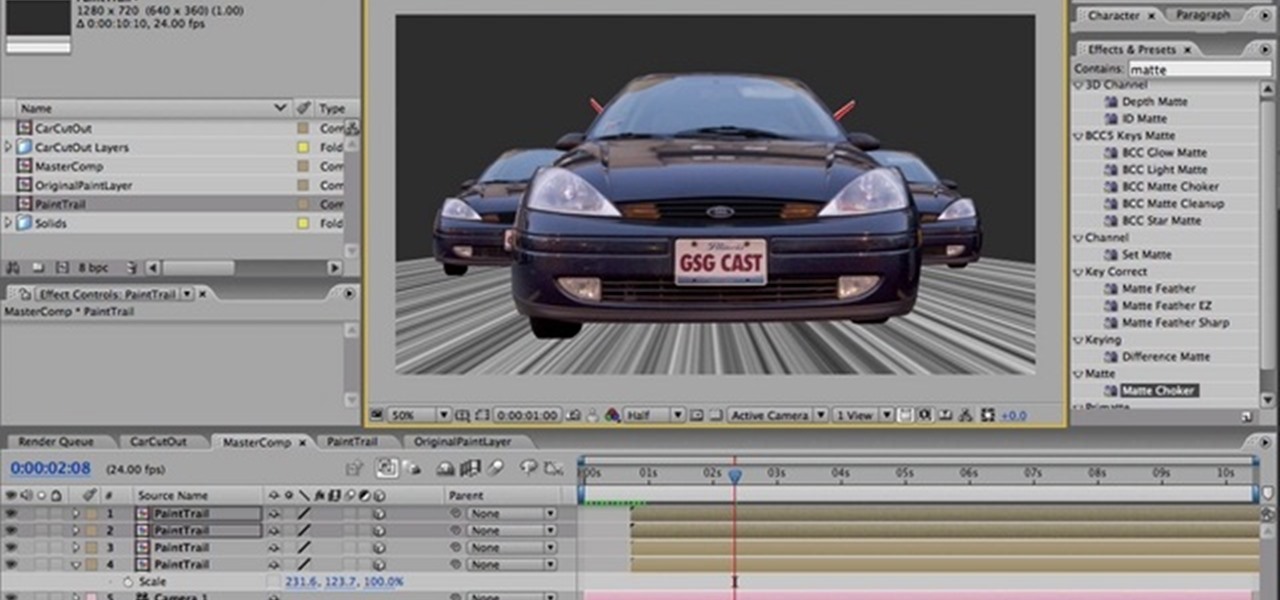
How To: Build a car racing scene from photographs
In this great, albeit long, tutorial Nick from Greyscale Gorilla shows you how to create a car racing scene from a series of photographs in After Effects. It's very kinetic and looks great.


In this great, albeit long, tutorial Nick from Greyscale Gorilla shows you how to create a car racing scene from a series of photographs in After Effects. It's very kinetic and looks great.
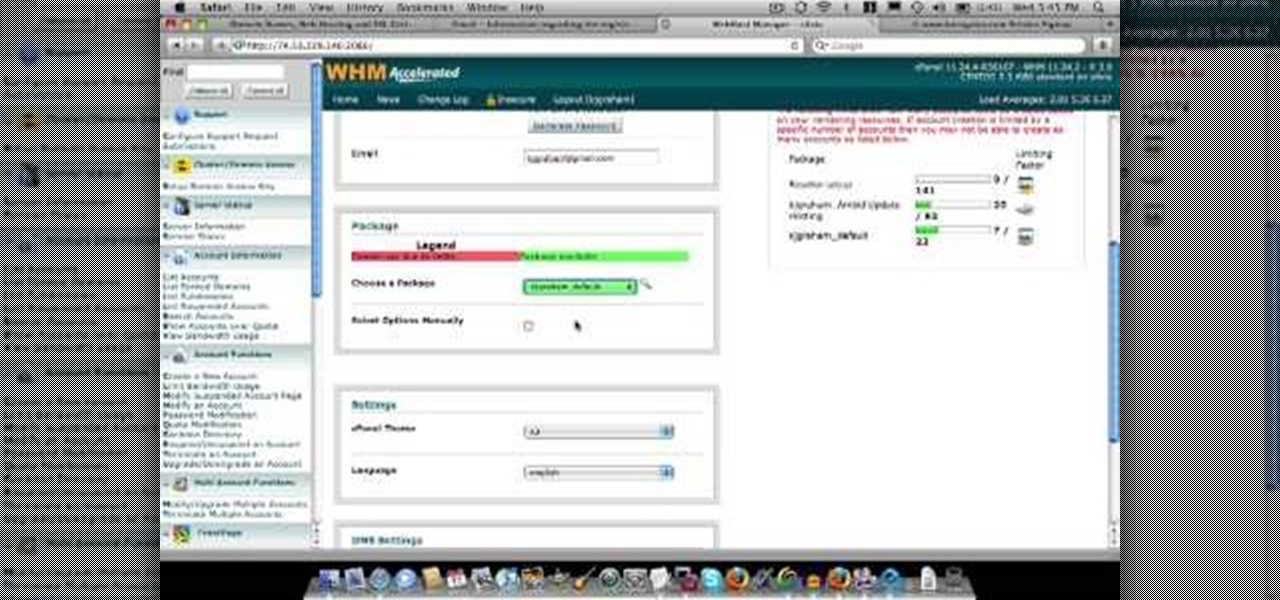
In this video about choosing a web hosting company. The narrator begins by saying that web pages are hosted on servers; the files that make up a web site are hosted or stored on a server. The narrator recommends a service called Host Gator. He indicated they are reliable and provide reasonably priced web hosting services. He briefly discusses the process they charge for their different levels of hosting services. Next he shows the steps to hook your domain name to the host account. He demonst...

This is a great instructional video on how to build an 8000 lumen CFL and makeshift rain shield. First you need build a PVC frame. For that you will need 3-3/4 'T'S, 4-12" 3/4 pipes,2-2 1/2 " pipes and 4-3/4 caps. You will also need 1-1 " 'T'. 2- 1" 1" pipes and 1-1"-3/4" reducer. Hold the job in a mechanical vice and cut the material into required sizes and make the snap fittings. Then friction fit the rest of the components into this stand. Then lastly you have to make the light box. That i...

Do your presentation skills need a little work? Being in front of a crowd or some potential clients may be one of the hardest things you will ever do, but staying confident makes all the difference. Losing any bit of confidence will result in your presentation falling flat and killing your self-esteem, and perhaps even risking your job. So, being confident is a must.

Eagle Lake Woodworking, hosted by John Nixon, offers great do-it-yourself guides for building your own furniture, especially in the American Arts and Crafts style, and turning your garage into an amateur woodshop. Search Eagle Lake on WonderHowTo for more carpentry tutorial videos. From Eagle Lake Woodworking on this specific lesson:

Temperatures plummet... a shelter, an igloo, can be built out of nothing but snow. It has to be the right kind of snow, cut from a well packed snow drift. The best snow is laid down in one single storm, it's hard and compact.

K'NEX is one of the most popular construction toys on the market, right next to Lincoln Logs and LEGOs, but what makes K'NEX stand out is the fact that children can build mechanically derived toys. Instead of blocks or little logs, kids use interconnecting plastic rods and connectors, which give them tons of contraptions to build and play with. Today, K NEX has even more possibilities with wheels, pulleys, panels and flexi-rods to make amusement park roller coasters, airplanes, animals, bikes...

K'NEX is one of the most popular construction toys on the market, right next to Lincoln Logs and LEGOs, but what makes K'NEX stand out is the fact that children can build mechanically derived toys. Instead of blocks or little logs, kids use interconnecting plastic rods and connectors, which give them tons of contraptions to build and play with. Today, K NEX has even more possibilities with wheels, pulleys, panels and flexi-rods to make amusement park roller coasters, airplanes, animals, bikes...

Build stones & cinder blocks for a diorama. Papa Tom teaches viewers how to make a building look like it is made of stone or cinder blocks using the Building and Structure Kit from Scene-A-Rama. This is super easy and tons of fun for all ages. It's great for school or class projects. Use a ruler, a fine point marker, a hobby knife, and a paint brush.
If you're a hacker, pentester, or any other type of Null Byte reader, and would like to create a website to showcase your services and skill set, you may not have the time or energy to do it the long way.

While we haven't covered Amazon Web Services, or AWS, on Null Byte before, Amazon's cloud computing platform is ripe for attack by hackers, pentesters, and cybersecurity researchers. It's also an excellent cloud hosting service to build or use vulnerable-by-design AWS setups and frameworks.

The next libSSH or OpenSSH exploit may be just around the corner. Keep your SSH service out of Shodan's database before hackers find new ways to bypass the password protecting the server.

London-based developer Andrew Hart has been working on AR navigation since Apple's original ARKit tool was still in beta preview. Now, he's ready to unleash his technology on the world.

Amazon Web Services is calling up an age-old tactic of the tech industry — the hackathon — to drum up excitement and encourage the development of apps built on the Amazon Sumerian AR/VR platform.

After a district judge approved the $85 billion merger between AT&T and Time Warner, we knew AT&T would be quick to reap the rewards of capturing Time Warner's media properties. Today, we get our first look at this with two cellular plans from AT&T. What makes these plans unique is they include a new cord-cutting service called WatchTV.

Location services company Mapbox has added new capabilities to its location-based gaming tool to fend off Google's challenge for the same mobile app category.

Augmented reality hardware maker Avegant has reportedly laid off between 20 and 30 employees, with founder Edward Tang returning to the CEO role at the company.
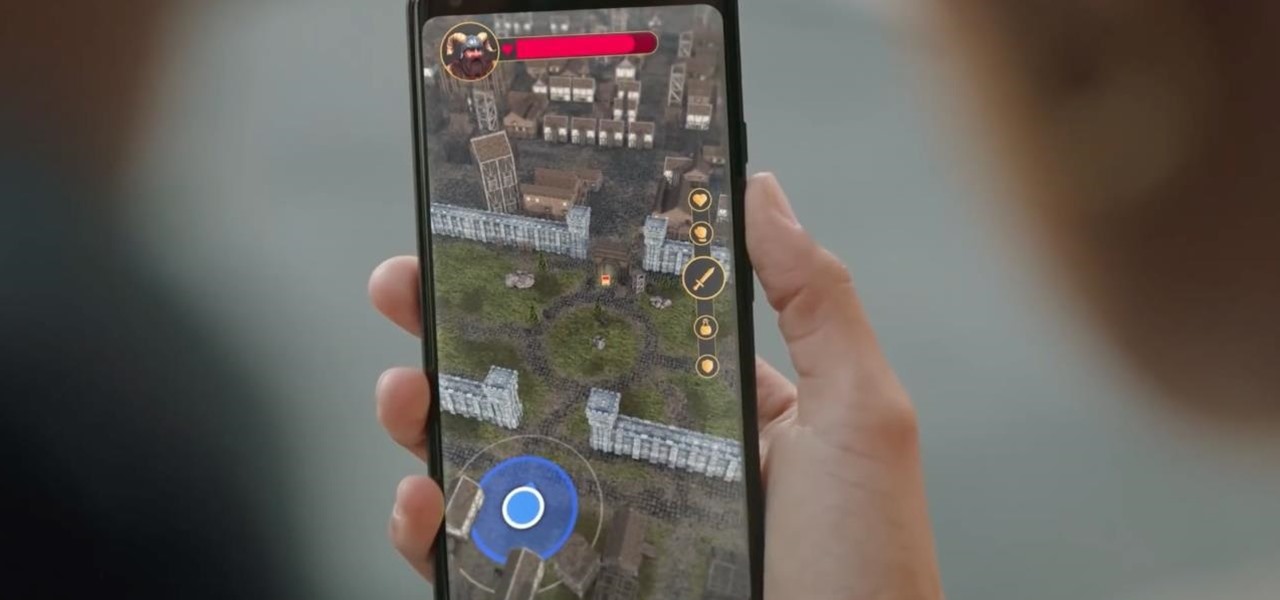
Franchises left and right are releasing Pokémon Go-style augmented reality games, and Google is making it even easier to churn out the apps.

The OnePlus 5T was just released, and it's packing several new useful features. While many OnePlus 5 buyers are feeling frustrated with the quick release cycle, lots of fans are still clamoring to buy the new device. Aside from the larger screen, most of the buzz around the 5T has centered around the new face unlock method. Thanks to a clever hack, you can now get this feature on almost any phone!

Apple released the second version of its iOS 11.2 developer beta Monday, exactly one week from beta 1, then opened up the public beta version on Tuesday. While beta 2 has been available on iPhone X since Friday, Nov. 3, all compatible iPhones can now update to this version.

Ransomware is software that encrypts a victim's entire hard drive, blocking access to their files unless they pay a ransom to the attacker to get the decryption key. In this tutorial, you'll learn how easy it is to use the USB Rubber Ducky, which is disguised as an ordinary flash drive, to deploy ransomware on a victim's computer within seconds. With an attack that only takes a moment, you'll need to know how to defend yourself.

At the Augmented World Expo Europe press conference in Munich today, RE'FLEKT will unveil the addition of remote video calling to their RE'FLEKT One enterprise augmented reality platform, in addition to ARKit and ARCore apps that demonstrate the platform's capabilities.

It has been an interesting few days in developer news. The Microsoft blog has been busy with information relative to the augmented reality space. Meta 2 has also announced an interesting development this week. Here is a collection of various tidbits that have been collecting up.
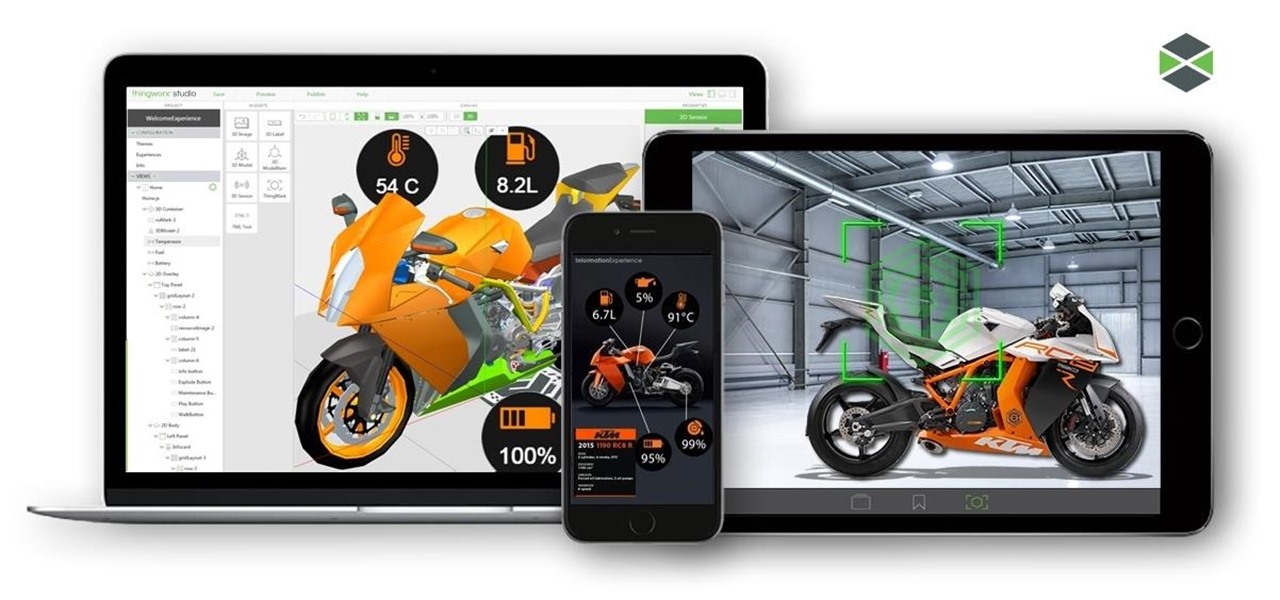
For companies wary of the temperature, PTC just made it easier for them to dip their toes in the waters of augmented reality.

The common thread between this week's Brief Reality stories is that augmented reality is beginning to prove its worth as a technology that improves workflows and processes. From customer service to healthcare to manufacturing, augmented reality is helping companies improve productivity.

Google's former driverless car boss Chris Urmson raised considerable funds to get his new startup company Aurora Innovation up and running. Axios initially reported that Urmson raised over $3 million to fund his brainchild in the wake of his Alphabet exit, according to an SEC filing.

This is a nice project that you can continue to work on and modify as you learn more Arduino projects. The Instructable linked below goes through the complete build for the Bluetooth-enabled robot seen in the first half of the video.

Welcome back, everyone. In the previous part of this rapid-fire miniseries, we built the attacker portion of the shell. In this article, we'll just be testing it to see if everything works correctly.

Android has a single text file named build.prop that determines tons of various system-wide settings on your device. You need root access to edit this file, since it's stored on the system partition—but the various lines of codes it contains are actually fairly easy to interpret and modify.

Firstly let me start by giving credit to Lucid for their guide on Evilzone which inspired this idea, as well as the recent talk of anonymity on here.

On Thursday morning, May 28th, Google announced an upcoming version of Android—and within a few hours, a preview build of this so-called "Android M" release was made available to select Nexus devices.
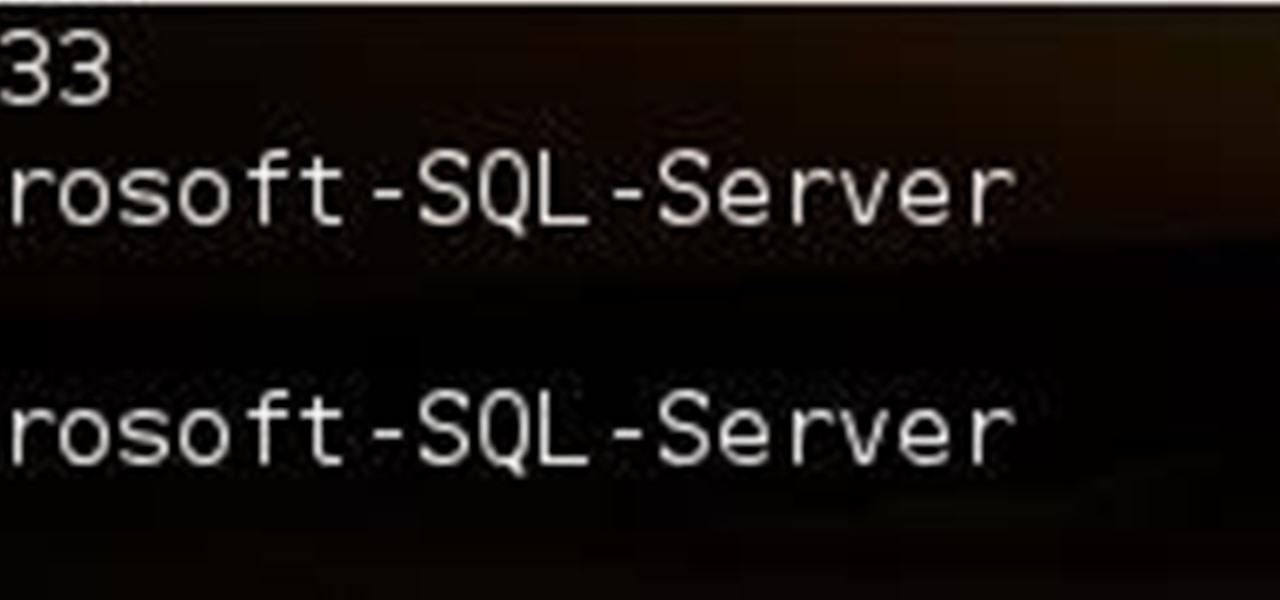
I wrote a python script that allows you to easily ask what service runs on a specific port and vice-versa. Now, I am sure that such a program already exists on our lovely linux OS's, but... I didn't think of that before I started, and haven't found it yet. So if you haven't found it yet either, maybe you'll find this of some use. It's just called getport. If I have a port number, and want to know what services run on that port, I do:

Google recently rolled out a new Smart Lock option labeled "On-body detection" for Android Lollipop via an update to Google Play Services. As I'm sure you can gather from the name, this new function keeps your phone or tablet unlocked using the built-in accelerometer to determine whether or not your device is being carried on your body, allowing you to set it down and walk away carefree knowing that's it's locked again.
When it comes to subscription-based music streaming services, the conversation doesn't go much further than Spotify and Google Play Music (previously called "All Access"). Both services are essentially the same aside from slightly different catalogues and social options, and they both run ten bucks a month for unlimited music streaming and offline track saving (although Spotify does have a free, ad-supported service).

Welcome back, my tenderfoot hackers! I have written many tutorials on hacking using Metasploit, including leaving no evidence behind and exploring the inner architecture. Also, there are my Metasploit cheat sheets for commands and hacking scripts.
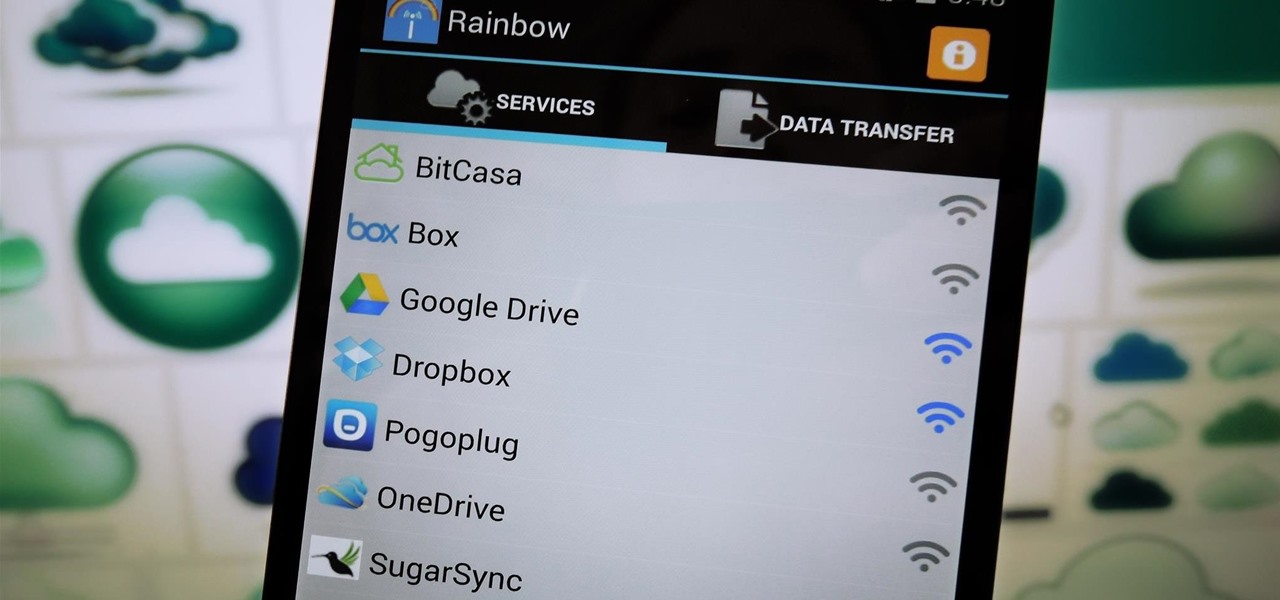
With limited storage options available on the Nexus 5, cloud storage can definitely come in handy. But sometimes, with the seemingly endless options of cloud services for us to choose from, our online data can get a bit disorganized.

Veering from common practice, XDA commenter, "the_commenter", discovered a changelog for the upcoming version of Android 4.4.3 tucked away on Google's servers.
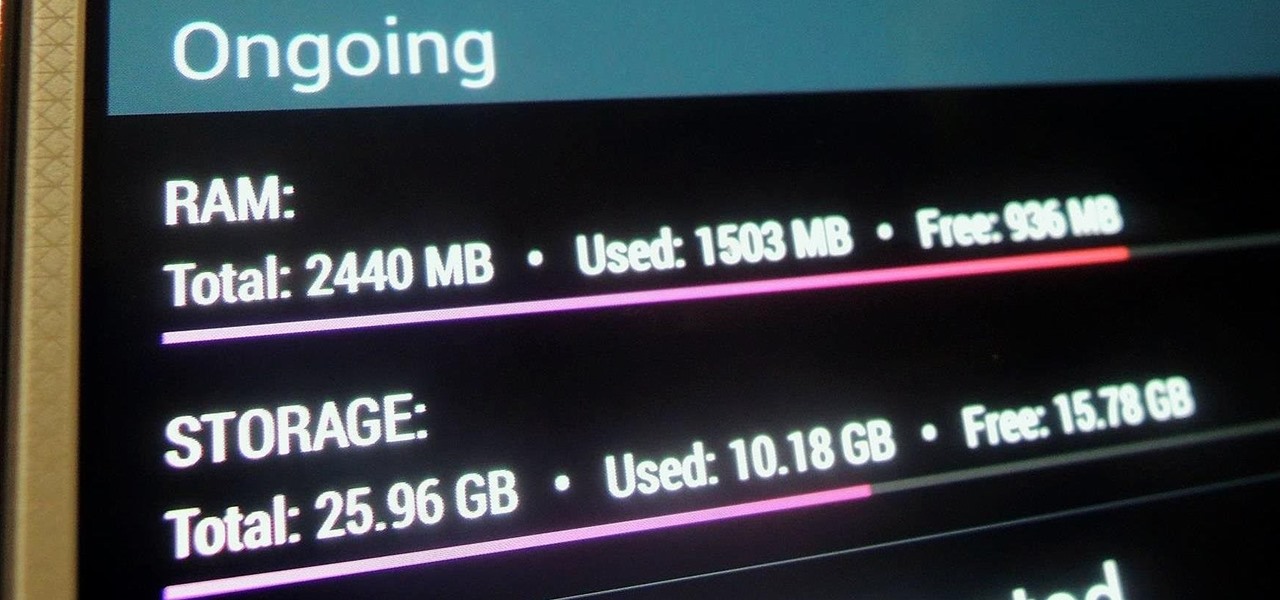
Modern smartphones can easily handle anything you throw at them, but it's always good to keep a tight grasp of what your phone is actually doing and how well it's doing it. System information can be viewed by looking through your Application Manager, but this process makes it difficult to keep an eye on usage in real time.
In the business world, it is always best to have the people you work with. For you to become the best you could give, here are at least 5 tips in using team building tools.

In this five part video series, we are going to be creating a gorgeous storage chest that is sure to be a favorite at your house. Over the course of these videos, I will give you easy to follow instructions, along with some helpful hints.