In this video the instructor shows how to hide any kind of file in a .Jpeg image file. To do this take the image in a new folder. Go to start button and then to run. Type cmd in the run and hit enter to open the command prompt. Now browse to the directory that contains the picture and also the file that you want to store using the CD command. Type the command to create our required file as shown in the video. Now a new file will be created that contains your image as well as the file that you...

In this video the instructor shows how to choose options on a batch file. In a batch file if you write the command '@ echo off', the person running the batch file cannot see the commands being executed. You can use the 'if' condition to make the program execute either of two commands depending on the condition. While writing the if statements make sure that there is space between the 'if' and the '%' sign. If you write 'shutdown -t 30' command in your batch file, then the batch program when r...

Is your Mac running slow? If yes, then the instructor in this video shows just how to diagnose and fix it. It is not an uncommon problem that a Mac begins to get slow with time. Though there are a million different things that can slow down a computer and it is never easy to pin point the problem, there are a few things that you can do to try and get it fixed. The first thing that you should do is check the free space in the hard disk drive. If it is less than 10 percent then you better start...
This video shows you how to easily remove the tracking Cookies from your web browser. Normally, if you use AVG Free, it will detect the tracking cookies but not delete them. This video will show you how to manually remove that tracking cookies without using any software. The first thing you have to do is click Start menu, then search for Run. In the Run windows, paste the following: C:\Users\YOUR PC NAME\AppData\Roaming\Microsoft\Windows\Cookies , and hit Ok button. Delete all the files that ...
Now your computer is running slowly while opening the multiple programs, and for checking mails. The following steps easy to get faster the computer.

This is a directional video of how to increase the speed of a Windows Vista PC. The first step is to uninstall programs that you do not use. Then you want to go into MSCONFIG and remove unnecessary start up entries. You can also configure the performance options of your computer in the computer's properties. The next step is to go to the system tools and run Disk Cleanup. It is also important to run the Defragmentor from the system tools.

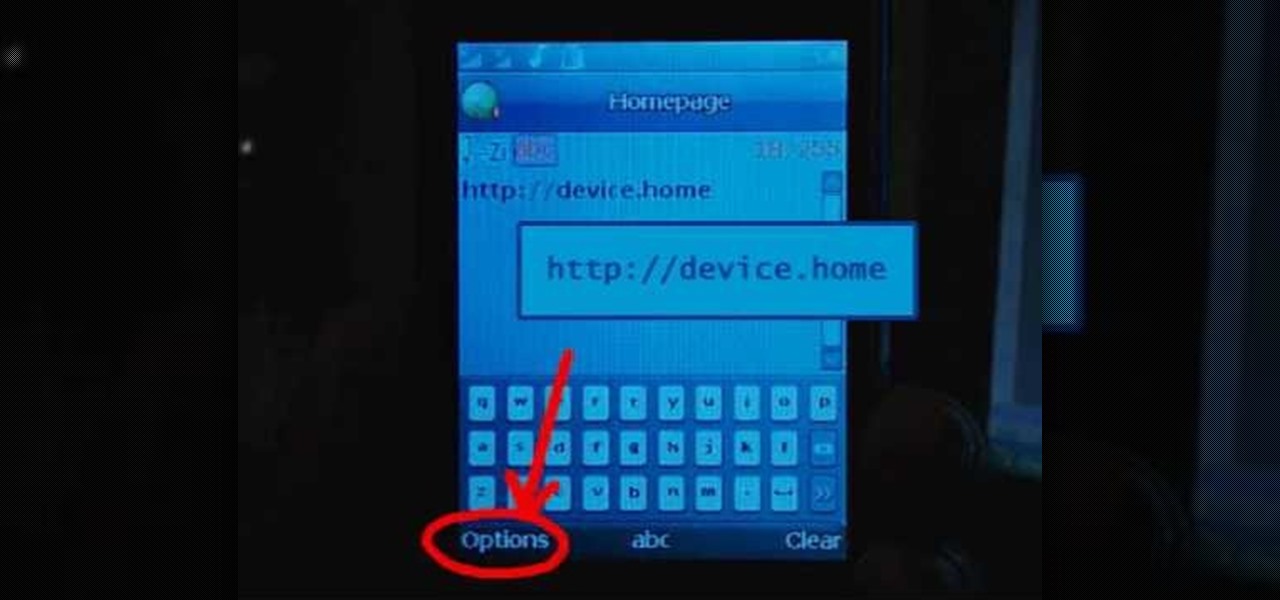
Learn how to set up Internet on iPhone clones with this video. *First thing you need to do is to make an AT&T GPRS data account.

This video is a quick overview for installing the "Google Chrome Frame" to speed up applications in your internet explorer.

Are you aware of your water usage? Are you really doing all you can to conserve water, our most precious resource? Here are some simple ways you may not have thought of and some facts about the amount of water wasted on a daily basis in America.

Get some tips and tricks to helping your dog become a well-obedient and well-trained dog. Watch this video tutorial to see how to teach your dog to "come".

The tarbuck knot is a non-jamming knot, great for when the rope will be bearing a heavy load, and shocked with sudden weight. Form the loop around the winch then make a serises of turns around the standing part in a clockwise direction. Bring the running end down to the base of the runs and make another clockwise turn finishing off with a figure eight through the exiting strand from the top turn. Watch this video knot-tying tutorial and learn how to tie a tarbuck knot.

In this tutorial video, we show you how to jailbreak Apple's latest device the iPhone 3G to start the process you need to do the following:

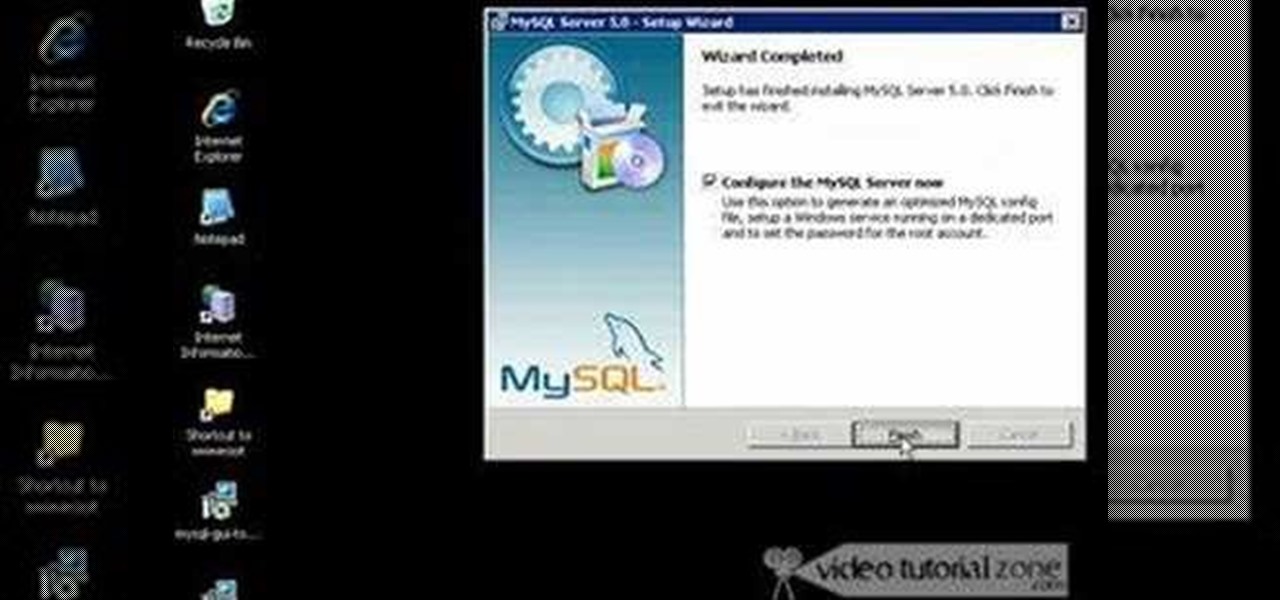
MySQL is a multithreaded, multi-user SQL database management system which has over 10 million installations. It runs as a server providing multi-user access to databases. It is by far the most popular and common database used in web applications throughout the world, and almost all hosting companies provide it free of charge to their users. MySQL AB makes MySQL Server available as free software under the GNU General Public License (GPL). For this tutorial we are going to download and install ...

The ability to browse the web in coffee shops, libraries, airports, and practically anywhere else you can imagine is more than convenient, but convenience has risks. Using public Wi-Fi allows others to spy on you easily. Even your own internet service provider can see every website you've ever visited. Don't fall into the trap of protecting your identity, data, and devices after it's too late.

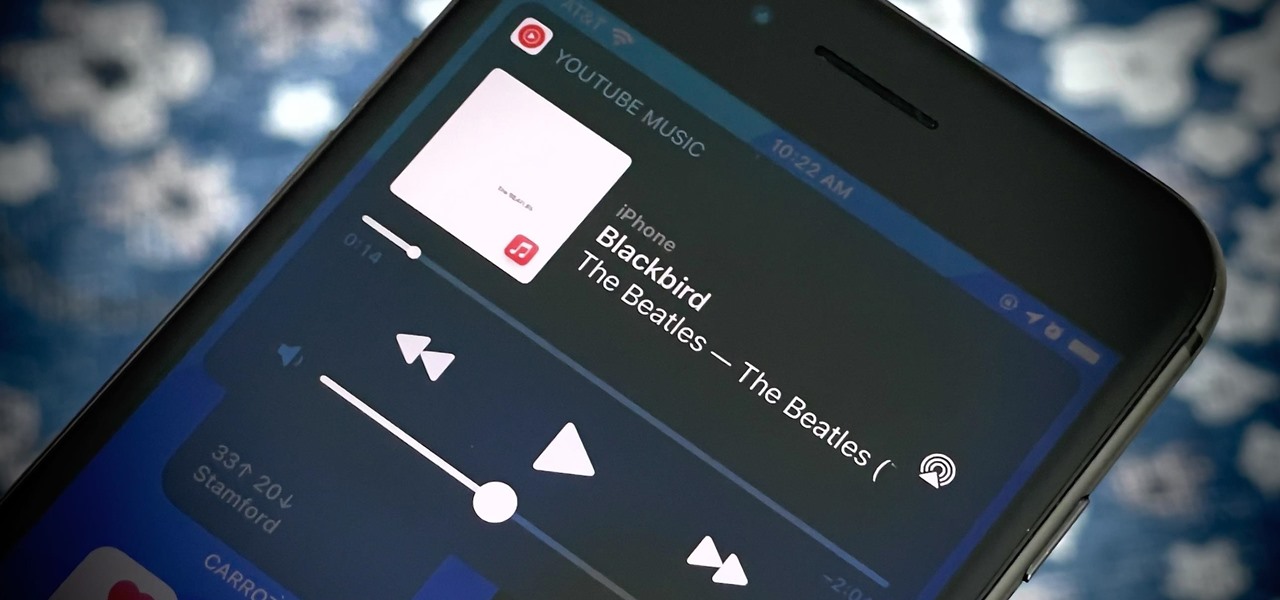
A new feature in iOS 14.5 lets you change your preferred music player for Siri requests. So if you primarily use YouTube Music over Apple Music and other services, Siri will learn so that you never have to tell the virtual assistant to play a song, artist, or album "on YouTube Music" again.

Now that 3D display maker Looking Glass Factory is closing in on $2.2 million raised in its crowdfunding campaign for the consumer-grade Looking Glass Portrait device, the company now has a 3D content generator to go with it.

Third-party apps on your iPhone must ask for your permission to access your library in the Music app. Some will even want to get access to your Apple Music account. If you no longer use the apps, you shouldn't be letting them have access anymore. It's easy to hunt them down, and doing so might even show some apps you can't even remember giving any permissions to.

SSH, or the secure shell, is a way of controlling a computer remotely from a command-line interface. While the information exchanged in the SSH session is encrypted, it's easy to spy on an SSH session if you have access to the computer that's being logged in to. Using a tool called SSHPry, we can spy on and inject commands into the SSH sessions of any other user logged in to on the same machine.

Every 5G model of the Galaxy S20 comes with 12 GB of memory. This amount of RAM is overkill, but Samsung's been putting similar amounts in its flagships for years. Since you have it, why not put it to use? With One UI 2, you can.

Thanks to numerous smartwatch deals this holiday season, many people are receiving their first one. But what exactly can they do? In regards to fitness, quite a lot. With a growing list of sensors and software updates, these small devices can be the very thing you need to ultimately reach your fitness goals.

Samba can be configured to allow any user with write access the ability to create a link to the root filesystem. Once an attacker has this level of access, it's only a matter of time before the system gets owned. Although this configuration isn't that common in the wild, it does happen, and Metasploit has a module to easily exploit this security flaw.

As we predicted this time last year, Magic Leap is finally moving from consumer entertainment hype to making a firm commitment to enterprise customers.

By now, you've probably been inundated with enough Baby Yoda memes to last you a lifetime. But if you don't have the new Disney Plus streaming service on your TV, you're probably wondering where all this is coming from. Well, lucky for you, just in time for the holiday season, we're here to guide you to the best ways to take part in all the streaming fun when you're not glued to your mobile devices.

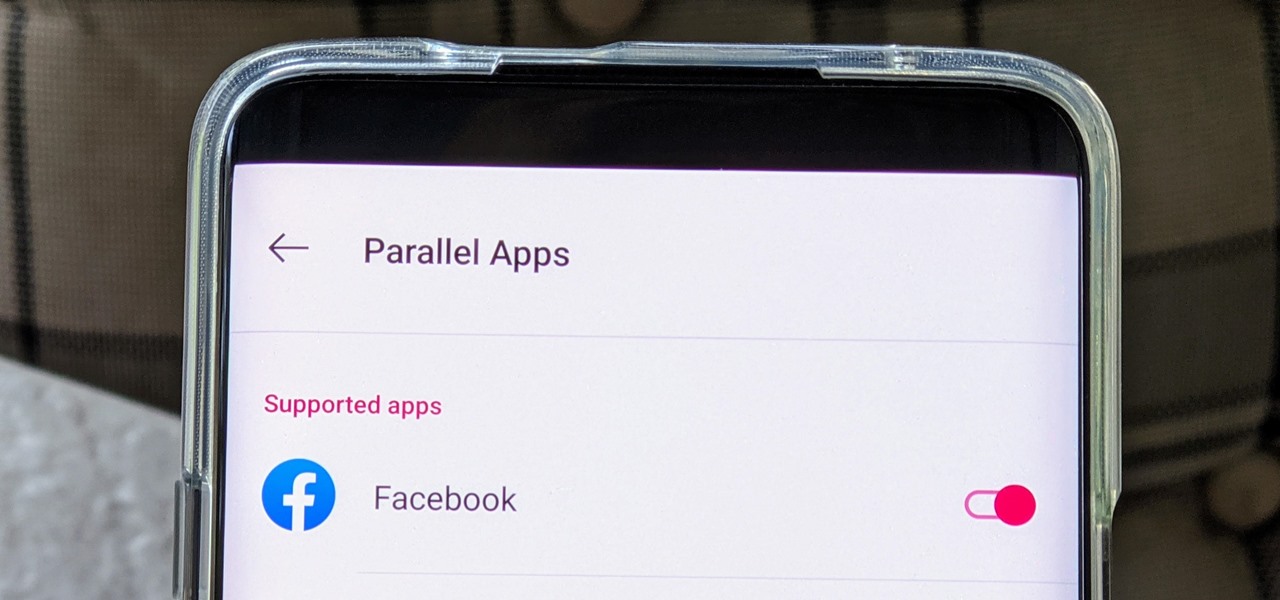
The Facebook app only supports one account being logged in at a time — but what if you need one for work and one for your personal life? That would normally involve logging out and logging in every time you need to switch accounts, but your OnePlus device offers a much better solution.

Apple's Reminders app is essential for those of us with a forgetful memory. But a standard Reminders entry isn't foolproof. They aren't great if you need to do something right when you get somewhere, since it can be tricky to set a specific time for that reminder. That's why Apple's location-based reminders are so darn useful.

While you might suspect your MacOS computer has been infected with malware, it can be difficult to know for sure. One way to spot malicious programs is to look for suspicious behavior — like programs listening in on our keyboard input or launching themselves every time we boot. Thanks to free MacOS tools called ReiKey and KnockKnock, we can detect suspicious programs to discover keyloggers and other persistent malware lurking on our system.

Following in the steps of Snapchat, Instagram, and YouCam, another popular photo app has gotten into the virtual try-on augmented reality game.

Google's strategy for updating its apps with dark mode options is apparently "one at a time" and "as slow as possible." Even after the company added a dark theme to many of its apps for Android and iOS, such as Calendar, Chrome, Keep, and Photos, Gmail seemed to remain "light" for the longest time. However, the app now supports dark mode on both mobile OSs. Here's how to enable it.

Apple slowly rolled out its new credit card, Apple Card, throughout August, but announced on Aug. 20 that it's now available to all qualified users in the US. Here's the problem: it's not totally obvious how to apply. Without any notification, directions, or clear settings, how do you even fill out an Apple Card application? Luckily for you, we're here to show exactly how to find it.

The mystery surrounding Overture, an app that showed up in the Magic Leap World app store along with the latest Lumin software release, has been cleared up.

Right now, Apple is testing two versions of iOS. On the one hand, you have iOS 13, buggy but feature-filled. On the other, iOS 12.4. The latter just got an update to the fifth developer and public beta versions, 13 days after the release of iOS 12.4 developer beta 4.

With iOS 13's developer beta in full swing, it can be easy to forget that there's an entirely separate iOS beta cycle still running right now. Yes, iOS 12.4 is still in beta, and unlike iOS 13, it's available to the public for testing.

UAC is something we've all dealt with on Windows, either as a user, administrator, or attacker. It's a core feature of the Windows security model, and for the most part, it does what it's supposed to. But it can be frustrating as a hacker when attempting privilege escalation, but it's easy enough to bypass UAC and obtain System access with Metasploit.

Apple had its Worldwide Developers Conference on June 3, 2019, which showcased big software announcements for all of Apple's hardware, and anyone can watch the keynote as it happened.

Talking Tom has long been mesmerizing children of all ages with his ability to repeat words and phrases and encourage touch interactions. Now, the lovable cat and his band of cuddly friends have ventured into the endless runner genre as heroes bent on saving Angela and their city from a band of mischievous raccoons.

EternalBlue was a devastating exploit that targeted Microsoft's implementation of the SMB protocol. Metasploit contains a useful module that will automatically exploit a target, as long as it's vulnerable. But what if we wanted to exploit this vulnerability without Metasploit holding our hand? It can be done using a Python file to exploit EternalBlue manually.

If you record yourself for a vlog or story post using your selfie camera, it can be challenging to stay on message. You might worry too much about the way you look or sound to focus on what you want to say. Using a script can help, but looking away from the camera to read is unprofessional, even on social platforms like Instagram. What you need is a teleprompter, and there are apps for that.

Magic Leap's business strategy for bringing augmented reality to the mainstream has become even clearer via its latest funding round.

Websites and web applications power the internet as we know it, representing a juicy target for any hacker or red team. TIDoS is a framework of modules brought together for their usefulness in hacking web apps, organized into a common sense workflow. With an impressive array of active and passive OSINT modules, TIDoS has the right instrument for any web app audit.

Many of our online accounts now come with an added two-factor authentication (2FA) functionality to help keep our data safe. This essentially means no one would be able to access the account until a specific set of requirements were met. It could be a combination of a password with a security key or even a passcode with some form of biometrics, like a fingerprint or face scan.