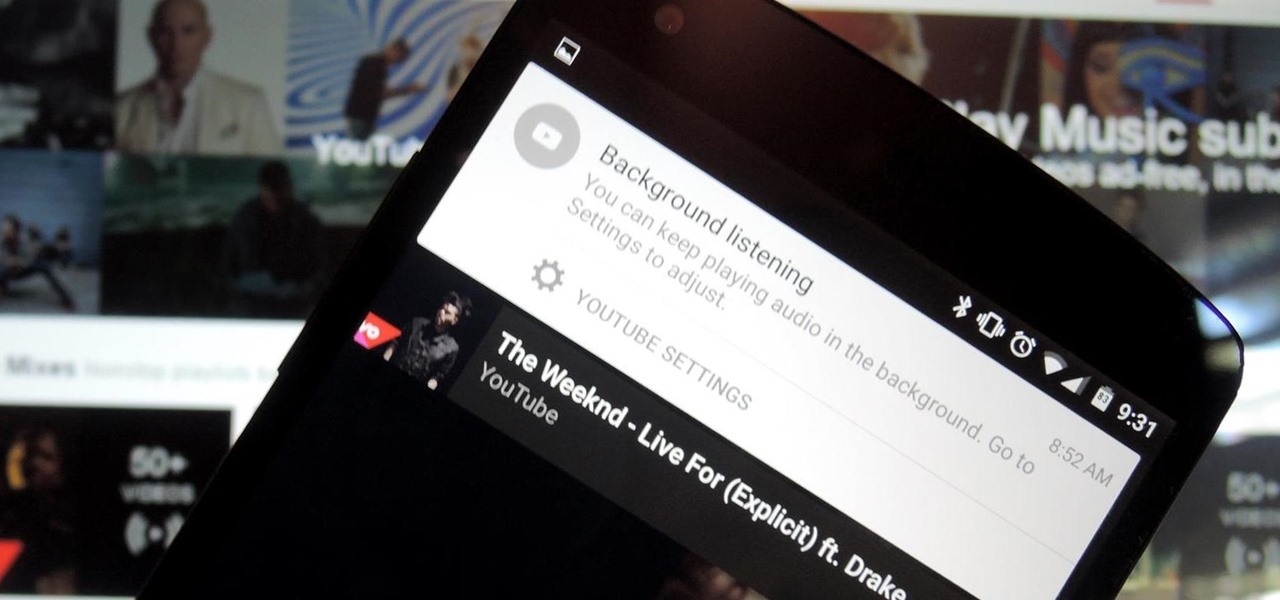
We recently showed you YouTube's new music streaming service, YouTube Music Key, with it's promise of ad-free music complete with background listening and offline play. Well, if you check your YouTube app, there's a good chance that Google flipped on the service for you. Activate the Service

Back in March, Samsung partnered with Slacker Radio to create a streaming service called Milk Music. For those of us who don't own a Galaxy device, this news was a non-starter, as it was exclusive to Samsung's flagship line of phones and tablets.
In places like underground bars or national parks, your phone's Internet service is sure to slow down to a very sluggish pace, making it difficult to surf the web. Or worst case, data will be non-existent, leaving you with only low-level network support for calls and SMS text messages.

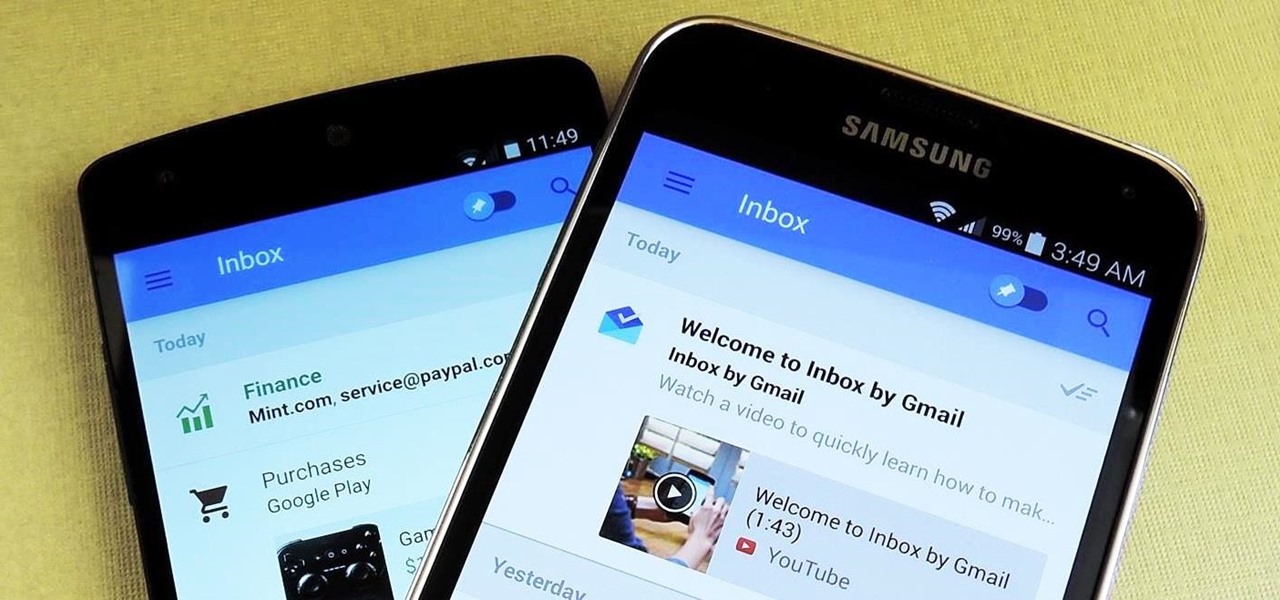
Google's new Inbox by Gmail service offers a new take on email with a particular emphasis on productivity. But, as an invite-only service at this stage, not many people can access Inbox just yet.

One of the biggest improvements in Mac OS X Yosemite came to the Spotlight search feature, allowing users to not only search through their applications, but also their emails, text messages, iCloud, and the web.

A musical hiccup during a DJ's set can completely ruin the mood, and that same feeling can definitely translate to mobile listening as well.

Sharing files has always been one of Android's greatest strengths. A system of "share intents" allow apps to freely exchange data with each other, making it possible to take a picture with your favorite camera app, then send it over to your choice of photo-sharing apps, for instance.

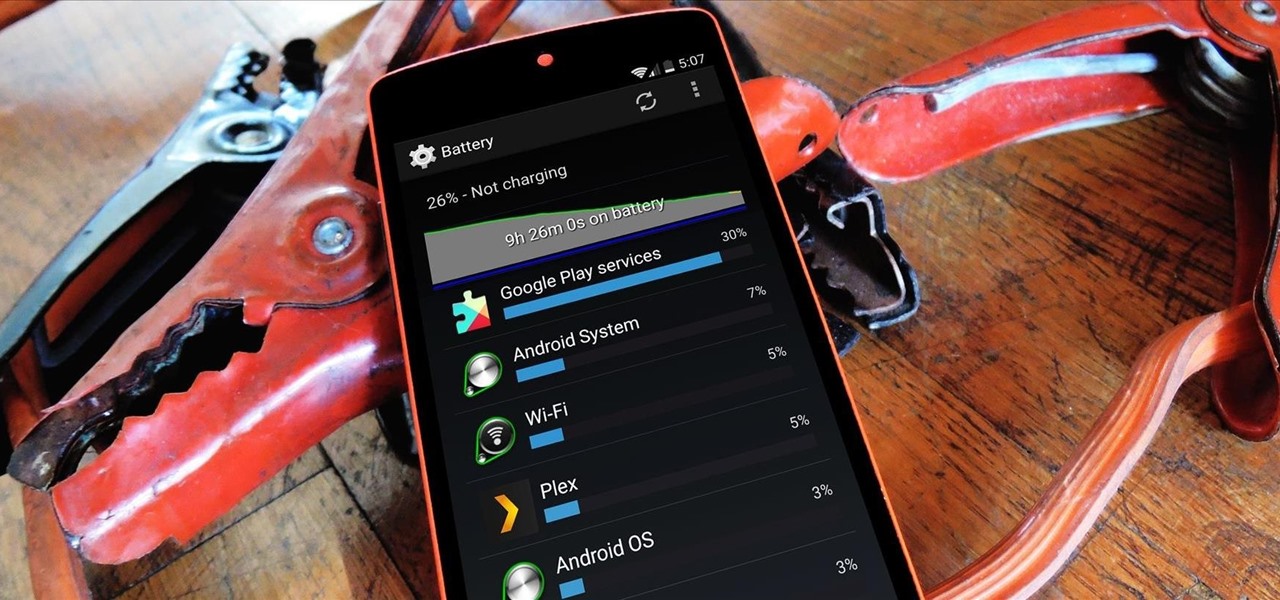
An app can request a wakelock to prevent your Android device from entering sleep mode so that it can sync data in the background. This obviously drains your battery, because instead of running in low-power sleep mode, your processor is fully activated while it performs its tasks.

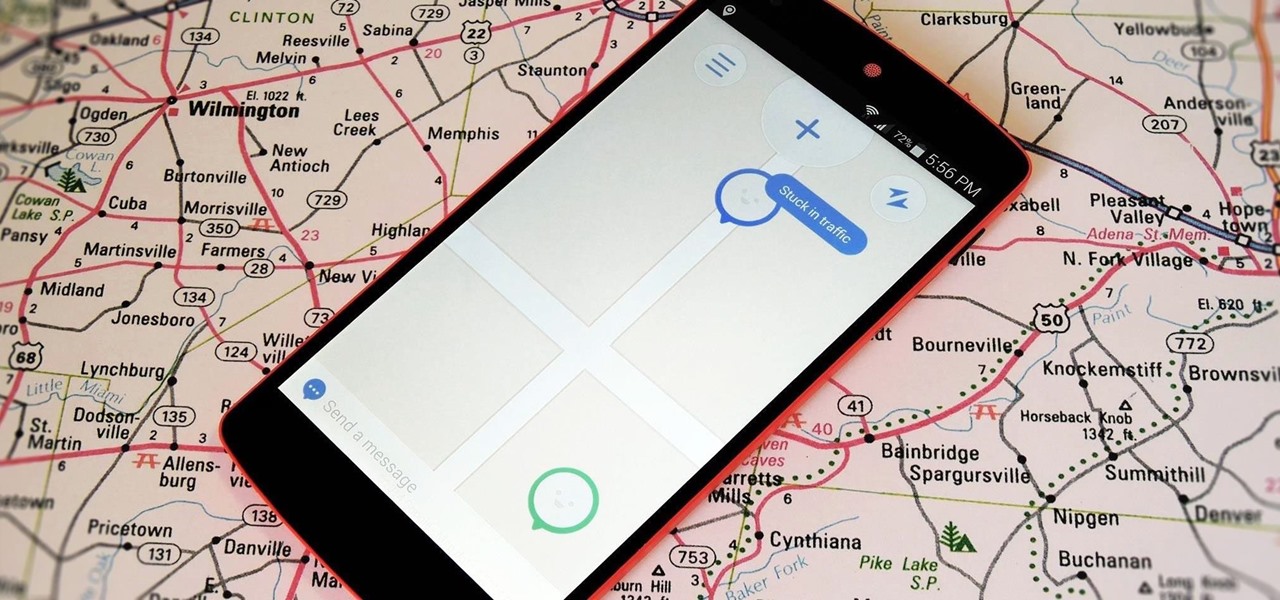
With GPS chips and Wi-Fi positioning systems, a modern smartphone is capable of tracking its user's location with pinpoint accuracy. This being the case, it's strange that the most common text message sent today is still "Where are you?"

There will always be a time when you're not entirely sure what you're doing with a certain subject. But the days of weighing the pros and cons yourself are coming to an end. Whether it's a common quandary like "Where should we eat?", or a more specific question along the lines of "Should I buy this shirt or not?", you can now simply AskInternets.

It's hard to believe it's already been a year since I was frantically searching every Best Buy in the Los Angeles metropolitan area to find one with a Chromecast in stock.

Gaining major consumer support and the ire of Big Cable, Aereo today announced support for the Chromecast through it's Android app. A revolution for cord-cutters, Aereo lets you record and stream live broadcast TV on your computer, smartphone, tablet, or media streaming player (Apple TV, Roku, and now Chromecast).

The folks behind StumbleUpon have created a video service that is just as awesome at introducing you to new content as their website service is.

Many of us were left scratching our heads when the iOS 7 update removed the Twitter and Facebook options from the Notification Center. Allowing you to quickly tweet and post Facebook updates, these were features used, and missed, by many—including me.

Streaming apps like Netflix, Hulu and Amazon Instant Video have been available on game consoles for a while, but if you're in a country where they're blocked, it can be hard to find a way around. There are apps and extensions like Hola Unblocker and Media Hint and that to bypass location restrictions on your computer, but what about your Xbox?

Gmail is a free, advertising-supported email service provided by Google. Users may access Gmail as secure webmail, as well as via POP3 or IMAP4 protocols. Gmail initially started as an invitation-only beta release on April 1, 2004 and it became available to the general public on February 7, 2007, though still in beta status at that time. The service was upgraded from beta status on July 7, 2009, along with the rest of the Google Apps suite.

The design of iOS 7 has its lovers and haters, and if you're an Android user who just happens to love it, there are plenty of ways to make your device feel more Apple-y.

Welcome back, my hacker novitiates! Finding vulnerabilities in systems can be one of the most time-consuming tasks for a hacker. There will be times, though, when you'll find yourself in a position that you know that a particular port represents a vulnerable application or service.

When the HTC One was announced, the fact that its IR transmitter was a side note more than a main feature made me dismiss it. When Samsung included one in the GS4, it became even less impressive. However, now that I actually have a One, I find that the "TV" app is way more than just one of Samsung's "S"-gimmicks. Step 1: Set Up Your Service Provider

Newsletters, subscriptions, and receipts are all necessary evils that come along with online services and shopping, and they take up a significant amount of space in a lot of people's inboxes. If you've ever signed up for an account on a website, chances are you've gotten an email from them.

Prepaid phones are becoming more and more popular, and tons of people can see the benefits of switching now that some companies are offering prepaid services that are on par with the big players. For a lot of folks, the only thing keeping them from switching is the huge early termination fees that service providers charge to break a contract early.

When was the last time you bought a CD? Most of us listen to music through a number of digital channels—MP3s, Internet streaming services like Pandora and Spotify, and satellite radio, to name just a few.

While putting content and information online gets easier every day, it seems like getting it back is only getting harder. In a lot of cases (we're looking at you, Facebook), once you upload something, it's forever in the hands of someone else. That's where The Data Liberation Front comes in. Believe it or not, The Data Liberation Front is a team of Google engineers who work to make it easier for users to take their stuff back whenever they feel like it.

As if iOS 6 wasn't under enough scrutiny, a new issue has surfaced regarding the App Store for iOS 6 on the iPhone and iPad. According to users, the application store is very sluggish and doesn't load properly. Below is a video of just how slow the application store is.

Dropbox announced Tuesday that a recent security breach compromised a list that included the email addresses of certain Dropbox users. To avoid future complications, the service announced that it would be implementing two-factor authentication, and even more useful, a security page that lets you monitor all activity on your account. In light of this and other recent web security threats, you might also want to know that services like Gmail, Facebook, and Yahoo! Mail have similar pages where y...

To properly set a table for an informal four course dinner, keep in mind that a soup course, a salad course, an entree and a desert will be served. First, add the service plate or charger to the table. Place it directly in front of the guest two inches from the table. It will serve as the under plate before the entree arrives. Use exactly the amount of silverware needed to accommodate the meal. For this meal, you will need a soup spoon, a salad fork, a salad knife, a dinner fork, a dinner kni...

How would you like to be able to watch all of the movies and television shows available on the Netflix watch instantly service on your HD2 Android phone? Check out this video to learn how to download the Netflix app.

Check out this basic back-to-school look that's also great for daily work and church services. It's a neutral makeup look with very little shimmer. It only takes about 5 minutes to create these beautiful eyes! Watch and learn how to apply these eyeshadows and cosmetics.

Want to receive daily, weekly or monthly updates on a subject of your choice? With Google Alerts, it's easy! So easy, in fact, that this home computing how-to from the folks at Easily can present a complete (and somewhat talky) overview of the process in just under five minutes' time. For the specifics, and to get started setting up and using Google Alerts yourself, just watch this handy how-to.

This tutorial will show you a super simple way to get free ringtones for your iPhone. This method will let you bypass iTunes's expensive ringtone service and create your own - anytime, from any song and for free!

This is an Apple iPhone video tutorial that will show you how to unlock an Apple iPhone 2G or 3G for use with another mobile phone service provider other that AT&T. If you are using a Macintosh computer, you can unlock both the 2G and the 3G phones. If you're using a PC, then you can only unlock the 3G iPhone.

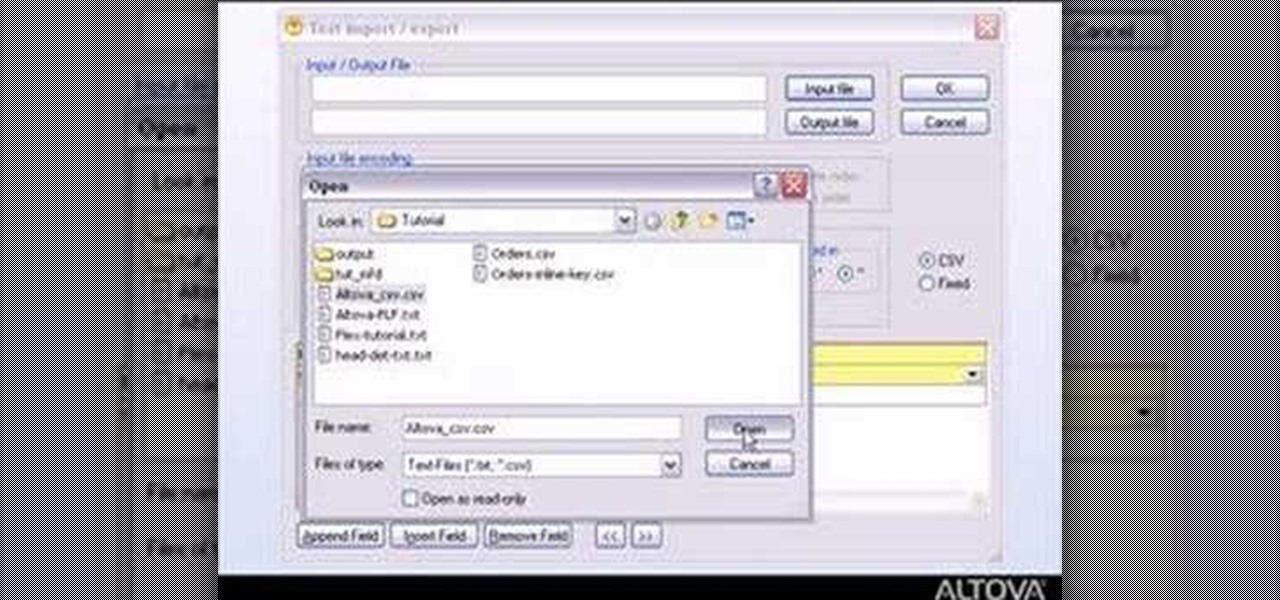
MapForce supports flat files as the source and/or target of any mapping involving XML, database, EDI, web services or other flat file data. In this how-to, you'll find instructions for mapping data from arbitrary text files (such as log files, CSV, fixed-width, and other legacy data sources) to databases and XML files.

The Prada cell phone (the LG KE850) is a unique, sophisticated and elegant mobile phone with the first complete advanced touch interface.

Watch this how-to video to learn how to get 30 days of Xbox Live Gold for free just by pretending you don't want it. Xbox Live Gold is normally a subscription service, but you can get 30 days of it for free by following the tips in this how-to video.

In this how to video you can learn to create a punk, goth, emo red Avril Lavigne inspired eyeshadow look. This makeup tutorial uses the following products:

An installer shows some tips to help remove your trialer hub so it can be serviced and then reinstall it so your wheel can be remounted.

Just some suggestions and roughly the way I handle calls. There is more than one way to do this and every call is different. Enjoy!