
Paper shredder not working like it used to? Soak several pieces of paper in baby oil and run them through the shredder, which will help lubricate the blades and make them run smoothly for future shredding purposes.

Android may be one of the world's most popular operating systems, but the fragmentation of it between devices can cause some confusion. Known for their deliciously sweet names, Gingerbread, Froyo, and Jelly Bean are just of few of the many versions of Android your device could be running.

Imagine if Apple sold customized, jailbroken iPhones at their retail stores. Do you know how freaking awesome that would be? Knowing Apple and their extremely tight-assed regime, it's more likely that Tony Romo will actually win a Super Bowl (Cowboys burn).
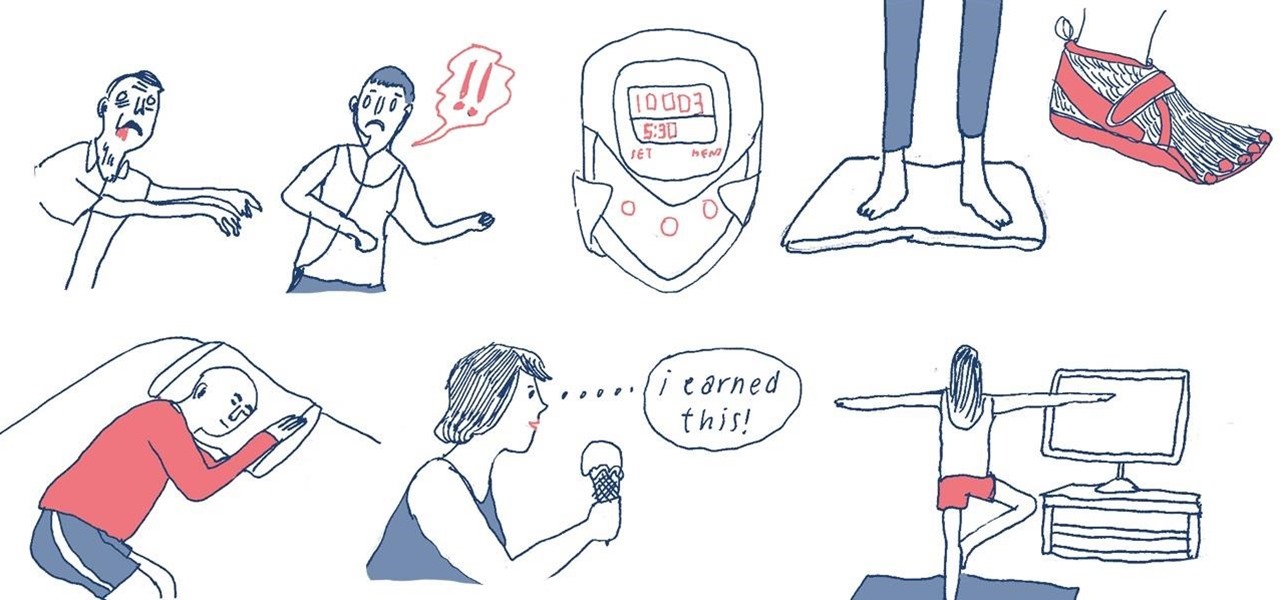
Would you exercise more if you were constantly running from zombies in a post-apocalyptic world where hundreds of people are depending on you to not get eaten? If your answer is yes, then you really need to snap out of your sedentary lifestyle ASAP and install the Zombies, Run! app on your smartphone.

Tabs are a beautiful thing. Without them, web browsing can be an incredibly tedious task. Tabs help organize all of your open pages in one window, saving you the time of constantly switching back and forth. And honestly, who wants to look at this? Want to add the convenience of tabs to Windows Explorer? The aptly named TabExplorer can help.

Warnings go to the streets and hand out trophies to people for whatever reasons and make the trophies out of very strong magnets

One of the many reasons Circuit City should go out of business is their sale of ridiculously expensive cables, wire and cords. The secret to the industry of Monster Cables is that it is unnecessary and ineffective. Gold-plated or otherwise, Monster's $100 cables are not intrinsically better than the cheaper versions they're stocked next to. Don't believe us?

Usain Bolt of Jamaica broke his own world record, running 100m in 9.69 seconds to win the Olympic gold medal. All the while his left shoe lace was untied.

Most bamboo in the United States is running bamboo, because nearly all cold hardy bamboo is the running or invasive type. The tropical bamboos are mostly "clumpers" and stay in a nice, tight clump. Running bamboos spread far and wide and can be very invasive. I grow many kinds of running bamboos and over the past 20 years I've had to learn how to control it's spread.

What is DansGuardian? Schools, offices and universities often tend to use a software like DansGuardian to prevent people from accessing certain websites - websites like Youtube, Facebook, Myspace, and so on. However, if you ever find yourself in a situation where you need to access a blocked website... it's possible! As a matter of fact, it's quite easy.

This is an intermediate guide on how to easily fix or retrieve data from a bad hard drive. What we're trying to do:

Im Going to keep this short simple and disastorous. Opening Scene: The guys Ehren, Bam, Steve O, Pontious, England, and Preston are standing on the shore line of the Santa monica pier. Dressed in Speedo bathing suits, (pontious in the bunny lifeguard suit) all the guys will have watter skis on ready to take off from the shore line they are all holding ski ropes attached to a boat. Cut to: Boat being Captained by Henry Rollans and his trusty Ship Mate Johnny Knoxville. Rollans stands up and ye...

Check out this interactive video tutorial from Verizon Wireless on the Samsung i730 mobile phone. If you have just purchases this sleek cell phone, here's your chance to learn everything you can possibly know about it.

On June 23, 2003, Linden labs created a free client program known as Second Life. This program allows users, or residents, to interact with each other in a virtual world by using avatars. Thanks to this program, residents are able to explore, socialize, and create and trade virtual property, and services with each other. Second Life has become one of the most popular programs used by various age ranges from 16 to 60, but how do you enter this world and get your own avatar?

Have you ever noticed that whenever you setup your voicemail account after getting a new cell phone number, it asks you to create a security pin to access your voicemail from other phone lines?
An emulator written in C#. There is a demonstration loading and running Notch's test program at line 252.
On this topic, Rick said: “We're looking for someone who writes what they believe in in stone and stands true to what they say."

Super useful run down of home chemistry tips and tricks.

VNC is a great protocol that you can use on Windows and Linux machines to remotely control computers. This is useful if you need to control your computer when away from home, help your grandma check her email, or help a client with a disk cleanup. VNC is secure in the sense that it requires authentication in order to make the connection, but after that, the data is sent over the internet unencrypted. This means that an attacker could sniff your traffic and snoop everything that's going on. Th...

If you've ever wondered how software pirates can take software and crack it time and time again, even with security in place, this small series is for you. Even with today's most advanced methods of defeating piracy in place, it is still relatively easy to crack almost any program in the world. This is mainly due to computer processes' ability to be completely manipulated by an assembly debugger. Using this, you can completely bypass the registration process by making it skip the application'...

A few days ago, CloudOn released their free mobile app that brought Microsoft Office directly to your Apple iPad. The cloud-based service effectively runs Office on their end, allowing you to use apps like Word and PowerPoint to edit your documents, which you would house in Dropbox. But after overwhelming demand, they removed the free app yesterday from the iTunes App Store.

This one goes perfectly with the 'Mosh Pit' achievement I posted about earlier today. To get the 'Monster Dance' achievement in Assassin's Creed: Revelations, you have to get a guard to incapacitate three civilians.

Welcome to Minecraft World! Check out our advanced tutorials and come play on our free server. Oh, the power of redstone! But, what good is any technology if it can't be harnessed for killing? Here's a redstone build for the mad scientist in each of us.

Minecraft mods (modifications) are additions to the game that change the way you play. They include texture packs, shaders, changes in gameplay, additions and subtractions and everything in between. Some of this information is very basic, other bits might help you along if you've been stuck. We'll start with the simple stuff.

What are the odds of drawing the same seven letters, e.g. JANITOR, twice during a lifetime of playing Scrabble—in two separate games. Michael Thelen, who runs Zyzzyva, breaks down the numbers.

Video games are one of the best non-medical things that have ever happened to sick children. They are stimulating, entertaining and require very little physical strength to play, which makes them perfect for those suffering physical maladies.

An unholy alliance has been forged between Street Fighter and Hello Kitty.

At a windows partner conference in Taipei, Microsoft unveiled their Windows 8 tablet. First impressions: WOW! Looks like they are actually innovating for once.
Apparently Lady Gaga is going to release songs from her album on FarmVille first in a specially-created section called GagaVille that will run until May 26. Will you be buying in?

Running late for The National Parks Project meant that Rajo took in a little election doc called GNARR... fitting viewing on the eve of one of the nail-bitingest Canadian Federal elections in recent memory.

Its often difficult to go on a diet without thinking of those foods you love, every moment of that day. Meditation is a fantastic way to clear you mind before work/school run etc..

Wacky "mutant bicycles" by Todd Kundla. Shoe Bike takes the cake. Previously, Thieves No More! If Gumby Were a Bicycle...

WoooofTTttTTTtT...! God Running Windows; Ah Yes I Seen The Light, & Rotten Apple CorezZz...LOL..

Calling a plumber can run in the upwards of $100. And the $5 Zip-It is... well, five bucks. But if you dig through your recyclables and kitchen drawer, you can whip up this cheap & easy drain declogger for next to nothing. You Will Need:

See ya later, 2010! Mike runs off his list of the 5 worst cinematic atrocities of the past year in this, our last WTI installment of MMX! Happy New Year!
Lately I've really been enjoying Trailers from Hell, and while a lot of the movies they do are from before my childhood, it's run by Joe Dante and he was, like, a staple of it. So that counts, right?

This is a video I made while building zip lines in Massachusetts. It gives you an idea of what goes into making these things. All the lines were still in the building phase so they run a little slow.


































