
Service Yang Search Results


News: Banks Around the World Hit with Repeated DDoS Attacks!
In recent weeks, major bank websites around the world have experienced outages after being have been hit with Distributed Denial of Service (DDoS) attacks. Although few, if any, of these banks have been totally knocked offline, these DoS attacks have dramatically slowed the response time of their websites to legitimate customers. The most recent victim was the Royal Bank of Scotland. Due to this attack, RBS customers were unable to access their accounts for about an hour last week.

Where Do I Start: Learn the Fundamentals
I am very new to Null Byte but I find much of its content and community incredibly interesting. I spent quite a bit of time just chronologically going through the posts and I noticed a common theme in many of the beginner posts. Many people seem to want to know the 'secret' or a paragraph on "How to Hack" and become a hacker in a few minutes. I started off this post as a reply to a question from a beginner but thought it might be beneficial to have for those stumbling across this site.
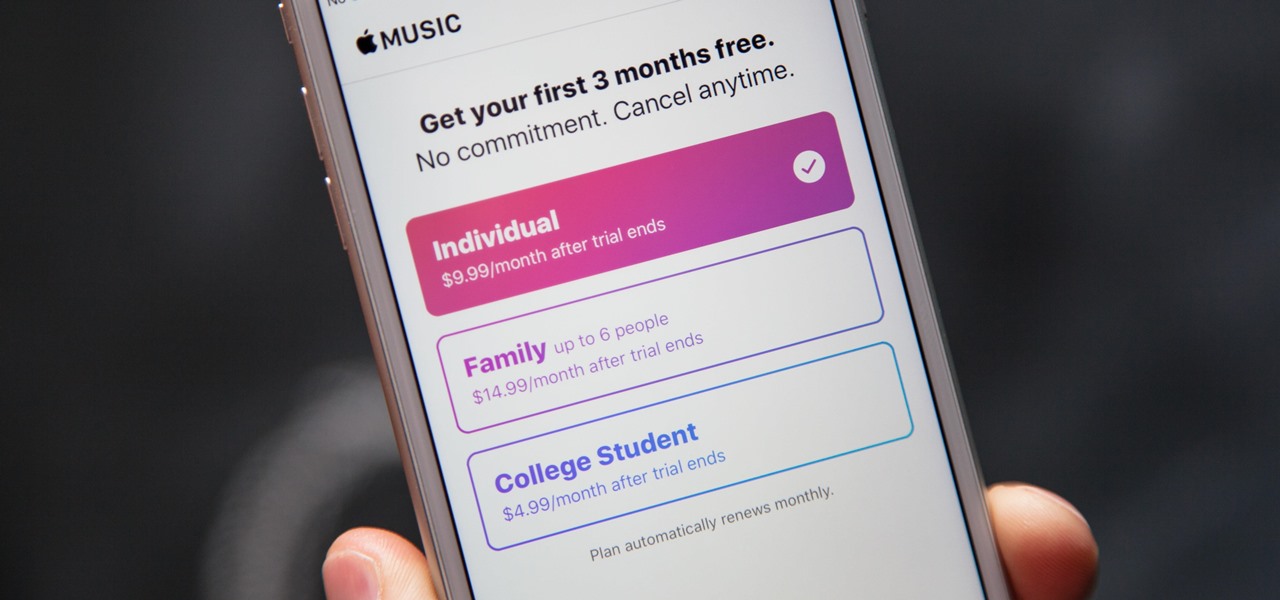
How To: Disable Apple Music's Auto-Renewal for Free Trials So You Don't Get Charged
Apple's streaming music service, Apple Music, offers a three-month free trial that hopes to get you addicted enough to pay for a monthly subscription. You may even see a one-month trial if you're a former subscriber. While it's not very obvious, there is a way to cancel either free trial from auto-renewing. That way, you don't have to deal with Apple support to try and get your money back because you forgot.

News: The 5 Most Useful File-Sharing Apps for Android
Heads up! We've done a new, more thorough review of the best Android file-sharing apps. You can check that out here. Our old file-sharing app roundup can still be viewed below for posterity.

How To: Completely Banish Google from Your Android Experience
Update (February 2019): The methods below will help on older Android versions, but we've recently revisited this topic. So if you have a newer Android phone and you want to get rid of Google, head here.

How To: Exploit Shellshock-Vulnerable Websites with Just a Web Browser
I'm sure that many of us have heard of that nasty Shellshock vulnerability, but not very many people know how to exploit it. Try these few tricks on vulnerable websites!

How To: A Sports Psychologist's Guide to the Perfect Workout Playlist
The right music can spur you to pick up the pace during an intense workout, pep you up before you hit the treadmill or walking path, and even encourage you to lift for just a few extra reps. Although we all have our favorite workout playlists, scientists have discovered what it is, exactly, that makes you workout harder when certain songs begin.

Best Android Antivirus: Avast vs. AVG vs. Kaspersky vs. McAfee
When it comes to antivirus software, you don't want some fly-by-night developer having access to the sensitive data that these apps can scan. Luckily, most of the longest-tenured antivirus companies from the realm of desktop computers offer complete security suites for Android these days.
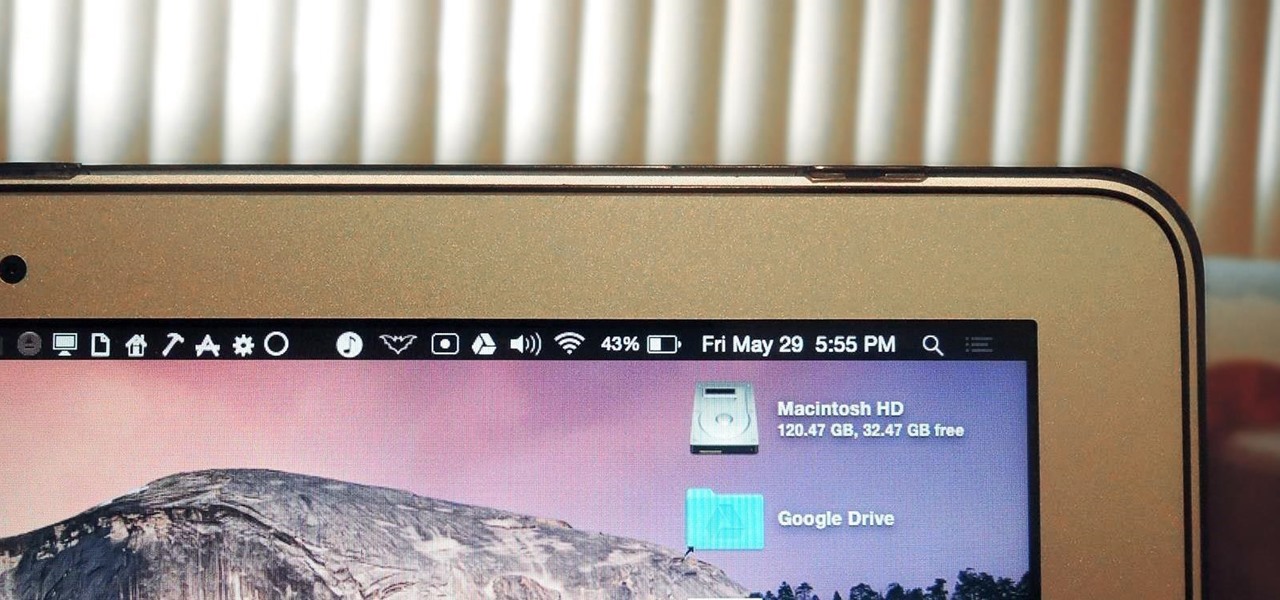
How To: 8 Menu Bar Apps Every Mac Power User Needs
The menu bar is a great place to perform quick searches, track battery life, and switch Wi-Fi networks on your Mac, but it can do way more than that if you let it. I've rounded up some menu apps below that not only have features that will boost your productivity, but are lightweight enough to run entirely from the menu bar.

SPLOIT: How to Make an SSH Brute-Forcer in Python
NOTICE: Ciuffy will be answering questions related to my articles on my behalf as I am very busy. Hope You Have Fun !!!

Cyberwar: Hacker vs. Hacker
From time immemorial, human beings seem to be at odds with one another. When these differences become so heated and unresolvable, it eventually erodes into physical violence. This violence has manifested into some of the most horrific exercises in human history, things which every school child is aware of and none of which we have to recount here. Although humans have been cruel and violent for a very long time, the 20th century may have epitomized that behavior. With two World Wars and many,...
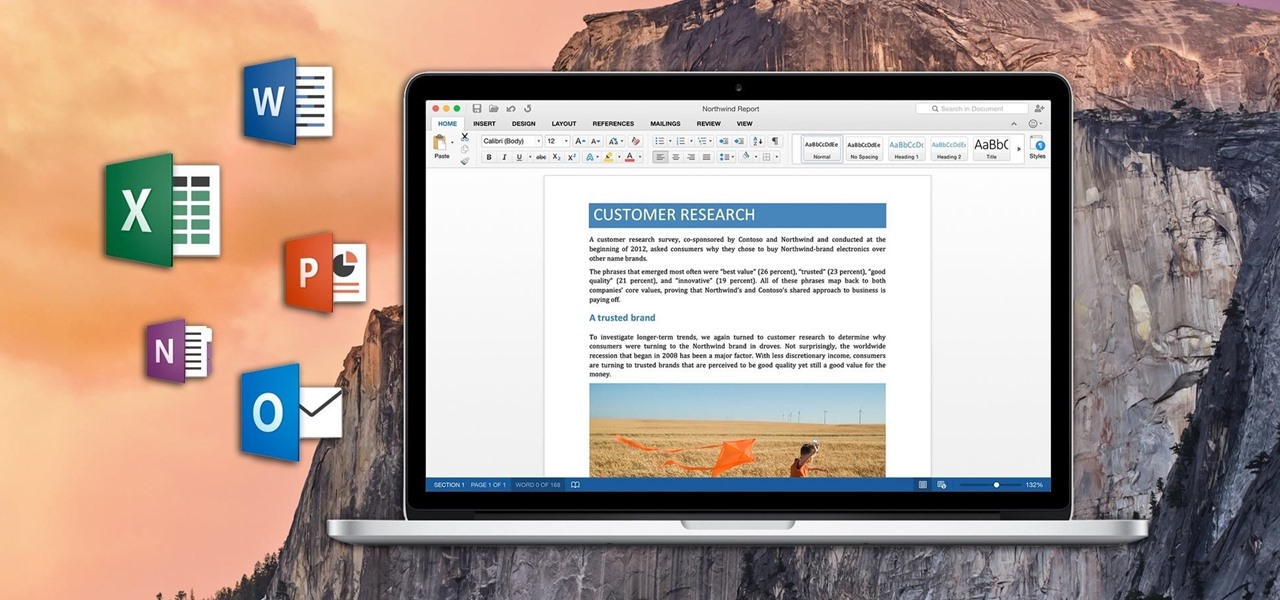
Office for Mac 2016: See What's New & Try Out the Public Preview
If you've ever attended school or held a job, you're probably well familiar with Microsoft Office, whether you used it or not. It's the most popular office suite available, and has been for some time. Apple does have its own suite of productivity apps (iWork), but Microsoft Office has always been the industry leader for word documents, spreadsheets, and presentations.

Hack Like a Pro: Metasploit for the Aspiring Hacker, Part 4 (Armitage)
Welcome back, my hacker novitiates! As you know by now, the Metasploit Framework is one of my favorite hacking tools. It is capable of embedding code into a remote system and controlling it, scanning systems for recon, and fuzzing systems to find buffer overflows. Plus, all of this can be integrated into Rapid7's excellent vulnerability scanner Nexpose.

Hack Like a Pro: Abusing DNS for Reconnaissance
Welcome back, my tenderfoot hackers! As you know, DNS, or Domain Name System, is critical to the operation of the Internet. It provides us with the ability to type in domain names such as www.wonderhowto.com rather than the IP address. This simple service saves us from having to memorize thousands of our favorite website IP addresses. Instead, we simply type in a domain name to retrieve the website.

How To: Connect to Protected Wi-Fi Hotspots for Free Without Any Passwords
Depending on who you ask, internet connectivity should be a basic human right. With Google recently embarking on a project to provide internet capabilities to remote corners of the world using balloons and satellites while Facebook attempts to do the same with unmanned drones, the concept of free web access is steadily gaining steam.

How To: Check Wi-Fi Reliability & Speed at Hotels Before Booking a Room
If you're anything like me, every time you travel you end up in a desperate panic for a decent W-Fi connection. Whether you want to post your photos, research the best beaches, or kill time during an overnight layover, a hotel's Wi-Fi quality is of paramount significance in making a reservation.

Hack Like a Pro: How to Find Exploits Using the Exploit Database in Kali
Welcome back, my budding hackers! When we are looking for ways to hack a system, we need a specific exploit to take advantage of a certain vulnerability in the operating system, service, or application. Although I have shown you multiple ways to exploit systems here in Null Byte, there are still many more exploits available that I have not yet shown you.

News: The 3D-Viewing, Gesture-Controlled Amazon Fire Phone Has Arrived
The long rumored and recently leaked Amazon phone has finally been unveiled, and in the interest of branding, continues down the Fire line—the Amazon Fire Phone. You can check out the full reveal here (warning: it's long), but I'll take you through all the features that sets this device apart from the rest. Before we get into that though, let's check out the specs:

Hack Like a Pro: The Hacker Methodology
Welcome back, my neophyte hackers! Many newbie hackers seem to be confused regarding the process or methodology to employ a successful hack. Most want to simply go straight to the exploit without doing the due diligence to make certain that the hack will work and you won't get caught.

News: Apple Finally Fixes Its Massive iMessage Failure with a New Deregister Tool
It took many months of cries from all around the internet—and a particularly large groan from an ex-Lifehacker editor-in-chief—but Apple has not only acknowledged the existence of its iMessage problem, it's promising a fix.
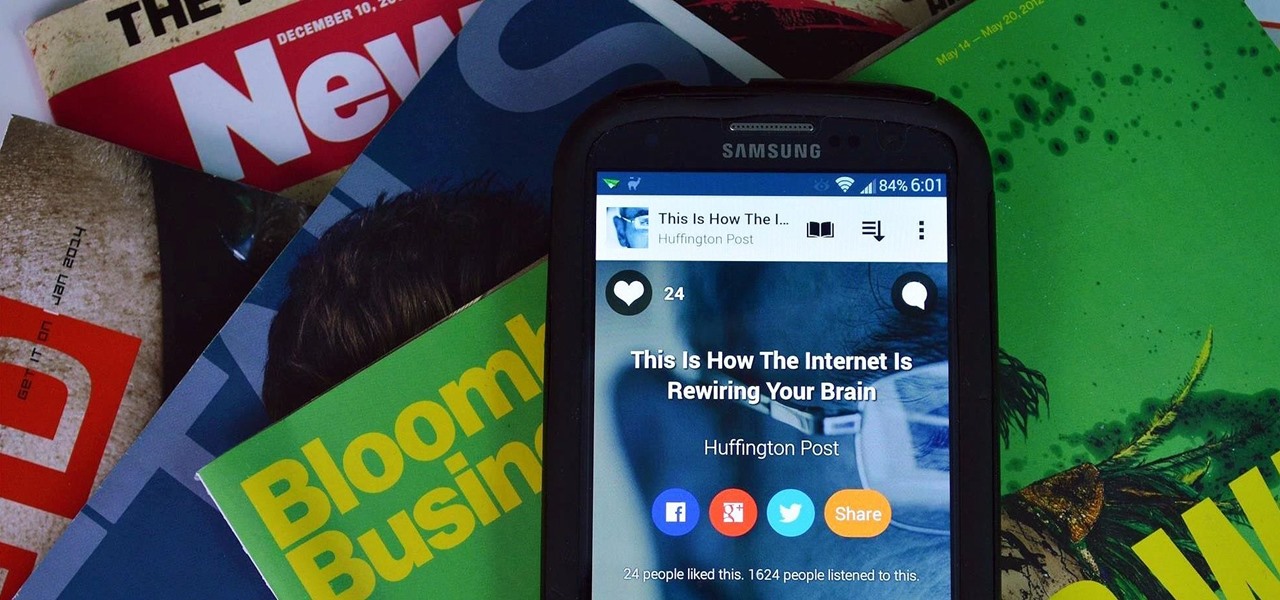
Daily News Without Reading: Listen to Articles Narrated by Real Humans on Your Galaxy S3
Keeping up with current events is a good step towards becoming a well-informed person, but sometimes it's a chore. In-between work, school, commuting, social lives, and hobbies, it can be extremely hard to find time to pick up a newspaper or browse CNN to find out what's going on in the world.

How To: The Safe & Secure Way to Get Your Phone to Remember Your App Passwords
LastPass is a password manager that's been around for some time, and has finally made its way over to Android for use with apps, not just websites.

Hack Like a Pro: Digital Forensics for the Aspiring Hacker, Part 4 (Evading Detection While DoSing)
Welcome back, my hackers novitiates! As you read my various hacking tutorials, you're probably asking yourself, "What are the chances that this hack will be detected and that I'll land behind bars, disappointing my dear mother who already thinks I'm a loser?"

How To: Watch the 2014 Super Bowl XLVIII Game Online or Live Stream to Your Phone or Tablet
The mother of all games is almost here. Super Bowl XLVIII pits the Seattle Seahawks (or Seachickens, if you're from the Bay Area) against the Denver Broncos and regent exemplar of neck surgeries, Peyton Manning.

Hack Like a Pro: Linux Basics for the Aspiring Hacker, Part 12 (Loadable Kernel Modules)
Welcome back, my budding hackers! In my continuing series on Linux basics for aspiring hackers, I now want to address Loadable kernel modules (LKMs), which are key to the Linux administrator because they provide us the capability to add functionality to the kernel without having to recompile the kernel. Things like video and other device drivers can now be added to the kernel without shutting down the system, recompiling, and rebooting.

How To: Install the Android 4.4 KitKat Home Launcher on Your Samsung Galaxy S3
The newest Android operating system, Android 4.4 KitKat, has been unleashed with the arrival of the Nexus 5, and soon to be rolled out to other Nexus devices and Google Play Edition smartphones any day now. Only problem is, the Samsung Galaxy S3 isn't getting 4.4 for a very long time. It doesn't even have 4.3 Jelly Bean yet.

How To: Use Android Device Manager to Find, Wipe, & Lock Your Android Phone or Tablet
If you haven't heard yet, Google made it possible a couple months ago for every Android user running 2.2 or higher to track his or her smartphone or tablet using their Android Device Manager service. It's a super easy way to track, lock, and secure erase your Android device from the web without ever having to download a third-party application, like Droid Finder, since it occurs in the background via Google Services.

Hack Like a Pro: How to Perform Stealthy Reconnaissance on a Protected Network
Welcome back, my fledgling hackers! One of the first issues any hacker has to address is reconnaissance. Before we even begin to hack, we need to know quite a bit about the target systems. We should know their IP address, what ports are open, what services are running, and what operating system the target is using. Only after gathering this information can we begin to plan our attack. Most hackers spend far more time doing reconnaissance than exploiting.
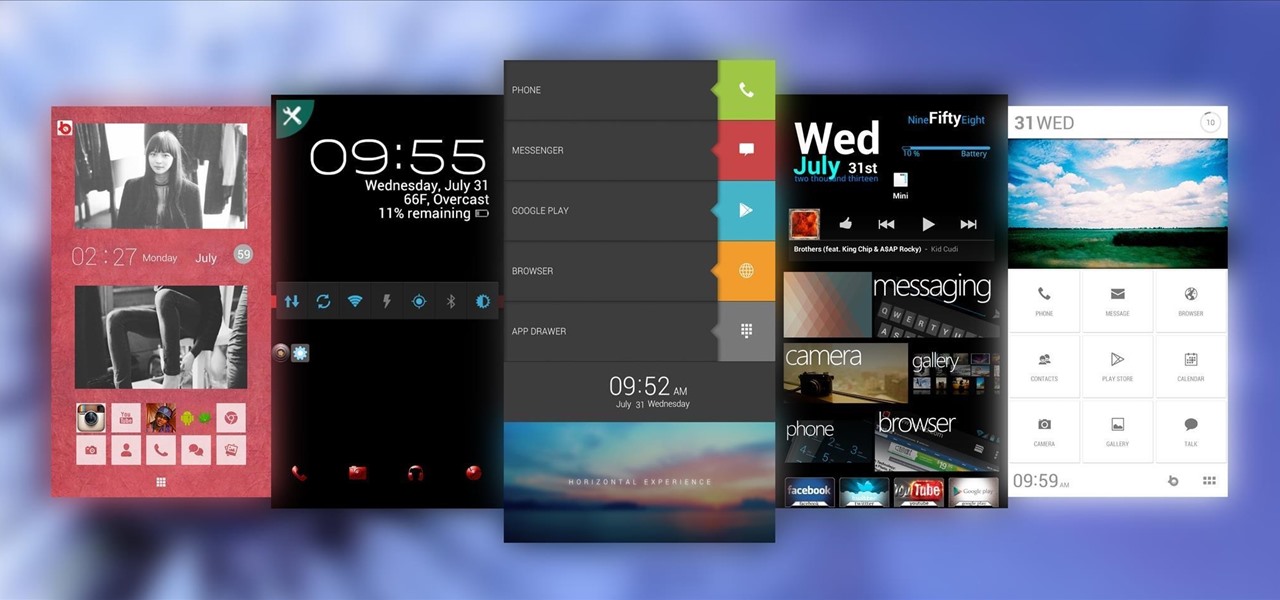
How To: 40,000+ Ways to Customize the Android Home Screen on Your Samsung Galaxy Note 2 (No Root Required)
Customizing isn't all rooting and ROMs—there are plenty of ways to customize your Samsung Galaxy Note 2 or other Android device without gaining superuser access. One of the easiest ways is to install an Android launcher, sometimes called a home launcher, that matches your style.

How to Hack Wi-Fi: Performing a Denial of Service (DoS) Attack on a Wireless Access Point
Welcome back, my neophyte hackers! As part of my series on Wi-Fi hacking, I want to next look at denial-of-service (DoS) attacks, and DoSing a wireless access point (AP). There are a variety of ways to do this, but in this tutorial we'll be sending repeated deauthentication frames to the AP with aircrack-ng's aireplay. Remember, hacking wireless networks isn't all just cracking Wi-Fi passwords! Our Problem Scenario
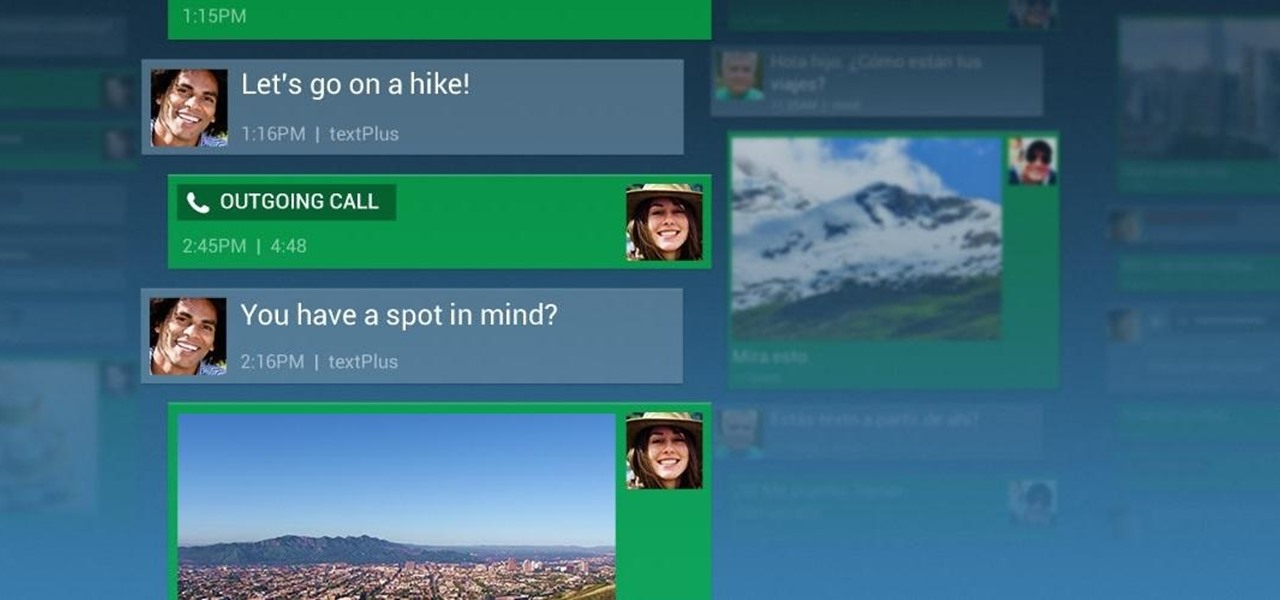
How To: Tired of Paying for Calls & Texts? These 6 Free Apps Can Cut Down Your Cell Phone Bill
Smartphones are great. They help you keep in touch with your loved ones and stay up to date on what's going on in the world. The problem is that like everything else that's useful, they cost money to use, and between calling, texting, and data plans, it can get really expensive.

How To: Find Out Who Doesn't Like You Anymore on Facebook, Google+, Instagram, Pinterest, Tumblr, and Twitter
Offensive pictures, depressing tweets, political statuses, and just plain old dumb comments are only a few of the reasons why people unfriend or unfollow others on social media sites. Sometimes it's just social spring cleaning, other times there's no reason at all.

Anonymous Texting 101: How to Block Your Cell Phone Number While Sending Text Messages
When browsing the web, I enjoy my privacy. It's reassuring that I can peruse the internet without the worry of having my activity tracked back to me, allowing me to leave fun, anonymous comments when I get the urge to troll.

How To: Make Room for Your New Gadgets (And Get Some Cash in the Process)
There's nothing like buying an awesome new gadget, but it leaves you with one problem (besides an empty wallet)—what do you do with the ones you already have? There are plenty of ways to put your old gadgets to use, but if you'd rather get rid of them, you may as well get something out of it, right? Here are five places where you can recycle your electronics and replenish your cash stash.

How To: Oops! Hit "Send" Too Soon? Here's How to Recall Sent Emails on Almost Any Platform
Send an email prematurely? Forgot to attach a file? Accidentally addressed it to the wrong person? It happens to the best of us. But what can you do to get it back? Hack into the other person's email account and delete the email before they get a chance to see it? Unless you're a hacker extraordinaire, that option is unlikely. So, what can you do? If the email has already been sent, you're probably out of luck. Even if they didn't read it yet, your chances of retrieving it are slim. But some ...

How To: Your Guide to Finding Free Creative Commons Images and Other Media Online
Creative Commons is awesome—really. If an image, video, or audio file is tagged with a CC license, that means you can use it as long as you give appropriate credit to the owner. For bloggers with no money for pricey stock media, it's a godsend. When you license your own media under CC, you can choose how you want it to be used by others and whether or not it can be used commercially.

Apple's Fix Failed: In-App Purchases Still Free with This Hack
A few days ago, Russian hacker Alexy Borodin found a way to get free in-app purchases on an iPhone or iPad. In-app purchases include things like items and power-ups for iOS games, as well as subscriptions and "premium" memberships for certain apps.

How To: A Hitchhiker's Guide to the Internet: Today and Now, How It All Connects
In the first part of this series, we took a factual and technical look at the history of the Internet. I explained how all of these wires and servers got here in the first place. Obviously, a firm did not just create and build the Internet around 1995! Now that we know how the Internet came to be, we can get into the really fun stuff—what the Internet looks like now! Well, that's not quite the network design I was talking about, but it does show what the Internet looked like back in 2007 befo...

How To: Follow along with cricket gameplay by learning the rules compared to baseball
Have you ever heard of cricket? No, we're not talking Jiminy Cricket or the wireless cell phone service provider. We're talking about CRICKET. The team sport, nicknamed "the gentleman's game," is the popular sport of choice in places like India, Australia, South Africa, Sri Lanka, England, Pakistan and Zimbabwe, though not America. But guess what? It's very similar to the American pastime we all love so much— baseball.

