Google made a huge splash this year in their annual Google I/O with an awesome announcement regarding their Photos app. Although I was primarily interested in the details surrounding Android M, my ears instantly perked up when Google announced that their Photos app will now offer free, unlimited, high-quality storage.

The Nexus Player is one of the most robust set-top streaming devices on the market. This is mainly due to the fact that the base software it runs is a direct fork of Android, which is a very powerful operating system itself.

With over a billion monthly active users, it seems that Facebook is nowhere close to being dethroned as the most popular social media service in the world (sorry, Ello). While their stats may be impressive, it doesn't mean that Facebook is as good as it can be.

Many modern Android devices use a display technology called AMOLED. These screens differ from traditional LCD displays in that each pixel emits its own light, so a backlight is not required. Even better, when rendering a black element on the screen, AMOLED displays simply don't light up the associated pixels, meaning virtually no power is used. Since black pixels use little to no power on an AMOLED screen, more black pixels means lower battery consumption.

When it comes to getting your computer and smartphone to work well together, there's no service more robust and capable than AirDroid. For years, it's been the go-to tool for users looking to transfer files between their devices or access contact lists and call logs from their computer.
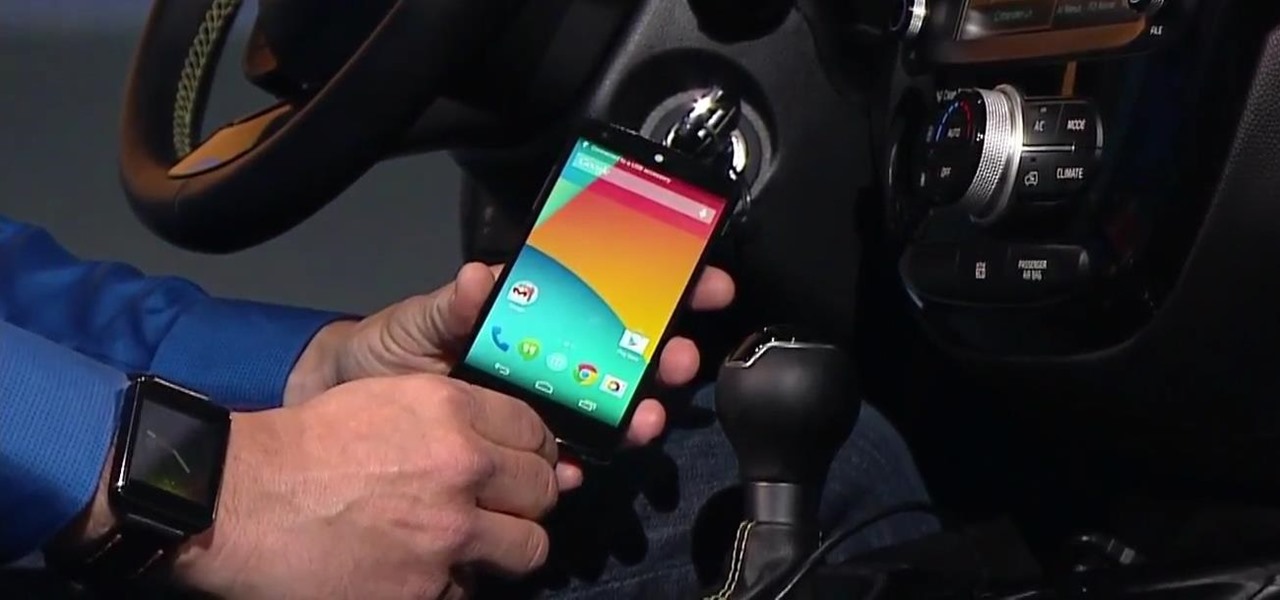
This year's I/O was all about bringing Android into the future and onto new devices. On top of announcing the upcoming "L" release of its mobile OS, Google showcased Android Wear, Android Auto, and Android TV.

Welcome back, my greenhorn hackers! Sometimes, we don't have a specific target in mind, but rather we are simply looking for vulnerable and easy-to-hack targets anywhere on the planet. Wouldn't be great if we had a search engine like Google that could help us find these targets? Well, we do, and it's called Shodan!

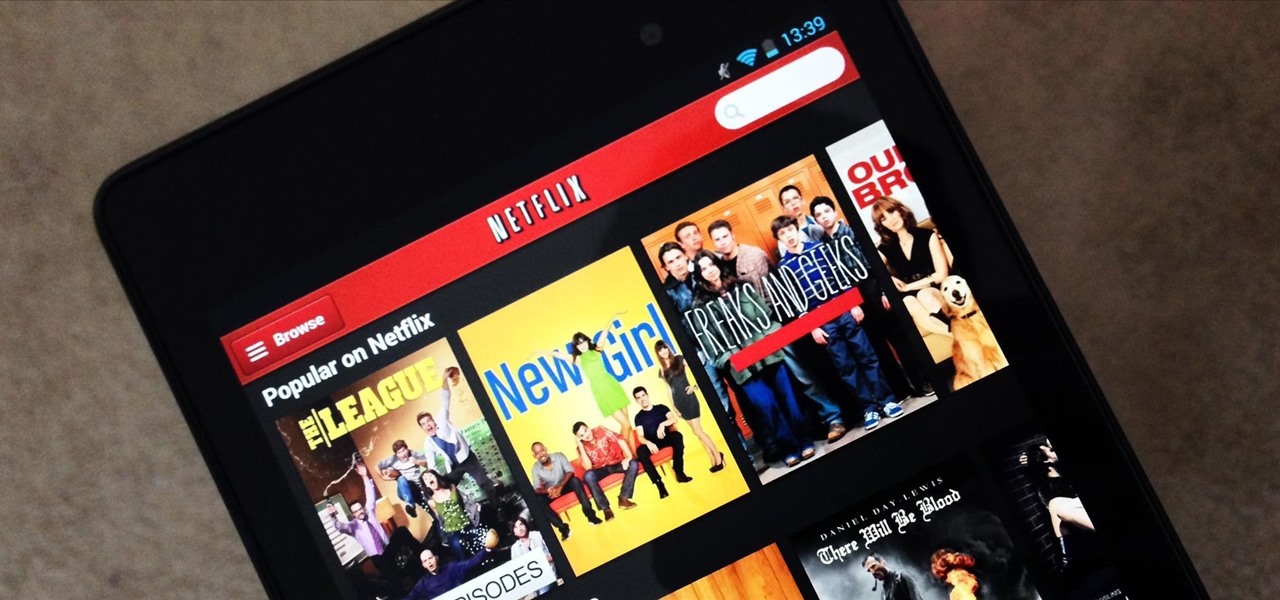
Netflix is more popular now than ever, but it still has a ways to go before satisfying everyone. Whether it's a lack of availability, buggy or unattractive apps, or just not being able to find anything to watch, lots of people have their complaints.

Not having internet sucks! We do a ton online these days, from working, shopping, studying, and collaborating, to watching fail videos and endlessly clicking through memes.

Google Reader is soon to be no more. Yesterday, the company announced that the service will be shutting down as of July 1, 2013, as part of Google's second "Spring Cleaning."

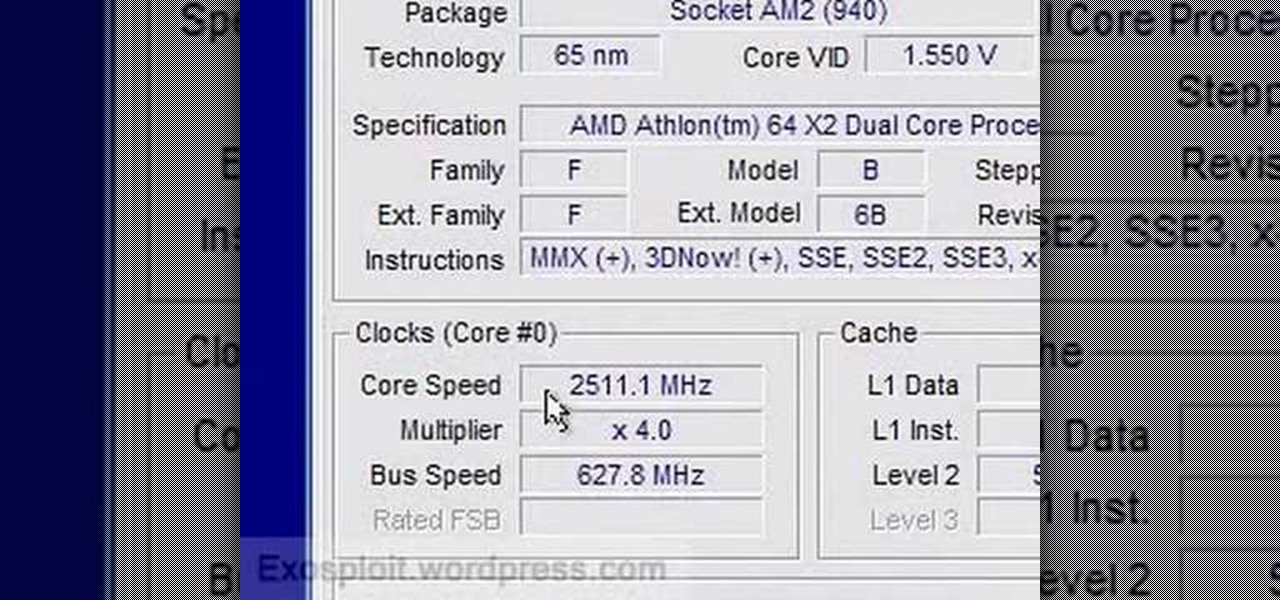
In this video from exosploit we learn how to find your system specs in Windows XP. If someone is trying to help your computer, you might need this information. Right click My Computer, and click Properties. Here you'll see your operating system, service pack, and how much RAM you have. Also google cpuz. Go to the first link and download it. Extract it and click the main file. Here it will tell you your processor, mother board, what bios version you have, how much RAM you have, and it will tel...

In this tutorial, we learn how to powerbleed your brakes. First, test for any leaks and then release the pressure so you can fill the bleeder tank with fluid. After this, you will screw the pump on and then start to pump pressure to approximately 15 psi or check your service manual for recommended pressure. As the pressure builds, you will see fluid traveling through the tube to the brake reservoir. Use a bottle to catch the fluid that is bleeding through the system. When you bleed your brake...

If you're working on a LLV postal truck, this video will show you how to determine if you've got a bad fuel pump or not. It's a quick diagnosis trick to determining if there's an electrical problem with the fuel pump, and first you need to take out the ECMB fuse, plug a jumper wire where it was, use a multimeter and labscope to see what's going on. The United States Postal Service (USPS) uses these trucks for all their postal deliveries, and if you're the mechanic working on it, this and the ...

The control arm on a Grumman Long Life Vehicle, or LLV, postal truck (used by the United States Postal Service (USPS)) is exactly the same as the control arm on the Chevrolet S-10 pickup truck, so the replacement procedure is almost identical. This video will show you that procedure, but it's important that you get the right part for the side you're replacing. The LLV is right-side steering, so the driver's side is the passenger's side on the S-10. It's a little confusing, so be careful.

The truck in this video was having a misfire problem during routine service. This video for mechanics will show how to find the problem of this misfire. The first thing to look at is the lab scope. After that, comes time for the smoke machine test to identify a possible cylinder compression leak. Watch and learn. This is very similar for a lot of different automobiles.

YouTube is a great video service because it's free and has invaded the world… meaning, practically everybody has been on YouTube at one point or another. Another great aspect of YouTube is the ability to embed content on your website or blog… like your WordPress blog. You can also embed full YouTube playlists. This video will show you the steps to embedding YouTube playlists on your WordPress blog, and the principles can be applied for other sites as well.

In this video tutorial, you'll learn how to change a damaged belt or brushbar on the Vax V-026 Rapide Deluxe carpet washer.

In this video tutorial, you'll learn how to change a damaged belt/brushbar on the V-006 Turboforce vacuum cleaner

In this first clip, Chef John shows the basic restaurant technique for poaching eggs. Due to the high-volume of a brunch service, it is almost impossible to poach eggs “to order.” They are poached ahead of time and held in cold water until final plating, when they are re-heated in simmering water for a few minutes. This method also works great at home for smaller batches as you’ll see. Once you’ve poached your eggs and have them in cold water you are free to set up the rest of the plate

You no longer have to worry about repair technicians accessing the personal information on your iPhone when you send it in for repairs. With Apple's new security feature, you'll no longer have to erase your iPhone to ensure your photos, messages, accounts, and other private data remain for your eyes only.

Apple's iOS 16.3 update for iPhone had impressive new features, but iOS 16.4 might impress you even more.

Planning a vacation overseas can sometimes feel overwhelming with the number of things you need to remember before heading out. Since smartphones keep us connected at all times, it's essential that you have everything you need here as well. Unexpected events can arise while on your trip, and you should be prepared for anything like a survival expert.

The tactic of brute-forcing a login, i.e., trying many passwords very quickly until the correct one is discovered, can be easy for services like SSH or Telnet. For something like a website login page, we must identify different elements of the page first. Thanks to a Python tool for brute-forcing websites called Hatch, this process has been simplified to the point that even a beginner can try it.

Many popular IoT devices have terrible security. For instance, a hacker who's on the same Wi-Fi network as a Sonos speaker can assume direct control over the device's behavior. If an IoT device doesn't secure the messages used to control it over a network, it's easy for somebody to write a few Python scripts to make it do whatever they want.

Kali Linux is established as the go-to operating system for penetration testing, but in its default configuration, it's less than ideal for regular desktop use. While in many scenarios, a live boot or virtual environment can resolve these issues, in some situations, a full installation is better. A few simple changes can be made to a Kali Linux desktop to make it safer to use in this environment.

Conducting phishing campaigns and hosting Metasploit sessions from a trusted VPS is important to any professional security researcher, pentester, or white hat hacker. However, the options are quite limited since most providers have zero-tolerance policies for any kind of hacking, good or bad. After researching dozens of products, we came out with 5 potentials that are ideal for Null Byte readers.

The internet is constantly under siege by bots searching for vulnerabilities to attack and exploit. While conventional wisdom is to prevent these attacks, there are ways to deliberately lure hackers into a trap in order to spy on them, study their behavior, and capture samples of malware. In this tutorial, we'll be creating a Cowrie honeypot, an alluring target to attract and trap hackers.

Every time you make a call or send a text, you're giving the recipient your phone number. This can be quite the security vulnerability, opening yourself up to scammers, spammers, and the feds. In this how-to, we'll look at what a burner phone is, why you might want one, and how to get started using a free second phone number on your regular smartphone.

Equifax reported on Sept. 7 that it discovered a breach on July 29 which affects roughly half of Americans, many of whom don't realize they have dealings with the company. Hackers got away with social security numbers, addresses, and driver's license numbers, foreshadowing a "nuclear explosion of identity theft." Let's explore what really happened and what you and those around you can do to protect yourselves.

The dark web is an intimidating place for a newbie hacker, but it's a powerful tool once you've learned to navigate it safely. To help you out with that, this guide will cover some need-to-know information for traversing the dark corners of the internet while keeping your identity and data safe. (Hint: Using Tor is not enough.)

Greetings all. Today I intend to append a new series to my mini-collection of posts. This series will consist of informative guides for the purpose of depicting certain aspects of the White Hat profession that I believe are of profound importance. Furthermore, I will keep this series simple for everyone to follow, regardless of your tech level. So without further ado, let's get right into it.

Apple's latest mobile operating system, iOS 9, may not be the huge overhaul that iOS 8 was, but that doesn't mean there aren't plenty of new features. In fact, there are a ton of subtle changes that you may not notice right away. Here's a rundown of all the coolest new features you need to know about on the new iOS 9 for iPad, iPhone, and iPod touch.

NOTICE: Ciuffy will be answering questions related to my articles on my behalf as I am very busy. Hope You Have Fun !!!

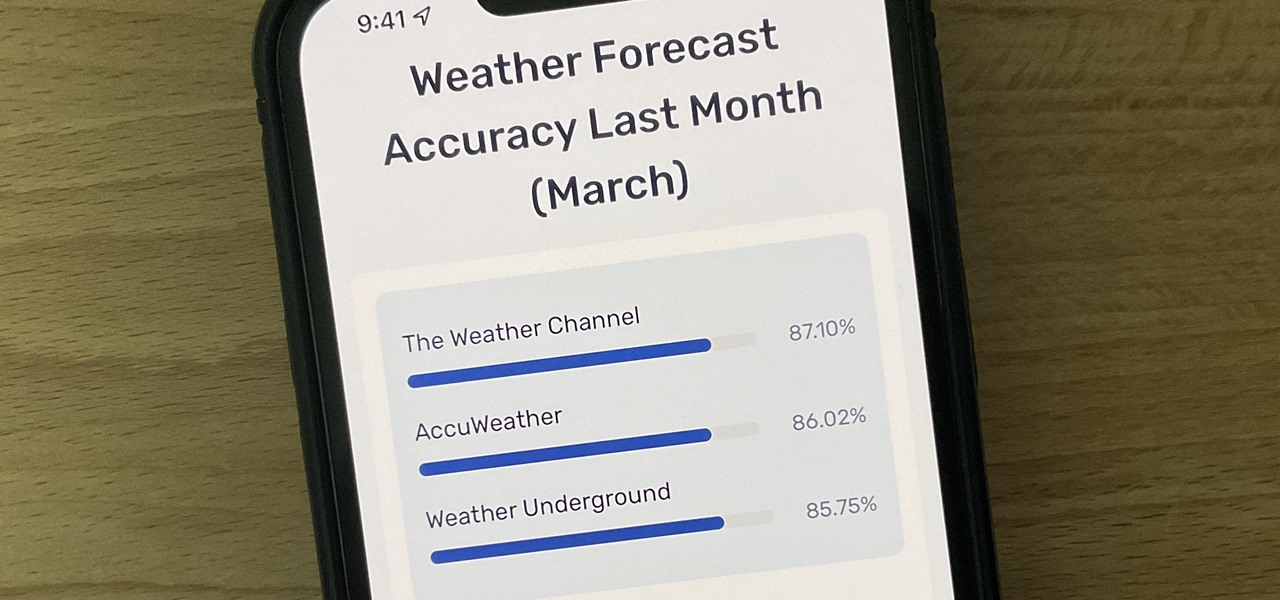
Not all weather sources are equal. When you're looking at the forecast, you hope that it's at least semi-accurate so you can plan the week and days ahead, but many sources are unreliable. And with the famous Dark Sky API shutting down on March 31, 2023, you'll need an alternative source of weather information if you use an app that utilizes that API.

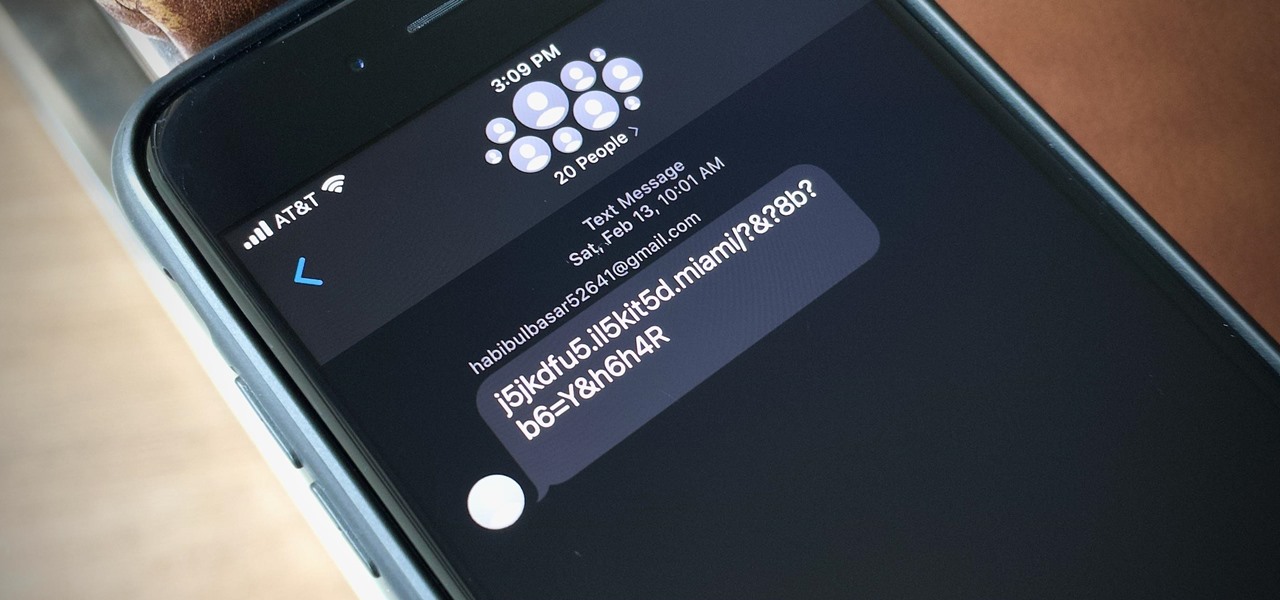
Next to spam calls, few things are more annoying than being inundated with spam, scam, and smishing texts. Your iPhone's Messages app should be a place for your friends and family to stay in touch, not a minefield of phishing attacks, malicious links, and viruses. Luckily, there are quite a few methods to block and report your way to a more spam-free iPhone.

If it has an internet connection, it's got a huge attack surface for hackers. But what makes your phone even more dangerous is its portability and the collection of sensors it houses that can be just as good at tracking you as the camera and mic.

Using a strong password is critical to the security of your online accounts. However, according to Dashlane, US users hold an average of 130 different accounts. Memorizing strong passwords for that many accounts is impractical. Fortunately, password managers solve the problem.

There's never been a better time for streaming movies and TV shows on the go. With so many services available, the only limitation to your enjoyment is your phone's accessories. Whether you're buying for yourself or someone else, here are some of the best gifts that improve the movie-watching experience on mobile.

In the first part of this series, we took a factual and technical look at the history of the Internet. I explained how all of these wires and servers got here in the first place. Obviously, a firm did not just create and build the Internet around 1995! Now that we know how the Internet came to be, we can get into the really fun stuff—what the Internet looks like now! Well, that's not quite the network design I was talking about, but it does show what the Internet looked like back in 2007 befo...

Apple announced support for mobile driver's licenses and state identification cards in Apple Wallet back in 2021, and Arizona was the first state to jump on board in 2022. Fast forward to now, and only eight states let you add a driver's license or state ID to Apple Wallet on your iPhone and Apple Watch. It has been a slow rollout, but more states are coming or are at least showing interest.