In the moment, buying a dozen donuts always seems like a good idea. In retrospect, however, it's always too much... and you inevitably end up with a box of stale donuts a few days later.

With the FBI getting access to iPhones, and apps like Waze being used to track people's locations, you've got to wonder just how safe and secure your smartphone is... or isn't. When you consider everything you do on your phone, from taking and sharing pictures to mobile banking, keeping your information safe is a crucial step that may seem out of your hands.

Making yogurt at home doesn't sound like an easy task at first. We initially saw it as detailed, hands-on, and precise—a process that required special equipment, specialized (and expensive) live-culture bacteria, and loads of yogurt knowledge.

I know I'm in the majority when I say that grilled cheese sandwiches are one of life's simplest and best pleasures: gooey, rich, melted cheese, sandwiched between two perfectly-buttered pieces of toast... perfection.

Plastic wrap is, arguably, man's greatest invention—or at least, the 2000 Year Old Man thought so. Its primary use is to protect food from getting dried out in the fridge or on the counter; but if that's all you're only using it for, you're missing out.

Welcome back everyone! It's been quite a while hasn't it? Today we're going to kick off the second part of the Python training series by introducing modules. We'll start off by explaining what a module is and we'll give an example. So, let's get started!

There are few things more annoying in life than getting interrupted—especially when you're in a groove, jamming out to your favorite song. If we can all agree on that sentiment, then why is it that our phones mute the music we're listening to for a few seconds whenever a notification comes in?

Netflix has become the subject of heavy buzz this week, and not due to the latest season of Daredevil (which gets two thumbs up, btw). The online video entertainment provider is drawing fire over its admission that it has been throttling video streams for its AT&T and Verizon customers for years.

Ever since the Google Play Store removed its "Designed for tablets" section, it's been a lot harder to find good, tablet-optimized Android apps. Not that it was all that great to begin with considering that they used to list apps like Facebook and Twitter, which only have oversized phone UIs on tablets, not actual customized UIs.

Google's YouTube Red is an awesome service, particularly in the United States where it comes bundled with a subscription to Google Play Music. You don't have to worry about ever seeing ads again on any videos, you can continue playback after you exit the YouTube app or even when you turn your screen off, you can download videos for offline playback, and you'll have access to YouTube Music.

New technologies in current-generations smartphones allow for much faster charging—Qualcomm Quick Charge 3.0, VOOC Flash Charge, and USB Type-C, for instance, can charge a phone up to 4 times faster than traditional methods. However, the majority of phones on the market still don't support these standards. So for the rest of us, I'll go over an easy tip that can charge any smartphone as much as 25% faster.

Very often we have processes in Linux that we want to always run in the background at startup. These would be processes that we need to start at bootup and always be available to us.

For years, users have been clamoring for a "dark mode" theme in Android, but it has always seemed like Google is so committed to the white motif from their web services that such an option would never become a reality. But in a stunning turn of events, Google is finally embracing the idea with a night theme that will work in any app, and I'll cover all of the specifics below.

Alright, this will be my first tutorial in C. Note that this guide is written for Linux.

Welcome back, everyone. In the previous part of this rapid-fire miniseries, we built the attacker portion of the shell. In this article, we'll just be testing it to see if everything works correctly.

For many people, the two main advantages of buying a Nexus device are prompt updates and the ability to root without much hassle. But in a cruel twist of fate, these two features are almost mutually exclusive, since OTA updates will refuse to run on rooted devices.

Welcome back, my budding hackers! One of the most basic skills the forensic investigator must master is the acquisition of data in a forensically sound manner. If data is not captured in a forensically sound manner, it may not be admissible in court. In my Kali Forensics series, I showed you how to acquire a forensically sound, bit-by-bit image of a storage device such as a hard drive or flash drive, but now let's dive into live memory.

Ever since developer bponury created his TouchControl app for the Galaxy Nexus back in 2011, manufacturers and modders alike have been racing to re-implement the "Double-tap-to-wake" functionality it brought to the table. We've seen LG do it with their "Knock On" feature, we've seen Motorola put a twist on it with "Active Display," and we've even seen Google implement the feature in their Nexus 9 tablet.

Samsung makes some wonderful phones, but one thing I've noticed is that battery life can start to degrade over time, causing the phone to die a lot faster than it used to. If you've been experiencing this issue, and have asked yourself, "Why does my Galaxy S5 die so fast?" there are a few likely causes—and we've got you covered with troubleshooting tips and simple fixes below.

I mentioned in one of my earlier articles something about ghost hackers, and very shortly stated a thing or two of what they do.

Five Phases of Hacking:- The five phases of Hacking are as follow:

Fewer and fewer Android phones are being released with SD card slots, so it's always a struggle to make sure you have enough free storage space for your photos, videos, and music. Things like app data and cache slowly build up as you use your device, which means your available storage number gradually decreases over time.

We all know them, and many of us despize them. And some might support them, regardless many have different opinions.

Welcome back to a tutorial on malware. We'll be discovering a method to beef up our little trooper. Without further ado, let's jump right in!

Android's copy/paste menu and text selection options have traditionally been downright terrible, but things are starting to get better with some recent improvements made in Marshmallow. That being said, there's still a lot left to be desired, and there's always plenty of room for more useful functionality.

If you purchased something from iTunes, the iOS App Store, iBooks Store, Apple TV App Store, or the Mac App Store and it doesn't work, didn't download, is buggy, or wasn't what you thought it was, you can get a full refund from Apple—you just have to know how to ask.

Welcome to an introduction on writing basic malware, an optional sub-series in which I expose you to malware and its technologies. This is written for those who wish to seek a beginning in malware analysis or enlightenment on the subject. We will be justifying the writing and covering types of malware.

A trip to any grocery store's produce section will quickly reveal that bananas are often picked from the tree well before their prime—which is necessary for them to arrive at our local store without going bad. In fact, bananas are refrigerated en route to our supermarkets in order to stave off the ripening process... which makes sense, since they travel quite the distance (from the Tropics around South America or Africa to our proverbial doorstep).

Just last month, Microsoft announced plans to take away a huge chunk of storage from the free tier of their OneDrive cloud service, and users are understandably quite upset. At the same time, they reneged on an offer to give Office365 users unlimited OneDrive storage, and instead, will only be offering 1 TB of storage.

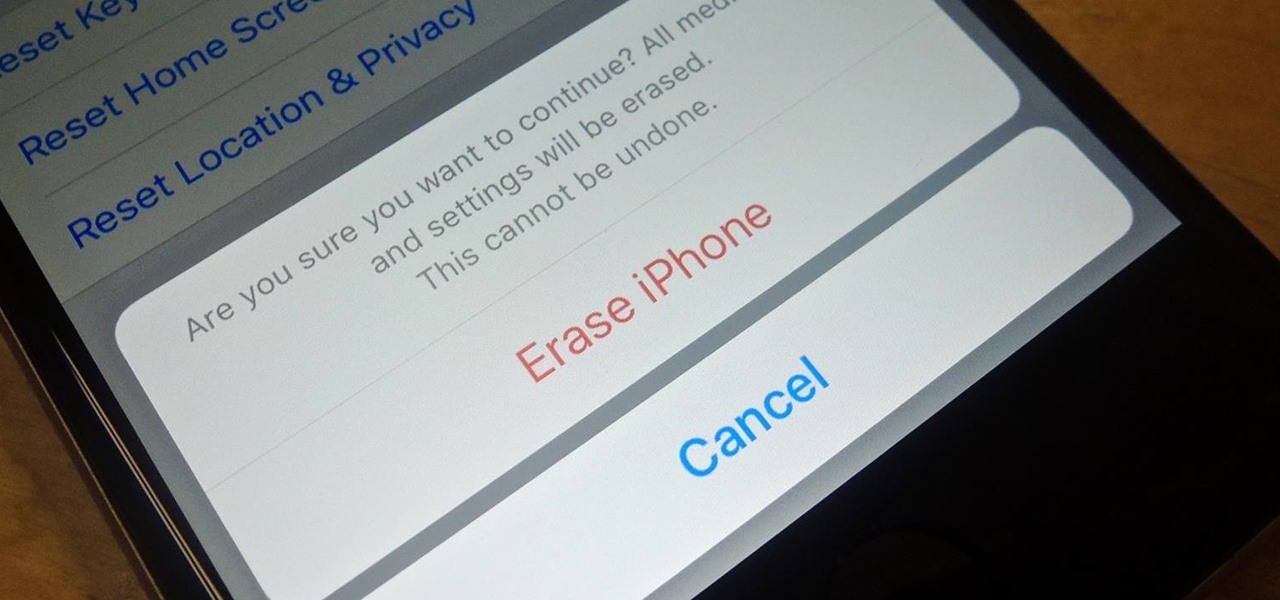
Before you sell your old iPad, iPhone, or iPod touch to a buddy or a company like Gazelle, it's vital that you wipe the entire device of all its content; including sensitive material like contacts, messages, pictures, and videos. There are two easy ways to wipe your iOS device, so let's show you how to do it using iTunes or directly from the device itself.

With over 10,000 possible combinations, a four-digit passcode may seem secure, but it's fairly easy for someone to crack your code—no matter how clever you think it is. Luckily, there are many other options for securing your iPhone's lock screen—especially if your running iOS 9.

Here's a not-so-well-kept secret about the food industry: retailers love to take your money. And one of the ways they do that is by dividing food into smaller sizes and charging more. Have you ever noticed that a container of precut, washed broccoli costs more than a head of broccoli with the same amount of florets and stems?

The 2015 LA Auto Show showcases the best of the auto industry—well, at least according to car companies. Increases in horsepower, better fuel economy, and most importantly—the latest tech—is all on display during the 10-day event in Southern California. Once of my first missions at the show was to figure out who is putting the most care and thought into in-cabin electronics, mainly the ones that guide us around and play our music, affectionately known as "infotainment."

As an avid coffee drinker, I used to be a big fan of single-serve coffee machines. One day, the machine decided to stop working—which does happen from time to time—so I decided to go old school and use my automatic drip. Then, I realized that all I had were pods of single-serve coffee grinds, and I was all out of regular coffee filters!

As you all know, Anonymous have declared cyber war on ISIS and have already proven what they are capable of and whats to come.

I think it was 1986 when I first discovered my love for making computers say stupid things out loud. My older brother got a Commodore 64 for his birthday, which came bundled with software that would speak out any term you typed in—and boy, that computer sure made a fool of itself after my five-year-old imagination got a hold of the keyboard.

Welcome back! In the last iteration of how to train your python, we covered loops, today we'll be covering something that I wish I had learned about much earlier in my scripting career, errors. We all run into them, and they can be frustrating, but there is also a silver lining to them. Today, we'll be discussing why some errors are unavoidable, and what we can do when we run into them. Also, this article will be more of a concept and less of writing actual code, but the information is equall...

In an article published in early-2015 by Peninsula Press, it was reported that the demand and the salaries for cyber security professionals are exploding! They cite that 209,000 cyber security jobs were unfilled last year, and that job postings have increased over 74% in the last 5 years. Job opening are expected to grow by another 53% over the next 3 years. You are definitely in the right field, my tenderfoot hackers! Some researchers are expecting information security jobs to continue to gr...

WPA Enterprise is widely used in large corporations as it offers individual and centralized control through a server that authenticate the users (RADIUS server). In this tutorial I will show you how to break the barrier and obtain the user credentials.

While it seemed like jailbreaking methods were always one update behind the current build, the team over at Pangu have already released a jailbreak tool for iOS 9, and it works up to iOS 9.0.2. It is not available for iOS 9.1 through 9.2 yet, but we will update this guide when they are ready.