Free trials are a great way to test out products before a purchase, or simply for the exploitation of free stuff for that limited amount of time. Some trials last a few days and some last even a month or two, but no matter what—these trials will always expire. But like most things in life, there is a way to get around such limitations.

Most of us have some sort of malware scanner or antivirus program on our computers, but what about our smartphones? A lot of people don't realize that computers aren't the only devices that are susceptible to malicious software and apps—they can follow you on your smartphone or tablet, too.
Like most new things, the Start Screen in Windows 8 has its adorers and detractors, but either way you slice it—it's here to stay. I'm still getting used to the Start Screen, so I'm not sure if it's a love or hate feeling yet, but I do know one thing—I want my own background!

There's really nothing safe about transmitting sensitive information electronically, but even if it gets there safely without being seen by prying eyes, there's no guarantee what happens to it once it reaches its destination. And let's face it, there are some things that you just don't want floating out there forever. So what can you do? Whether you want to send an email, a text, or a link, there are ways to send messages that self-destruct so that once they're read, they immediately vanish. ...

All of my hacks up to this point have been operating system hacks. In other words, we have exploited a vulnerability usually in an operating system service (SMB, RPC, etc.) that all allow us to install a command shell or other code in the target system.

In my first few articles, we focused on operating system hacks. These hacks have been primarily on older operating systems such as Windows XP, Windows Vista, and Windows Server 2003.

People are always looking for ways to save money, and for the most part, saving money and cheating the system are synonymous when it comes to things like free internet access. Practically every new gadget is capable of connecting to the web, which means more and more people are looking for ways around those hefty internet bills.

Getting a new phone is like getting a pair of new socks—you can't wait to try them on and when you do, they feel totally awesome. Maybe that's just me, but for many customers that have already received their highly anticipated iPhone 5 in the mail, awesome is definitely not the word they are using.

If you've never heard of geocaching, it's kind of a grown-up treasure hunt you play everywhere in the world. GPS coordinates are given as clues and the players must find the cache box. There is usually a log book to write your name and a small toy or present to collect.

What's the first thing you would do once you realized you were lost in, say, a desert? If you're like me, you would immediately pull out your cell phone and start dialing every number. But what if you have no service? What if your battery is dead?

Learn tips for using the Celtx free screenwriting software, including project library, production schedule, editors, and online services in this free screenwriting video series.

Using a strong password is critical to the security of your online accounts. However, according to Dashlane, US users hold an average of 130 different accounts. Memorizing strong passwords for that many accounts is impractical. Fortunately, password managers solve the problem.

A few months ago, iOS 12.1 came out with a handful of useful new features, and iOS 12.2 goes even further. While some of iOS 12.2's new features for iPhone are much welcomed, there are some that we'd be better without.

It's easier than you might think to hack into Wi-Fi routers using just one unrooted Android phone. This method doesn't require brute-forcing the password, a Windows OS for converting PowerShell scripts into EXE format, a reliable VPS for intercepting hacked Wi-Fi passwords, or Metasploit for post-exploitation tricks.

Since iCloud's introduction in 2011, you get only 5 GB of complimentary cloud storage with your Apple account. With iPhone backups, app data, iCloud Drive files, and even emails (if you have a Mac, Me, or iCloud email address), you'll quickly run out of space to back up photos and videos. Fortunately, Google offers 15 GB of free storage, making it easy to upload your Camera Roll for safekeeping.

The Pixel 3 runs stock Android, so you might think that since you've used an Android device before, you should know your way around the new phone by default. But Google has actually added several great Pixel-exclusive software features to its flagships, and not all of them are easily discoverable.

The most common Wi-Fi jamming attacks leverage deauthentication and disassociation packets to attack networks. This allows a low-cost ESP8266-based device programmed in Arduino to detect and classify Wi-Fi denial-of-service attacks by lighting a different color LED for each type of packet. The pattern of these colors can also allow us to fingerprint the tool being used to attack the network.

It only takes a few commands to manipulate a MacBook's secure HTTPS traffic and pluck login passwords out of the encrypted data. Let's take Facebook and Gmail hacking to the next level by intercepting Safari and Google Chrome web traffic in real time.

Defcon is the largest hacker conference with something for everyone, whether it be the talks, parties, villages, or any of the hundreds of events. In this guide, we'll take a holistic view at everything that goes into attending the con for the first time, from securing your electronics and making the most of your time to the logistics of getting there and finding the right place to stay.

While our time with the Protostar VM from Exploit Exercises was lovely, we must move on to bigger things and harder challenges. Exploit Exercises' Fusion VM offers some more challenging binary exploitation levels for us to tackle. The biggest change is that these levels are all network services, which means we'll write our first remote exploits.

In just a few months, Binance has experienced explosive growth, overtaking its rivals to rank among the top three cryptocurrency exchanges in the world by trading volume. Without a doubt, Binance is now among the best sites for trading alt-coins like Ripple (XRP), Stellar (XLM), and NEM (XEM) to name a few.

For all those times when an app either isn't available or simply won't cut it, your phone's internet browser provides access to your favorite websites and services. But some browsers are flat-out better than others, and chances are, the browser that came pre-installed on your phone isn't the best option out there.

Armis Labs has revealed eight vulnerabilities, called "BlueBorne", which put 5.3 billion Android, iOS, Windows, and Linux devices that use Bluetooth at risk. With it, hackers can control devices, access data, and spread malware to other vulnerable devices through networks. In this post, we will learn about the vulnerabilities, then look at how to find devices that have them.

Aircraft equipped with ADS-B are constantly shouting their location into the radio void, along with other useful unauthenticated and unencrypted data. In this guide, we will make an ADS-B receiver using a Raspberry Pi with a software-defined radio (SDR) dongle, which we can use to track aircraft anywhere in real time.

Smartphone manufacturers do their best to keep you tied down to their ecosystem, but the reality is that there's not much keeping you from switching. Transfer some files, install a few apps here and there, and all of a sudden, you're knee-deep in a new operating system.

Welcome back, my fledgling hackers! Hacking has a long and storied history in the U.S. and around the world. It did not begin yesterday, or even at the advent of the 21st century, but rather dates back at least 40 years. Of course, once the internet migrated to commercial use in the 1990s, hacking went into hyperdrive.

If you like to shop online then it is extremely helpful to have a PayPal account to safely make your online purchases. Help reduce your risk of identity theft by using protected methods like PayPal when your credit card information is involved.

Learn how to use a MotionX-GPS including its functions, and how to use other applications such as music and internet while still in this application.

Learn how to repair a lawn mower in this free DIY video instructions, including service and maintenance such as oil draining and lawn mower blade repair.

Summer is almost here and you’re looking forward to that exotic vacation but you are going to need a passport and photos to go in it. There are a few simple ways to get a photo for your application. Find the method that is best for you and get traveling.

Most people have multiple email addresses these days. Gmail is one of the more popular services, but did you know you can access your Gmail account using the Mac OS X mail program? Not only is it possible, but it is incredibly easy!

Darth Vader is the legendary sci-fi character from the Star Wars movies. Everyone has heard of the Star Wars Trilogy, right? The older ones from the 70's? Darth Vader is the primary antagonist from those intergalactic space flicks. DragoArt has this video tutorial on how to draw Darth Vader from "Star Wars". Get more detailed instructions on the step-by-step cartoon drawing here.

Another name for jumper's knee is patellar tendinitis. Jumper's knee is an injury that affects the tendon connecting your kneecap (patella) to your shinbone. The patellar tendon plays a pivotal role in the way you use your legs. It helps your muscles extend your lower leg so that you can kick a ball, push the pedals on your bicycle, and jump up in the air. Learn about the different causes of, symptoms of, and treatments for jumper's knee in this video.

Bodyguard jobs can lead to an extremely rewarding and exciting career path. Learn to become a bodyguard with tips on training and salary from a professional bodyguard and former Secret Service agent in this free career video series.

Butter cream frosting isn’t only delicious but allows for great decorating possibilities. It can be a little difficult to create smooth surface to of the frosting if bubbles have created pock marks when laid, but as the video demonstrates you can use a smoothing tool to get that perfect service with a little work. Using a delivery bag and more colored butter cream you can create tropical flowers for a paradise cake.

In this atv maintenance video series, learn ATV maintenance tips from certified Polaris mechanic Tom Roland. Tom will teach you necessary Polaris ATV maintenance based on professional atv maintenance manuals and service schedules. You will learn about the parts of an ATV, such as a Polaris 500. Tom will teach you about replacing the air filter on a Polaris ATV, how to change the oil in a Polaris ATV, how to check the suspension on an ATV, how to check the tie rods on an ATV, and how to diagno...

Ever wished you could check your cell's voicemail online? You can, for free, with the YouMail web application. In this tutorial, you'll find step-by-step instructions for signing up the the YouMail service. For more, or to get started signing up for you own YouMail account, take a look! Sign up for, and use, YouMail visual voicemail.

The crew from NASA's International Space Station wish planet Earth a heartwarming Merry Christmas and a Happy New Year. (Check out flight engineer Cady Coleman's hair. Zero gravity is awesome.) For the nostalgic, the legendary Apollo 8, the first manned mission to the Moon, wishes the world Merry Christmas in s live television broadcast from lunar orbit, December 1968:

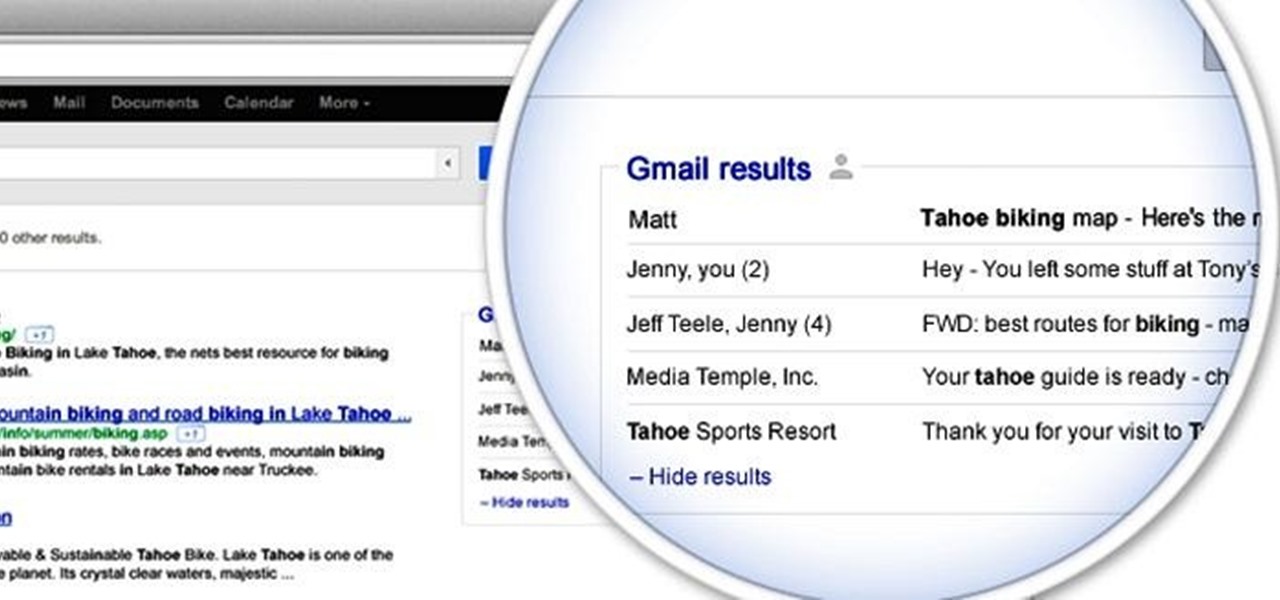
Google is rolling out a new feature that will integrate your Gmail account with Google searches. The feature will add results pulled from your email correspondences to create more "personalized" Google search results. Google is currently doing a test run of the service. To activate it for your account, head on over to this page to sign up. It's currently restricted to the English version of the site, and for those with @gmail.com email addresses (not available on Google Apps accounts). And be...

When a design is converted to an advanced template set, it is already made up of a collection of template modules defined and maintained by TypePad. If you wish to override these template modules with your own, simply create a new local template module with the same name as the one you wish to customize. To then use this customized template module as opposed to the default TypePad template module, you will need to modify the include directive used to import the template module into another te...