In this clip, you'll learn how to change the location of an audio track within an Audacity session with the Audacity Time Shift Tool. Whether you're new to the Audacity DAW (digital audio workstation) or are simply looking to pick up a few new and useful tips and tricks, you're sure to be well served by this video tutorial. For more information, including step-by-step instructions, take a look.

In this clip, you'll learn how to create a fade-out effect across the tracks of an Audacity session. Whether you're new to the Audacity DAW (digital audio workstation) or are simply looking to pick up a few new and useful tips and tricks, you're sure to be well served by this video tutorial. For more information, including step-by-step instructions, take a look.
In this clip, you'll learn how to use the Envelope Tool to automate the levels of your tracks within an Audacity session. Whether you're new to the Audacity DAW (digital audio workstation) or are simply looking to pick up a few new and useful tips and tricks, you're sure to be well served by this video tutorial. For more information, including step-by-step instructions, take a look.
In this clip, you'll learn how to export each indvidual track within an Audacity session to a separate WAV or MP3 audio file. Whether you're new to the Audacity DAW (digital audio workstation) or are simply looking to pick up a few new and useful tips and tricks, you're sure to be well served by this video tutorial. For more information, including step-by-step instructions, take a look.
Learn how to restore your lost data with Sony Vegas video editor. Whether you're completely new to Sony's popular nonlinear editor (NLE) or are a seasoned digital video professional simply looking to pick up a few new tips and tricks, you're sure to be well served by this free video software tutorial. For more information, including detailed, step-by-step instructions, take a look.

Without sharps and flats, piano players would fall asleep at the piano bench and faceplant their sheet music. Keep your next piano session a lively (and alive) one by watching this tutorial on what sharps and flats are and where they're located on the keyboard.

More often that not, beginner harmonica players will have to be told the key to use during a jam session. It's perfectly reasonable to ask the key, so long as it's before the song starts that you're asking. But if the answer is obvious, you're better off knowing than asking. You don't want to look silly by asking obvious questions. This video will show you to know the key without asking.

Hunting and pecking through your gaming session can be a real drag, so why not ease your play with hotkeys? Download the appropriate set of custom keys and then follow the video to learn how to install and enable them. Now isn't that a lot easier?

Does your man run every time he sees a dance floor? It's common. Luckily, YourTango put together this advice video on how to get your man out on the dance floor with you! By enrolling in a class, sparking up a low-key dance session in your living room, or implementing small trade-offs, you might just see a change of your heart from your better half in no time at all!

This audio editing software tutorial shows you how to record audio and MIDI tracks in SONAR Home Studio 6. The SONAR 6 tutorial includes setting inputs, tempo, metronome, checking levels, inserting Virtual Instruments, and using the Session Drummer 2. If you are new to using SONAR 6 to edit and create music recordings, this tutorial will get you started.

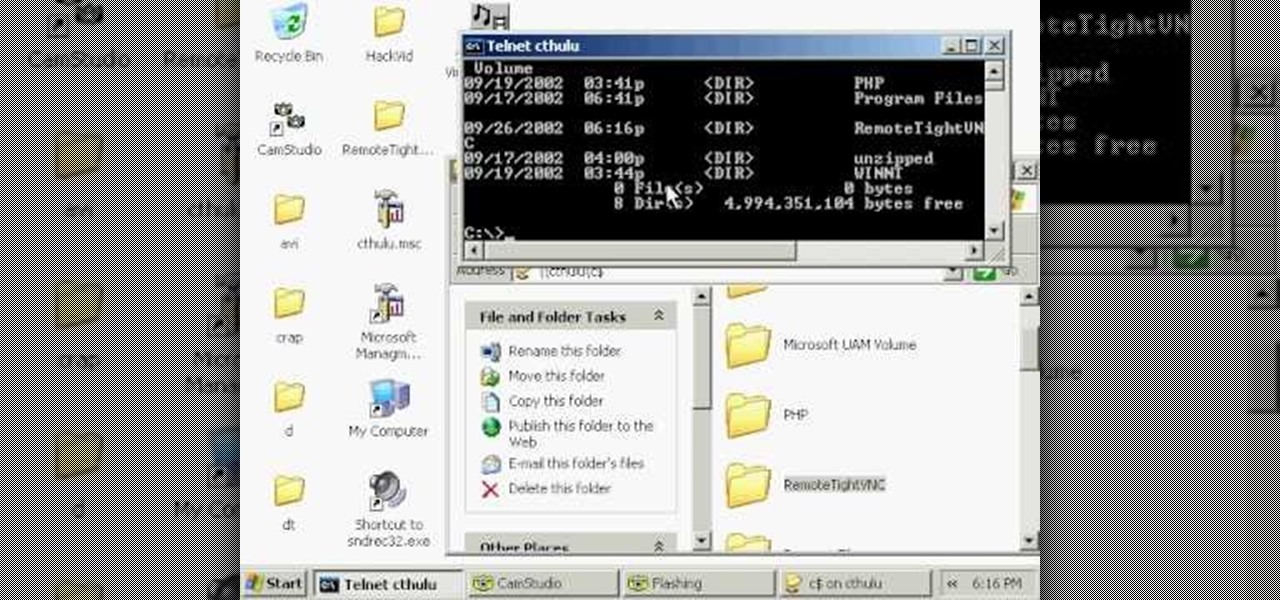
In this video tutorial, you'll learn how to install VNC, or Virtual Network Computing, remotely onto a Windows machine for GUI access. This tutorial assumes you know how to start a session and get into active command line access in a remote Windows PC. For step-by-step instructions, press play.

Get flat firm and fabulous abs with tips form the experts. In this fitness how to video SELF Magazine demonstrates an extensive abdominal workout session. Watch and learn how to do the following exercises: slideshow, dolphin pull, bridge plus, krav maga kick, bow wows, chair roll ups, waist whittler, oblique X, tense/relax, chair lifts, swan dive and side slimmer. These twelve core strengthening moves are sure to give you flat, firm and fabulous abs.

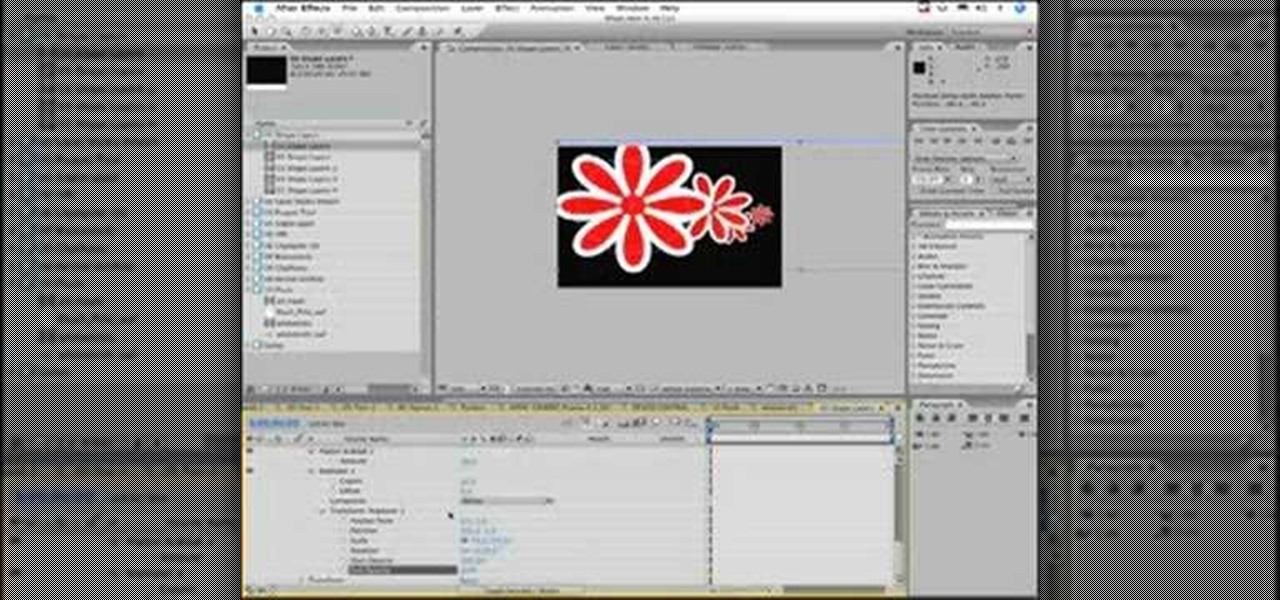
Learn how to use the Shape Tools to create dynamic motion graphics elements in After Effects. This tutorial was recorded as part of a session at the 2007 NY Post Production Conference. Watch and learn how to effectively use the shape tools in After Effects CS3 for your motion graphics and compositing projects.

It is alway important to focus on our body when practicing yoga. But the truth is that we can't always do that. This how-to video has a yoga breathing routine that will help you to tune in and relax at your next yoga session.

This screencast is a pair programming session between David Heinemeier Hansson and Miles K. Forrest. Miles is new to web application programming and a "bunny hill" Ruby on Rails developer at best. If you're new to Ruby on Rails this 35 minute screencast programming tutorial might help point you in the right direction.

This is a clip from the seven hour session in which David I. Herman, known as "Doz", tattoo's his own upper right thigh with a Tiger and Flame tattoo design. Warning: Please do not try this unless you are professional tattoo artist. Do not try this at home

Your man will be putty in your hands after this session of Love U! Learn how to train your man.

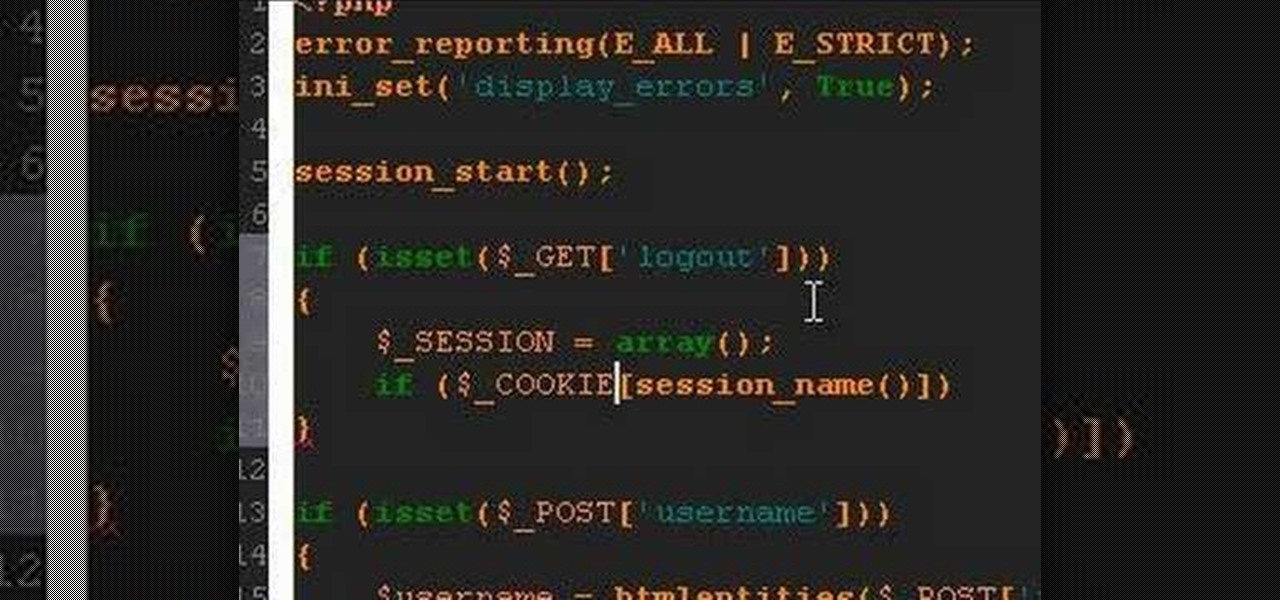
A PHP tutorial on how to log out a user and destroy a session.

Scientology Minister Marlene Coates demonstrates the E-Meter, the much discussed electronic instrument used in Scientology Counseling sessions. Ms. Coates shines the light of truth and simplicity on a much misunderstood, yet invaluable tool of the trained Scientology Practitioner.

This video demonstrates how to end a Reiki session. The video walks you through closing the Chakra and giving the patient Reiki water in order to achieve balance.

Post-exploitation information gathering can be a long and drawn-out process, but it is an essential step when trying to pivot or establish advanced persistence. Every hacker should know how to enumerate a target manually, but sometimes it is worth it to automate the process. Metasploit contains post modules that can quickly gather valuable information about a target, saving both time and effort.

Augmented reality developers who have exhausted their treasure trove of video tutorials and panels from the recent Magic Leap developer conference can now shift their continuing education attention to Unity.

Coming up at the end of May is the world's largest conference and expo dedicated to all things augmented and virtual reality, the Augmented World Expo, more commonly known just as AWE. And this year, a few of us from NextReality are going to be there.

Once you've designed some holograms with HoloLens, you'll need to get them to interact with the environment. That's where Spatial Mapping comes in. There are five basic purposes for using HoloLens's Spatial Mapping with your app:

Welcome back, my novice hackers! In this continuing series on Metasploit basics, let's next look at a module that many aspiring hackers find useful—autopwn.

Gardening school is in session and Shirley is teaching the absolute basics, such as: what to wear, what tools to use, what is the difference between an annual, perennial, and biennial? What is a garden zone, and which one is yours? Class is in session, so spit out your gum and listen up. Time to learn Gardening 101.

If you're a musician, Google wants you on Google+ Hangouts. In an effort to make it easier to stream your concerts, performances, and impromptu jam sessions, they've revealed their latest feature: Studio Mode. Enabling the new Studio Mode optimizes your Hangouts On Air for music, and the quality difference is massive.

Google Fit houses all of your essential fitness-related information in the cloud for safekeeping at all times. You can easily let your device detect your workout sessions for you automatically based on a variety of sensors. At the same time, the Fit app makes it easy to manually start a workout as well.

With a fresh infusion of $9.7 Million in funding on its ledger, enterprise augmented reality company Scope AR has now expanded the functionality of its WorkLink platform.

While the USB Rubber Ducky is well known by hackers as a tool for quick in-person keystroke injection attacks, one of the original uses for it was automation. In this guide, I'll be going the latter, explaining how we can use it to automate Wi-Fi handshake harvesting on the Raspberry Pi without using a screen or any other input.

Hello Friends … My name is Suresh Senarathna and this is my first “How-To” post,

It's easy to forget sometimes that even when you're sitting in the basement playing Grand Theft Auto 5 Online that you're not really alone. Everything you say into the mic can be heard by anyone else in that same session.

I've had the thankless duty of choosing the music for far too many get-togethers, and no matter how good you think your music taste is, or how many new tracks you have on your iPhone or iPod, you will never—ever—satisfy everyone.

Take a look at this video and learn how to fish for crabs with crab pots. These tools are typically used on fishing ships or rather, "crabbing" ships. The average king crab pot typically uses 66 fathoms of line, which is a total of 198 feet.

It turns out that attending the L.E.A.P. conference last month may have mostly been best for demoing the Magic Leap One in person, as the company has now uploaded the majority of the insider panels held at the event in Los Angeles.

Welcome back, my greenhorn hackers! A few years back, Microsoft implicitly recognized the superiority of the Linux terminal over the GUI-based operating system by developing PowerShell. Since Windows 7, every Windows operating system has had PowerShell installed by default, and they even made PowerShell capable of running Linux commands on Windows!

Imagine this scenario: You exploited a system using metasploit and you want to install a backdoor. You have a few options;

Let's say that we want to see what someone is doing on their computer? In this tutorial, we'll be hijacking cookie sessions to do just that!

Welcome back, my budding hackers! With this article, I am initiating a new series that so many of you have been asking for: Hacking Web Applications.

Easttexas937 shows viewers how to properly use a Ouija board to get the best experience. First you will need a Ouija board and a pointer. If you want to make these two things, you should use lightweight glass and make sure you make the board properly. You have to have an open mind and good intentions when you go in to use the board. There also must be no secrets between the friends playing and you should not have a friend that is not trustworthy. This will keep evil spirits out. Always have m...