Many operators use elevators to control access to particular floors, whether it be the penthouse at a hotel or a server room in an office building. However, the law requires them all to have a fire service mode, which gives emergency access to restricted floors, and a hacker can use that to bypass security altogether.

Since its introduction, the Bixby button has been a big point of contention among Galaxy fans. Many view the dedicated button as a wasted opportunity, which they argue could be put to better use if Samsung would let them use it for other commands. Thanks to an awesome app, you'll be able to remap the Bixby button on your Galaxy S9 to perform almost any function.

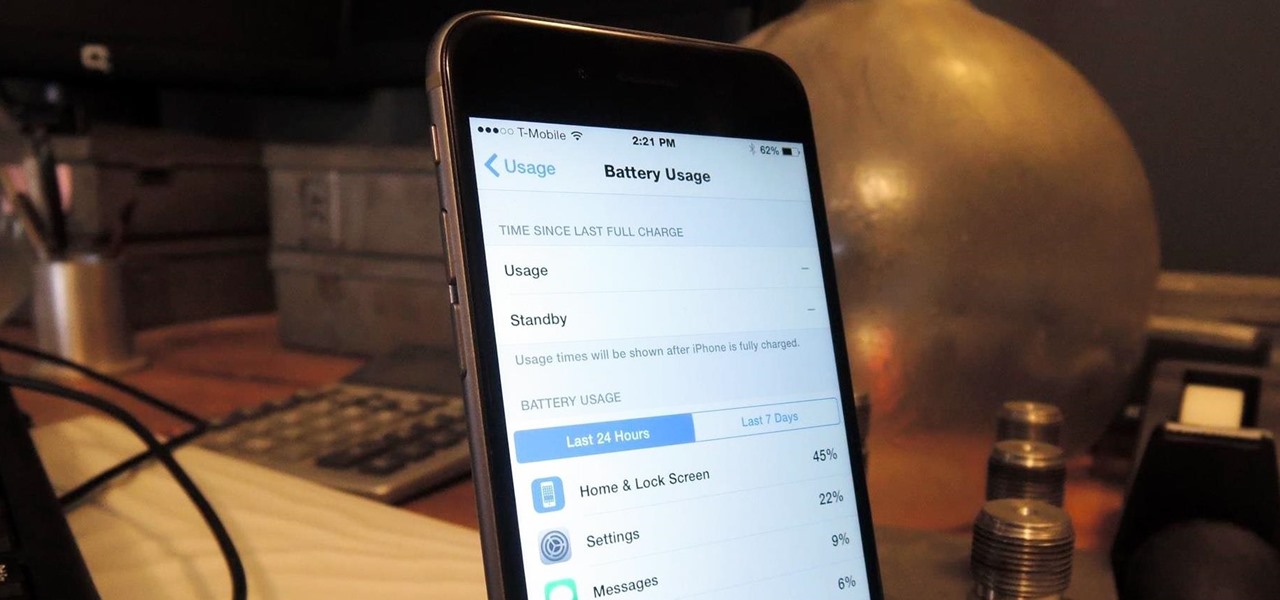
Before, the only way to really tell how your iPhone's lithium-ion battery was performing was to use tools such as Geekbench and Battery Life, but now Apple has included some quick battery health checks right into iOS 11.

Amazon Web Services (AWS) opened its re:INVENT developers expo with a bang by launching Amazon Sumerian, a new tool that could become the dominant platform for building cross-platform augmented and virtual reality applications.
One of the best parts of being an Android user is the countless awesome features. Many of these features are well-known and user-facing, like custom icon packs and launchers, but some get lost in the shuffle. Back at Google I/O 2016, Android Instant Apps were introduced to developers and enthusiasts. Since then, the feature has seen a wider rollout, but few users are aware of it.

If you own a Porsche, there's a good chance you're interested in two things: speed and quality. Porsche Cars North America wants to extend that experience from the driver's seat to the service center.

A partnership between augmented reality company Zappar and IoT services provider EVRYTHNG will bring AR experiences to consumers while supplying market data to brands.

Virtual private networks, or VPNs, are popular for helping you stay anonymous online by changing your IP address, encrypting traffic, and hiding your location. However, common IoT devices, media players, and smart TVs are hard to connect to a VPN, but we have a solution: Turn a Raspberry Pi into a router running through PIA VPN, which will ensure every connected device gets the VPN treatment.

Influenced by the growth of augmented and virtual reality technology as well as 3D computer vision, Ericcson Ventures invested in Matterport, whose hardware and software help companies create AR/VR experiences.

The USB Rubber Ducky comes with two software components, the payload script to be deployed and the firmware which controls how the Ducky behaves and what kind of device it pretends to be. This firmware can be reflashed to allow for custom Ducky behaviors, such as mounting USB mass storage to copy files from any system the Duck is plugged into.

Cruise Automation is actively seeking to recruit a lead engineer to head its development efforts of 3D maps with expertise in city environments, signaling the GM driverless unit's move towards a mobility-as-a-service business model.

The US driverless market has become a competitive – and crowded – arena, with big names like Google, Apple, Uber, and even Intel intent on leading the pack. Not to be outdone, the EU is also getting in on the automated car action with self-driving fleets launching in both the UK and the Netherlands within the next two years.

Who pays for live TV anymore? Better question, who watches live TV anymore? With a ton of streaming services available, there's no room in our lives for things like schedules, commercials, or going weeks between episodes. (What is this, 2010?)

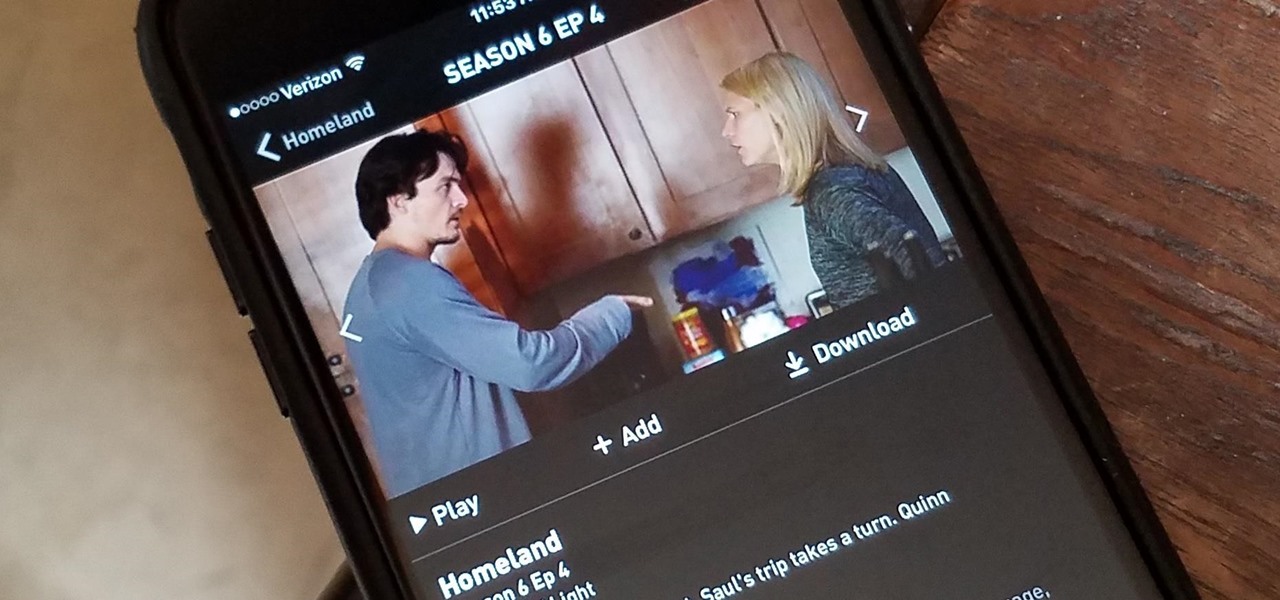
Have you ever wanted to catch up on Homeland or Shameless, but are out and about and don't want to use up your data? Those problems are for days of old now, as Showtime has announced their mobile app will allow titles to be downloaded and viewed without an internet connection.

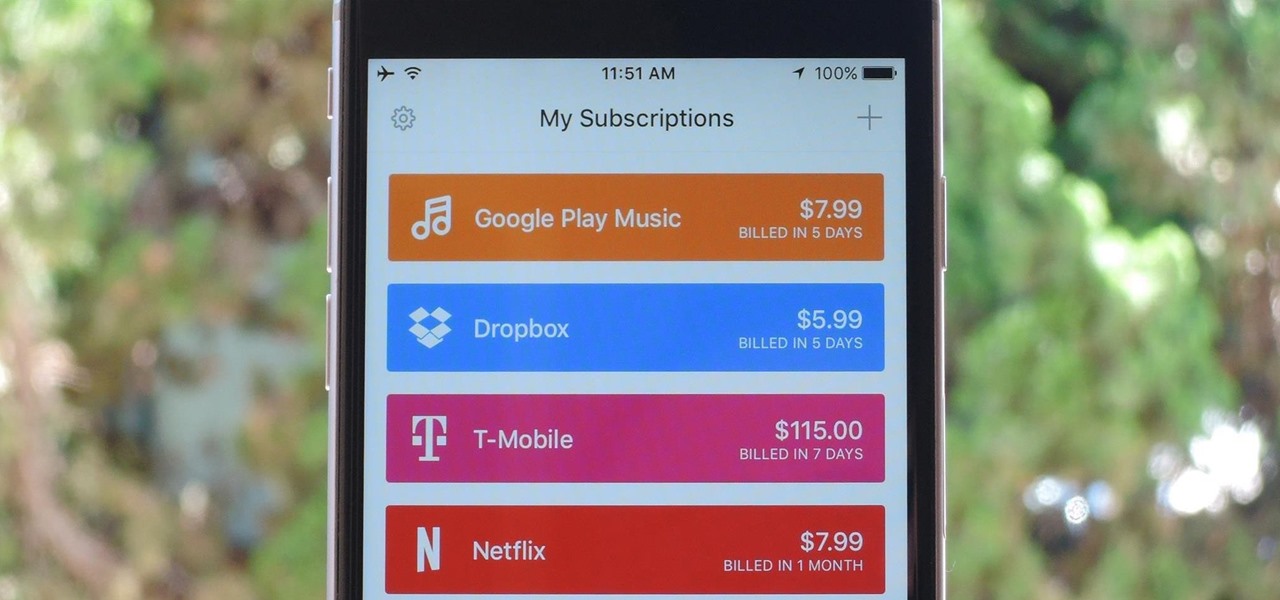
As the internet continues to become a bigger part of our day-to-day lives, we slowly but surely start to rack up a bunch of web-based subscriptions. These internet subscription services—Netflix, Hulu, and Amazon Prime, just to name a few—may seem innocuously cheap individually, but when combined, they actually comprise a significant portion of our monthly bills.

Android's personal assistant is more than just a sassy backtalker—it's a full-on suite of all the information you could need at a given time. Google Now, as it's called, uses data from various sources to predict what you'll want to know before you even search for it, and it's an amazing experience once you've got everything set up.

Cellular carriers like to nickel-and-dime us out of every bit of money they can feasibly justify, so as consumers, we owe it to ourselves to make sure that we're getting our money's worth.

Welcome back, my neophyte hackers! Metasploit is such a powerful tool that I can only scratch the surface of its capabilities here. As it has developed over the years, it is now possible to use Metasploit for nearly everything from recon to post exploitation to covering your tracks. Given its versatility, every aspiring hacker should have at least a tentative grasp of Metasploit.

School internet filters serve a valid purpose—they keep students from wandering off into the deep corners of the web while still allowing at least some internet access. But a lot of these restrictions are completely ridiculous, to the point where some school districts block access to the educational material in National Geographic or forbid searching terms like "China," "Iran," or "Russia"—because, you know, breasts and commies.

You'll have to forgive me if I sound a little overexcited about this, but in my opinion, Google's "Now on Tap" is one of the most innovative™ smartphone features that I've seen in years. Sure, Microsoft heard about the feature being in the works and rushed out a similar Android app so they could say they were first, but that solution pales in comparison to this one.

In this tutorial I am going to look at what services are running on our Metasploitable machine and setup firewalls. This is more basic scanning of our machine to get an idea of how to get in. Obviously in a real engagement you would want to do research on Google and whatnot to find out as much as you can about your target but this series isn't about all of that.

Remember portable MP3 players like the classic iPod? Seems like forever ago that they were all the rage, and I don't think I've seen a real one in the wild for a good 5 years now. These devices died out so quickly as a direct result of the onset of smartphones, which allow us to do everything that an MP3 player could do and then some.

This tutorial is for those who've purchased an account with Private Internet Access to hide your VPN and would like to set it up in Kali. Please note, you can chose to run your PIA service from your Windows computer without configuring it in linux as long as you'll be using a NAT connection. Using a NAT connection will allow your Windows machine and Kali Virtual Machine to use the same IP address, hence if your IP is hidden on one, it will be hidden on the other.

There is much to be learned about Apple Music and the revamped Music application introduced in iOS 8.4. Throwing their hat into an already competitive field with other companies like Spotify, Tidal, or Rdio, this is a bold move on Apple's part. So, before you consider signing up for the new streaming service, let's take you through all the changes and features you should know about before doing so.

Google constantly adds useful little features to stay on top of the search engine heap. Recently, we've seen them add "Find my phone" functionality, as well as the ability to set alarms and send directions to your Android phone or tablet.

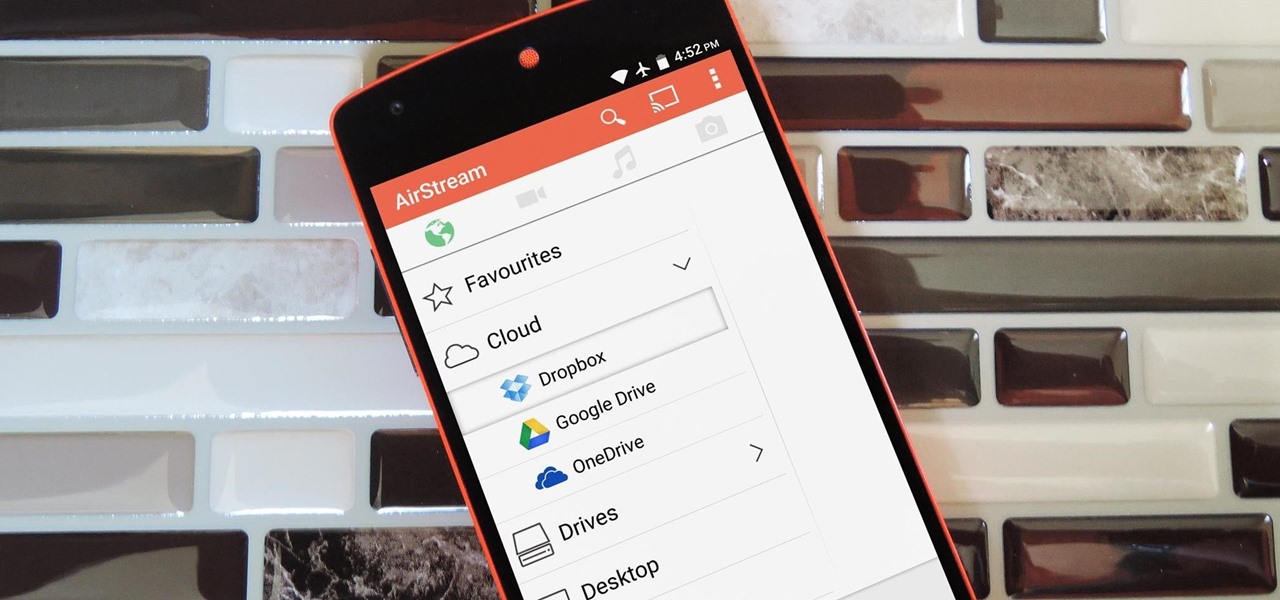
Smartphones generally have limited storage, but counter this issue with an always-on internet connection. This led to the proliferation of cloud storage services, which allow us to store and access our large media libraries remotely.

We previously showed you how to make your Android's LED notification light dance to music, but the app itself was limited in customization options, the devices it worked on, and the music apps and services it worked with. Now we'll be showing you a similar app that supports more music services and lets you select which colors will display through the LED.

It's been a long time coming, but HBO will finally be releasing their cable-free streaming service next month in the U.S., over two years after they had released similar standalone subscriptions in countries such as Norway.

Probably SSH is not as clean and fast as other useful tools like netcat, but it has some features which are very useful, and when you'll need them, here's how to behave with that huge amount of computers all over your house.

The new iPhone 6 and 6 Plus are supposed to last a lot longer in your pocket with improved battery life, but that doesn't mean that iOS 8 will be that friendly on your older iPhone model. All of those awesome new features could be killing your battery, but with some simple tweaking, your battery life concerns will be a mere afterthought.

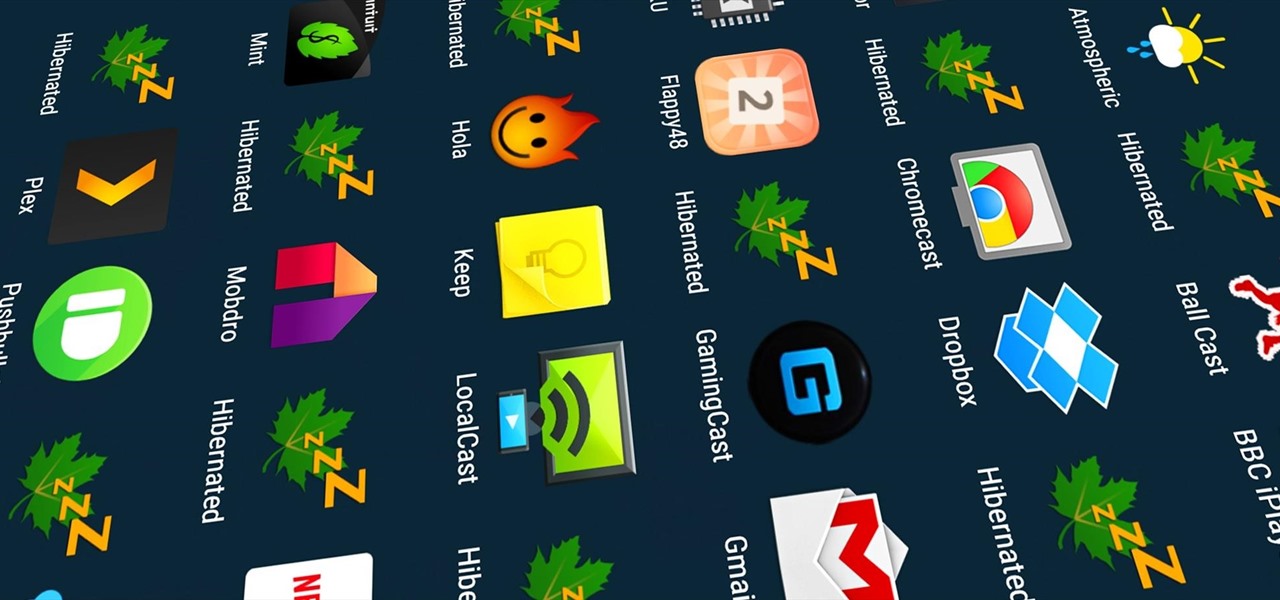
Greenify is a terrific app that allows you to put battery-hogging apps into "hibernation." Effectively closing the problematic apps and preventing them from running until you explicitly launch one of them, hibernation is a great way to save battery life while you're not using your phone.

When the Nexus 5 debuted, one of its coolest features was the fact that you could say "OK Google" any time you were on the home screen to launch a Google Voice Search. This feature was ultimately made available for other devices by way of the Google Now Launcher.

Netflix releases monthly reports on major ISPs relating to how well their service works on each provider. The purpose is to educate the public on their choice of service provider, but since many of us hardly have any choice at all when is comes to an ISP, it backhandedly works to shame them (if they're even capable of feeling shame under all those millions of dollars).

Recently, Mike over on Samsung Galaxy S4 softModder showed how to scroll from the bottom to the top of a page with a single tap, a feature that Apple is well known for, and something I missed very much on my Galaxy Note 3. However, there's always room for improvement.

Welcome back, my novice hackers! I've written a couple of articles on reconnaissance and its importance, and as I've said before, a good hacker will spend 3 to 4 more times doing reconnaissance than actually exploiting the system. If your recon isn't good, you'll likely fail, or worse—end up serving time and becoming Bubba's wife for a couple years. I can't say it enough—recon is critical.

UPS gives you all the tools you need to take away the complications and confusion of international shipping. UPS provides simple, step-by-step online instructions and helps guide you through the required documentation to reduce the likelihood of customs delays.

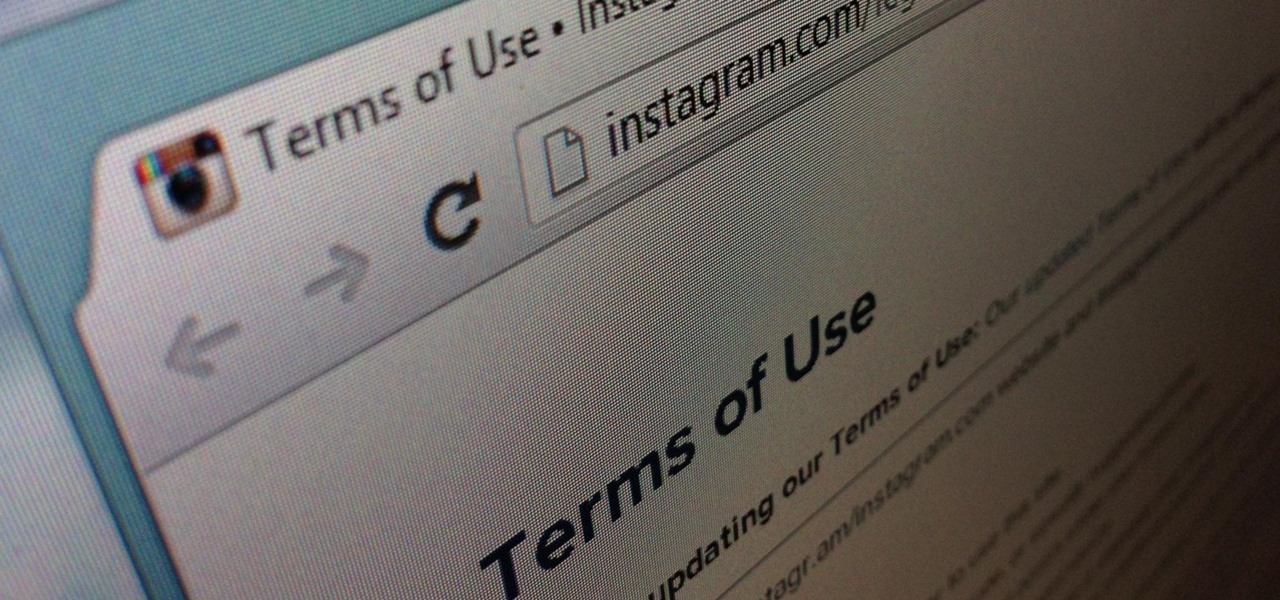
Every so often, a big site will make a change to its terms of service that's not so great for its users—without even informing them—and they (understandably) get really pissed off. Recent examples are Facebook's and Instagram's changes, which resulted in user backlash.

Instagram's controversial terms of service update this past month has spurred an onslaught of dismay and anger from users of the popular photo-sharing social network. The specific set of the new terms that set off this firestorm basically said that businesses could use your uploaded photos for advertisement, without you receiving any of the profit.

It always sounds like a good idea to throw a party... until the party gets there. Next thing you know, you're running around hiding anything breakable, and once everyone leaves, you're stuck cleaning up the mess. But the worst part is footing the bill for everything, and if you don't charge at the door, your chances of getting anyone to chip in are slim to none once the party starts.

Feeling a little slow when you're running around in Battlefield 3? Find out how to run faster by using jumps while you sprint forward. This guide will show you exactly how to use the jumps so that you don't slow down.