Welcome back, my aspiring hackers! Those of you who've been reading my tutorials for some time now know that I am adamant regarding the necessity of learning and using Linux to hack. There is no substitute, period.

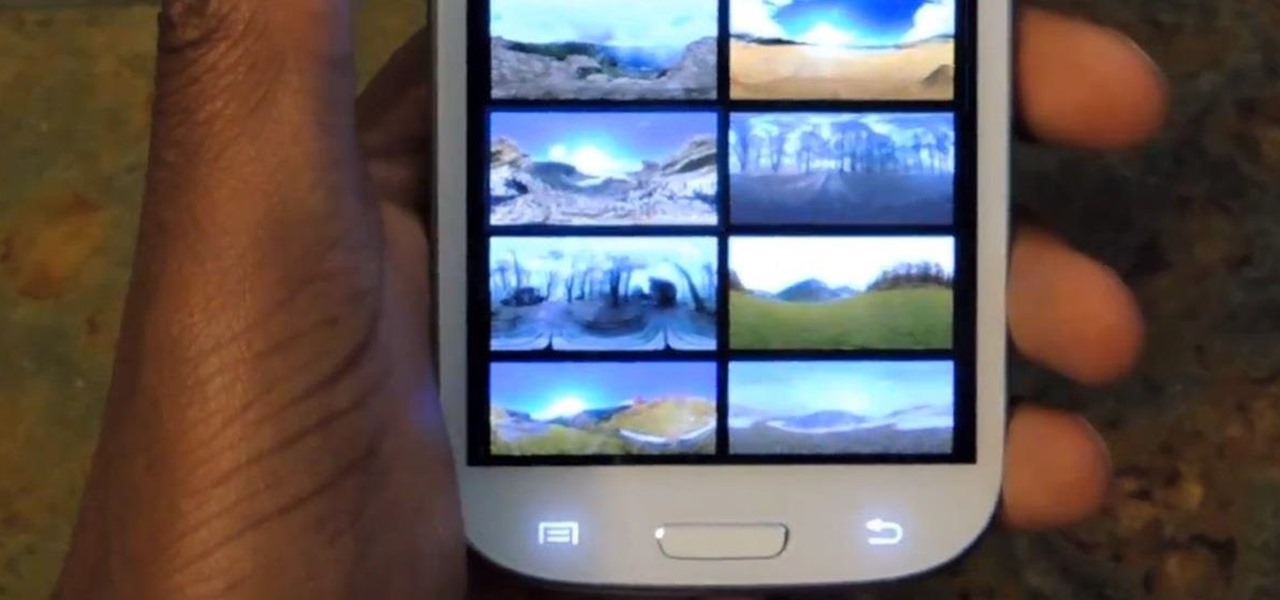
Slide to left, slide to the right, one hop this time. Okay, so maybe those are some of the dance instructions for the "Cha Cha Slide", but sliding and swiping on your Samsung Galaxy S3 can become so much more than just a simple gesture.

If you've got a MacBook, I'm sure you've spent some time messing around with the Photo Booth app. Who would have thought that adding simple effects like Comic Book or Stretch could make a selfie look so hilarious. Photo Booth is available for all Mac OS X computers running 10.4 or higher with an iSight camera, and it's also available on a few of Apple's iOS devices. Actually, it's only for the iPad 2 and all newer iPads since. It is NOT available on the iPhone, don't ask me why.

Welcome back, my novice hackers! I have tried to emphasize throughout this "Hack Like a Pro" series that good reconnaissance is critical to effective hacking. As you have seen in many of these hacks, the techniques that we use are VERY specific to the:

Whenever a new version of a phone comes out, there's always that one cool feature you wish you had on yours. For me, that's Group Play.

The Xperia Z1, Sony's flagship device, has been extremely popular overseas, so much so that it has made its way into the U.S. market as the Xperia Z1S, a modified version of the original. Known more commonly as the "waterproof smartphone," the Xperia Z1 packs one of the most powerful cameras on the market, with an impressive 20.7 megapixels. Since the device is only available for T-Mobile here in the States, unless you currently have that carrier, the chances of you getting your hands on Sony...

Here's a routine that I'm sure all of us smartphone users go through at least several times a day. You notice your Samsung Galaxy S4's notification LED blinking, grab your phone to see what it is, and enter your PIN. Only instead of anything important, you find that it's just some online store enticing you with sales promotions, or some other email that you could have easily done without.

The status bar is where we get all of the important need-to-know information for our phones. At a quick glance, you can see what time it is on your Samsung Galaxy S3, how much battery power you have remaining, your current signal strength, and more. But after a while, things can feel a little stale up there.

Midway through 2013, a popular custom ROM called Paranoid Android introduced their multitasking feature "Halo." Bubble-style notifications inspired by Facebook chat heads pop up near the top of the screen, and you simply tap on them to bring up the app in a floating window.

Welcome back, my rookie hackers! The more we know about a system or network, the better our chances of owning it and not leaving a trace for investigators to follow. One of the often overlooked sources for information is the Simple Network Management Protocol (SNMP). Many rookie hackers are not even aware of it, but it can prove to be a treasure trove of information, if you understand how it works and how to hack it.

Amazon.com has been around for a long time now, but there are still a few things most people don't know about when it comes to buying products from them. Here's a quick roundup of tips to help you get the most out of Amazon and save some money in the process. The holidays are the busiest time of year for online shopping, but these tricks will work all year around.

We're only years away from a complete Robot Revolution and Google Inc. will surely be leading the charge.

If you have friends like mine, letting them check out one photo on your phone means they're going to check out all of the photos on your phone. Before you realize what they're doing, it's too late, and they're sending out perverted emails to your coworkers, making you look like a newb at Candy Crush Saga, and viewing your Snapchats for you.

This week, Silk Road was shut down for good when the FBI seized the anonymous online marketplace after Ross Ulbricht, aka Dread Pirate Roberts, was arrested. This comes just two weeks after another illegal marketplace called Atlantis shutdown. However, there are plenty of other black markets hiding within the Deep Web, freely and anonymously accessible using the Tor browser.

Whenever the word "popup" pops up, I immediately cringe because all I can think about are those obnoxious ads that ruin my everyday browsing experience. But, not all popups are evil.

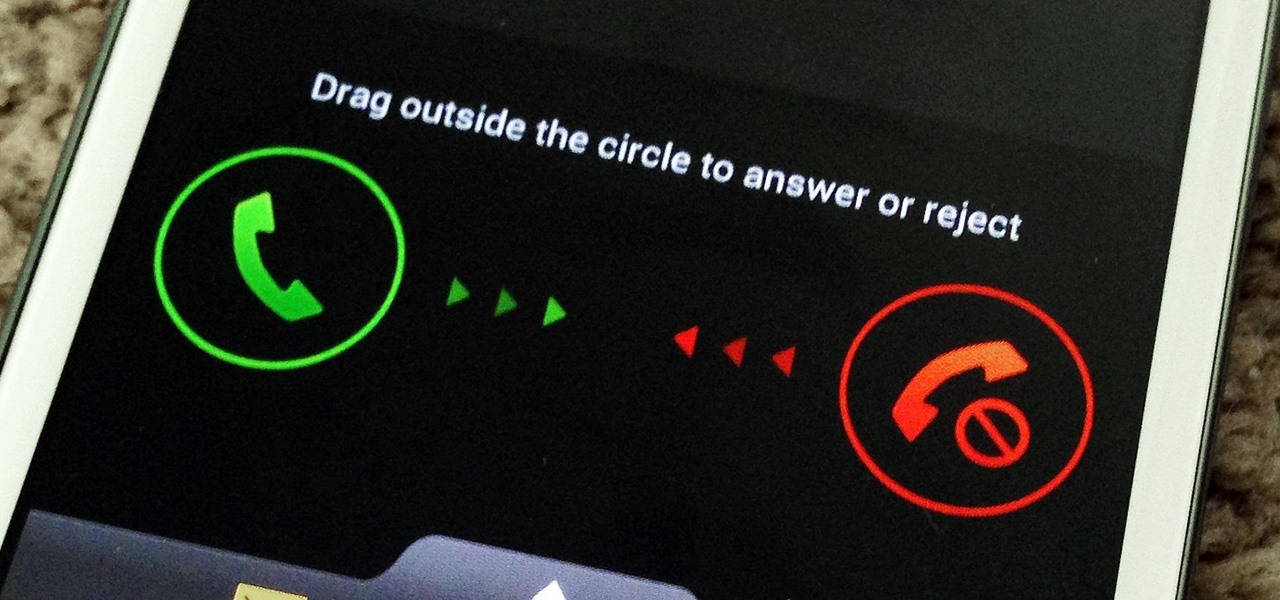
You don't have to be in debt to receive annoying calls from unwanted numbers. You may love your grandma, but if she calls you three times a day to ask how to turn on the television, you might just want to push all of her calls to voicemail.

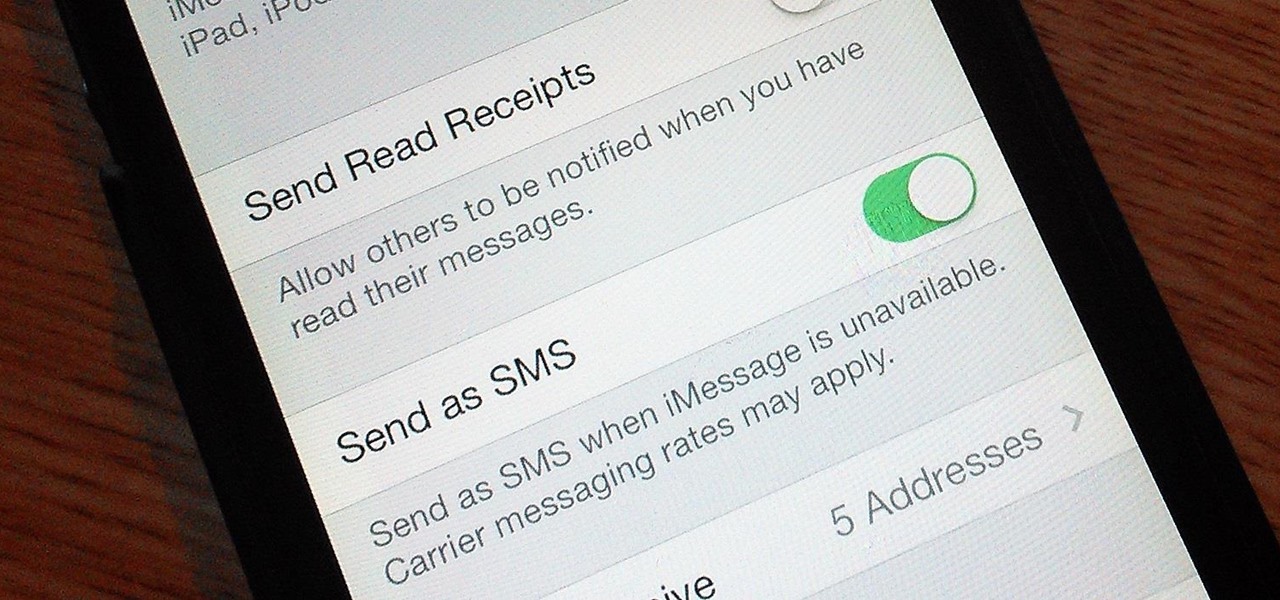
If you're an iPhone user, iMessage is great for cutting down on SMS costs from your carrier, but it doesn't always work right away.

Ubuntu isn't just a cool sounding name, but pegs itself as the world's favorite free operating system. It gained its popularity for being lightweight, fast, and visually appealing, and now that great look and speed can be placed right on the lock screen of your Samsung Galaxy S3.

From a very early age we have an intrinsic obsession with things that float. Why do you think we love balloons and bubbles so much? So, it's no surprise that our smartphones are being invaded by floating features.

For the first time ever, iPhones will be getting live panoramic wallpapers in iOS 7, but it's something Android devices have always embraced.

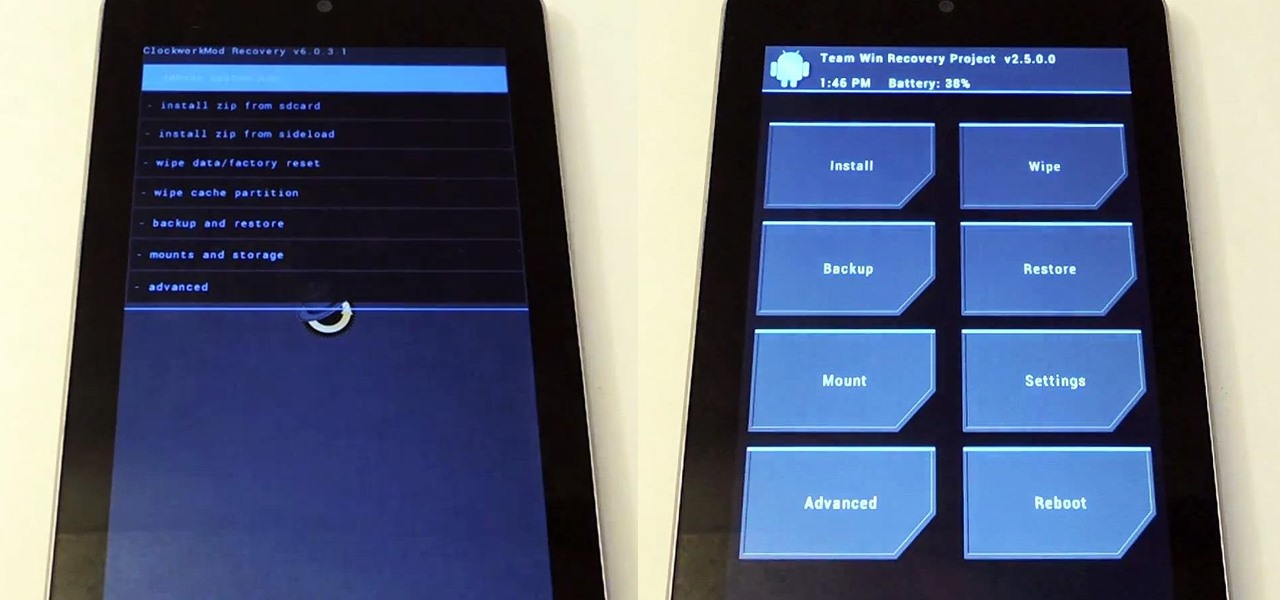
Android is constantly being refined, and the tools used to root and install custom recoveries are no exception. Earlier methods to root and install custom recoveries were very long and complicated. Any misstep along the way and you can end up with a bricked tablet.

Apple is set to release its latest operating system for iPad, iPhone, and iPod touch this fall, and if you haven't noticed yet from our iOS 7 softModder guides, it's going to be pretty slick.

The very first text message was sent on December 3rd, 1992 by Neil Papworth, an engineer for Vodafone, and it simply said "Merry Christmas." He may have jumped the gun on the whole Christmas thing, but you trying coming up with the first text message in history!

Welcome back, my nascent Hackers! In my last blog, we looked at a passive way to gather information necessary for a hack. The advantage of using passive recon is that it's totally undetectable, meaning that the target never knows you're scouting them and you leave no tracks. The disadvantage, of course, is that it's limited to only some websites and not entirely reliable.

Welcome back, my novice hackers! Most of my tutorials up until this point have addressed how to exploit a target assuming that we already know some basic information about their system. These include their IP address, operating system, open ports, services running, and so on.

In most countries, there is one single emergency telephone number that allows you to contact local emergency services when in need of assistance. In the United States, that number is 911, which most of us know by the time we're able to speak, unless you're Buckwheat and Porky.

I'm not lying when I say that my iPhone is at my side at all times, and is really one of the best devices I own. My second favorite gadget would be my PlayStation 3, however, when it comes to browsing apps like YouTube, it's pretty terrible.

Do you like Samsung's TouchWiz and the iPhone's user interface, but wish you could bring the best of both worlds together onto your device? You can! MIUI (pronounced me-you-eye) is a heavily modded custom ROM that brings a different UI experience never before seen on stock Android devices. Over in the Nexus 7 SoftModder forum, Shashou Jian mentioned MIUI as a ROM every user should try out. The interface is a fresh mix of Apple’s iOS and Samsung’s TouchWiz elements—with a large dose of customi...

Okay, you're Nexus 7 is awesome, but ever wish you could explore those nifty TouchWiz features that make the Samsung Galaxy Tab and Samsung Galaxy Note 2 so interesting?

Not having internet sucks! We do a ton online these days, from working, shopping, studying, and collaborating, to watching fail videos and endlessly clicking through memes.

Google Reader is soon to be no more. Yesterday, the company announced that the service will be shutting down as of July 1, 2013, as part of Google's second "Spring Cleaning."

UPDATE (February 26, 2014) Yesterday, the U.S. House of Representatives passed H.R. 1123 with a 295-114 vote decision. The ruling repeals the 2012 Library of Congress (LOC) decision that limited the ability to legally "unlock" your smartphone (see below).

I recently wrote about Twitter's super now app called Vine, which lets people create 6 second video clips that can be embedded in a tweet. Those videos have their own proprietary extension, but if you want to turn those 6 second videos into an animated GIF, you can now do so thanks to developer Esten Hurtle, who created VineGifR, a seamless way to transform your (or someone else's) Vine movies into GIFs.

I can definitely say that my MacBook is one of my best friends, but I was still very disappointed when I realized that the only game my laptop came with was chess. For starters, I'm not very good at chess. I haven't even beat the computer once, which really grinds my gears. But, it has come to my attention that chess isn't the only pre-installed game on my Mac—there seems to be some hidden gems that I simply wasn't cool enough to know about. For some of you, this may be old news, but for me, ...

Cross-dressing and gender-bending are nothing new, but the realm of Steampunk seems to be especially accepting of role-reversal in dress.

Caller ID is great to have, but there are certain situations where you don't want the person you're calling to have your number. People who sometimes use their personal phones for work may not want clients knowing where to reach them outside of work, and anytime you're dealing with Craigslist, it's better to be safe than sorry.

As a kid, I was always interested in what was beyond our world. I remember lying down on the top of my dad's car and watching the stars for hour, gleefully excited whenever a shooting star streaked across the night sky.

Having access to your computer from your cell phone is an extremely useful feature. Whether you need to edit documents or send files that are on your home desktop, or you simply want to watch movies you have saved on your computer, access is key.

Clearing the cache on your computer is (usually) a quick and easy way to help speed it up. Deleting those temporary files frees up space, helping you computer run smoother, especially if you have not cleared the cache for a extended period. However, finding the different caches in Windows 8 is a little trickier than in previous Windows systems.

In my last hack blog on crashing your roommates Win7 system, we started looking at client- side attacks. As promised, we will be looking at some more client-side attacks.